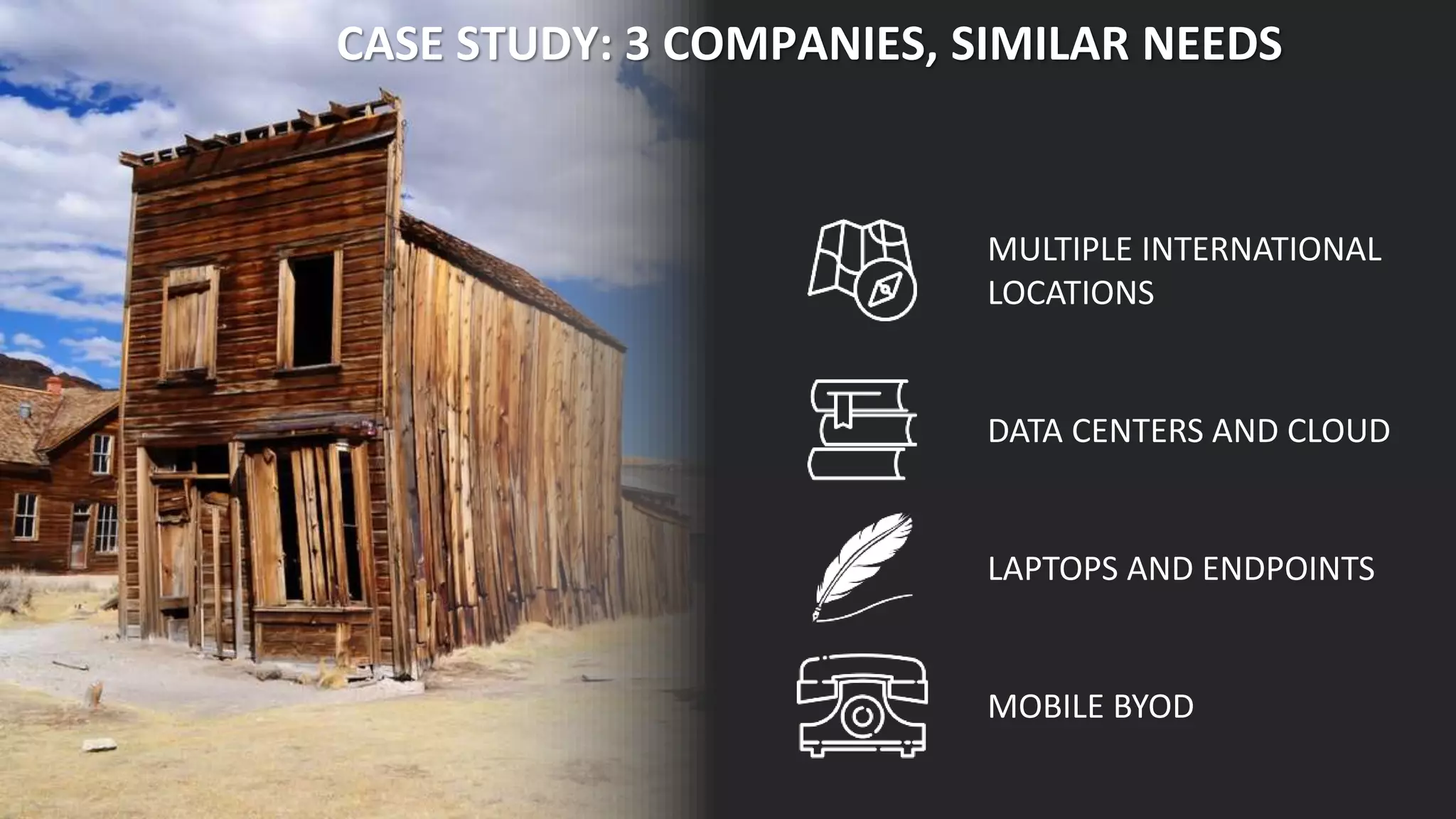
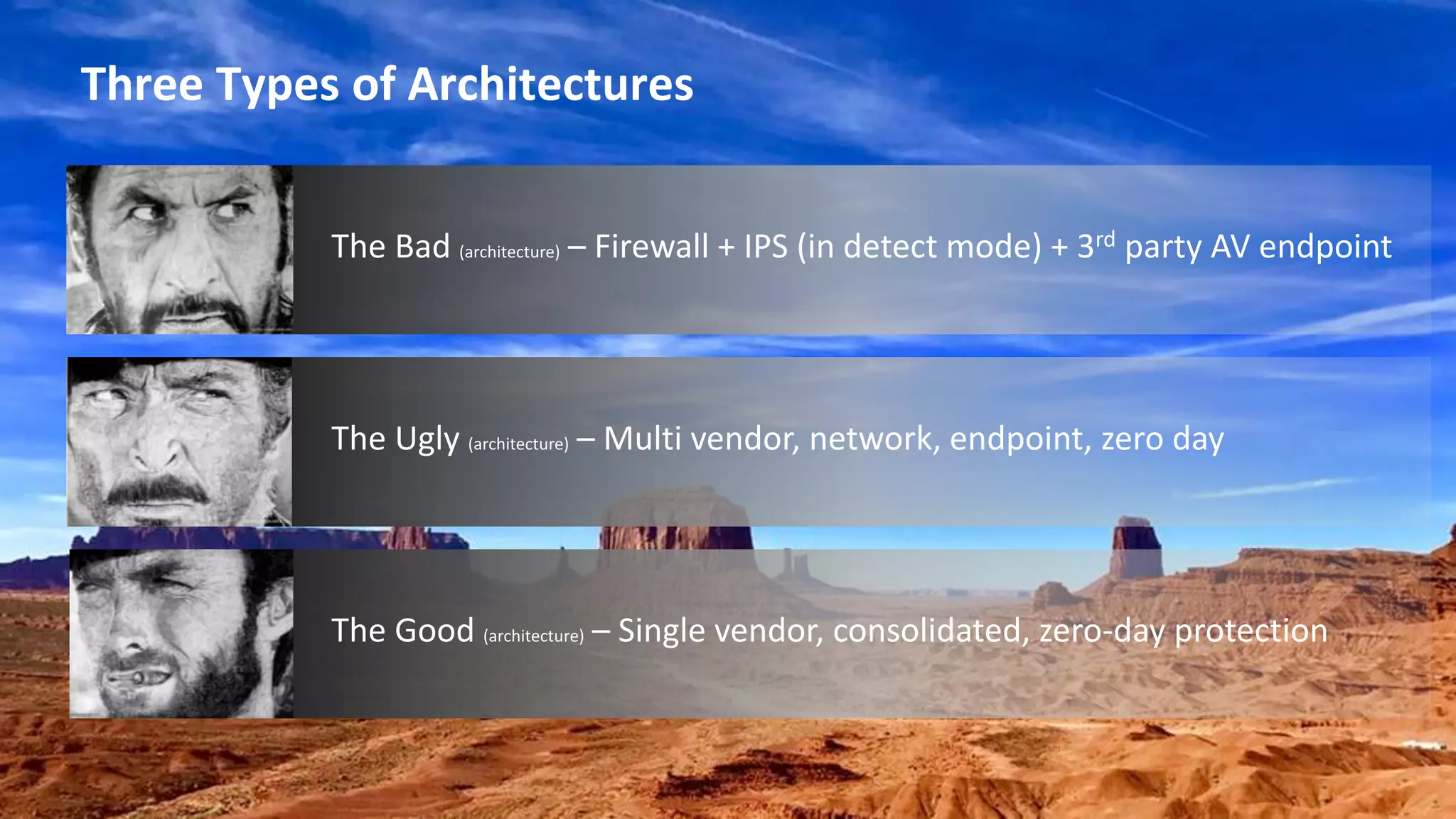
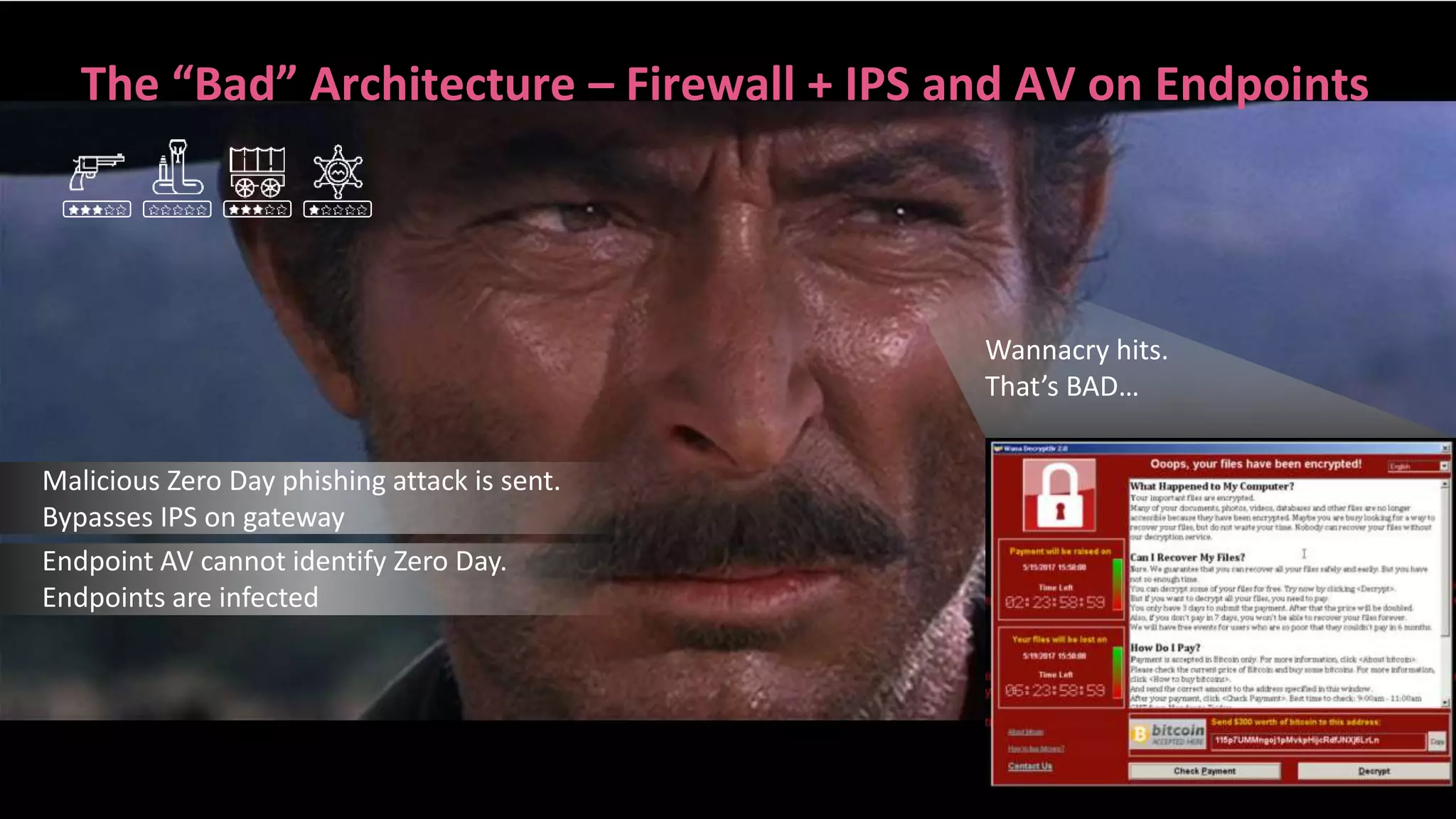
