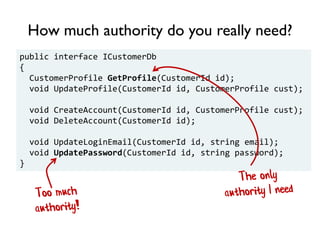
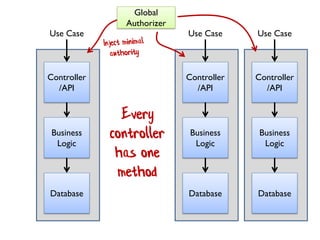
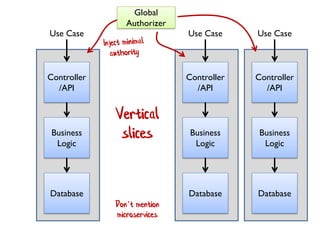
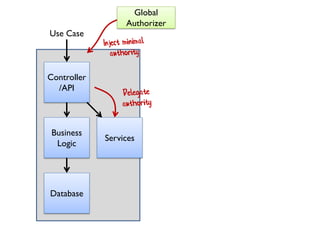
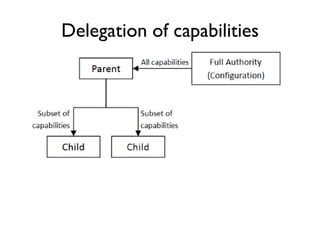
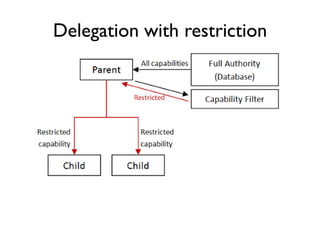
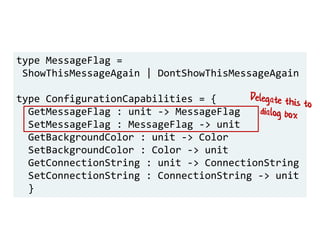
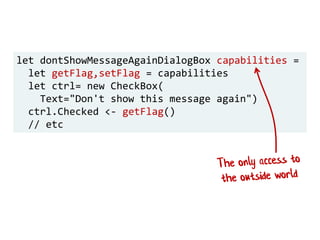
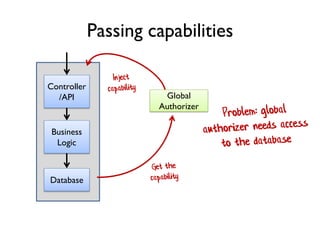
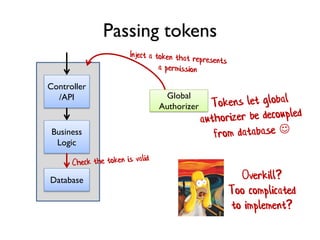
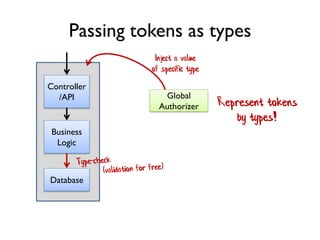
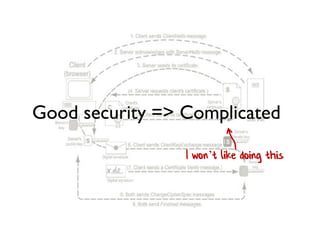
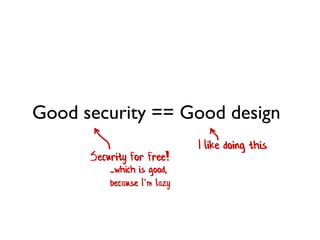
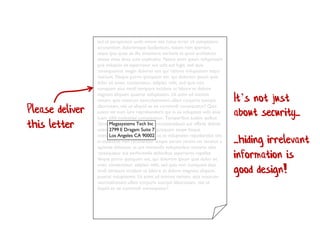
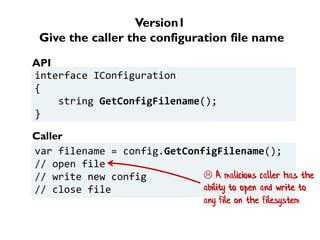
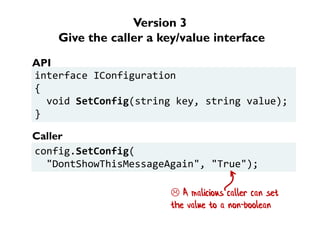
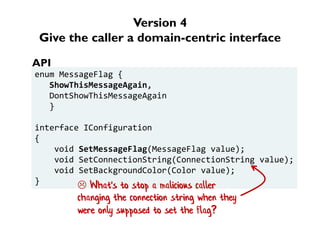
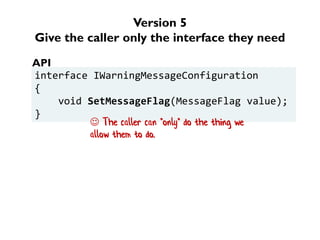
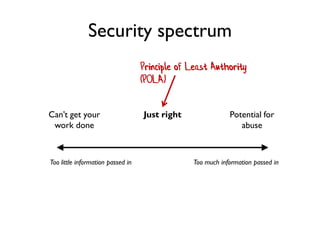
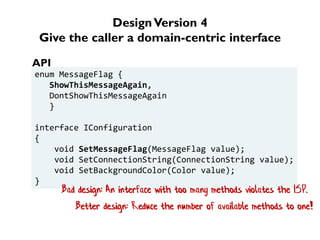
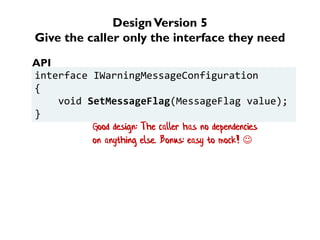
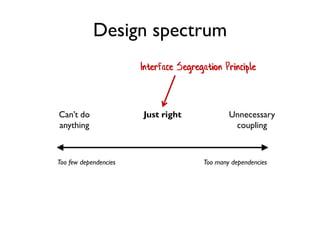
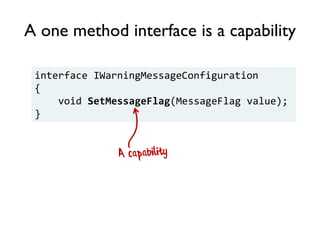
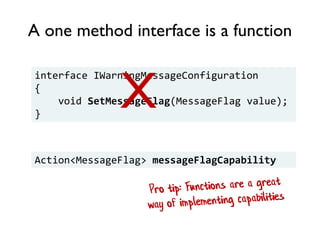
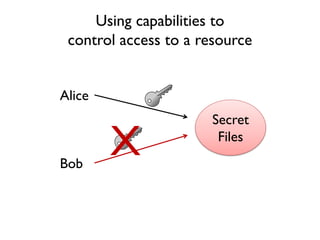
