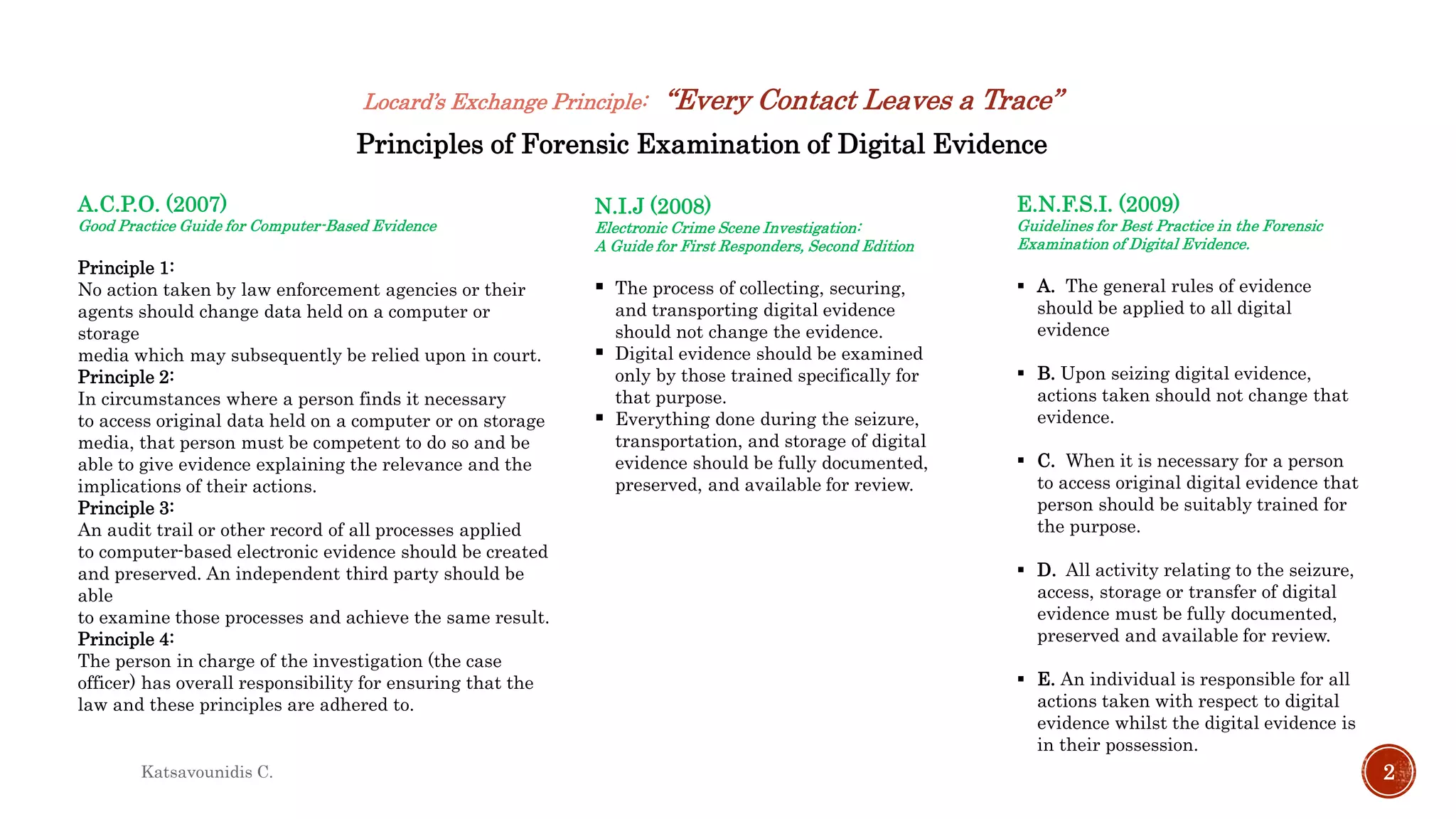
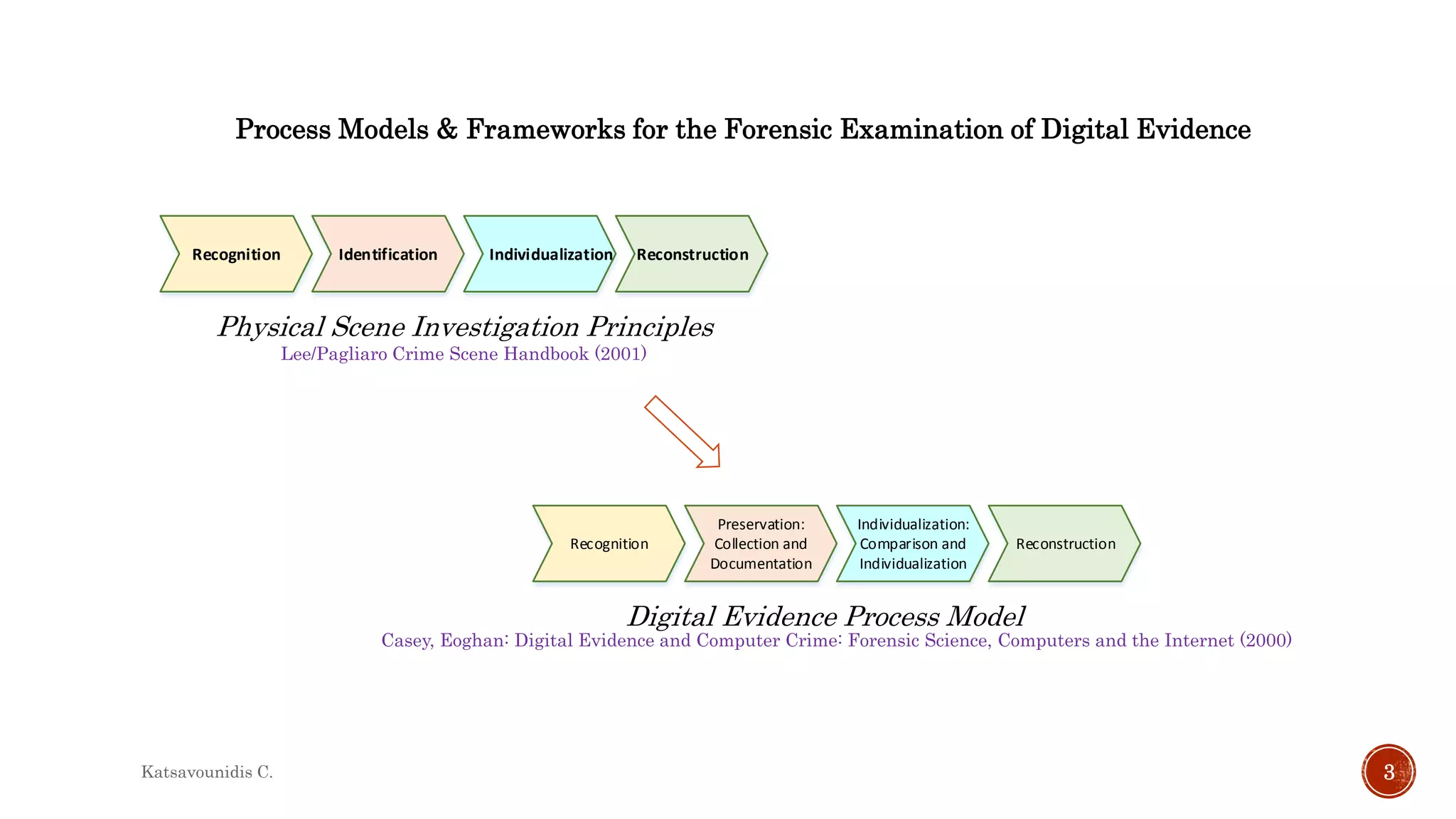
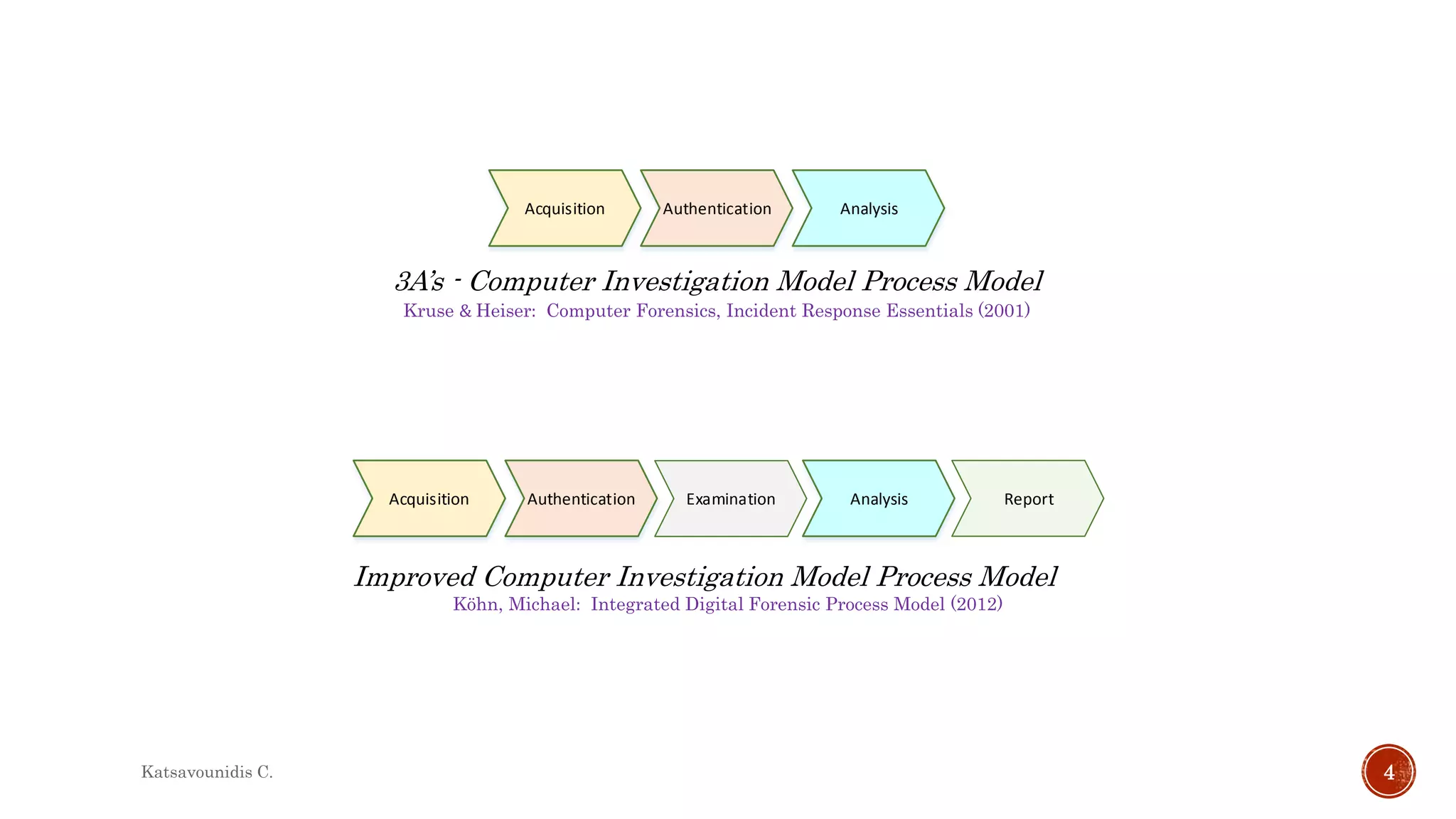
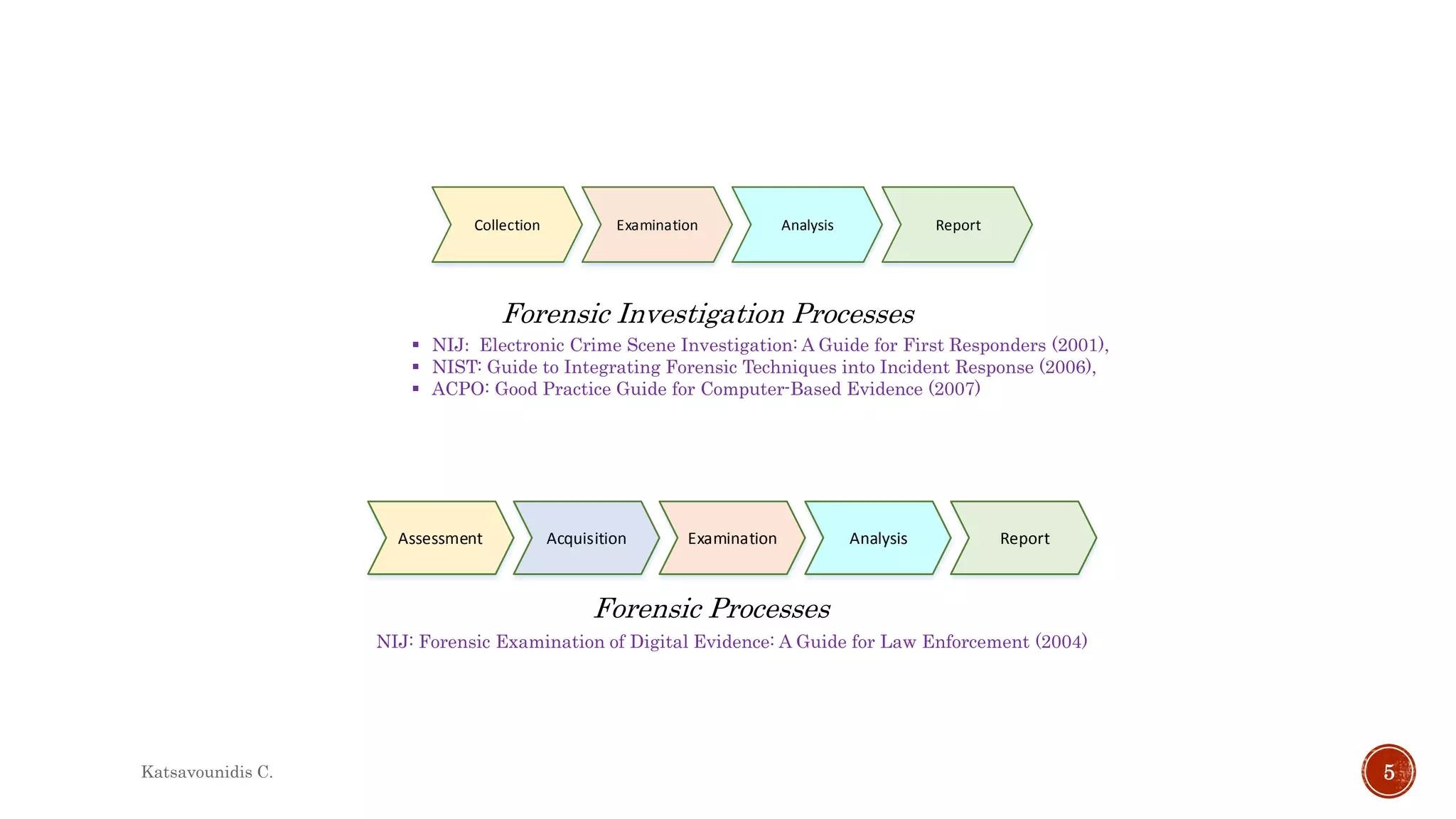
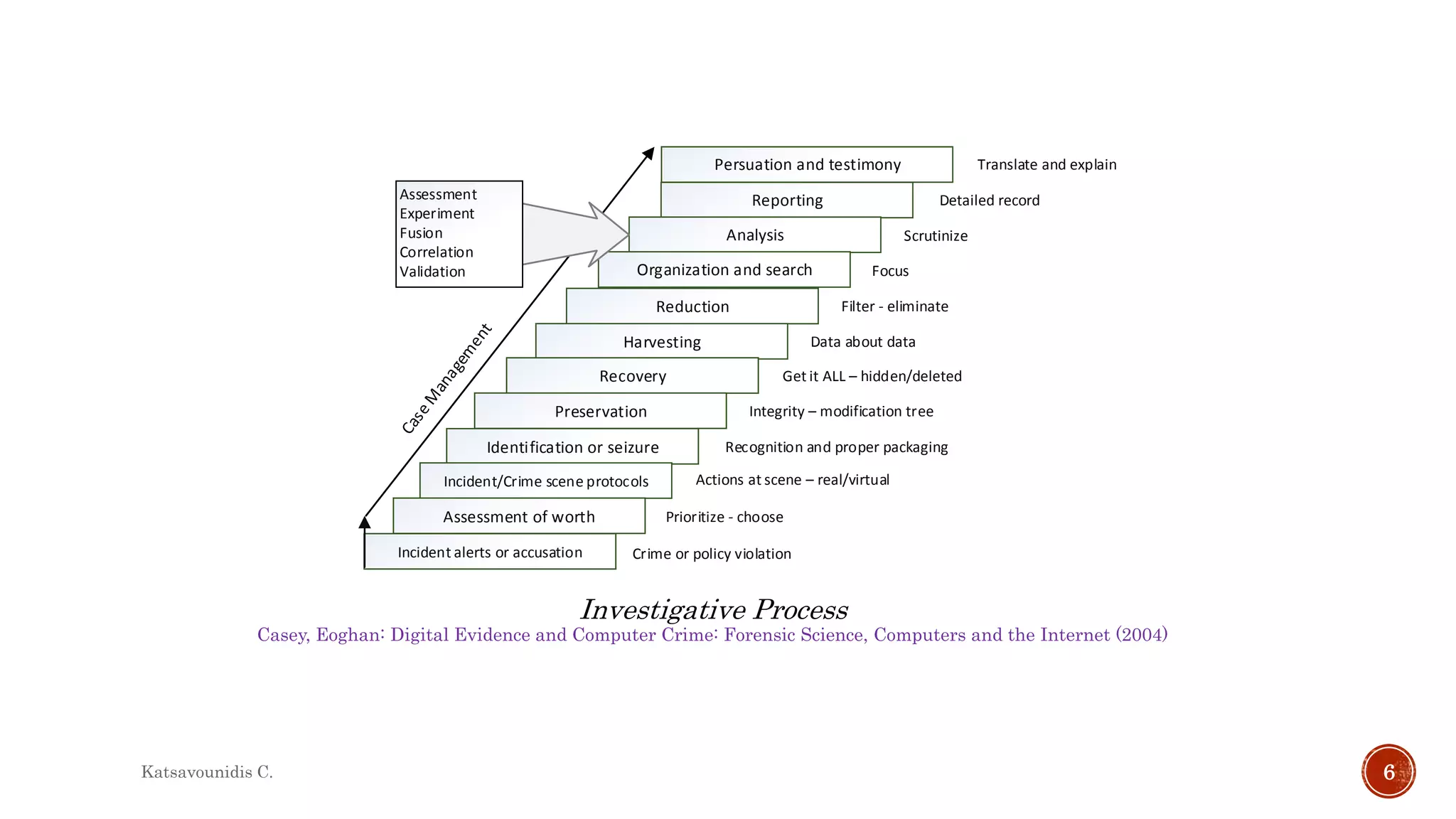
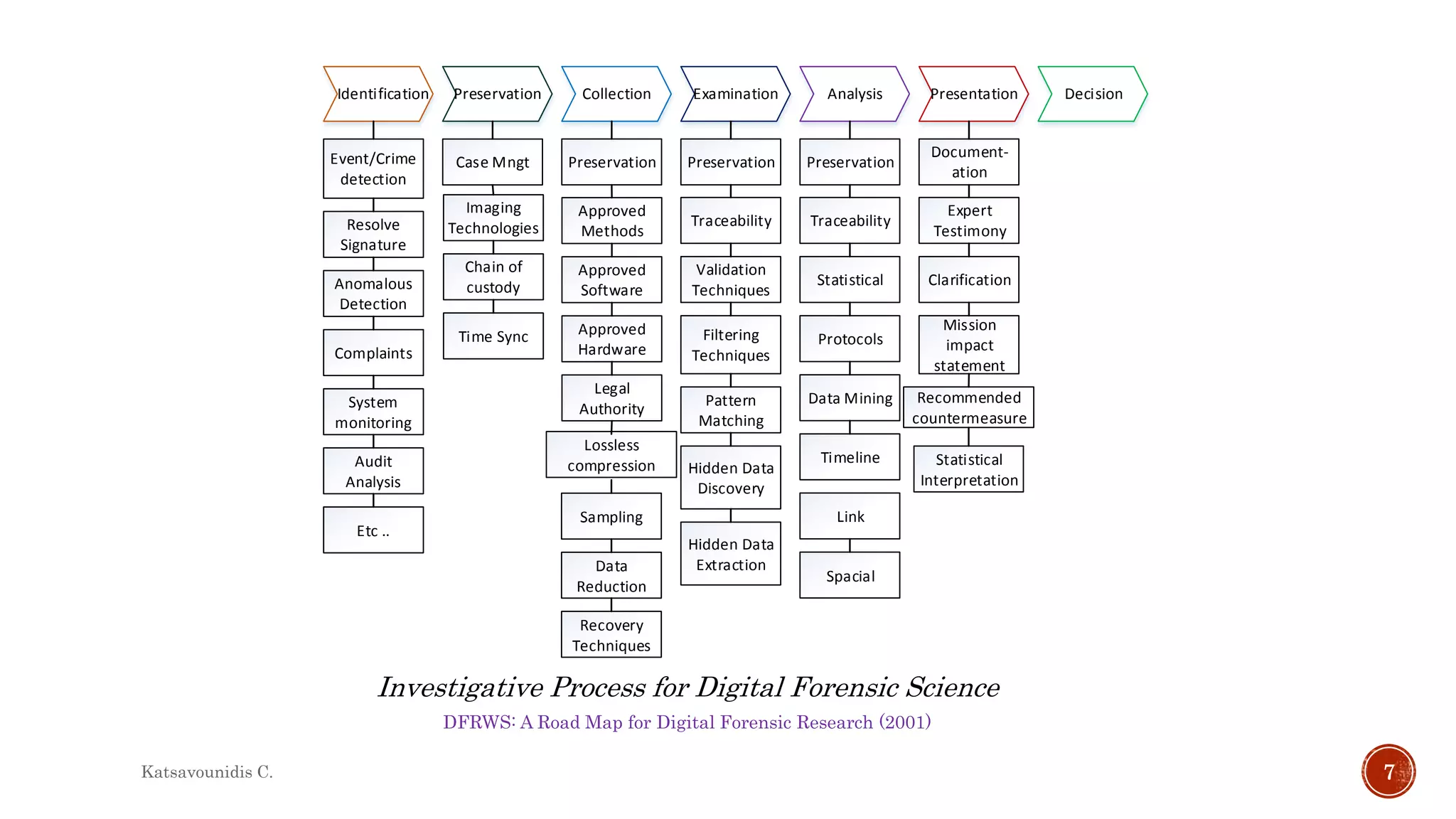
