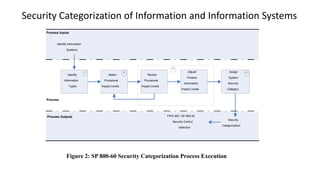
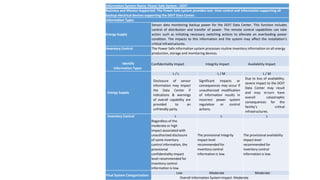
The document discusses security categorization of information and information systems. It provides definitions for information type and information system. The security categorization process involves identifying information systems and types, selecting provisional impact levels, reviewing levels, and finalizing categories. An example is given of categorizing an energy supply information type and inventory control type within the Power Safe system, which is given an overall moderate system impact categorization. Action items are outlined for developing policies, templates, training, and completing agency categorization studies.