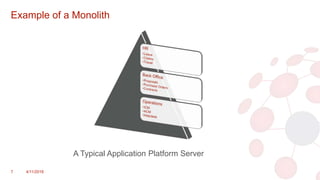
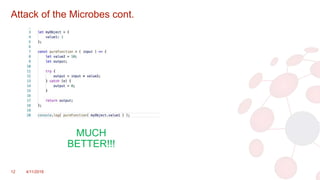
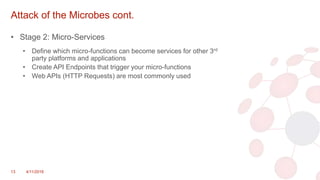
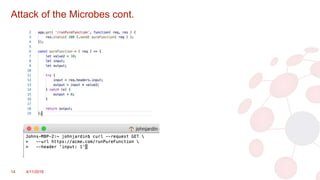
The document discusses key concepts in modern software architecture, specifically focusing on the transition from monolithic applications to microservices and the use of containerization technologies like Docker and orchestration tools such as Kubernetes. It outlines challenges faced in application development and deployment, such as scaling issues and code conflicts, while presenting solutions that include breaking down applications into micro-functions and utilizing Istio for managing microservices. The document concludes by offering resources and contact information for further exploration of these technologies.