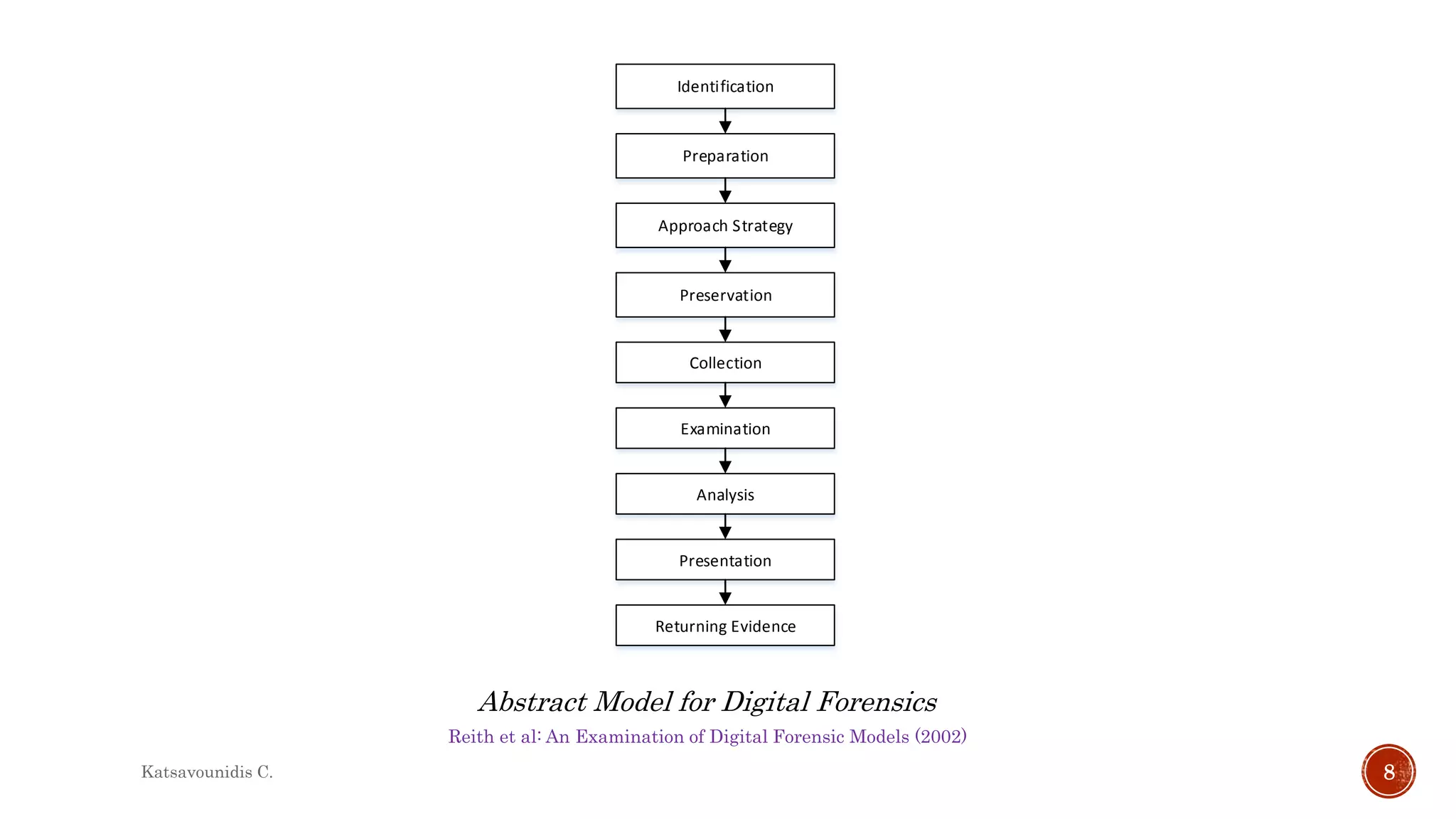
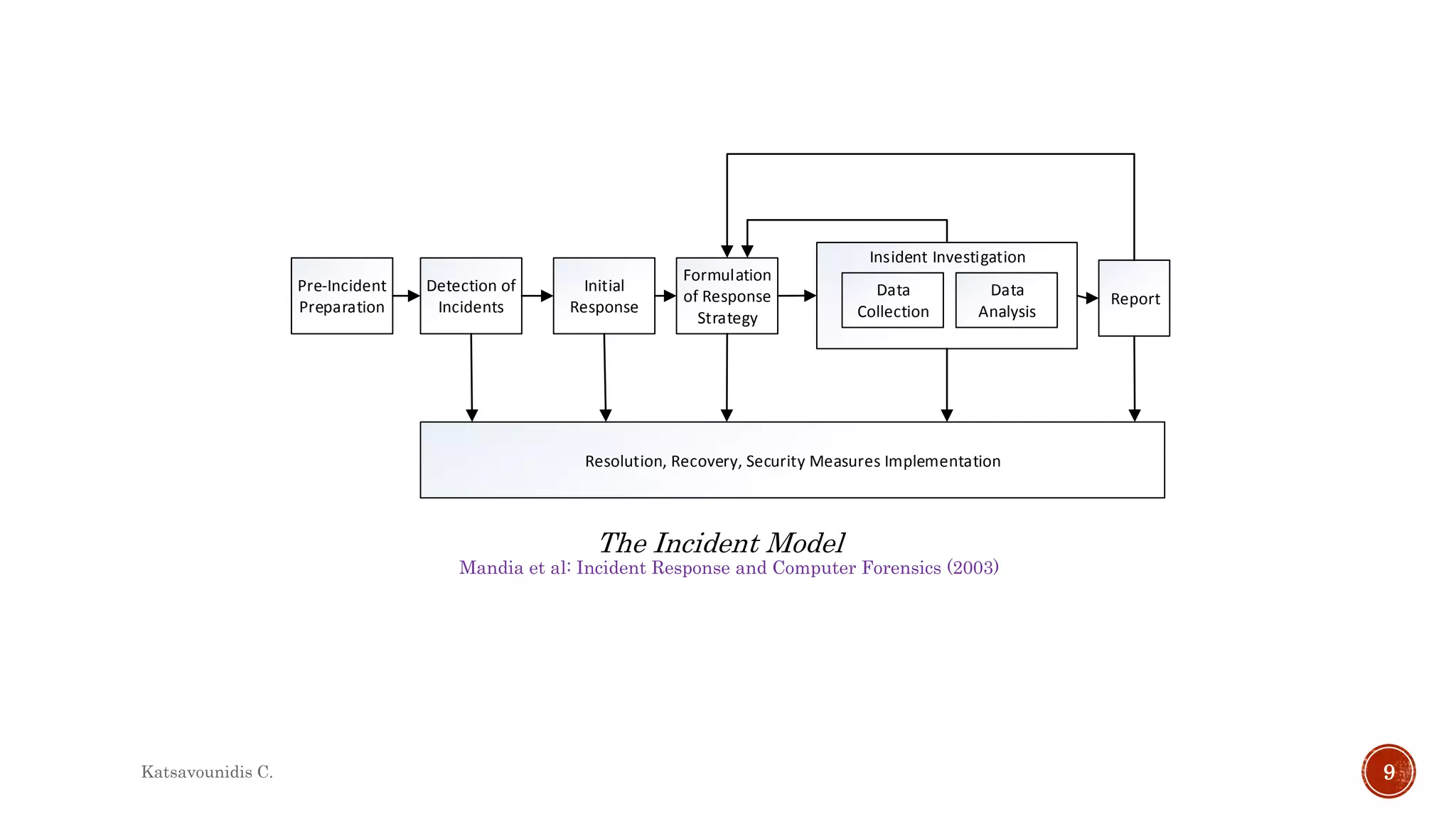
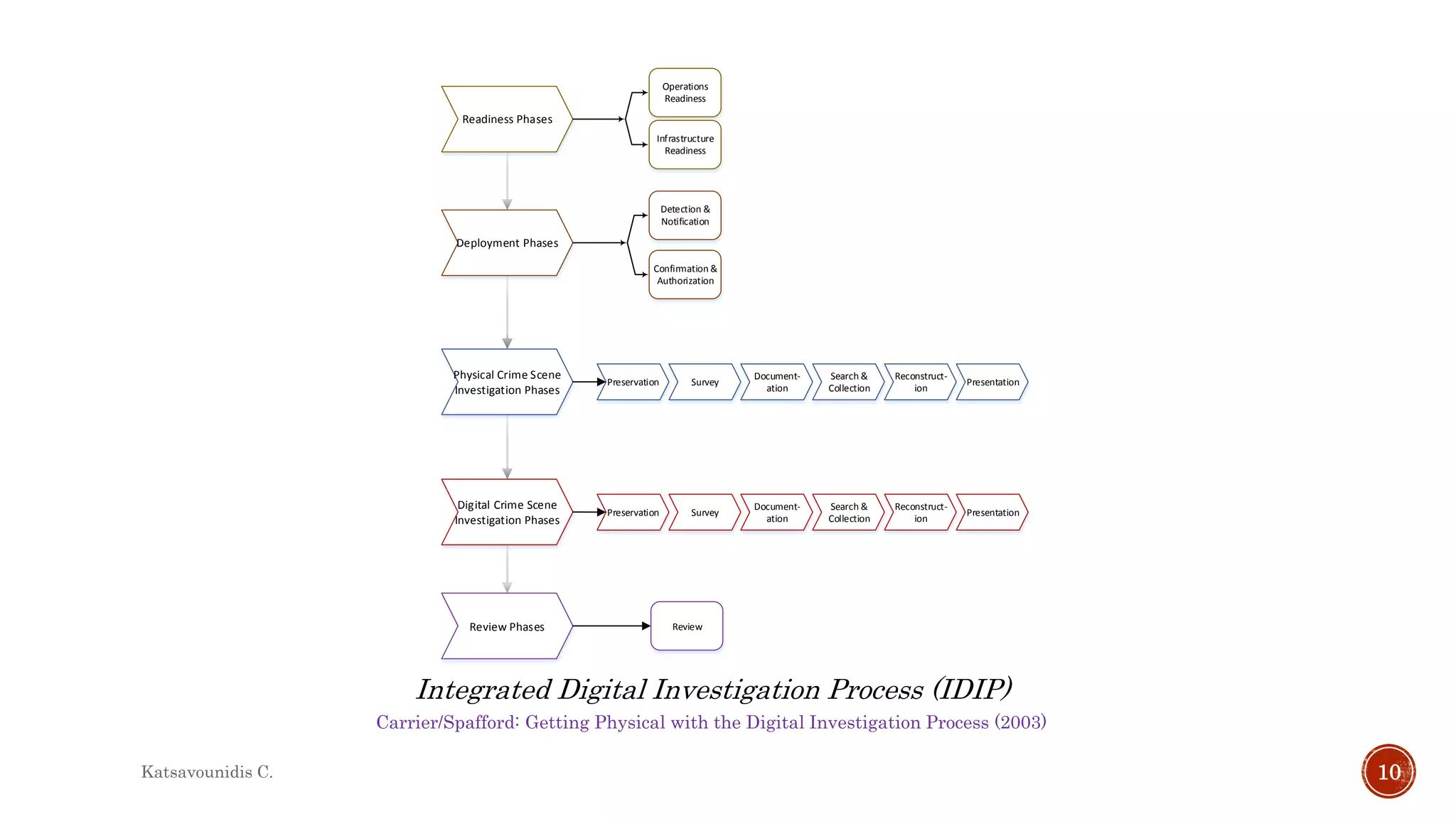
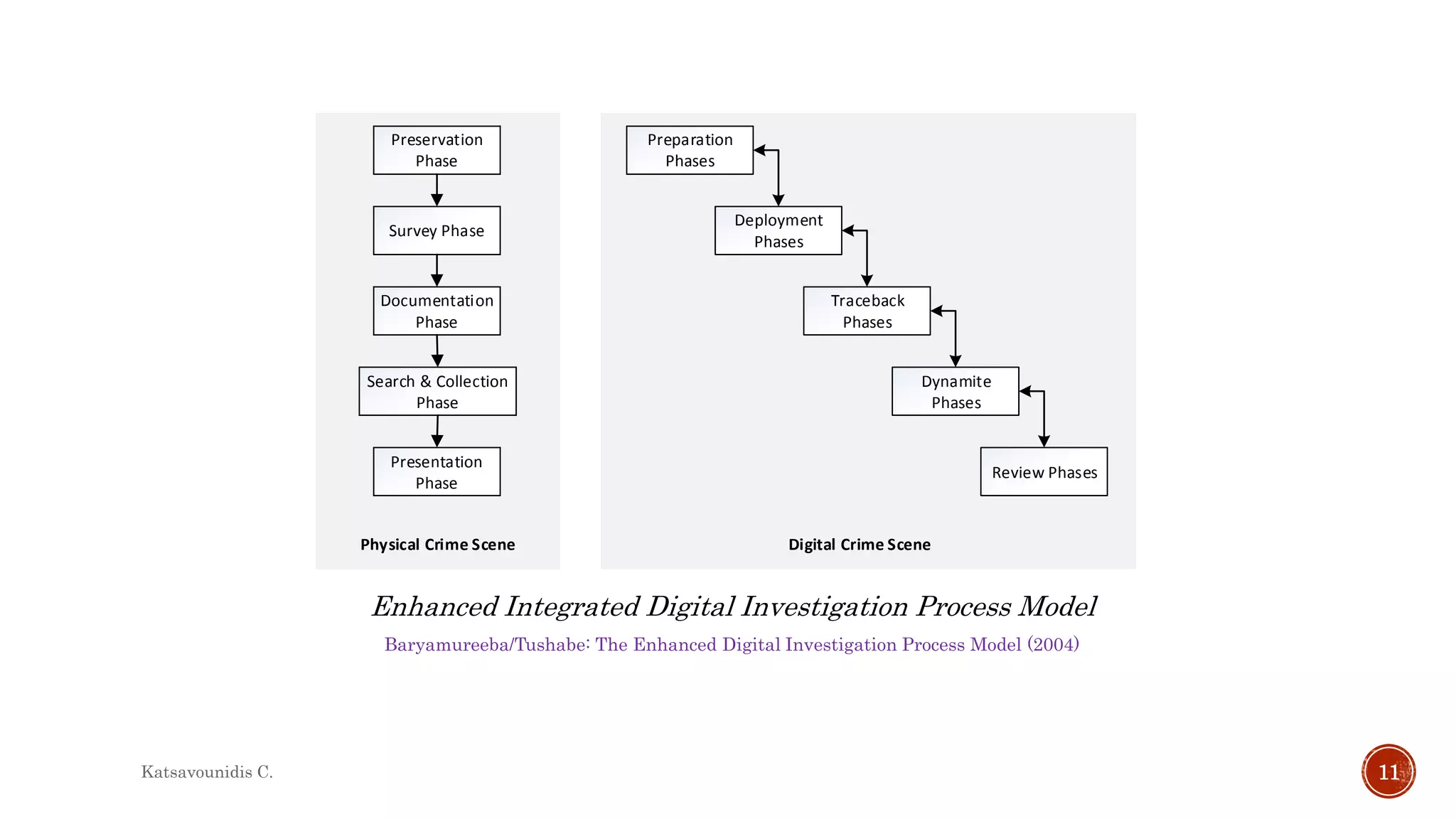
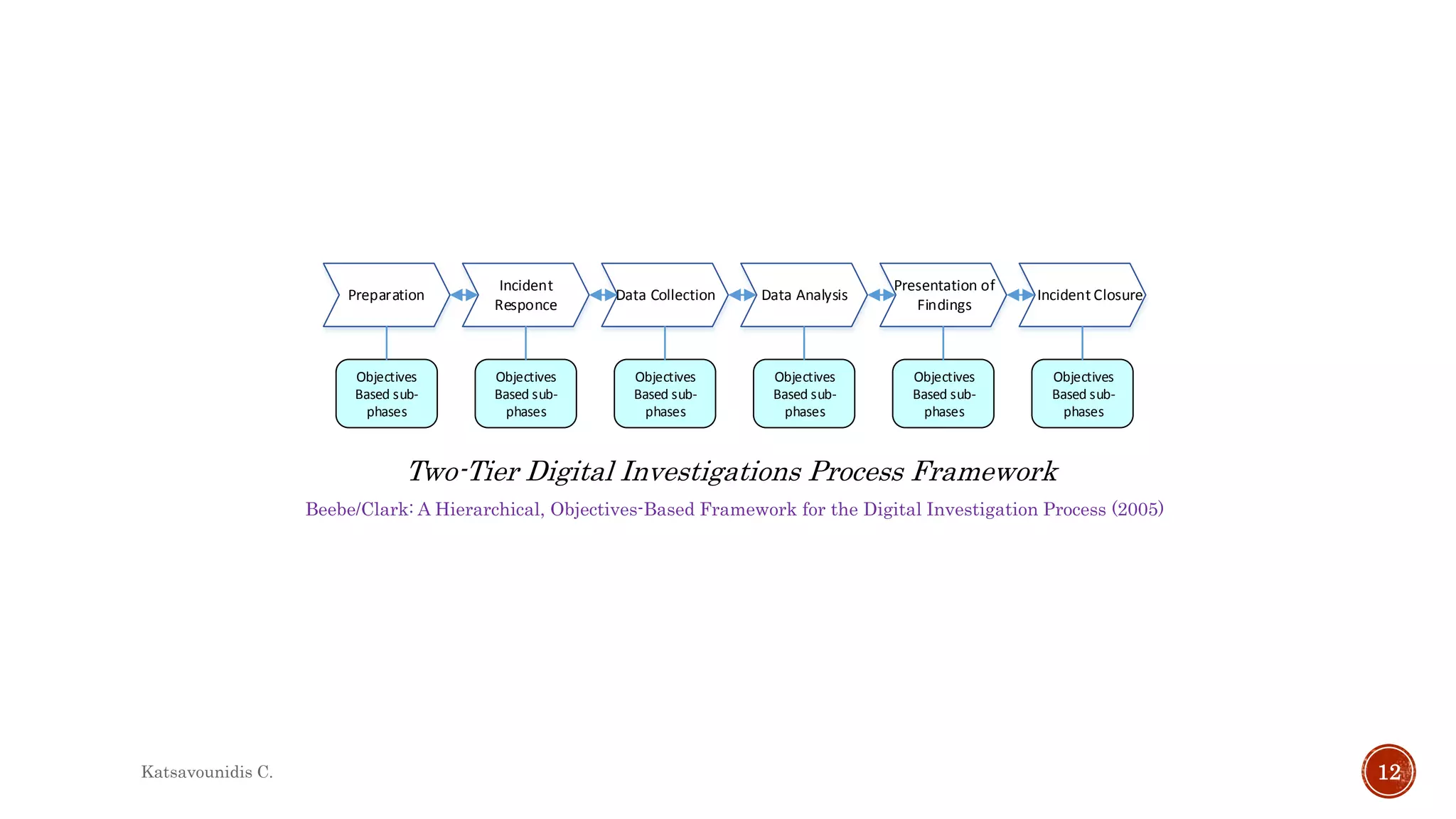
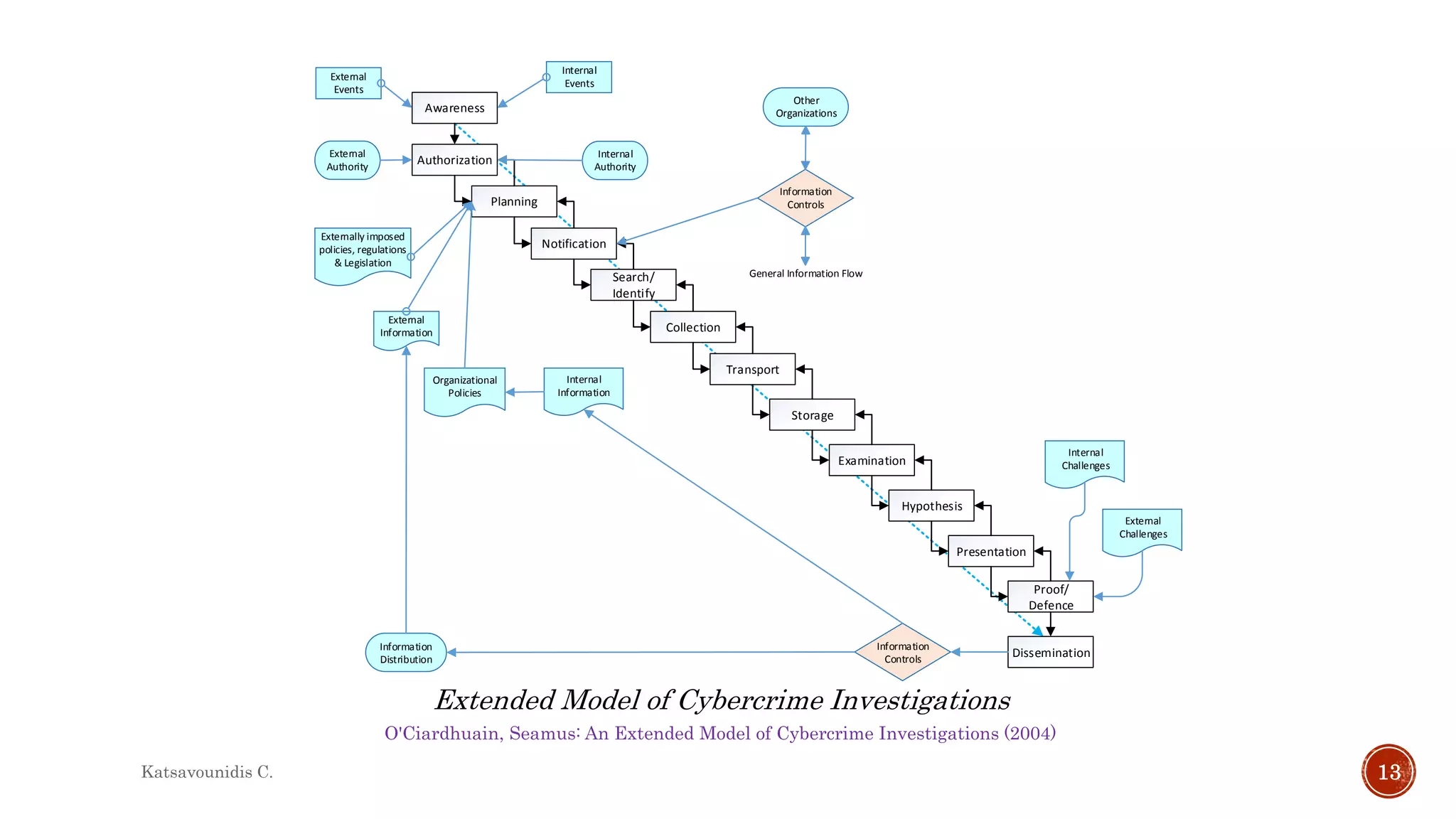
