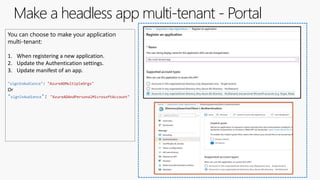
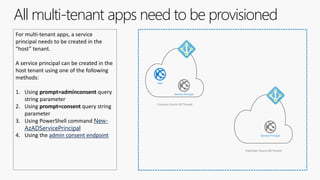
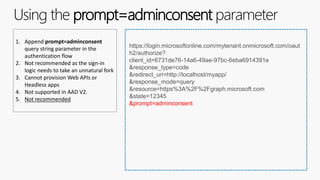
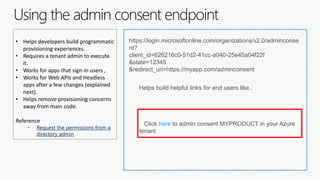
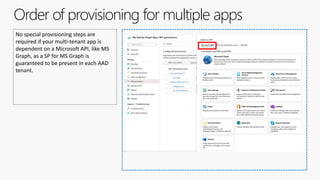
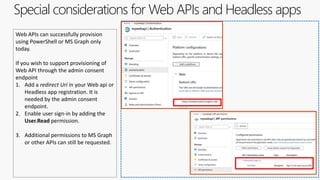
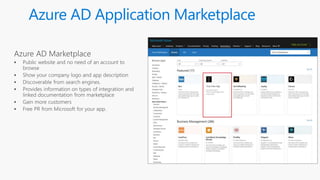
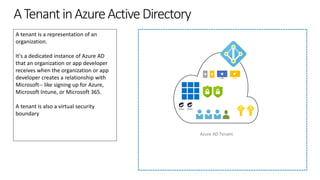
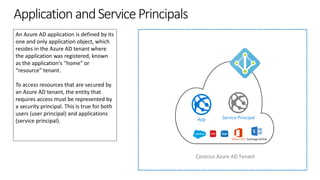
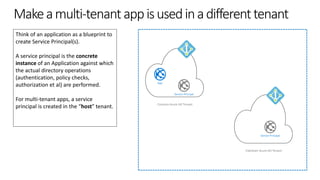
The document outlines the development of multi-tenant applications using the Microsoft Identity Platform, highlighting key concepts like Azure AD tenants, application and service principals, and security practices. It covers the necessary prerequisites, steps for provisioning multi-tenant applications, and differences between single-tenant and multi-tenant setups. The document also emphasizes best practices for permissions management, branding, and promoting SaaS applications, while providing cautions about common pitfalls in multi-tenant app development.






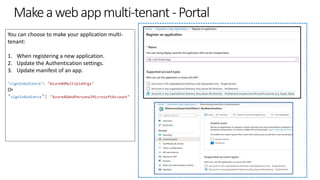


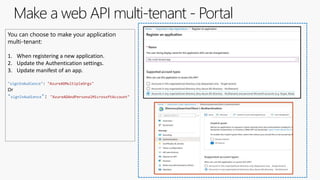
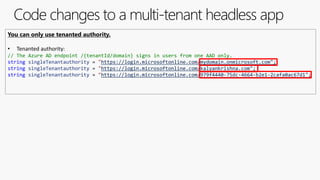
![Code changes in a multi-tenant Web API
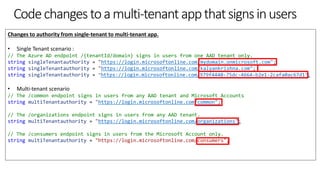
During token validation, inspect the access token and allow callers from all tenants
new WindowsAzureActiveDirectoryBearerAuthenticationOptions
{
Tenant = ConfigurationManager.AppSettings["ida:Tenant"],
TokenValidationParameters = new TokenValidationParameters
{
ValidAudience = ConfigurationManager.AppSettings["ida:Audience"],
// If you do not care which tenant the user came from, or sign-in users from any AAD tenant, then set this flag to false.
ValidateIssuer = false
},
});](https://image.slidesharecdn.com/developmulti-tenantappswiththemicrosoftidentityplatform-200417162959/85/Community-call-Develop-multi-tenant-apps-with-the-Microsoft-identity-platform-20-320.jpg)
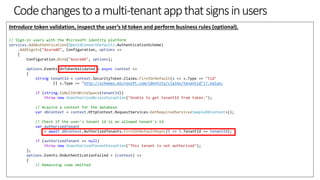
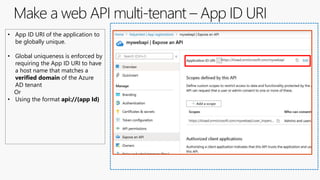
![Code changes in a multi-tenant Web API
During token validation, allow certain tenants.
new WindowsAzureActiveDirectoryBearerAuthenticationOptions
{
Tenant = ConfigurationManager.AppSettings["ida:Tenant"],
TokenValidationParameters = new TokenValidationParameters
{
ValidAudience = ConfigurationManager.AppSettings["ida:Audience"],
// When you wish to limit the tenants from where users can sign into this app, then set it to "true"
// and populate the ValidIssuers collections as explained above.
ValidateIssuer = true,
ValidIssuers = new List<string>()
{
"https://sts.windows.net/72f988bf-86f1-41af-91ab-2d7cd011db47/",
"https://login.microsoftonline.com/161335b9-9e1b-4386-bb58-160a62e6c889/v2.0",
"https://login.microsoftonline.com/c72a295d-d7a5-41ea-a351-b15dd9f67215/v2.0"
},
},
});](https://image.slidesharecdn.com/developmulti-tenantappswiththemicrosoftidentityplatform-200417162959/85/Community-call-Develop-multi-tenant-apps-with-the-Microsoft-identity-platform-21-320.jpg)