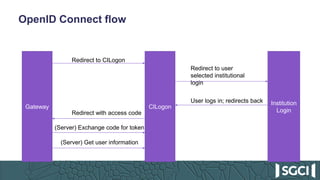
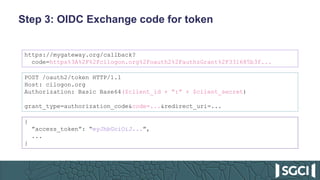
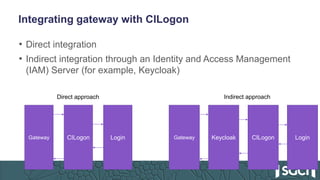
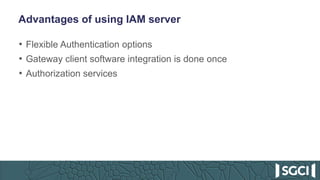
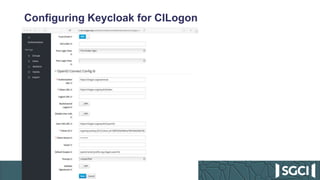
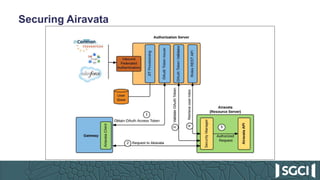
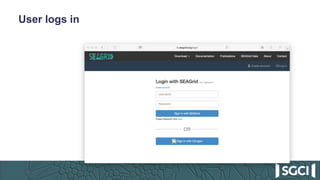
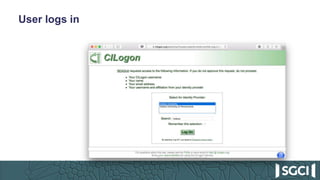
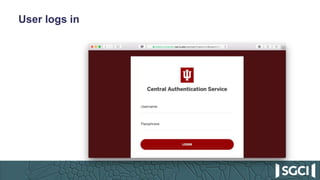
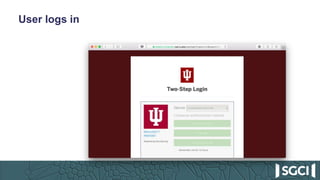
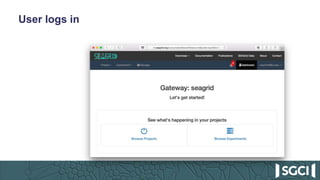
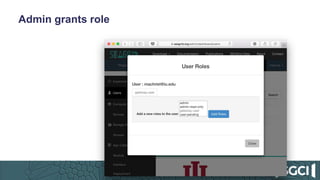
The document discusses the integration of Keycloak for authentication and authorization in science gateways, addressing issues like managing multiple user credentials and access controls. It outlines the workflow for using OpenID Connect with CILogon, detailing the steps required for client registration and user authentication. Keycloak is highlighted as an open-source identity and access management server that allows flexible integration and user role management to streamline access to various gateway services.