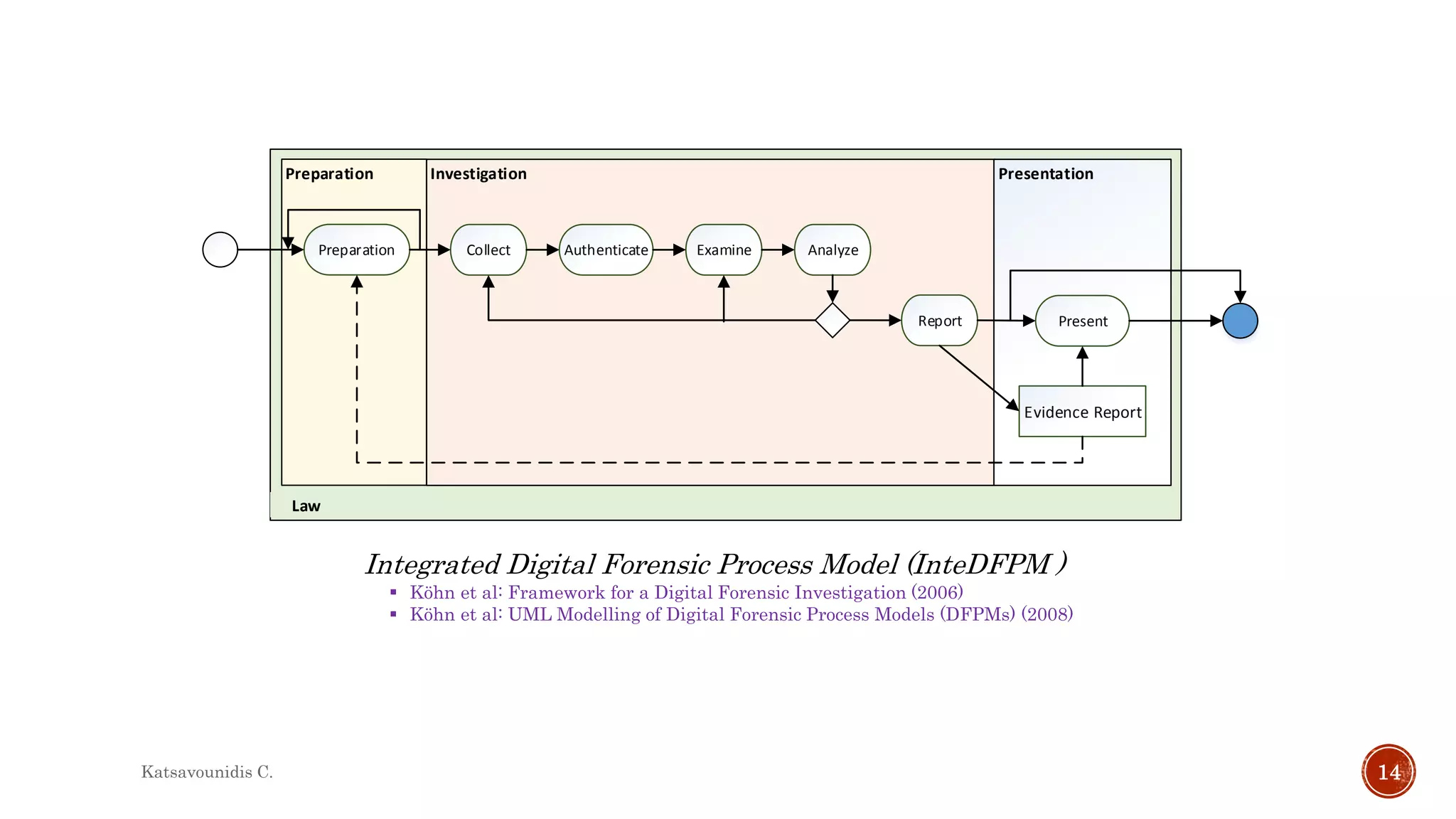
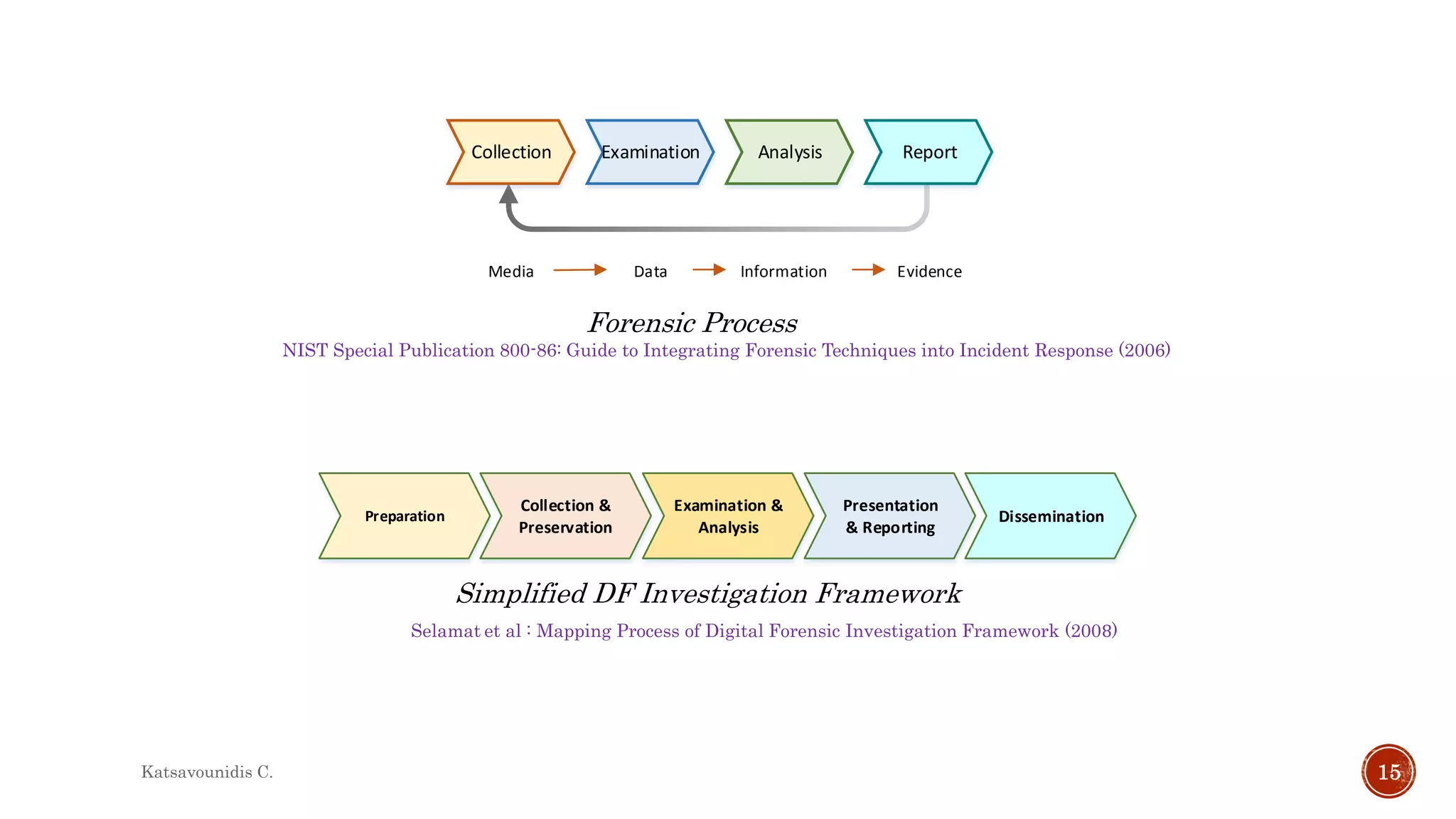
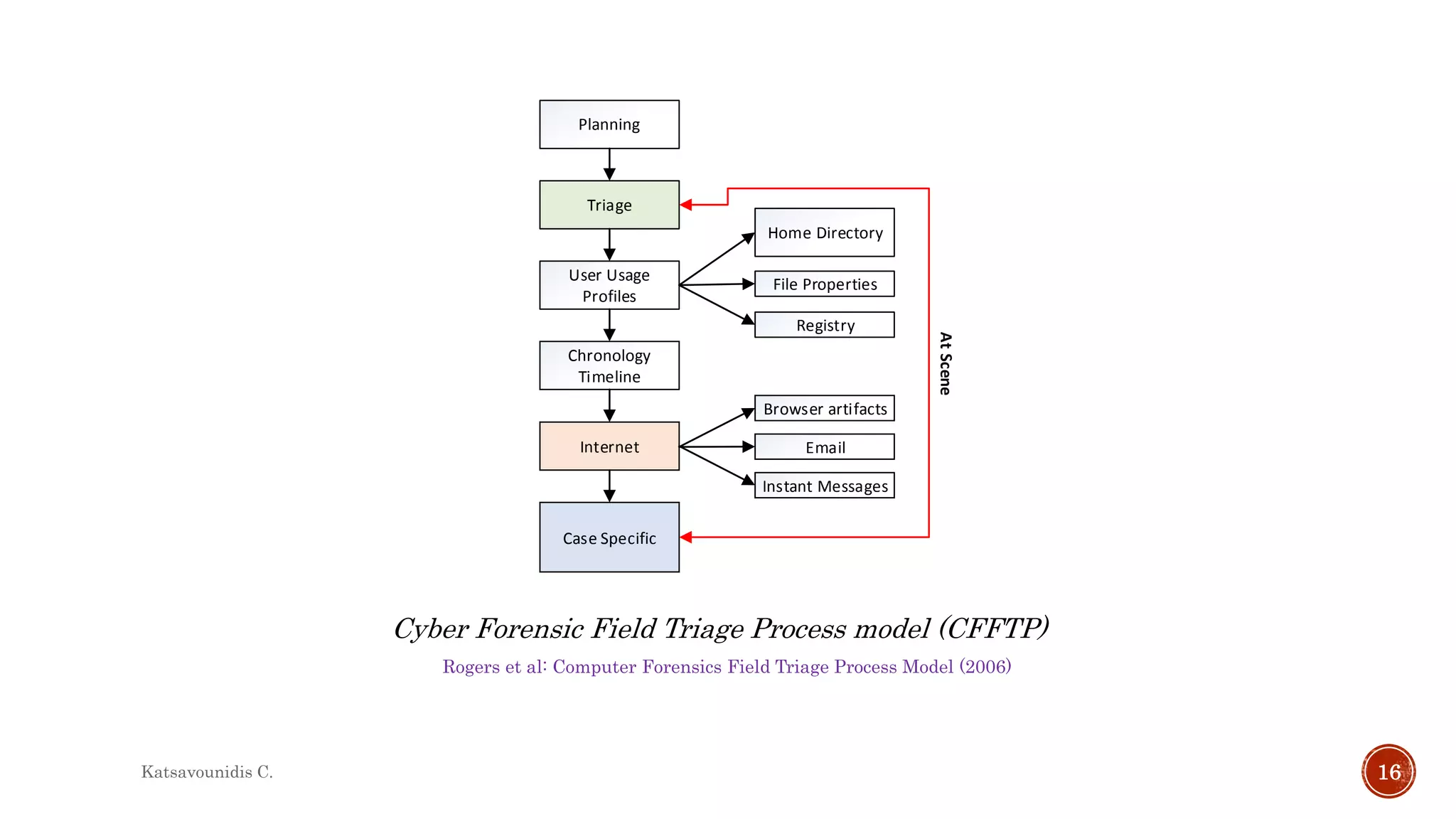
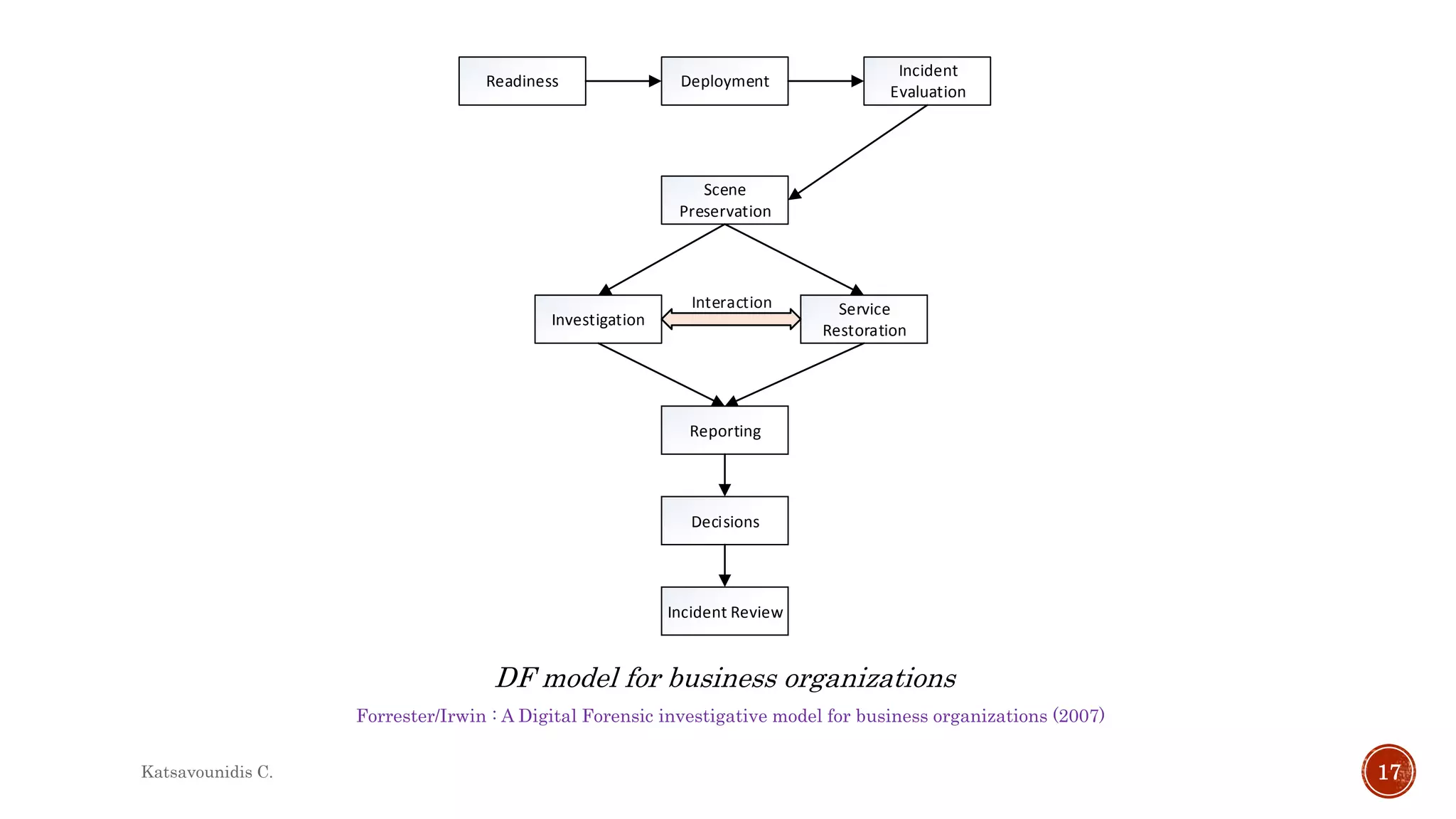
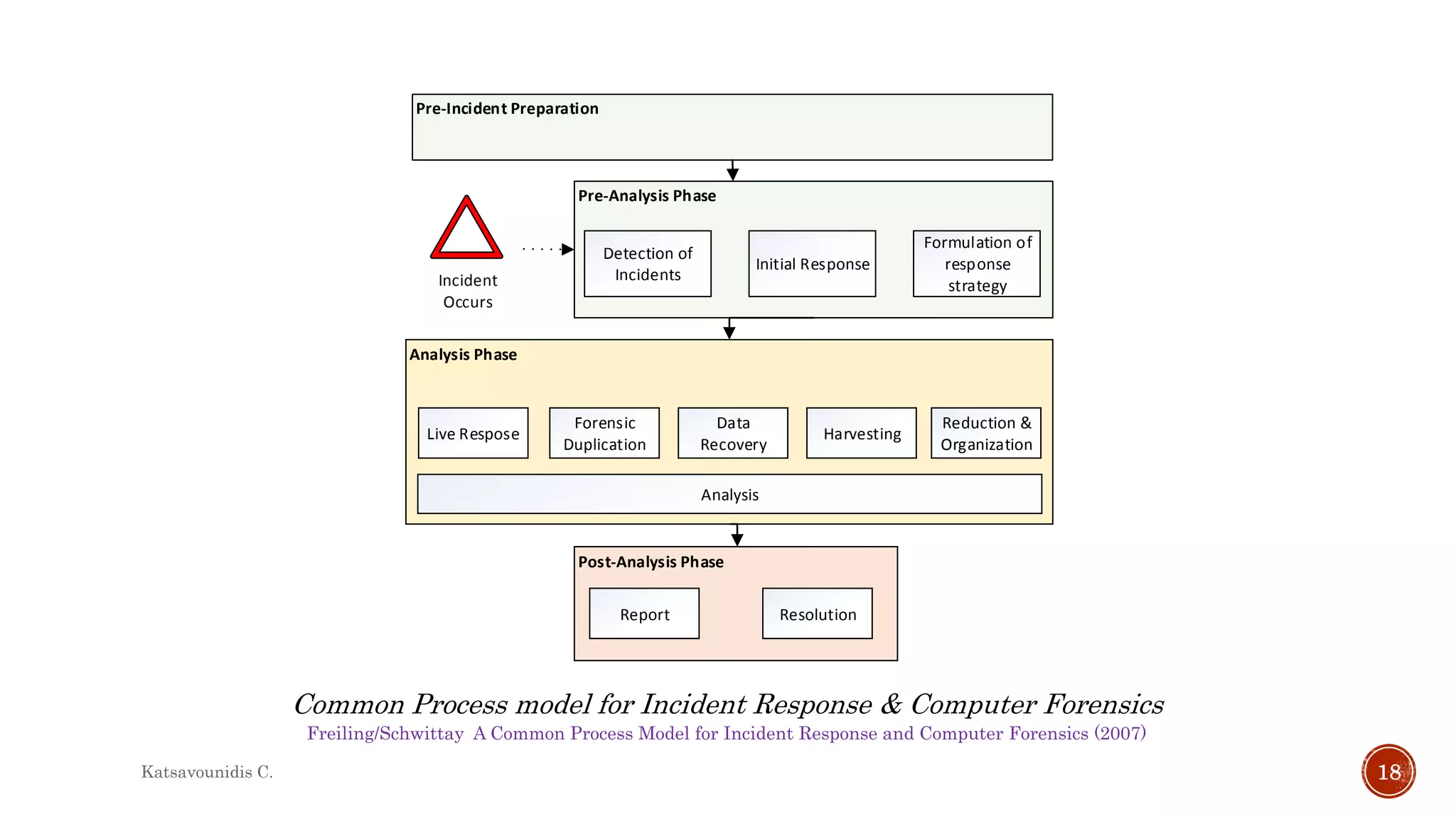
