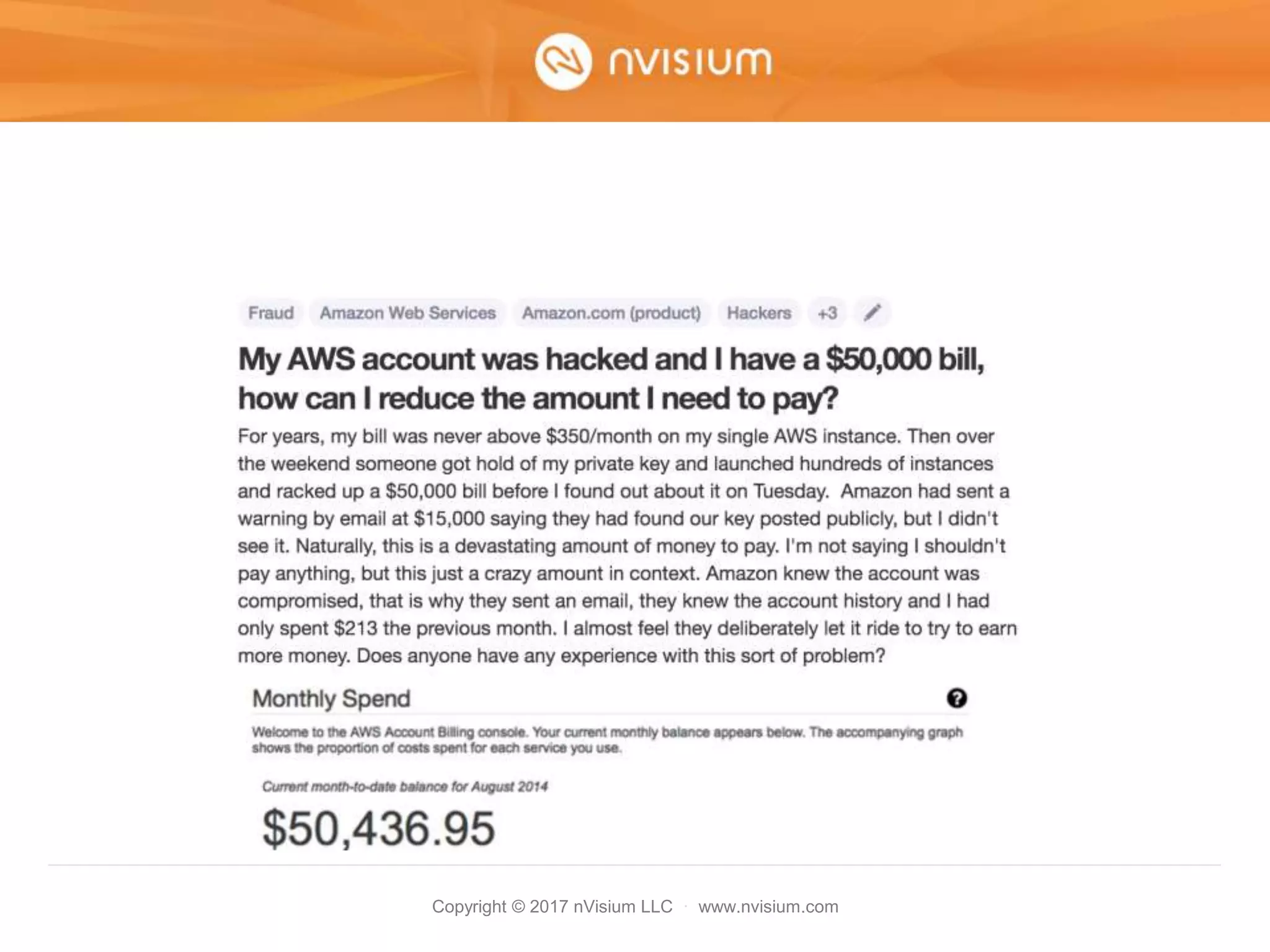
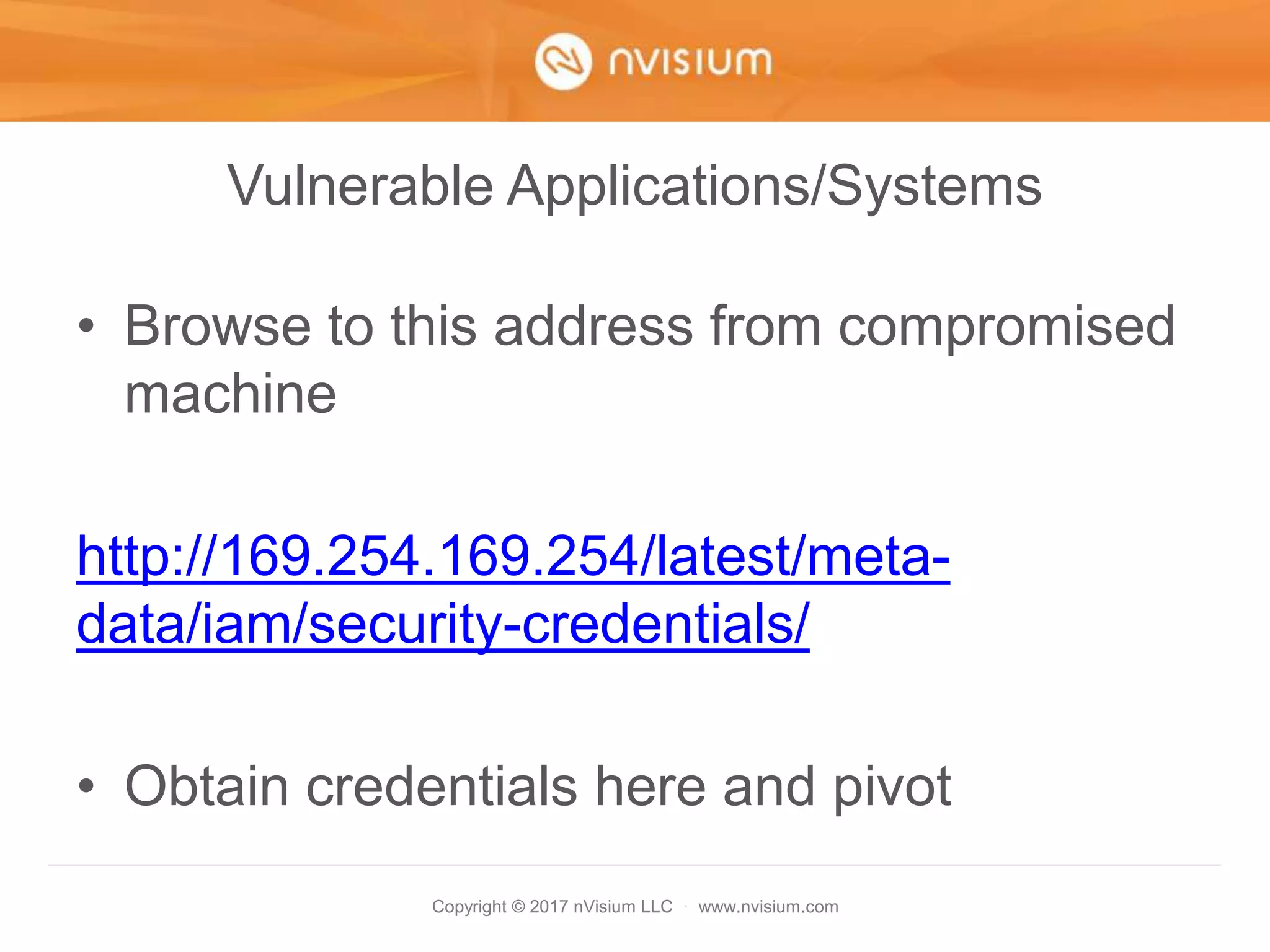
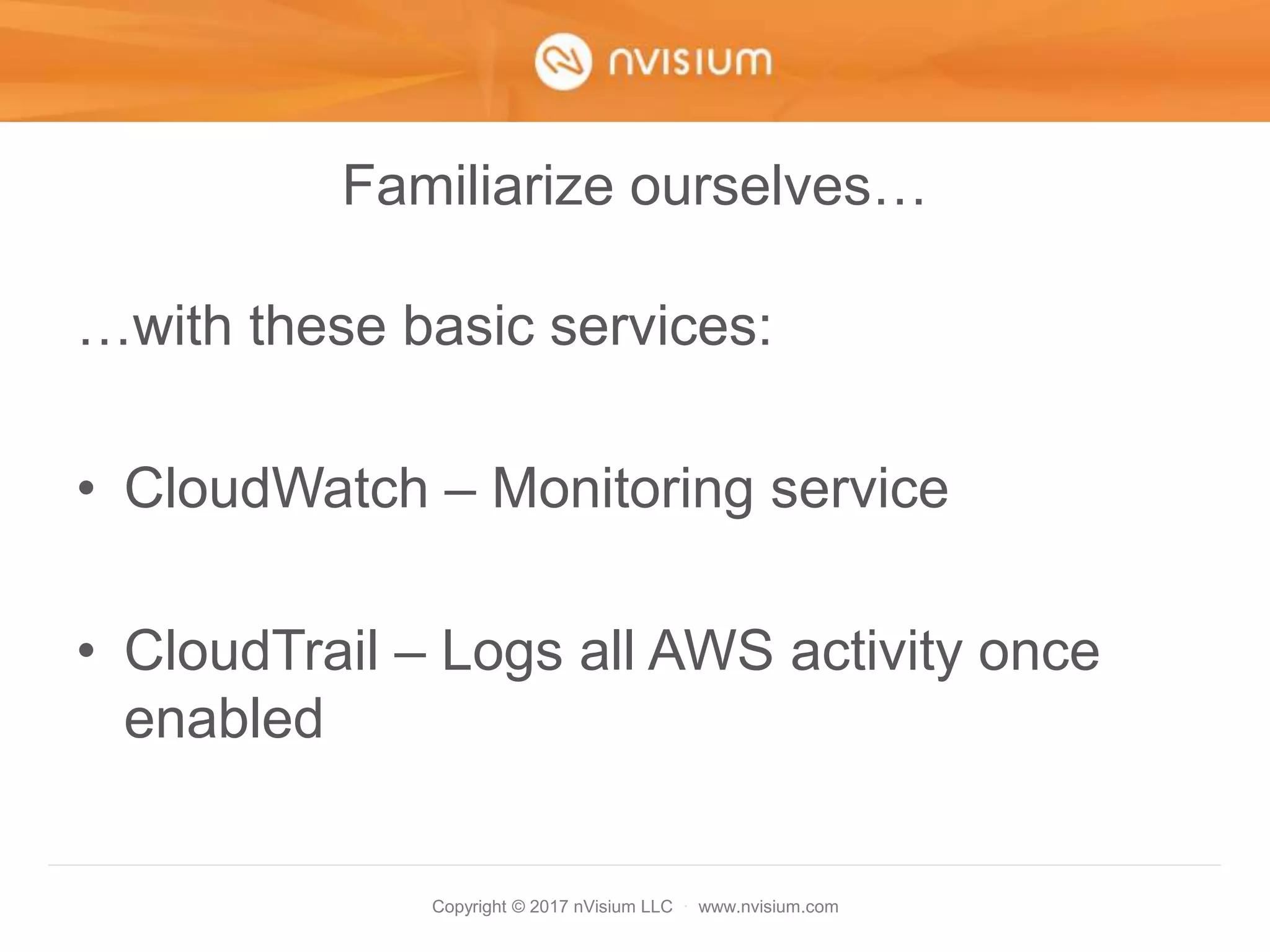
