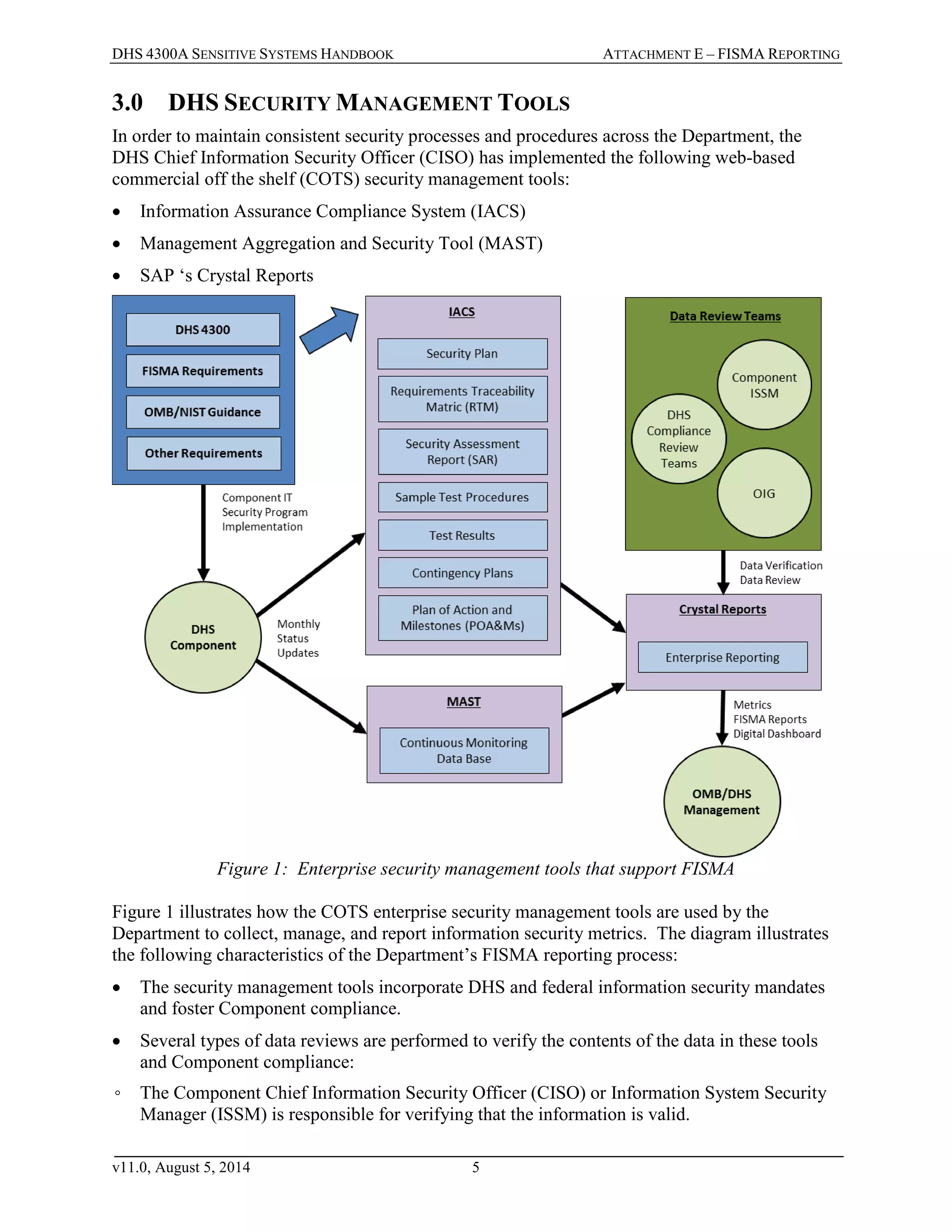
The DHS 4300A Sensitive Systems Handbook Attachment E outlines the Federal Information Security Management Act (FISMA) reporting requirements and the procedures for the Department of Homeland Security (DHS) to comply with these requirements. It describes the purpose, background, reporting mechanisms, and security management tools utilized by DHS for maintaining compliance and improving information security oversight. Additionally, the document provides details about the responsibilities of various officials involved in the FISMA reporting process and the metrics collected to ensure effective cybersecurity measures within the agency.