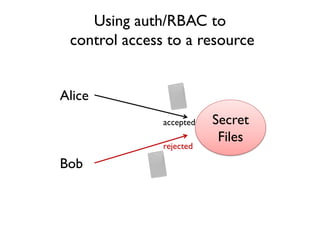
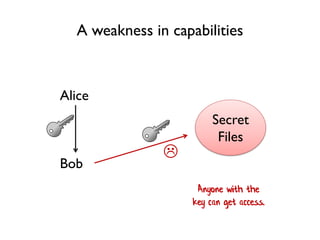
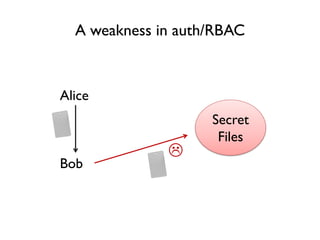
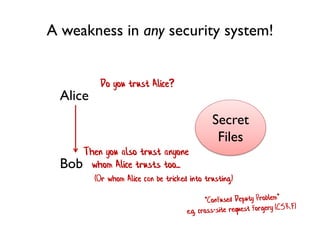
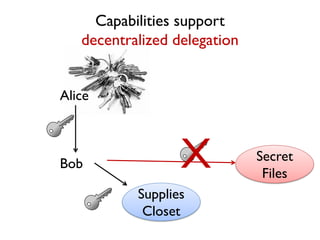
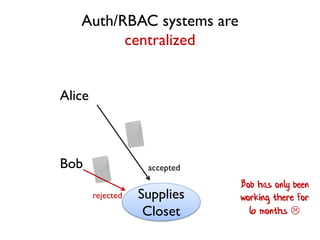
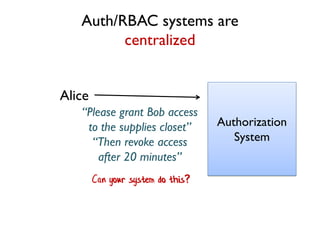
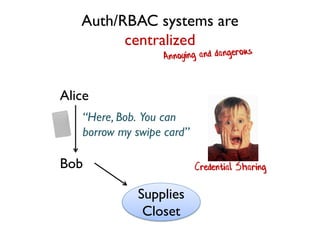
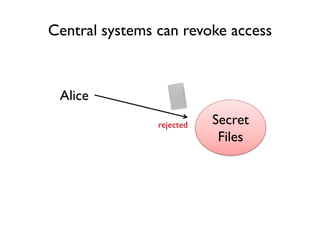
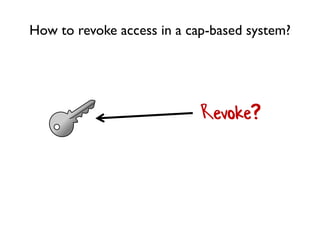
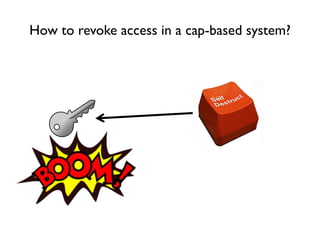
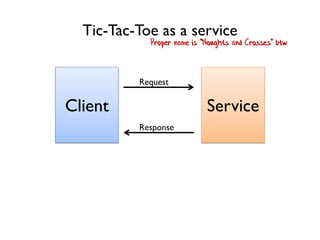
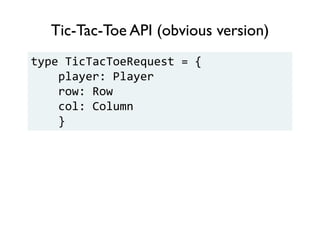
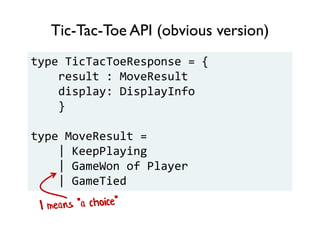
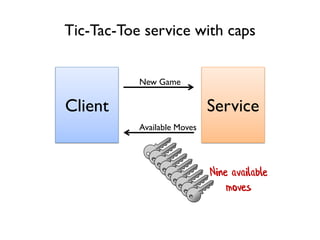
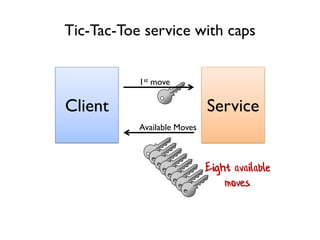
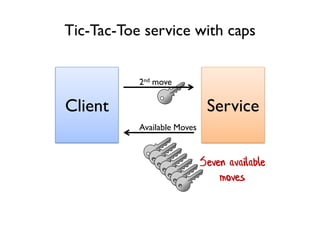
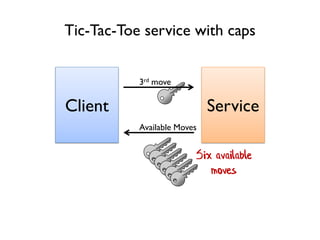
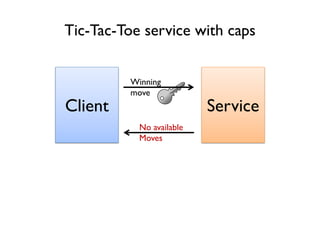
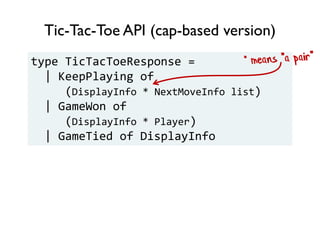
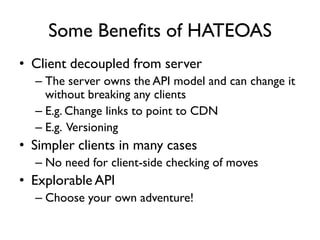
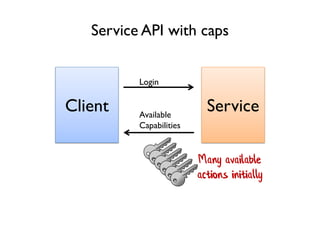
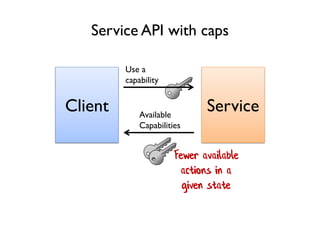
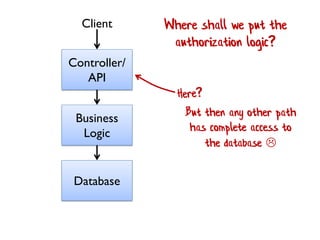
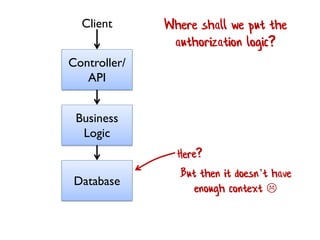
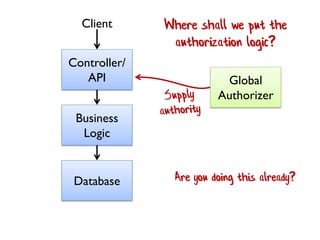
The document discusses the importance of capability-based design in API development, emphasizing that good security is inherently linked to good design. It explains how limiting the capabilities of API callers can prevent security risks and encourages practices such as minimizing exposed surface area. The talk integrates principles from both security and design to propose a systematic approach to building secure and flexible interfaces.
































![public class CustomerController : ApiController
{
readonly ICustomerDb _db;
public CustomerController(ICustomerDb db)
{
_db = db;
}
[Route("customers/{customerId}")]
[HttpGet]
[GetCustomerProfileAuth]
public IHttpActionResult Get(int customerId)
{
var custId = new CustomerId(customerId);
var cust = _db.GetProfile(custId);
var dto = DtoConverter.CustomerToDto(cust);
return Ok(dto);
}](https://image.slidesharecdn.com/designingwithcapabilities-160116160830/85/Designing-with-Capabilities-78-320.jpg)