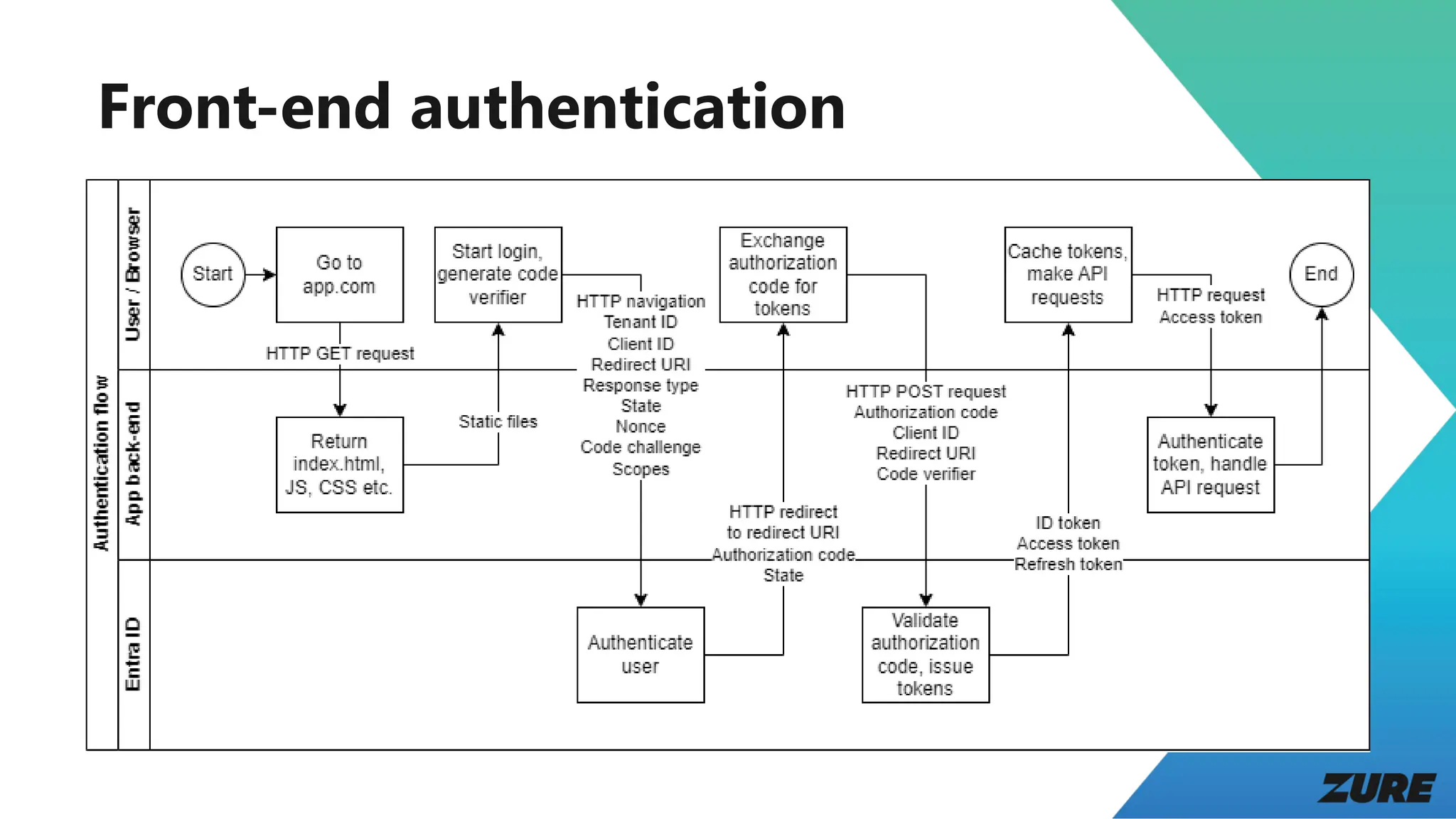
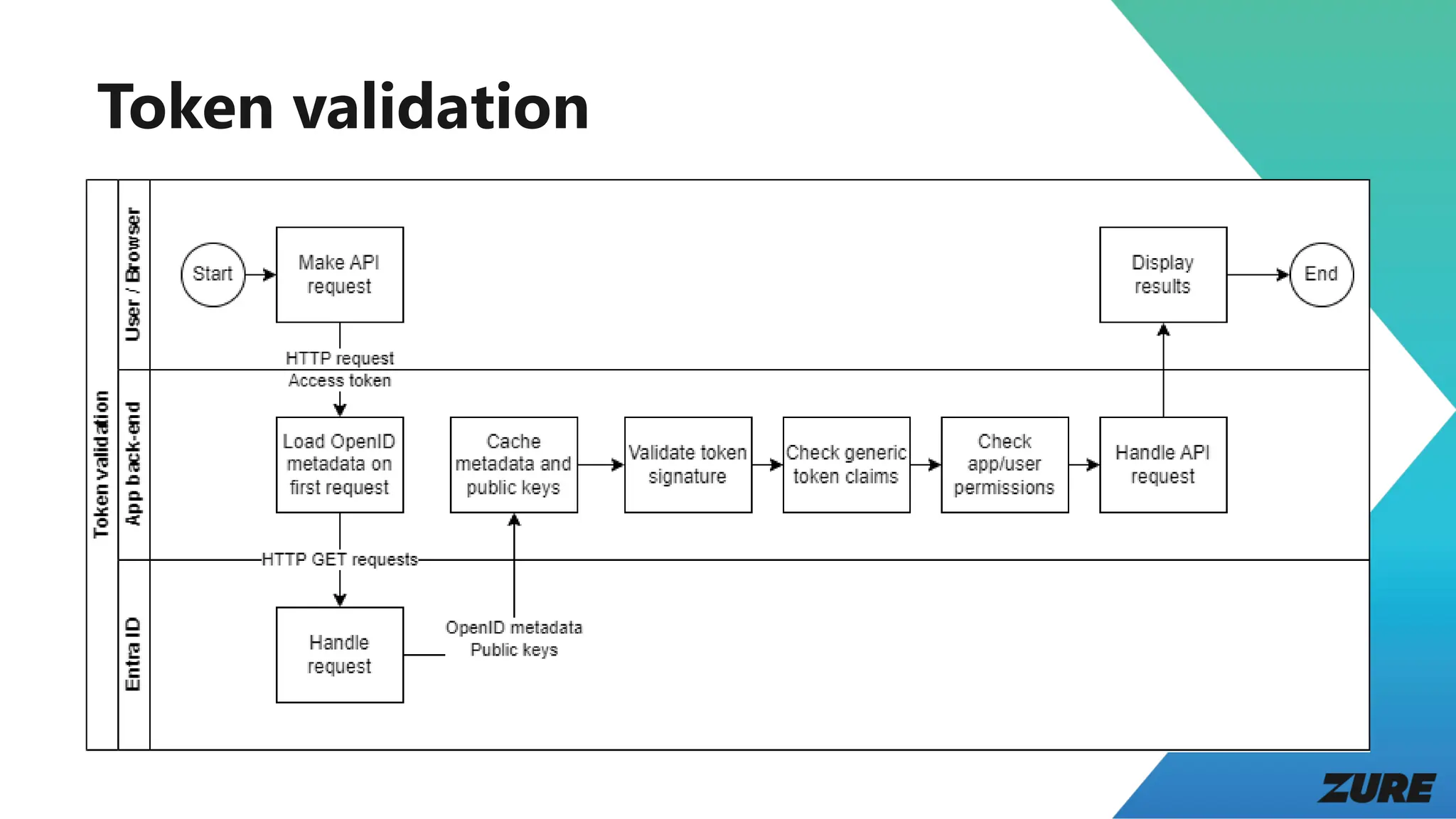
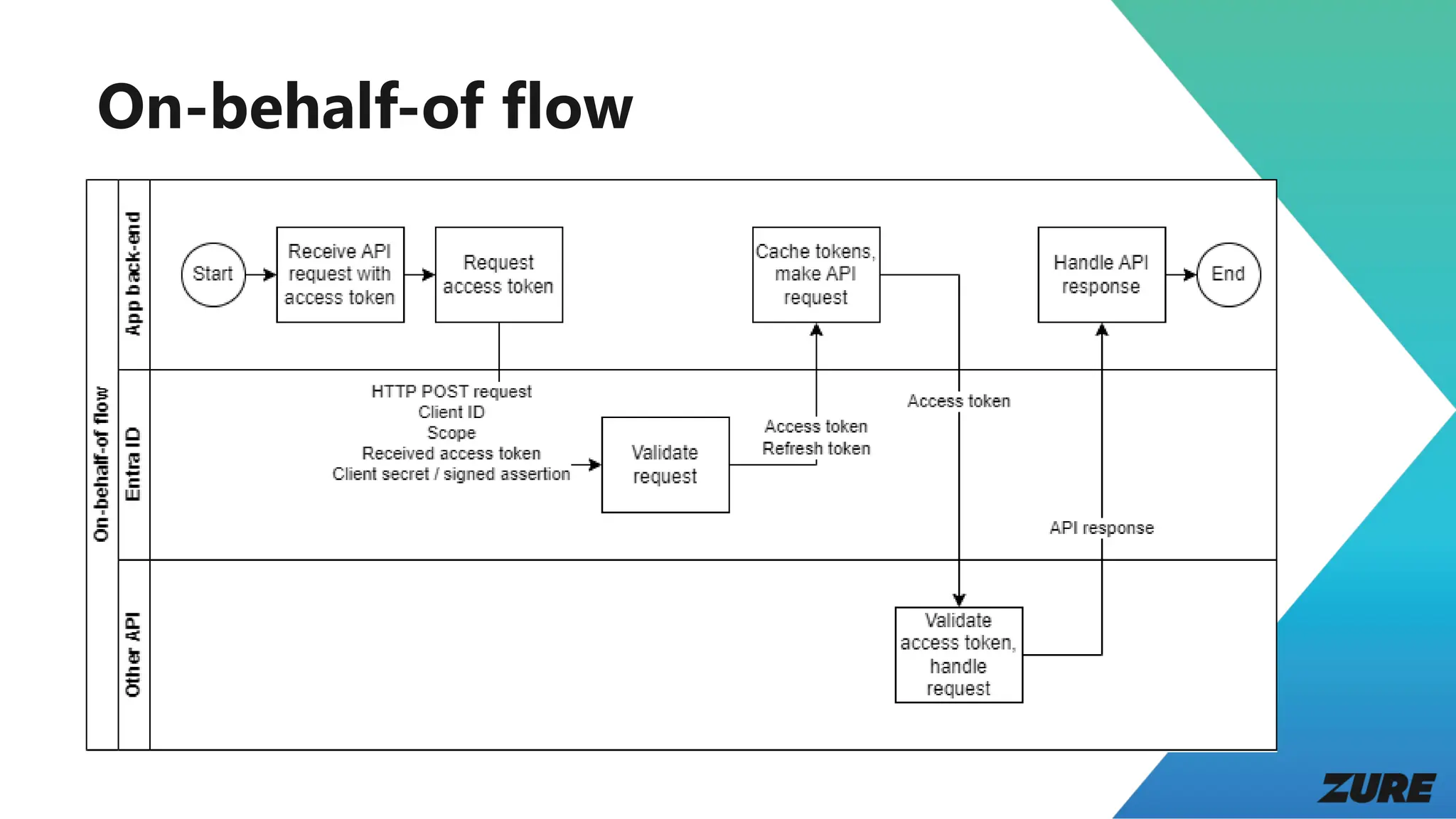