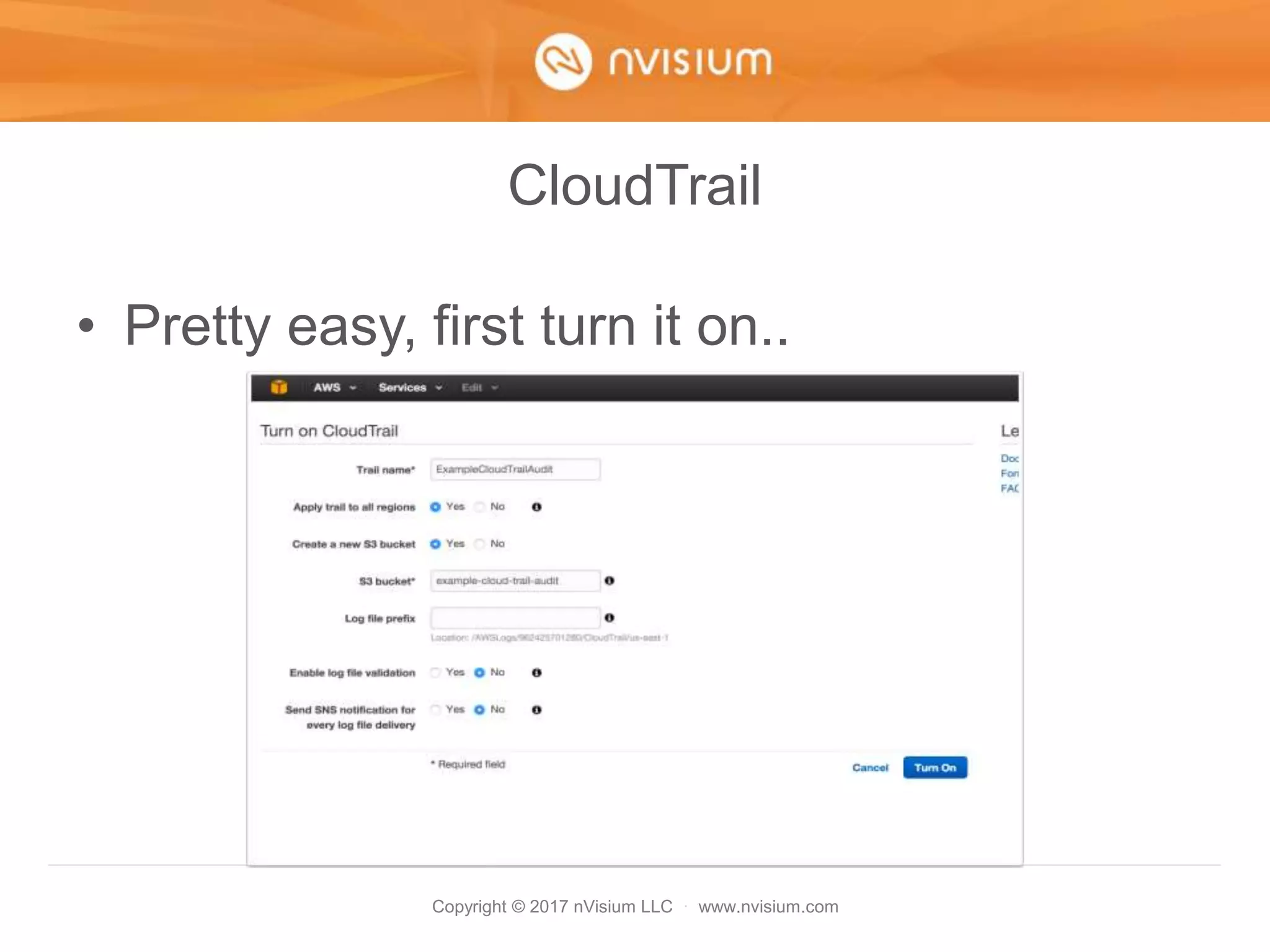
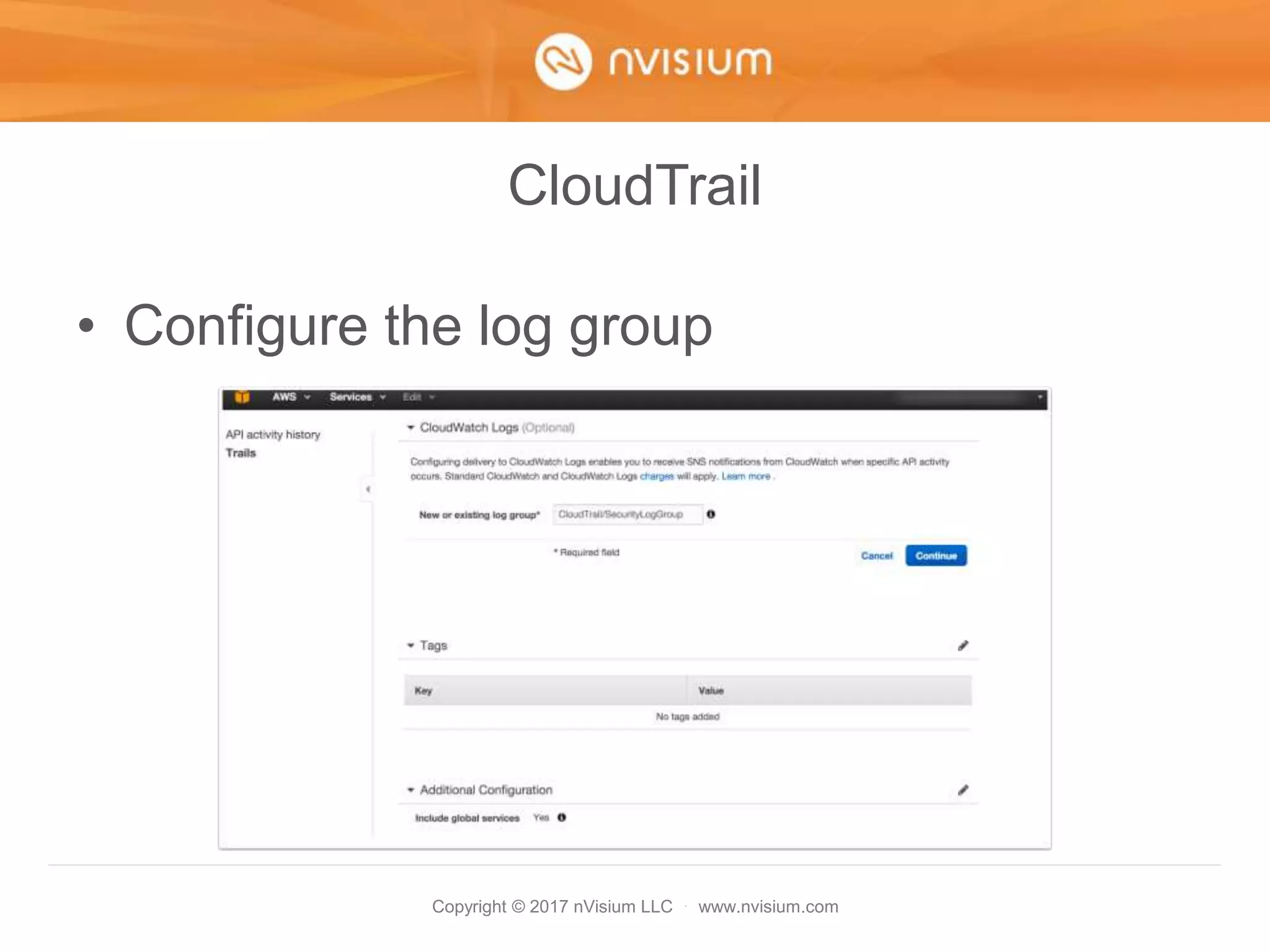
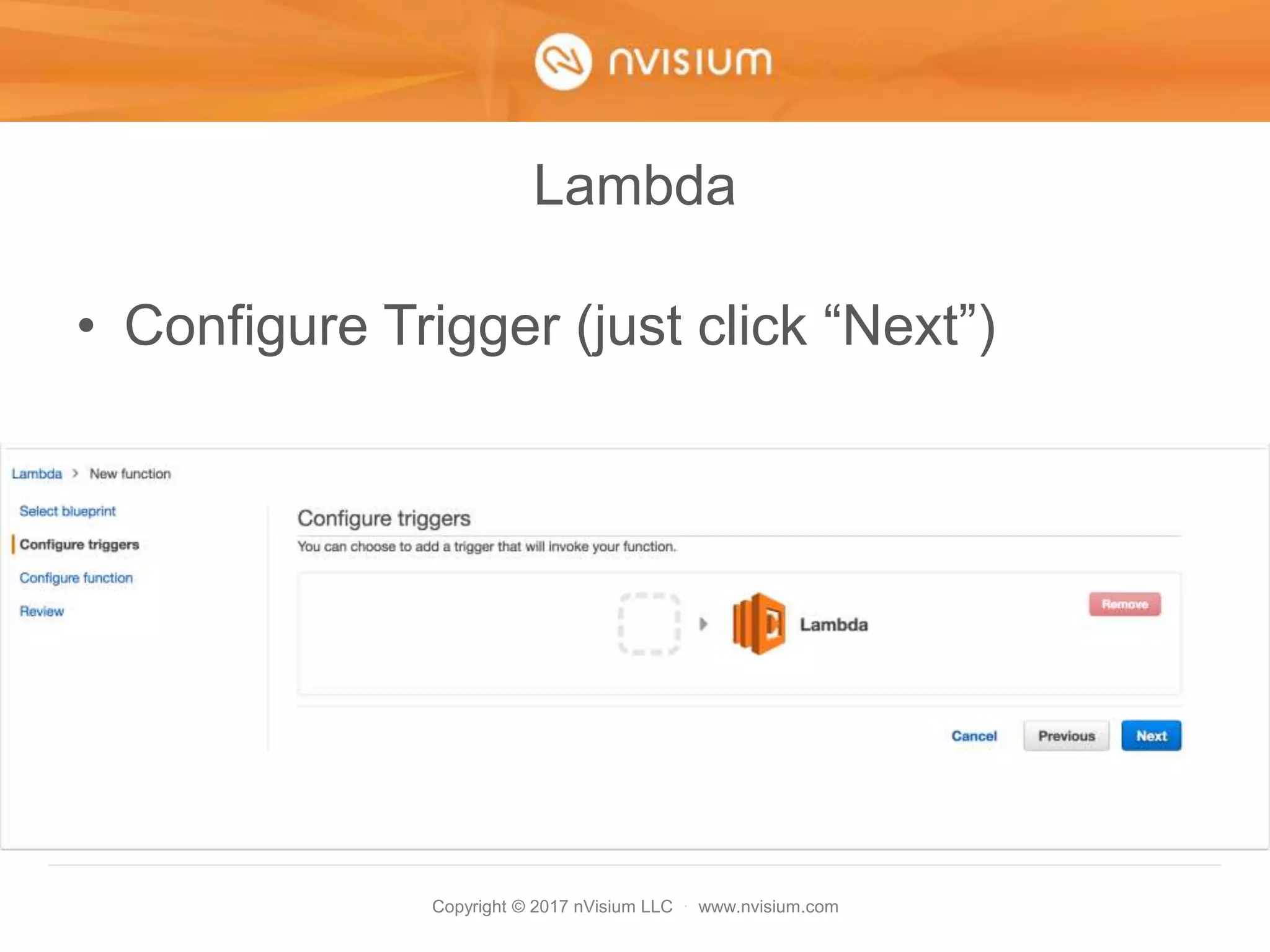
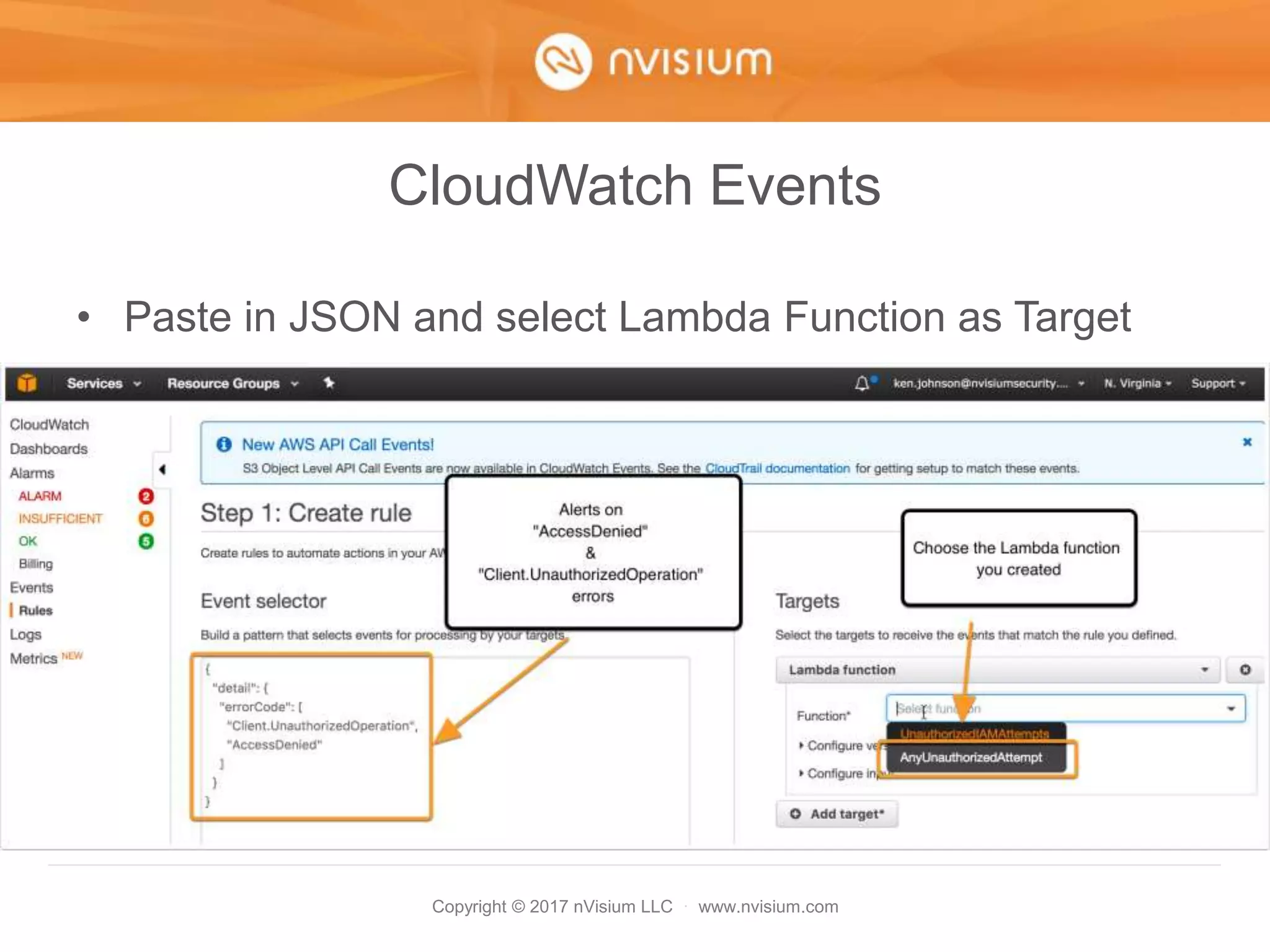