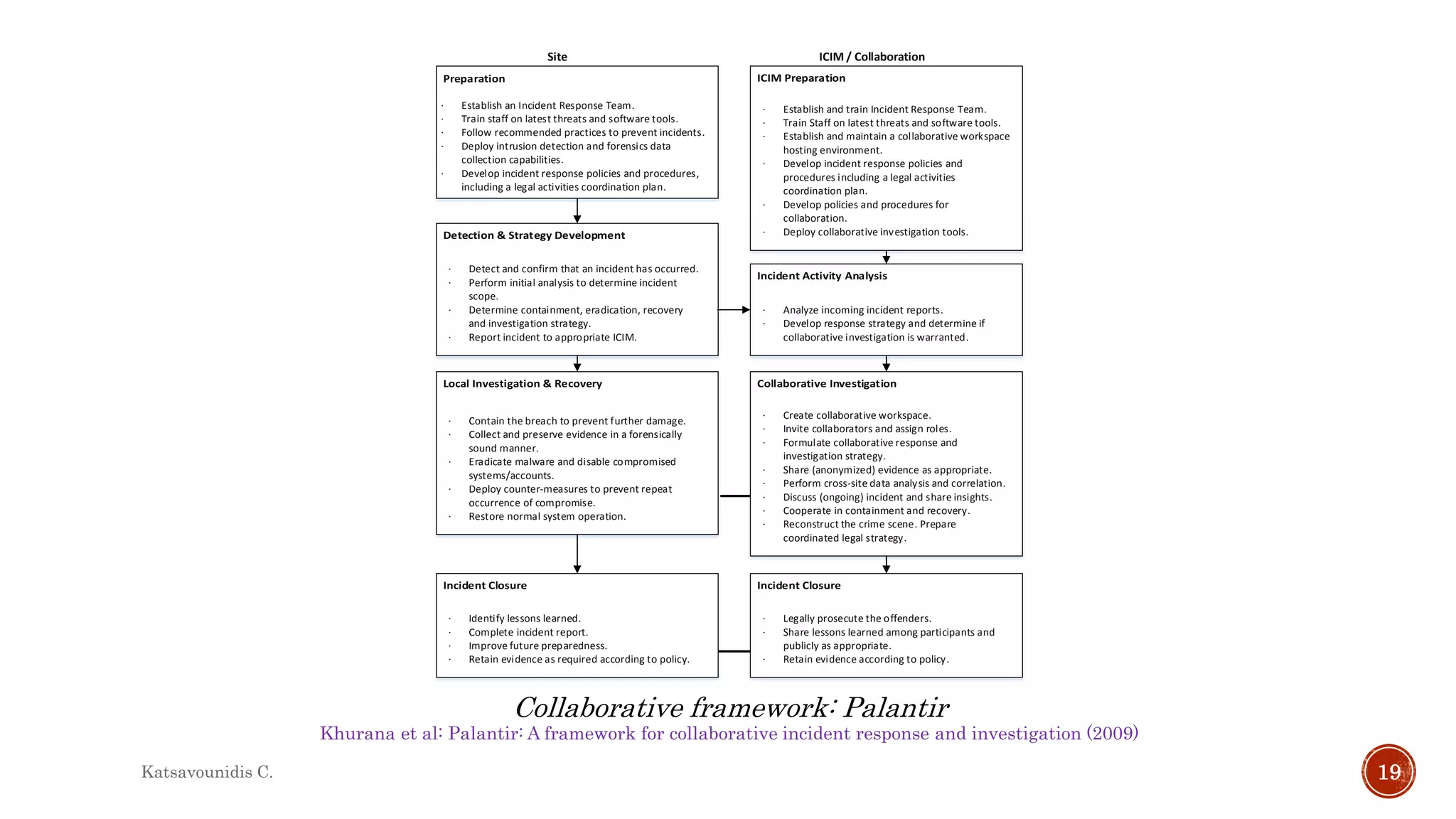
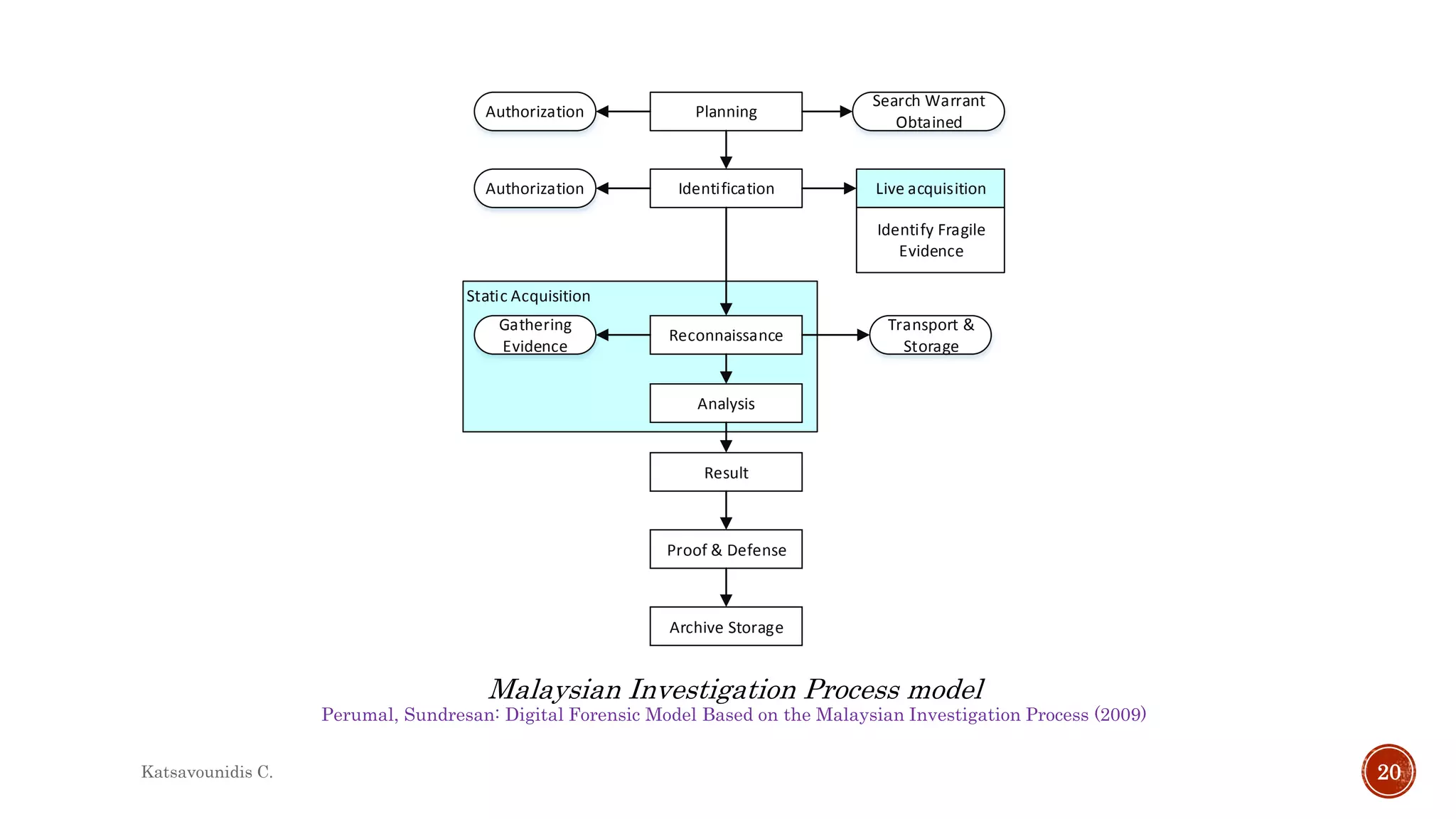
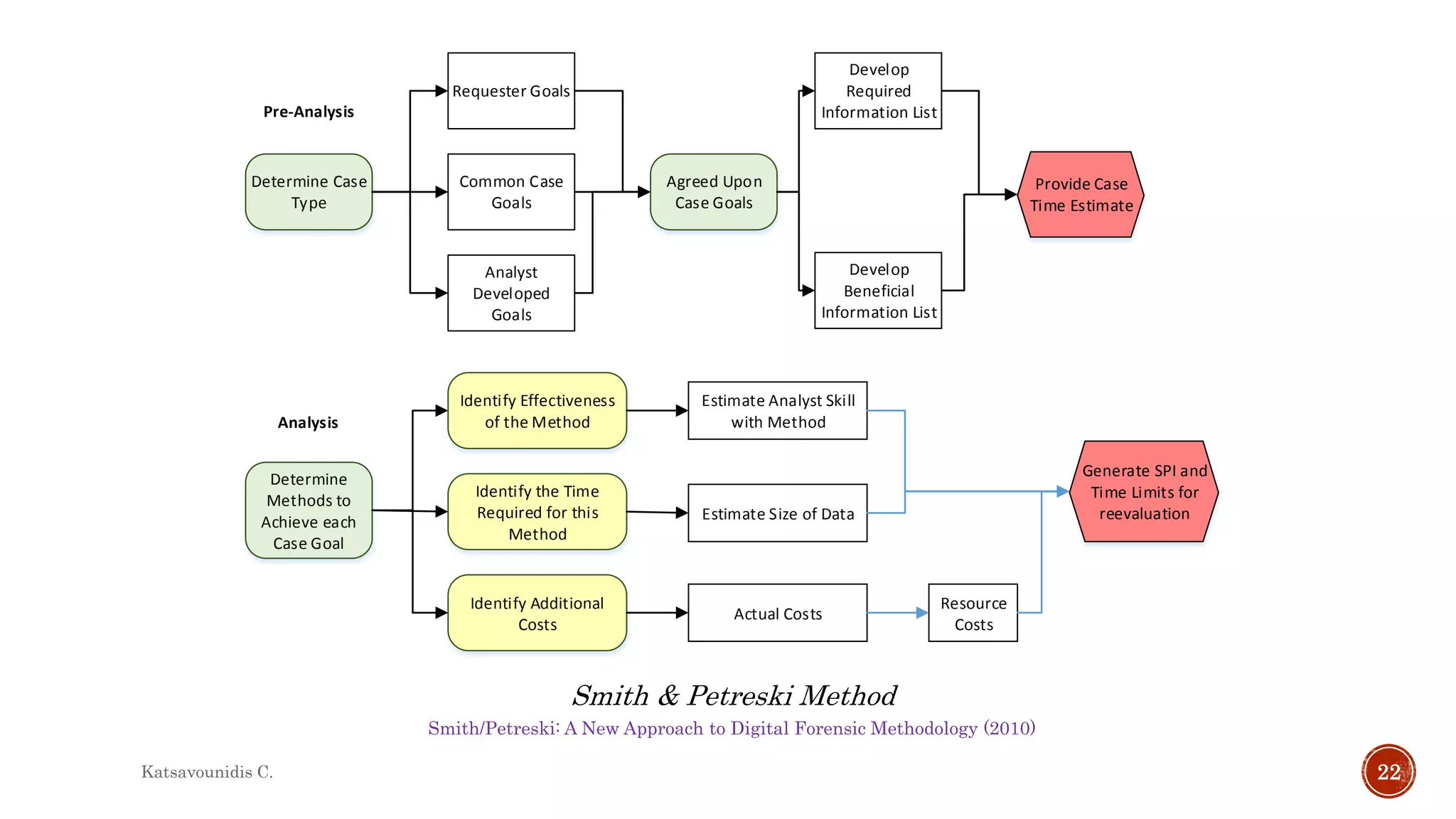
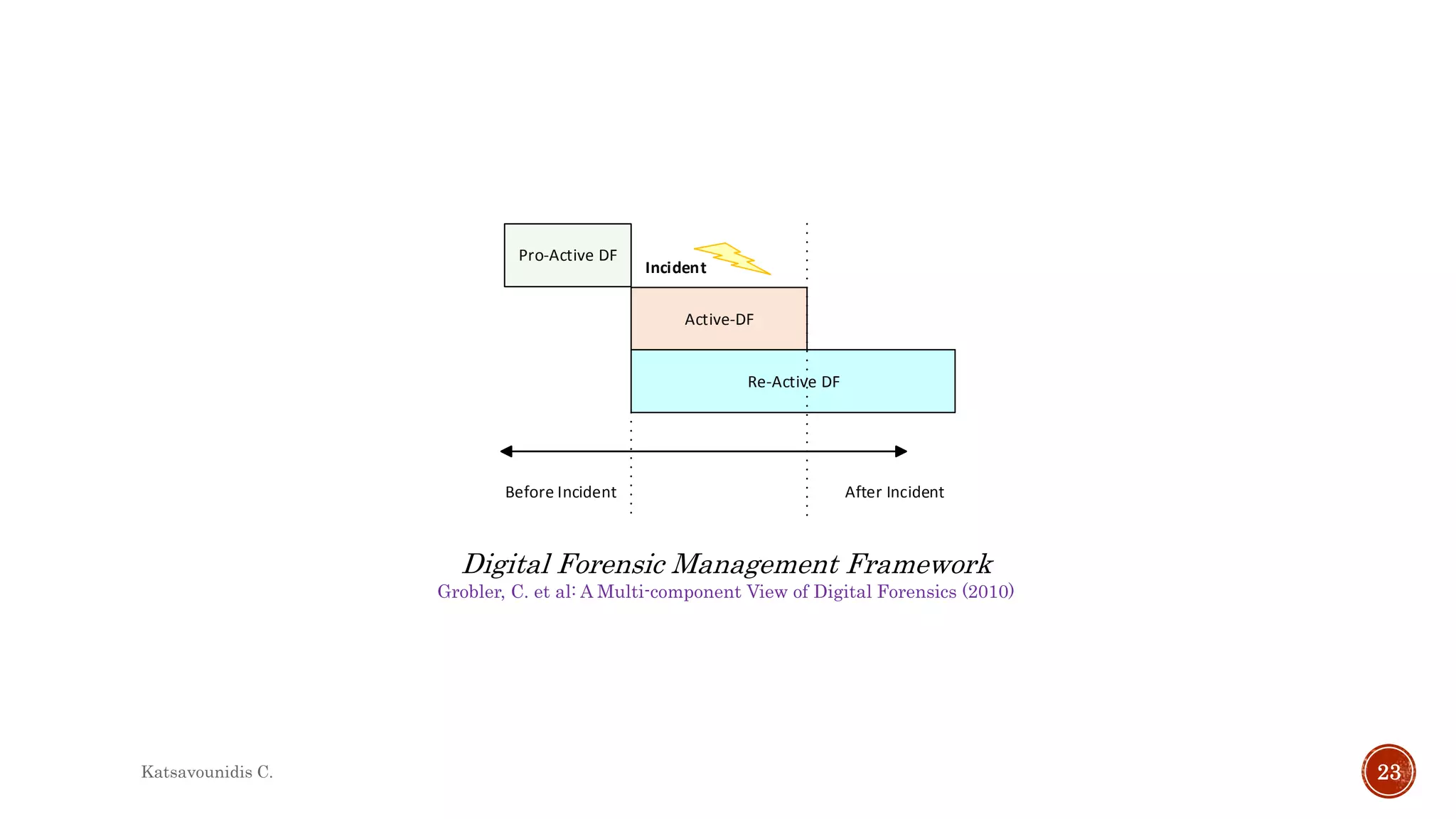
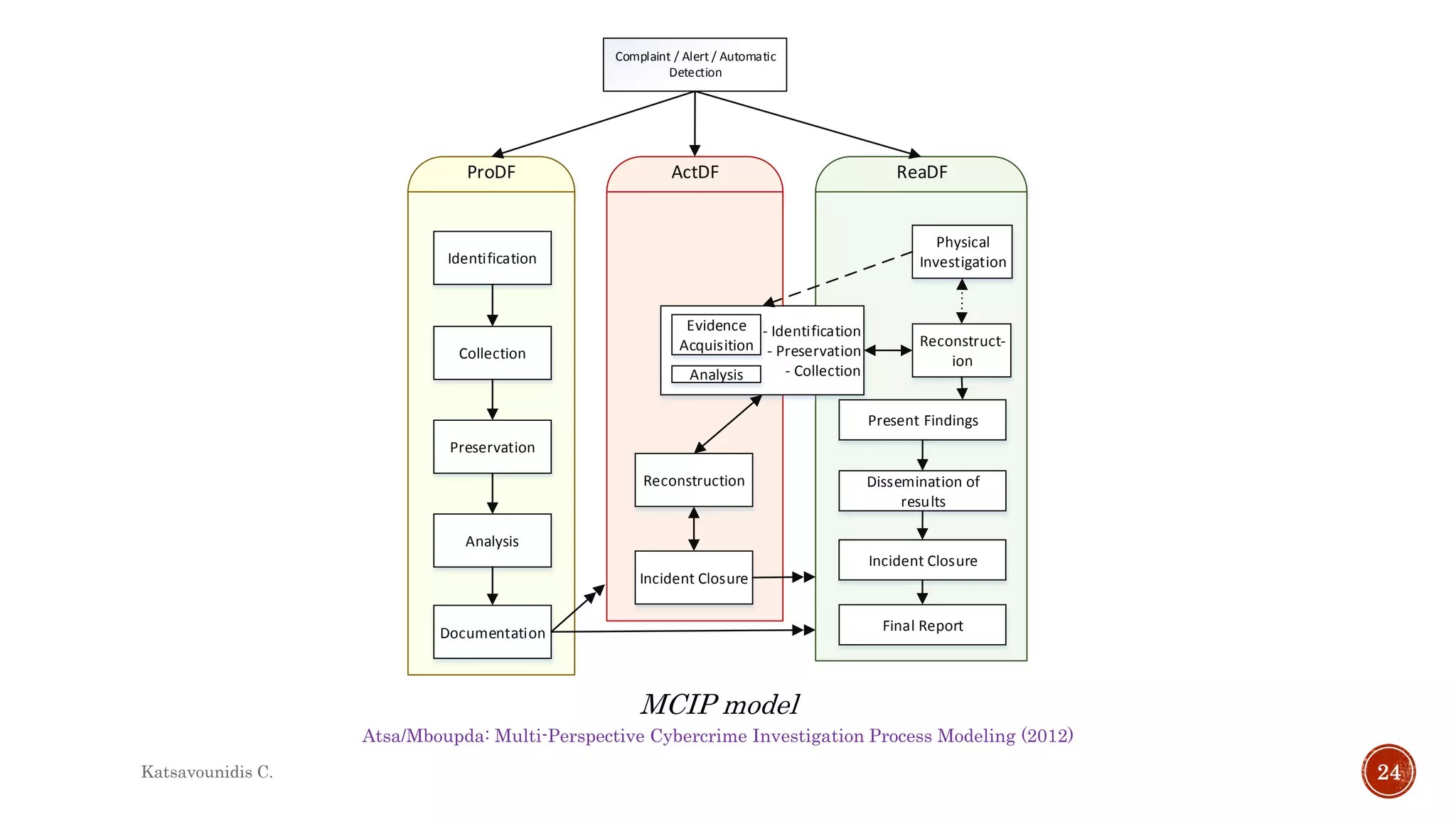
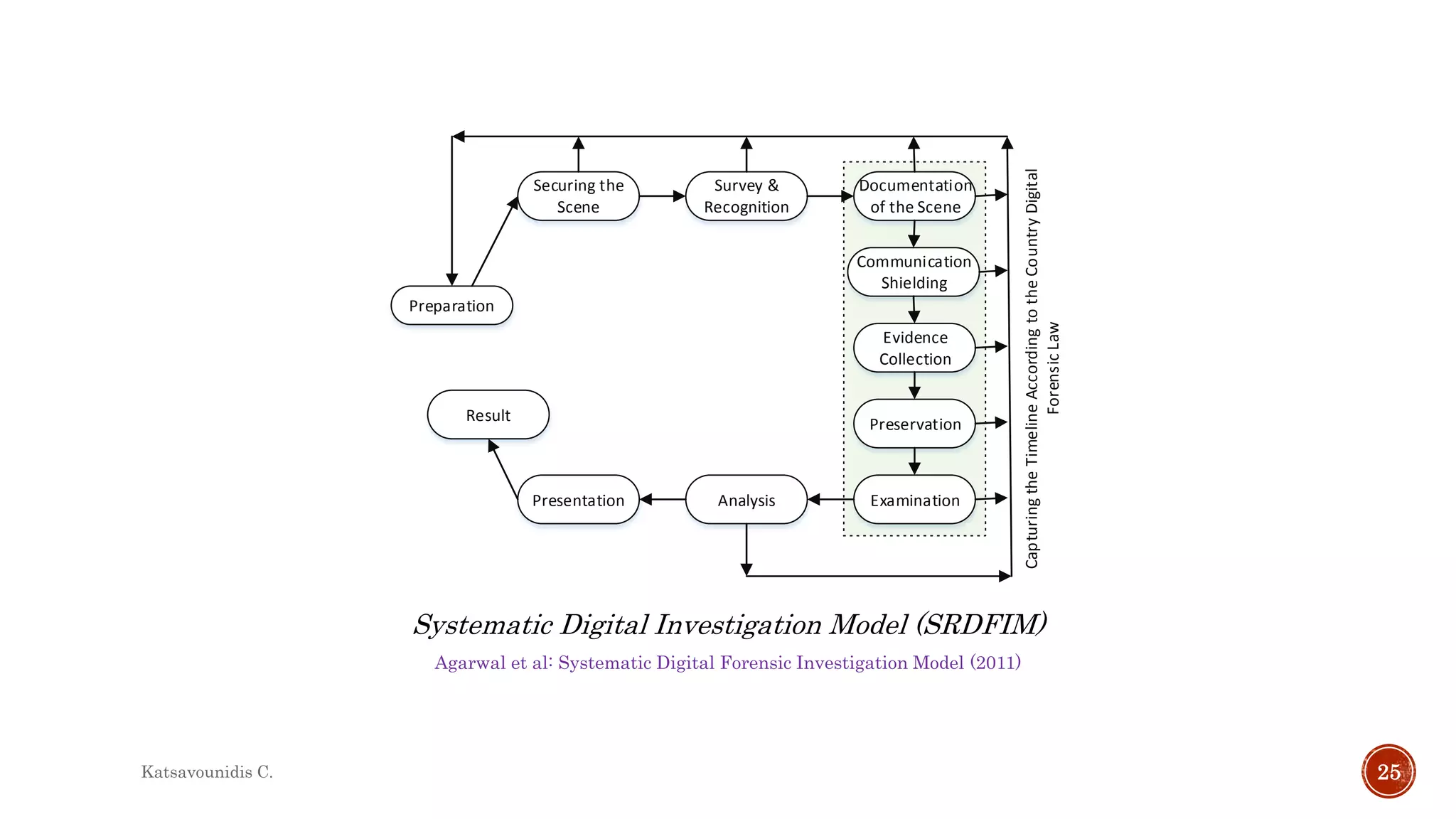