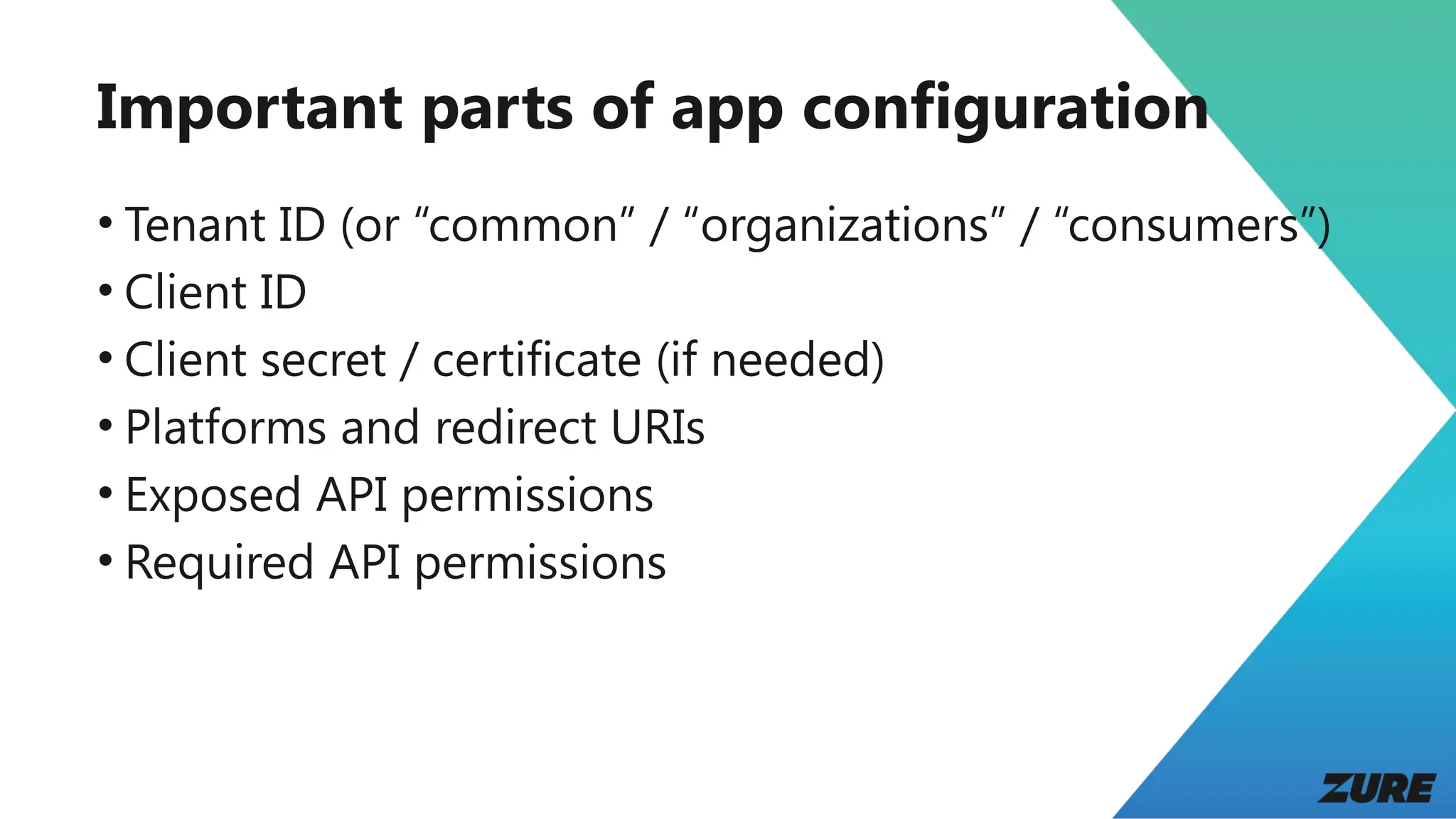
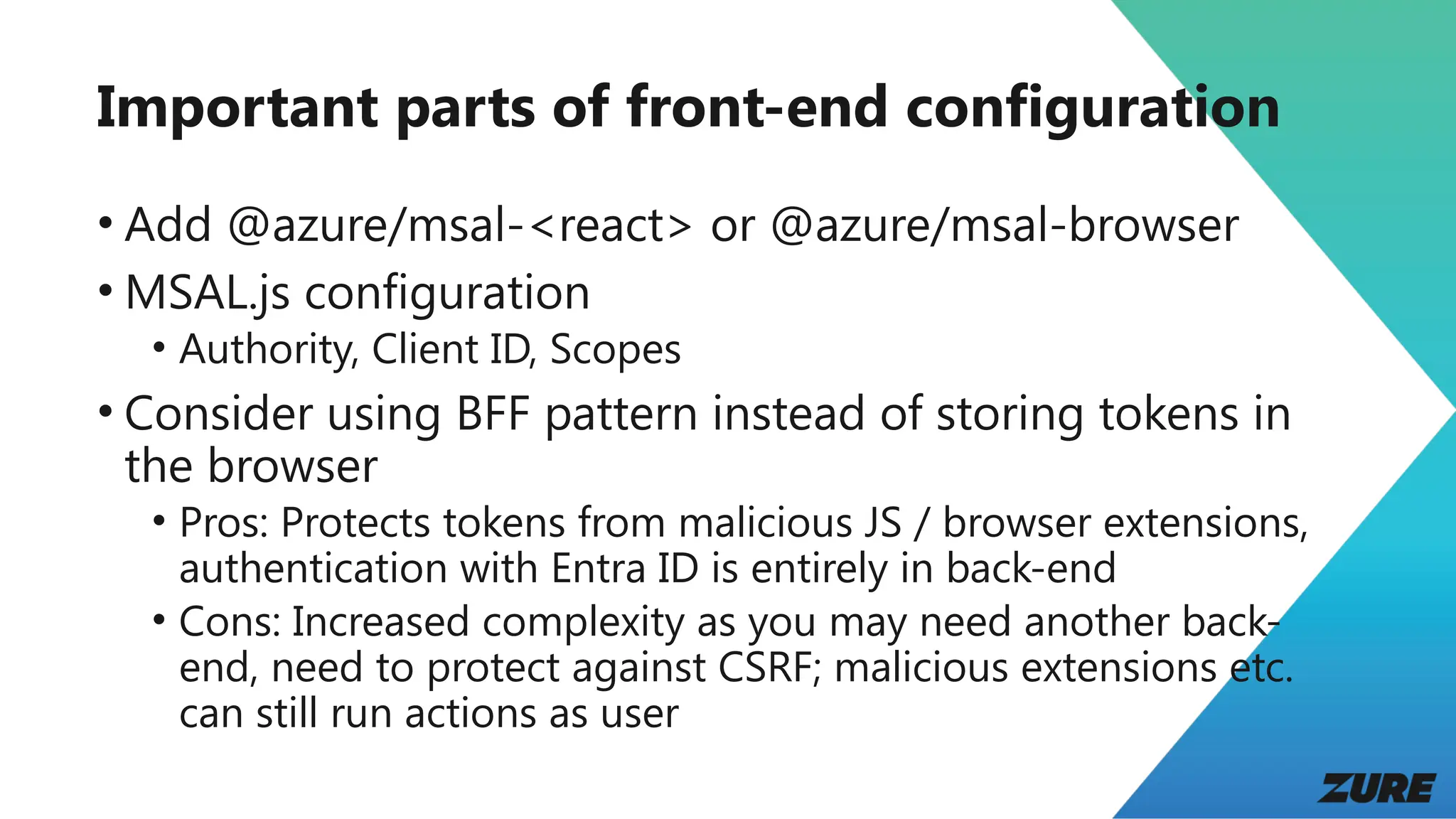
The document outlines a presentation by Joonas Westlin on securing modern web applications using Entra ID, OpenID Connect, and OAuth 2. It includes a series of demos covering app configuration, token types, and front-end and back-end integration, as well as important considerations regarding permissions and security. Additional resources and sample applications are provided to assist in implementation.