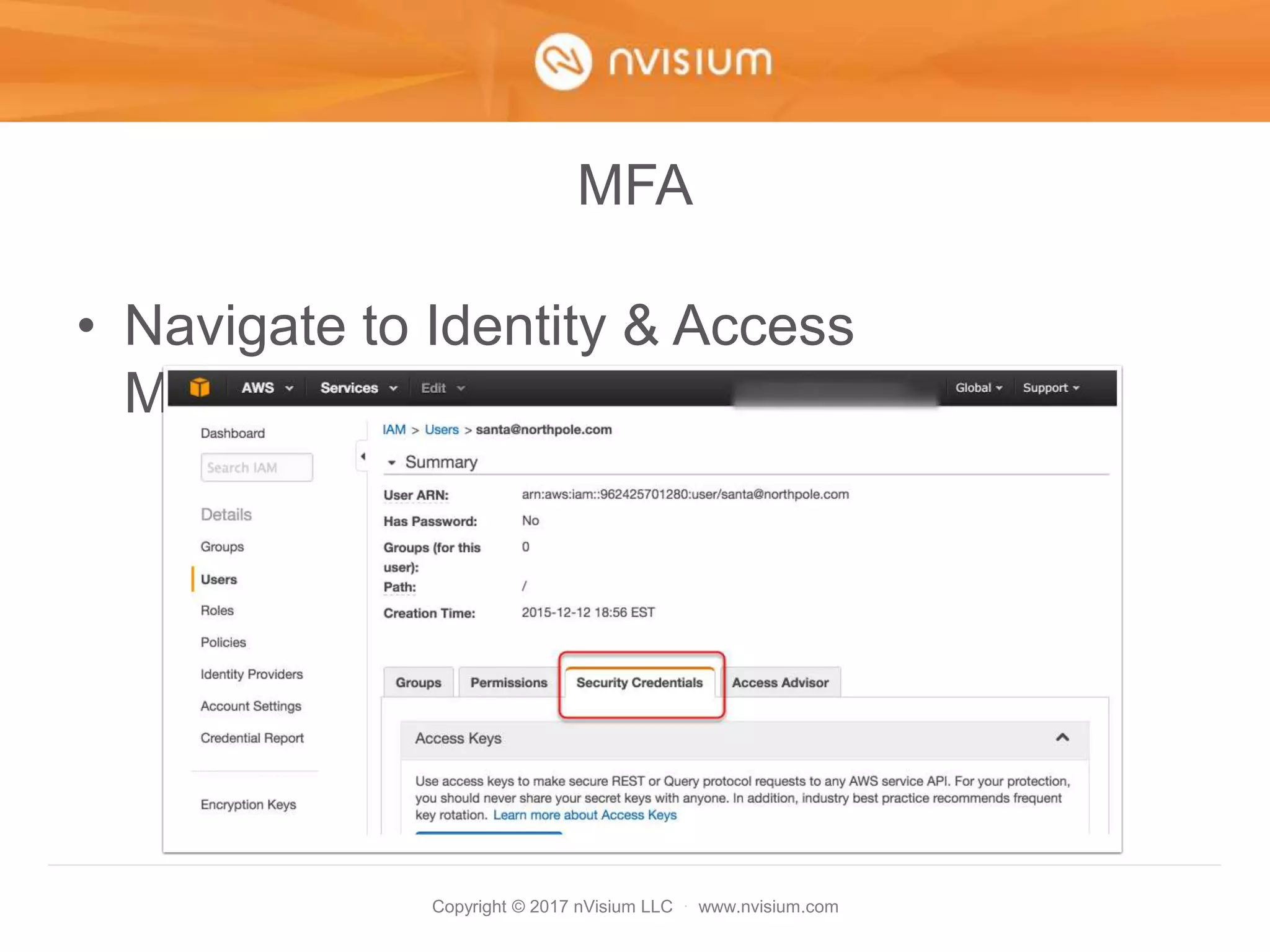
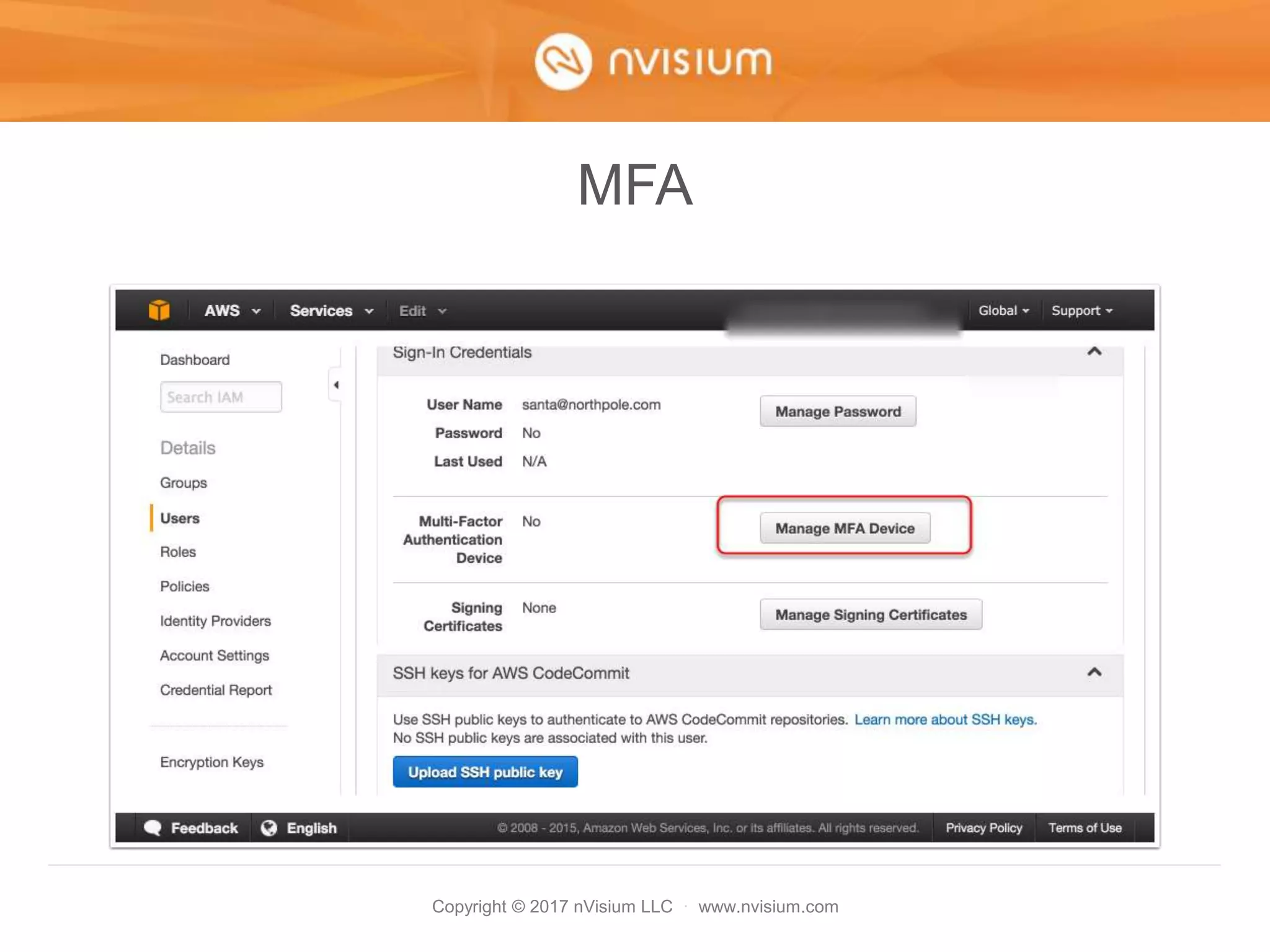
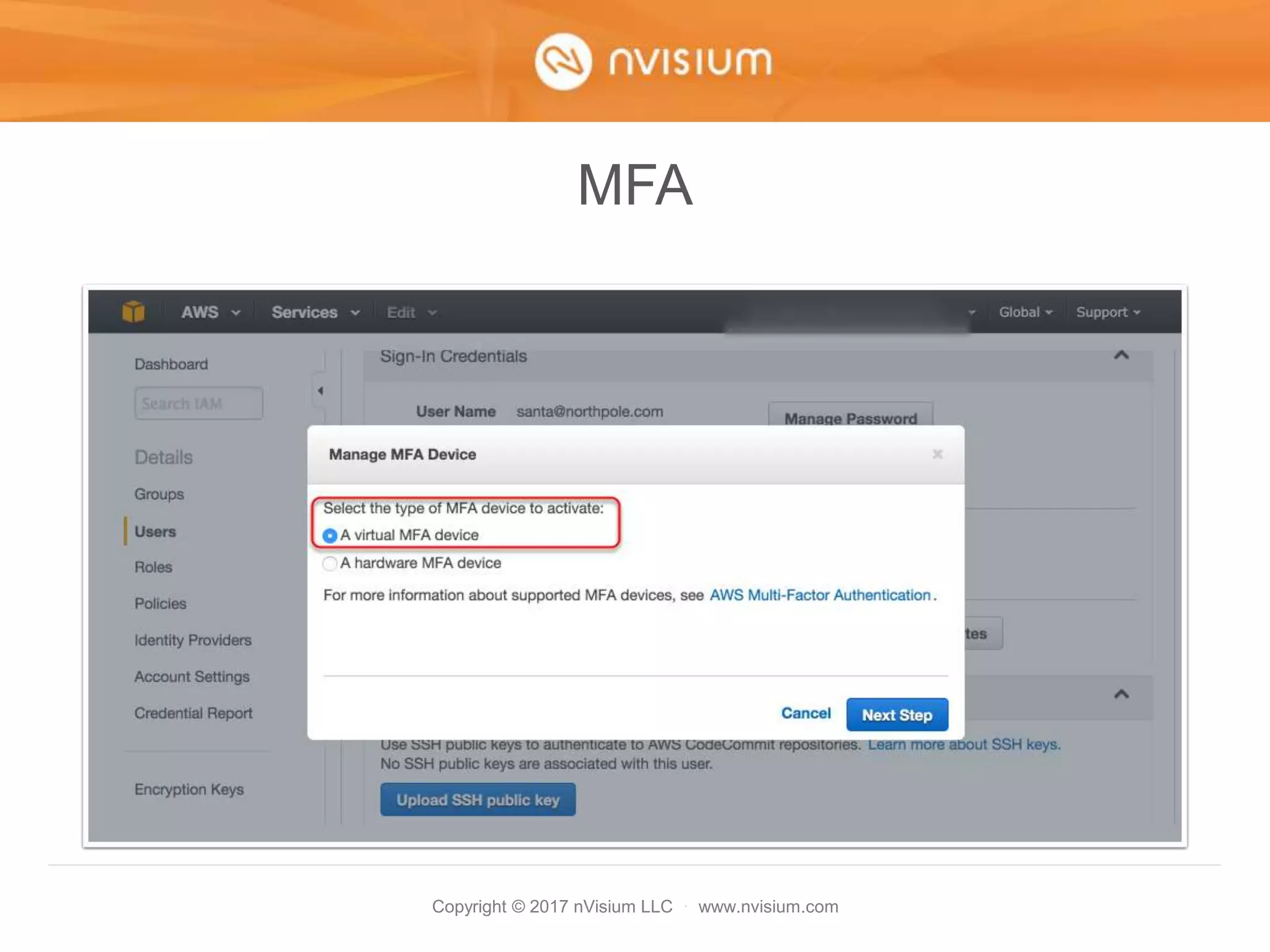