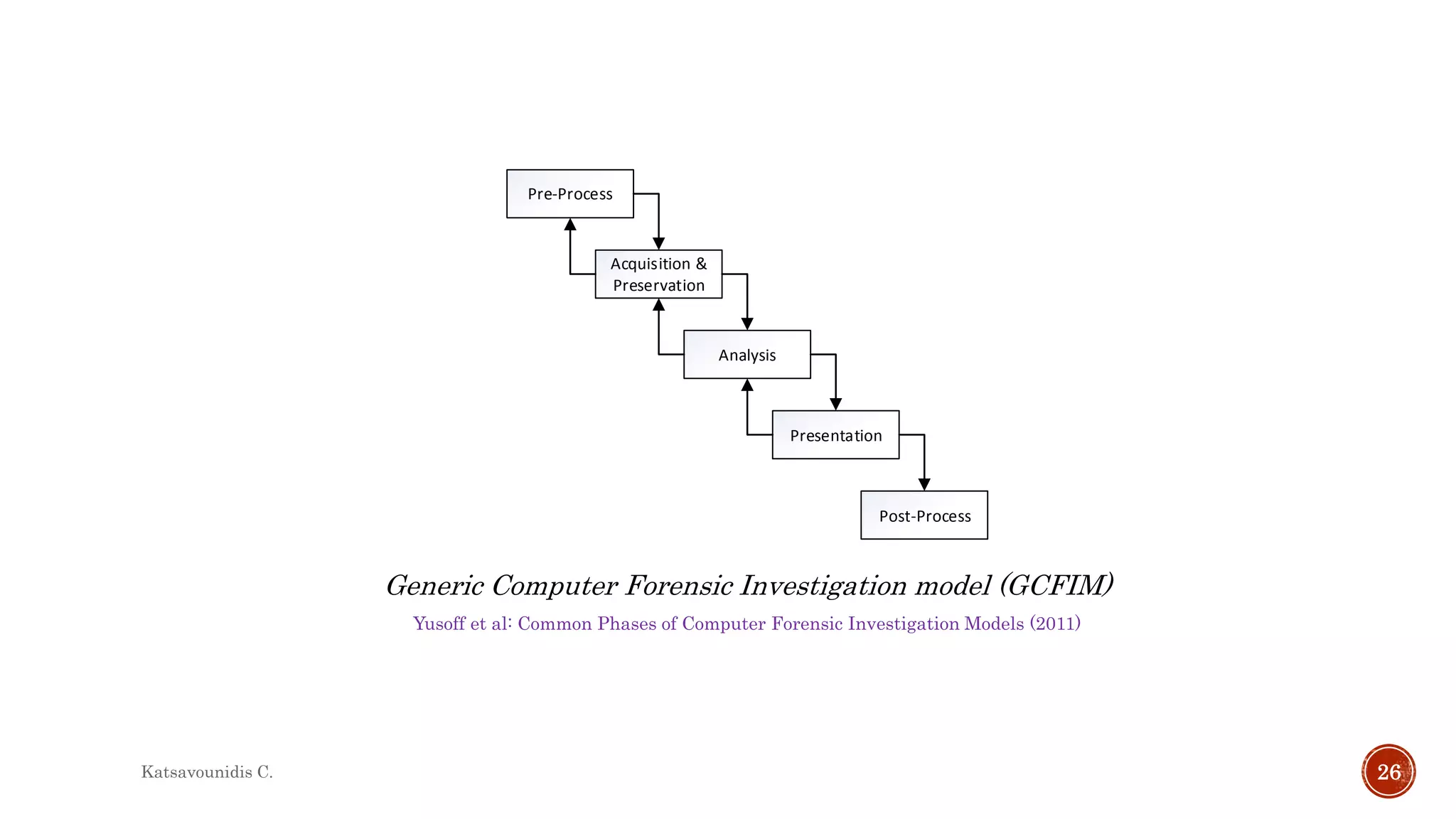
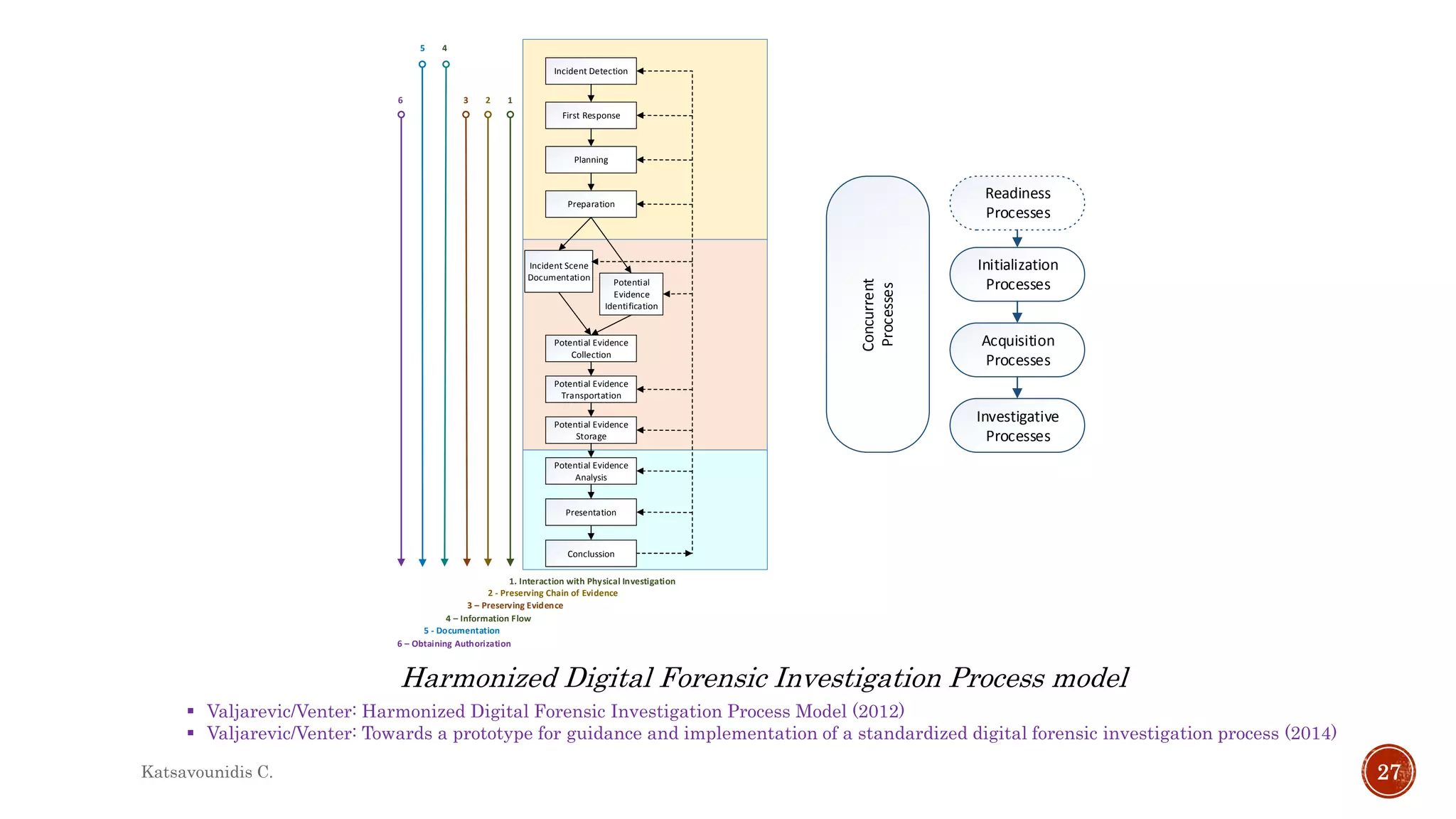
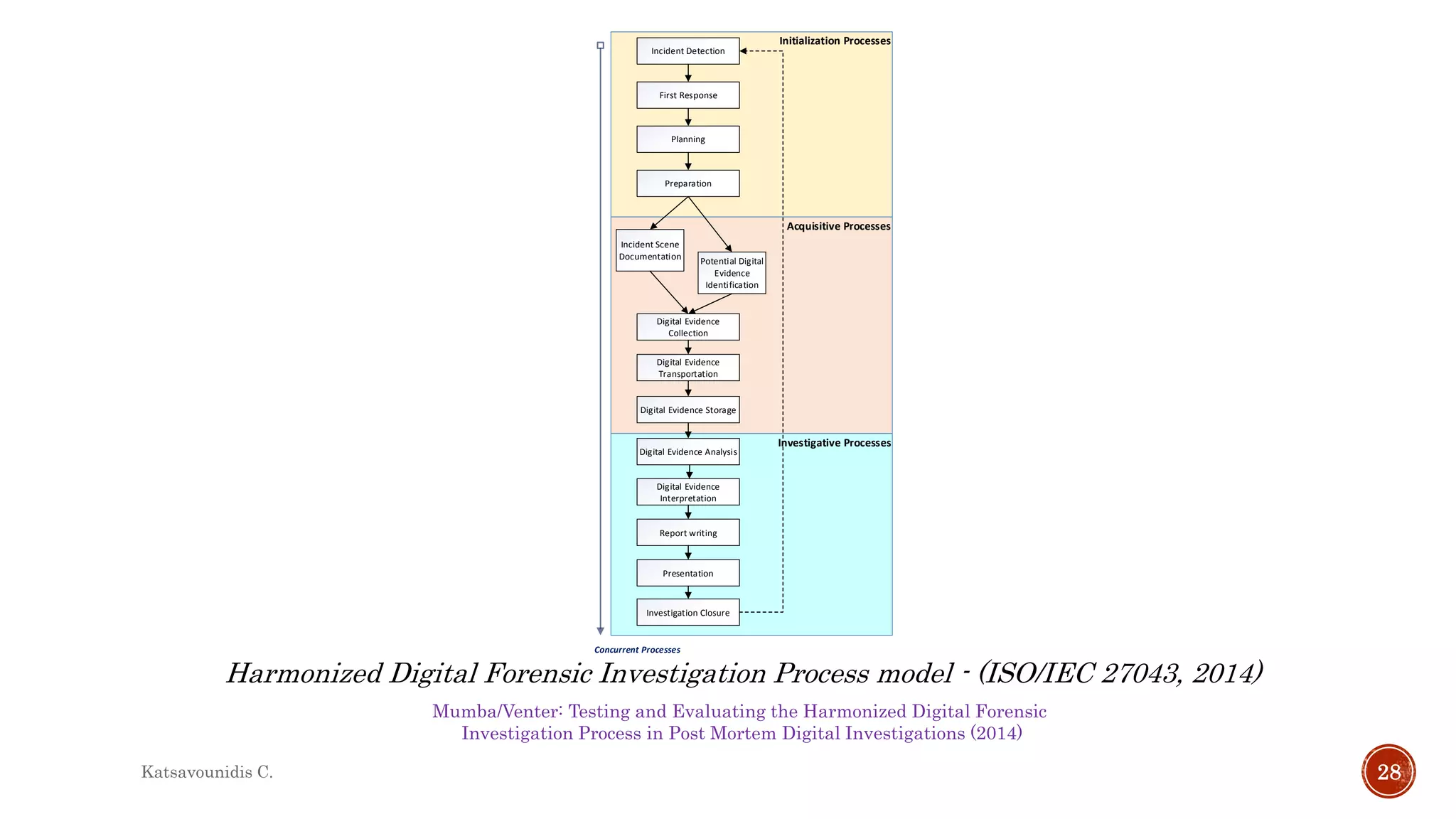
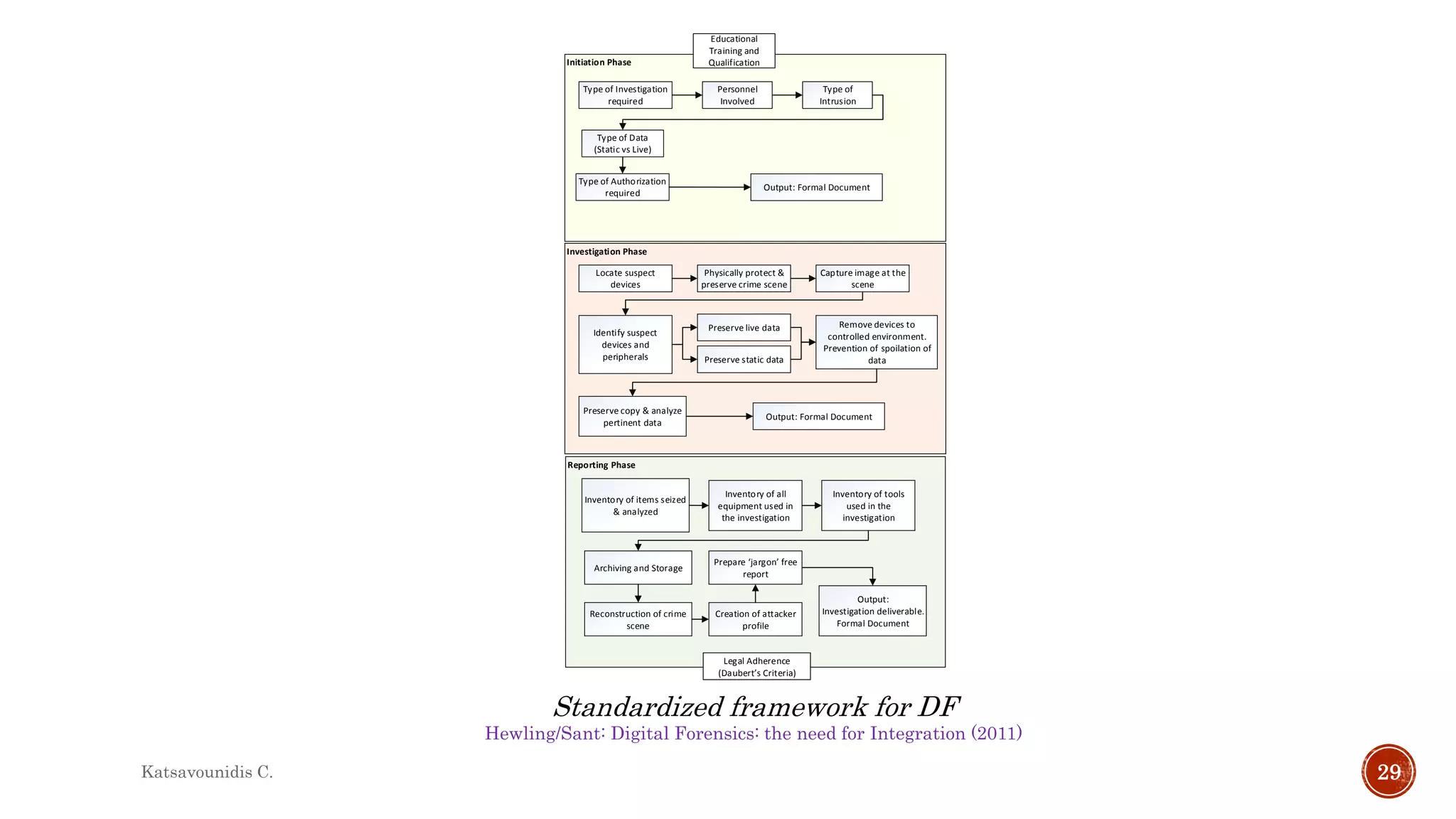
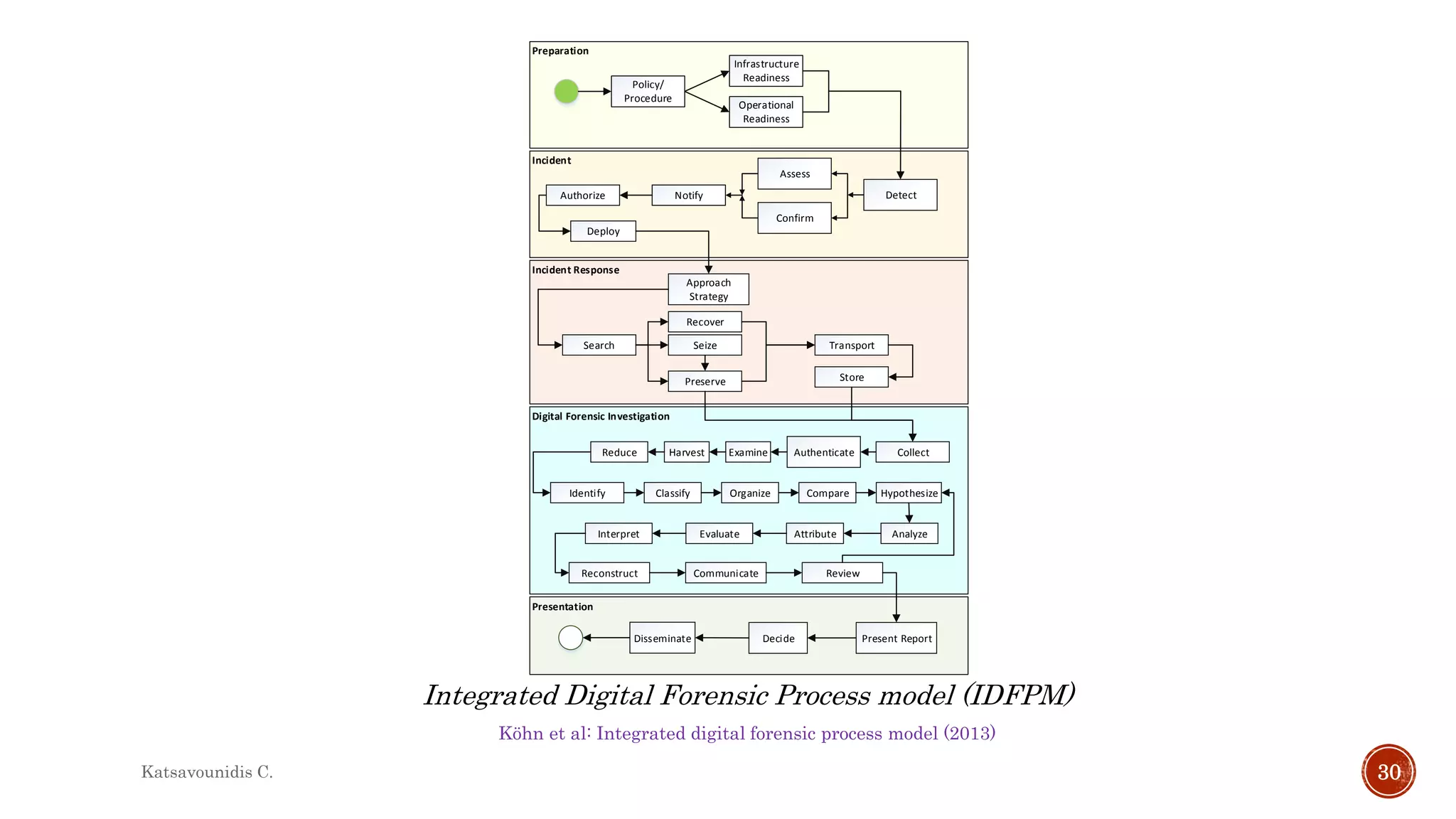
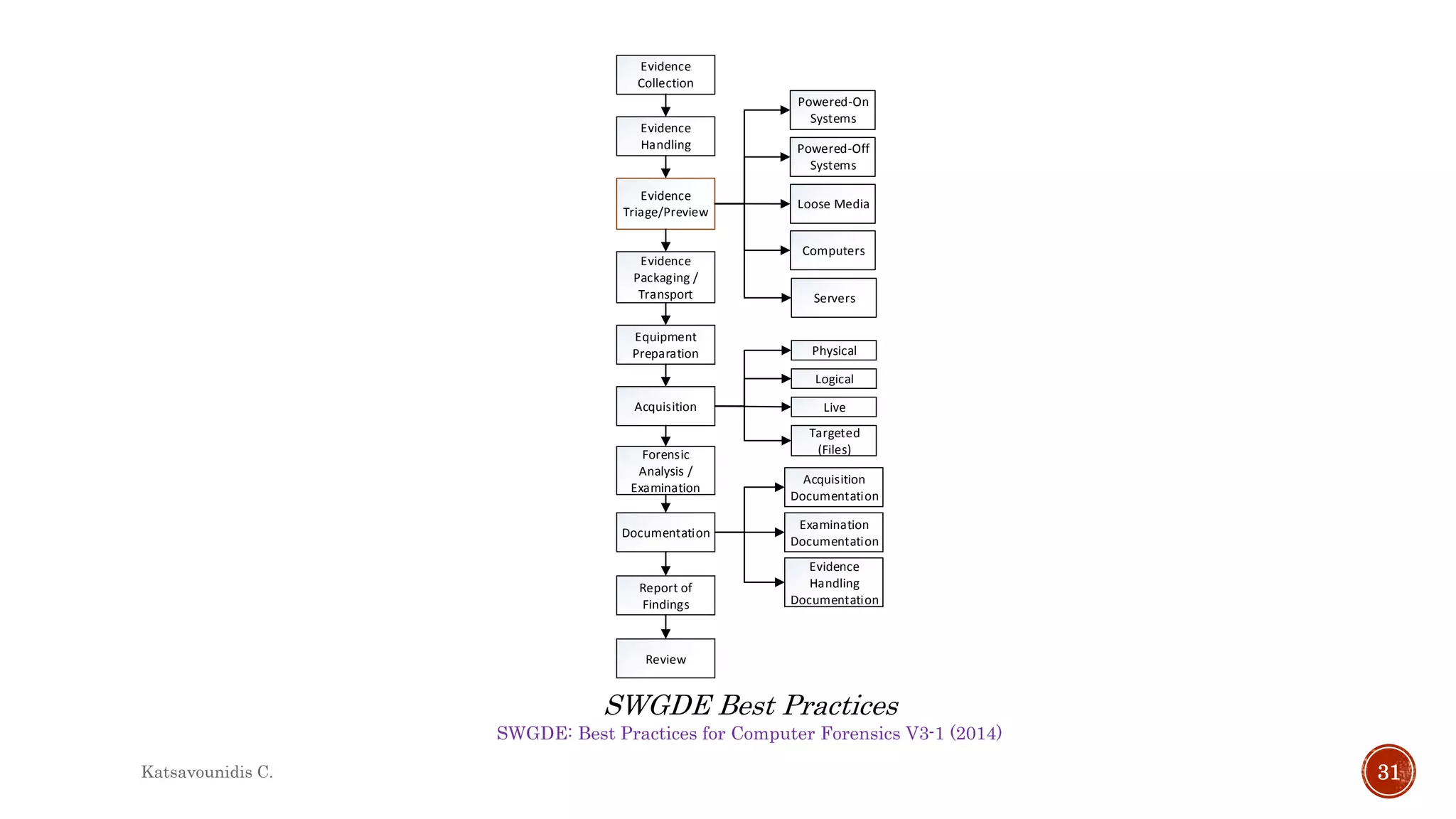