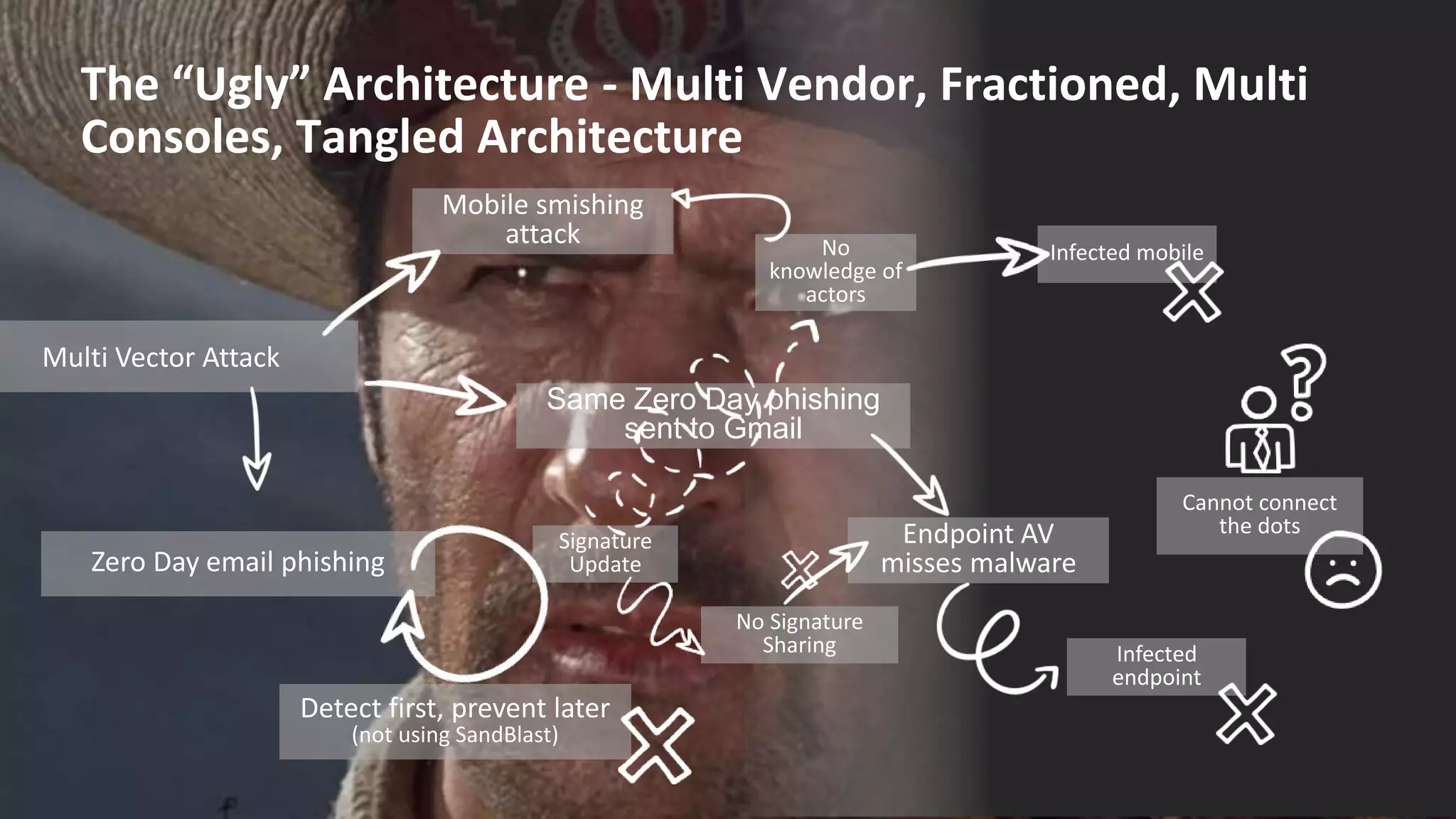
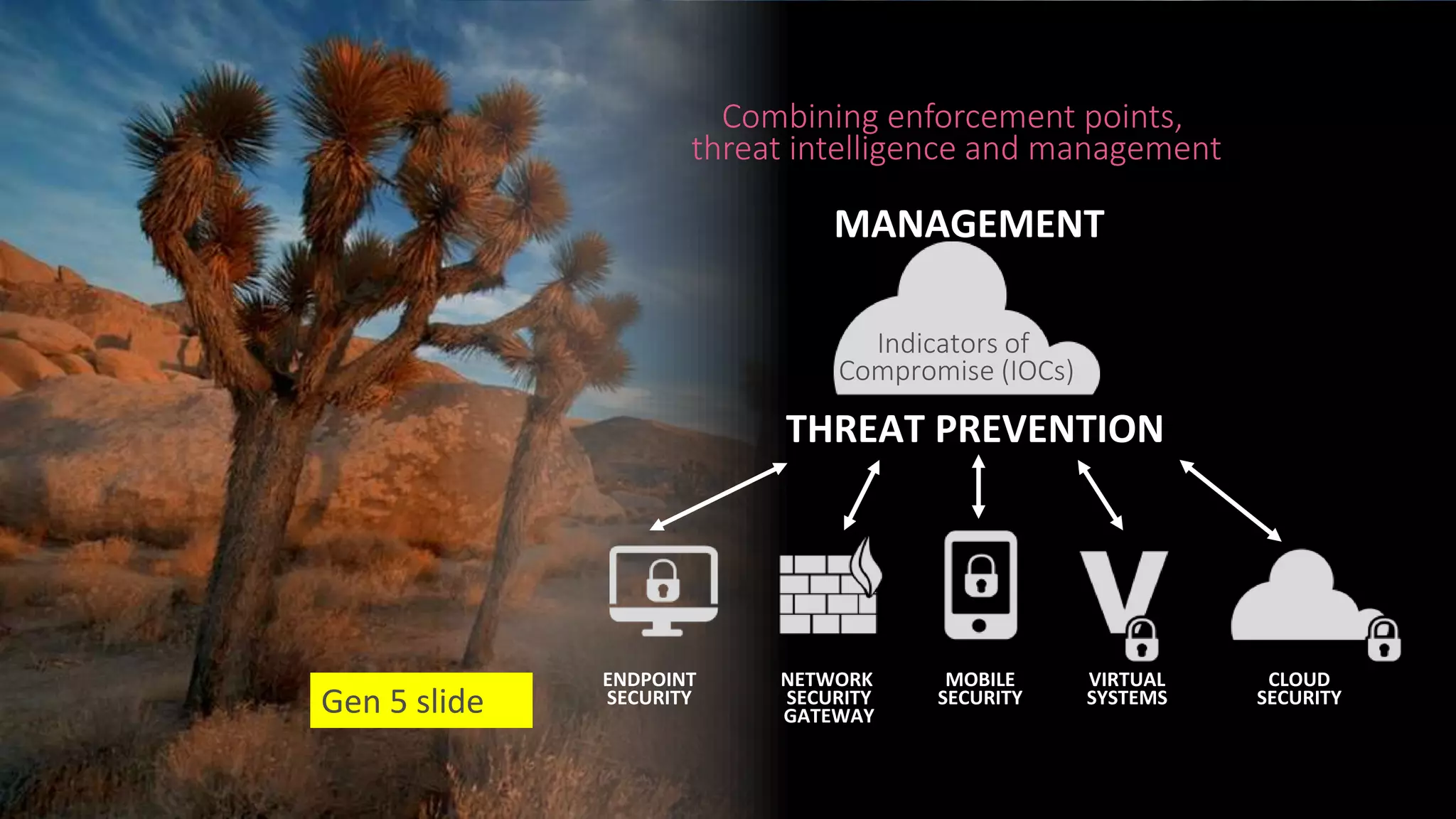
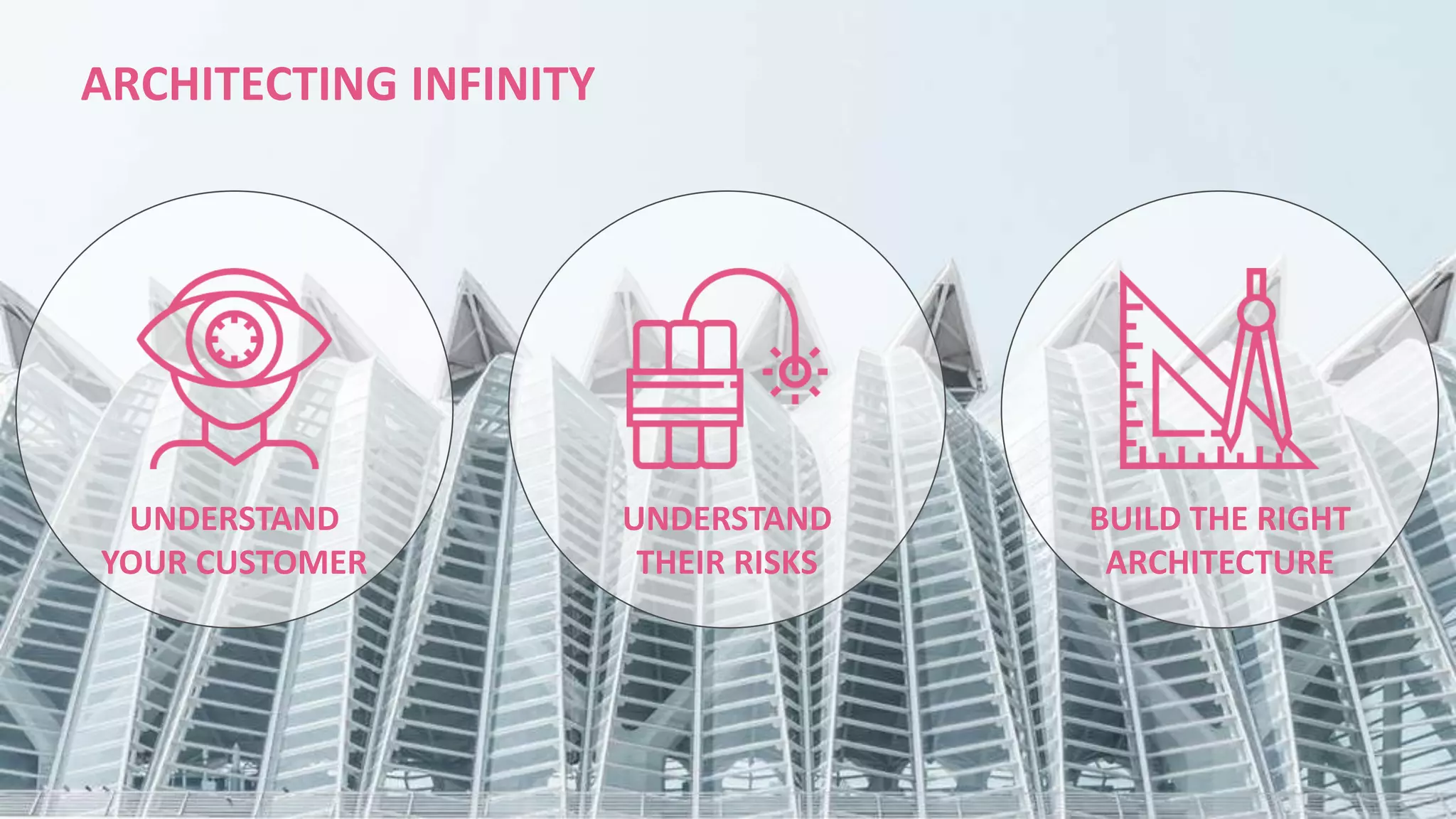