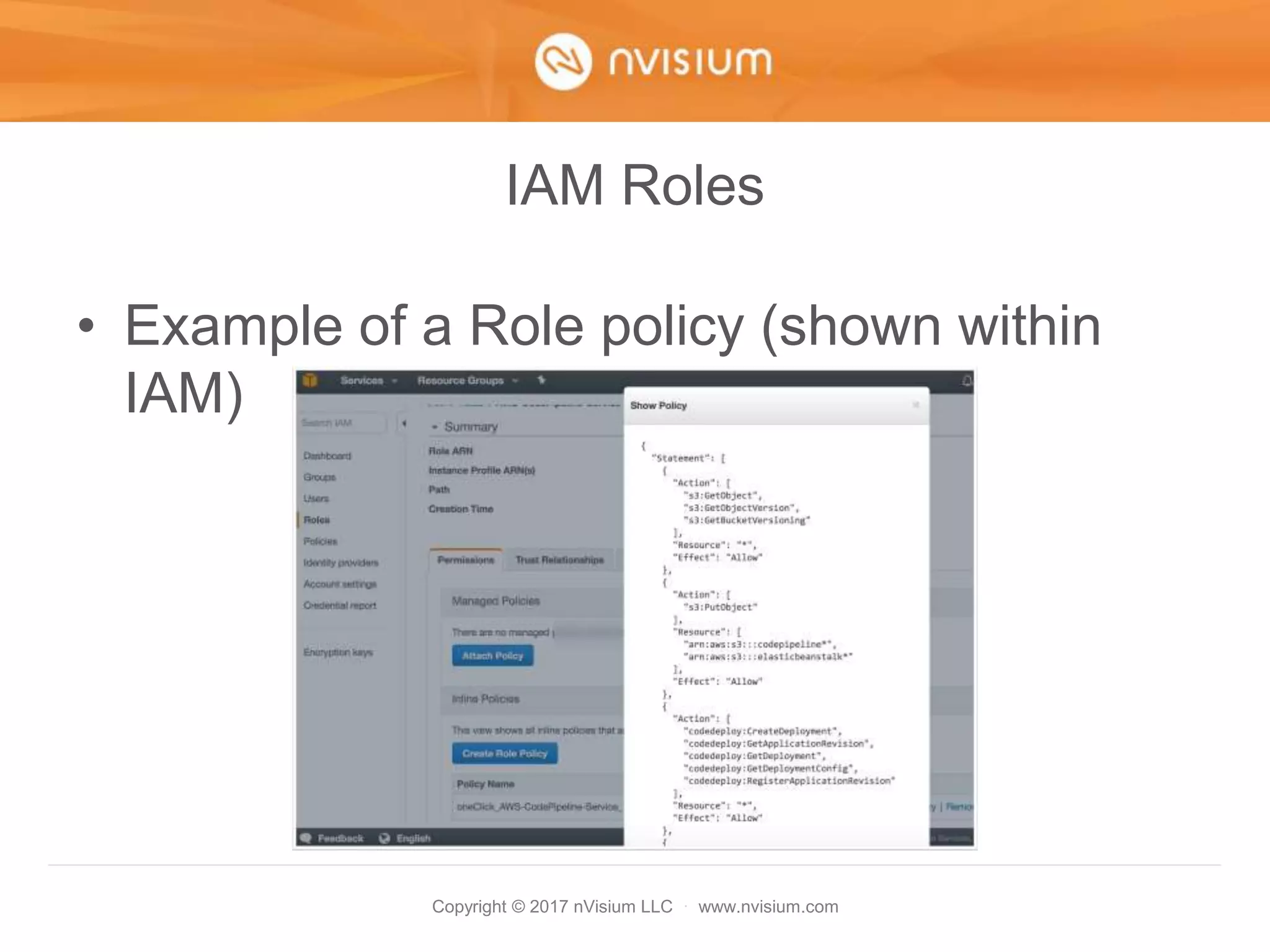
This document is a presentation on AWS security best practices given by the CTO of a security company. It covers monitoring AWS resources using CloudWatch alarms and events to detect unauthorized access. It then discusses hardening AWS security by not using root credentials, auditing IAM policies, enabling multi-factor authentication, using IAM roles, and other techniques. The presentation provides examples of setting up CloudWatch alarms and events to send unauthorized access alerts to Slack. It also demonstrates enabling MFA on IAM user accounts. The goal is to help users learn how to monitor and secure their AWS infrastructure.