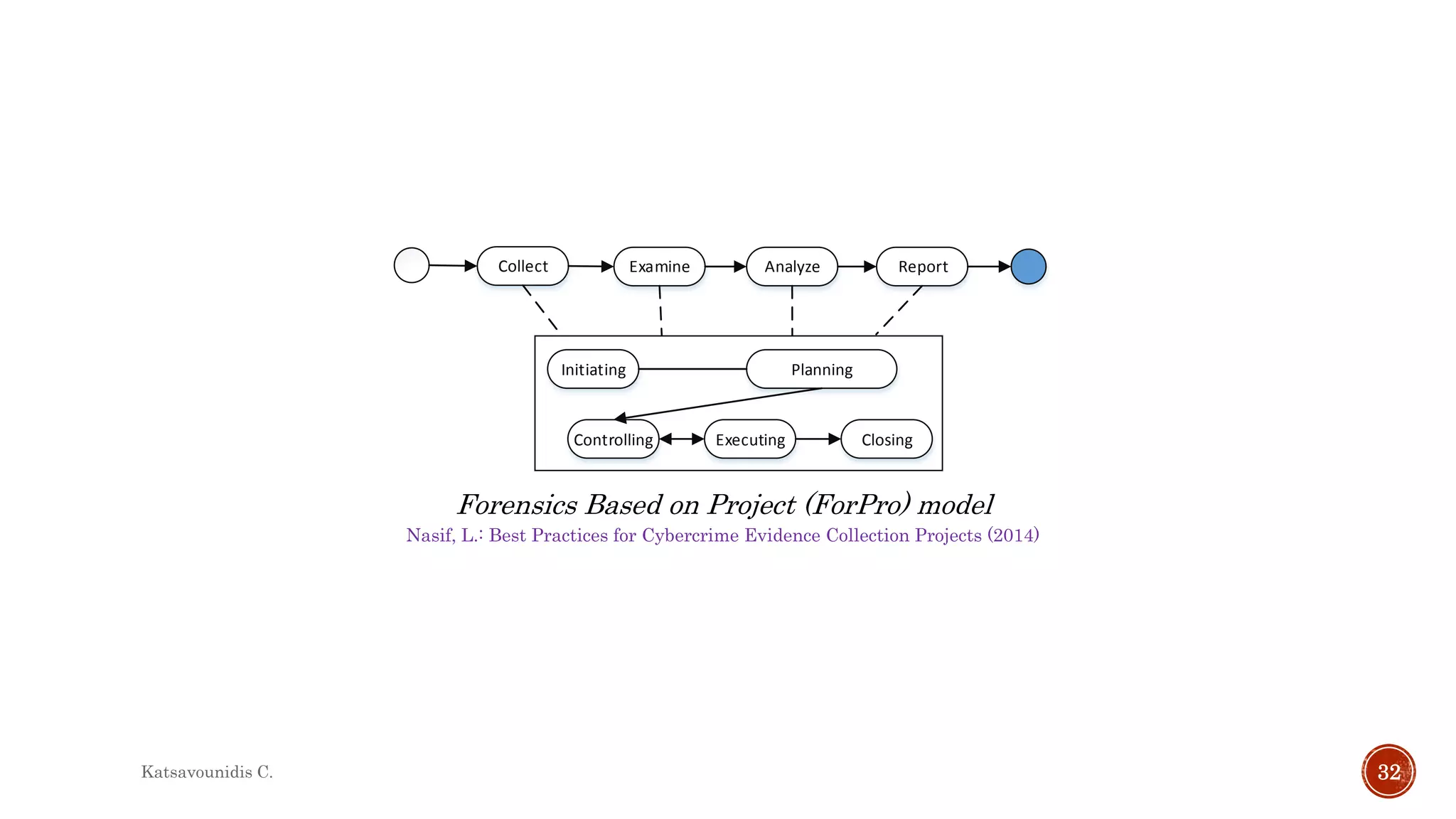
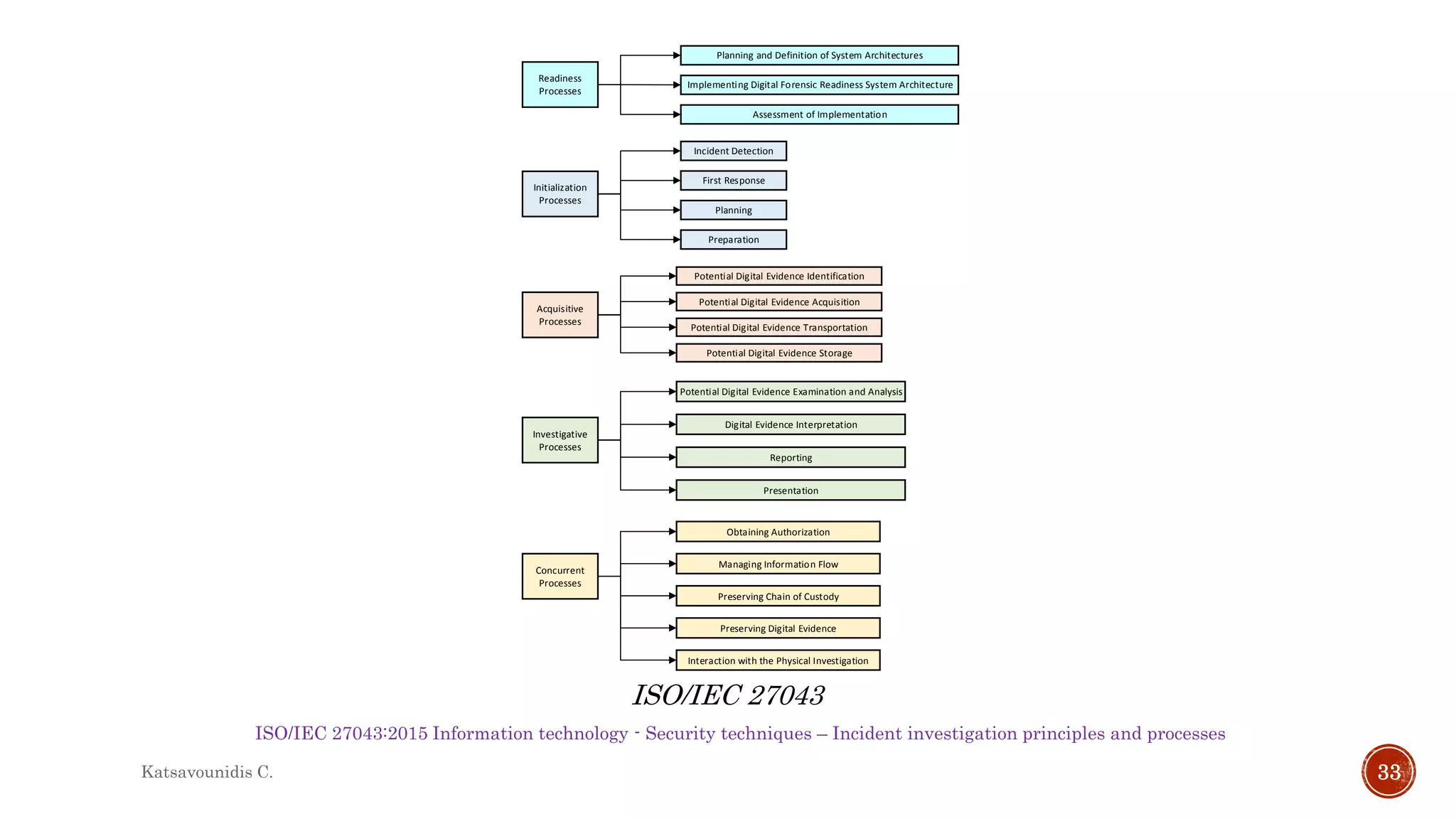
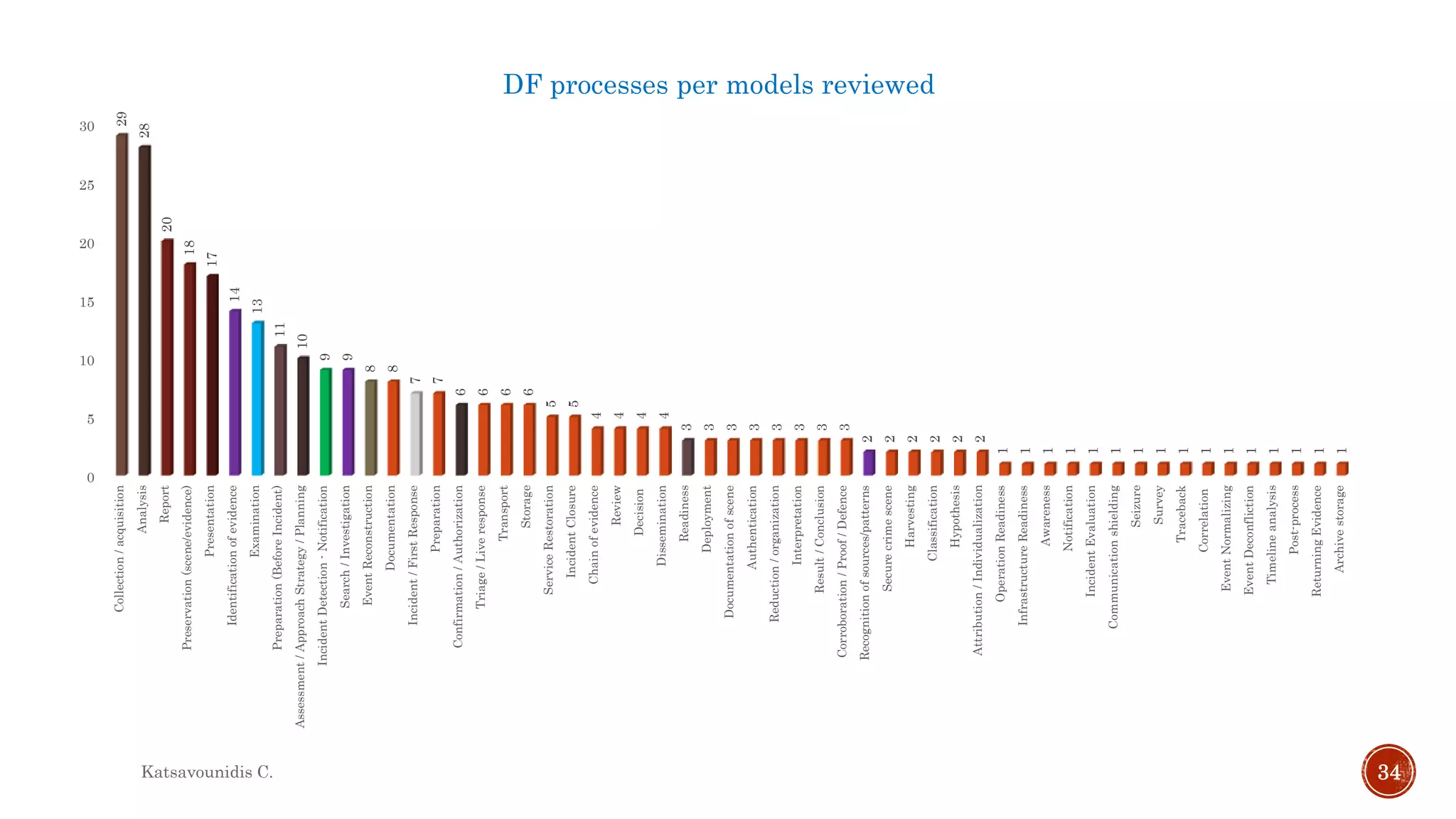
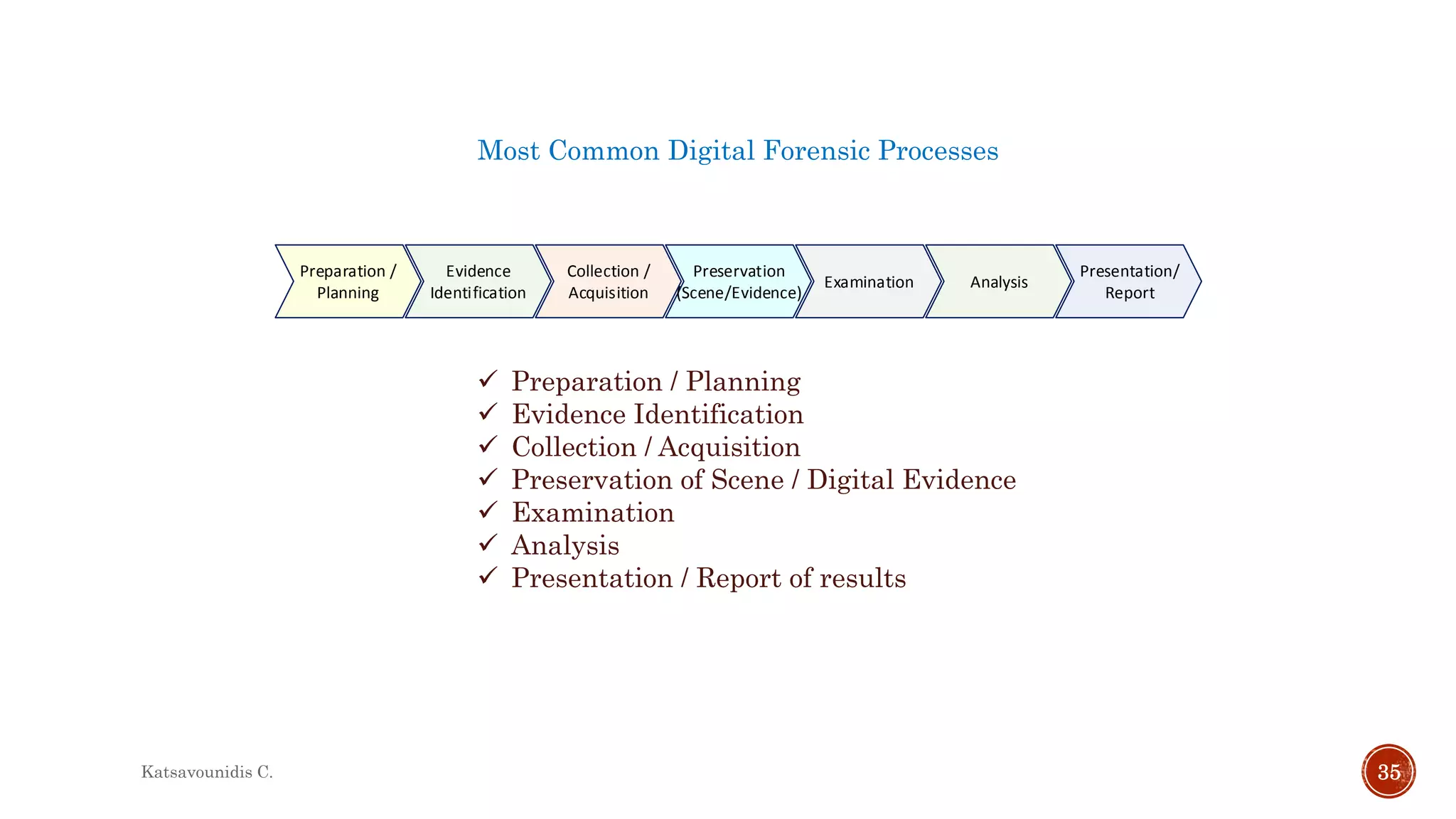
This document summarizes several models and frameworks for digital forensic examination developed between 2000-2015. It provides brief descriptions of key frameworks such as the ACPO principles of 2007, NIJ guidelines of 2008, ENFSI guidelines of 2009 and several process models including the 3A model, IDIP model, InteDFPM model and Palantir framework for collaborative incident response. The document is intended to provide an overview of the evolution of digital forensic examination processes and standards over this 15 year period.