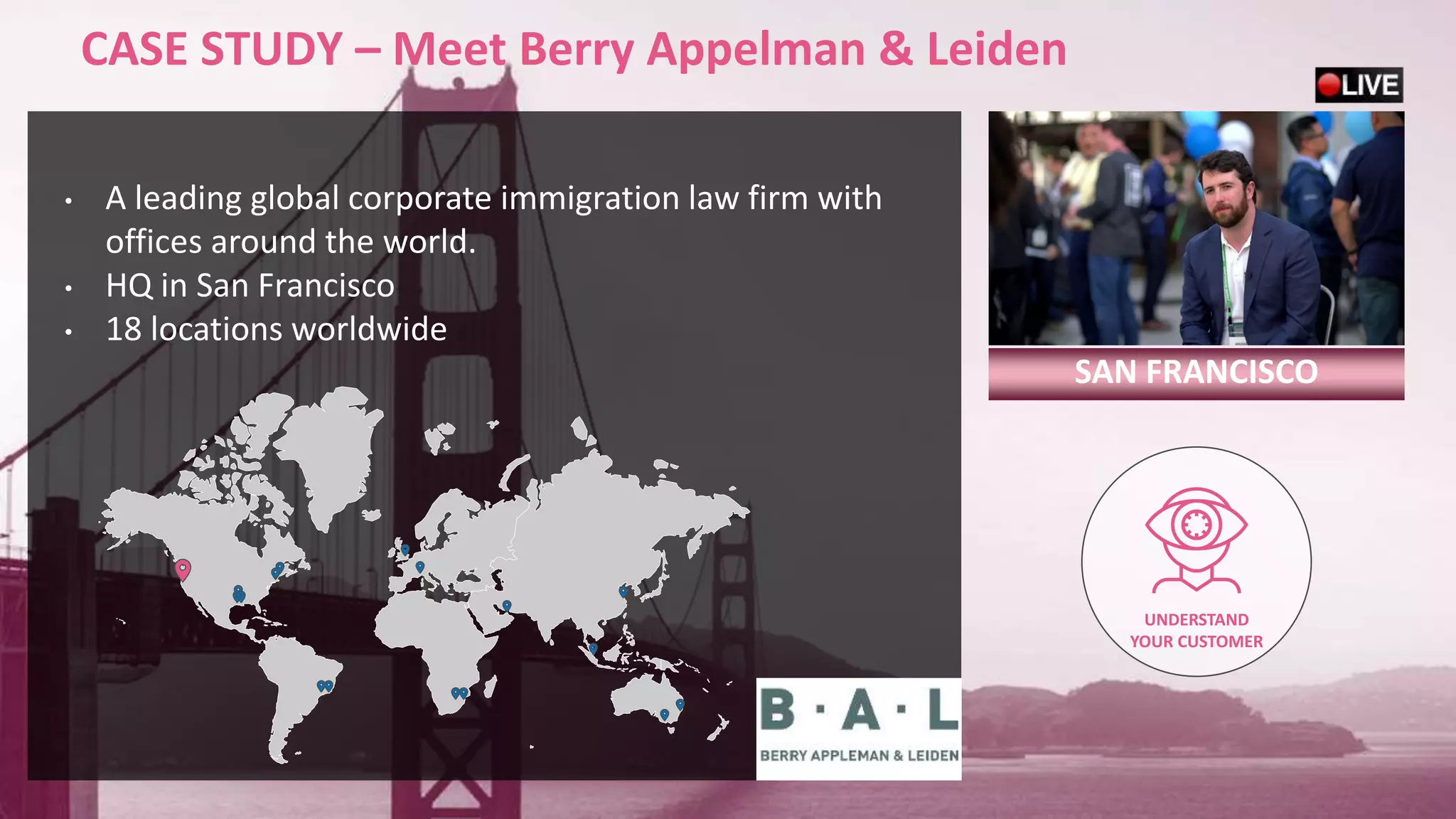
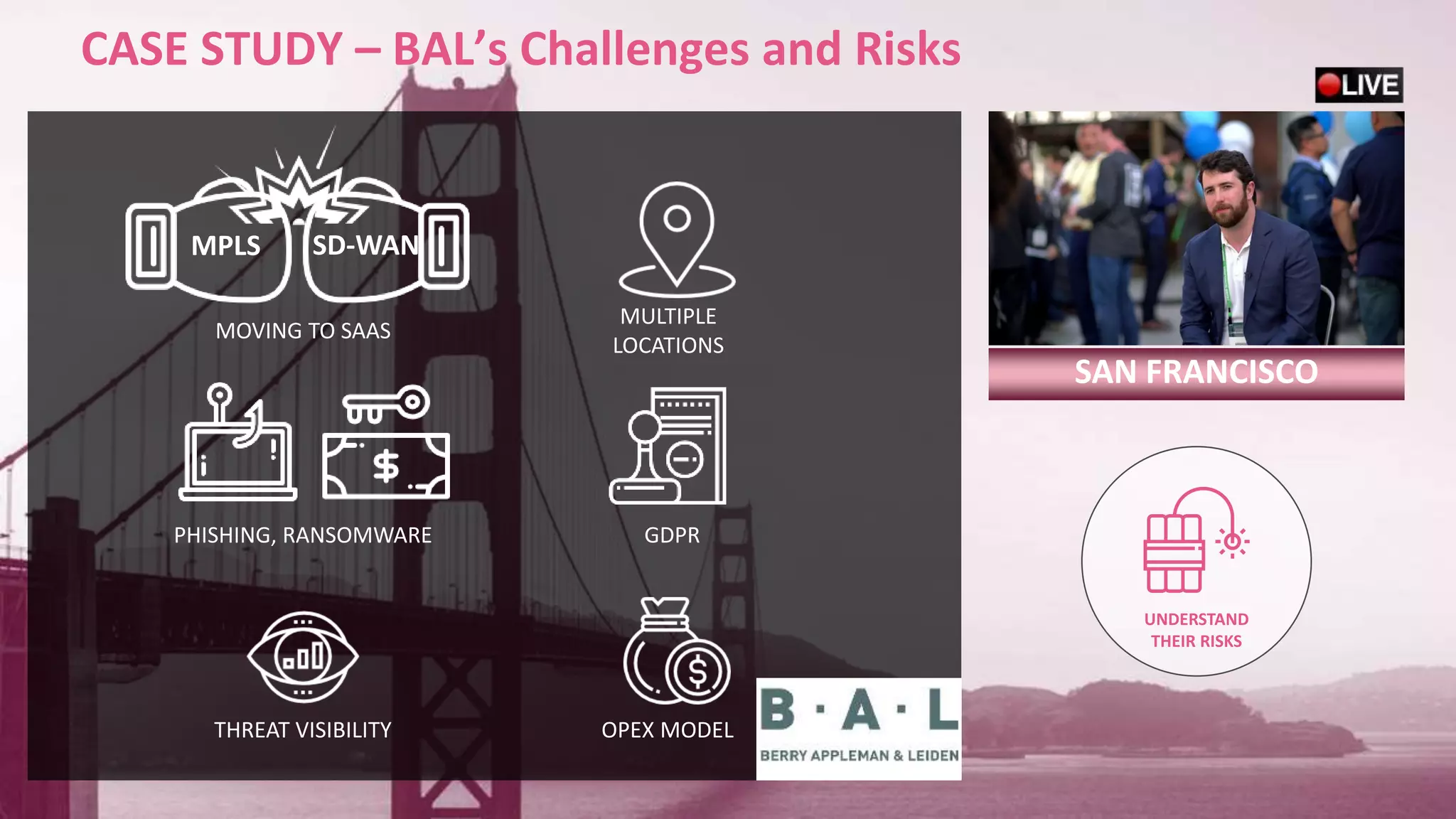
This document discusses consolidating security architectures using Check Point's Infinity platform. It outlines three types of architectures: bad (firewall + IPS), ugly (multi-vendor), and good (single vendor). A case study of a law firm is presented that has multiple locations and uses cloud services. Their challenges include threats, visibility, and compliance. The document recommends moving to an SD-WAN architecture using Check Point to protect cloud services and endpoints from threats in a consolidated manner while meeting compliance and moving to an OPEX model. When architecting security with Infinity, it advises understanding the customer, their risks, and building the right architecture.