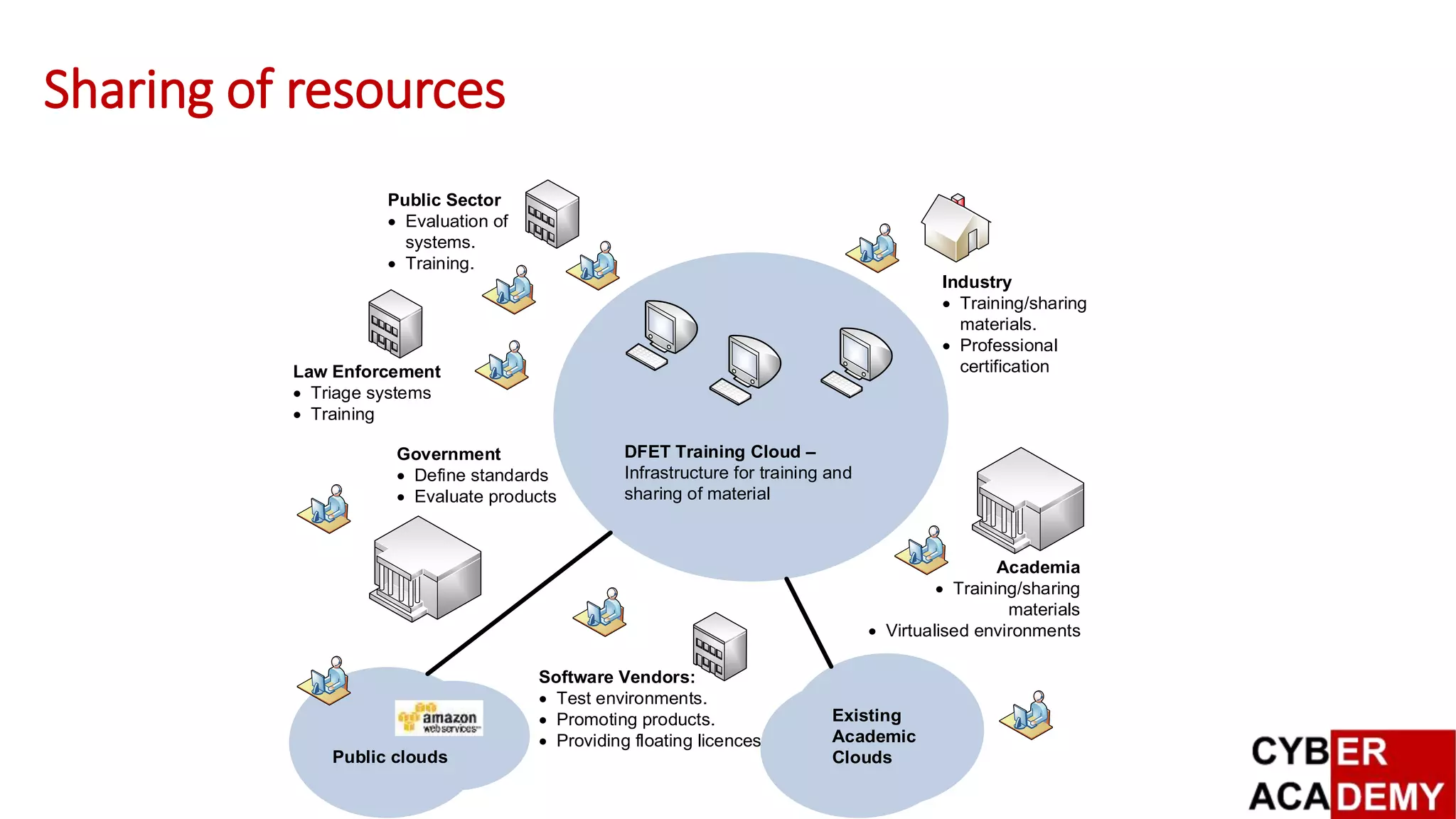
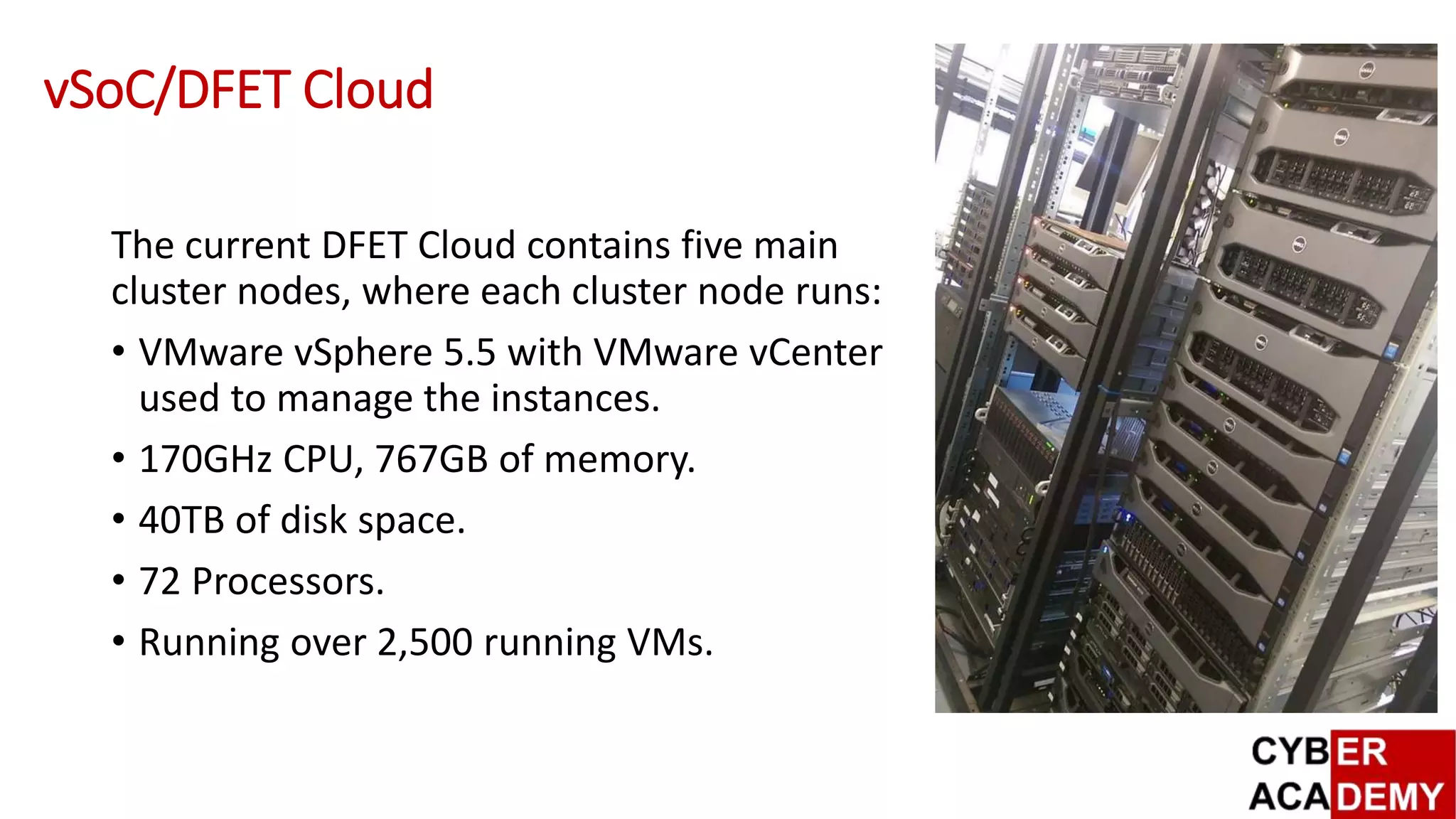
This document describes the design and evaluation of a virtualized Security Operations Centre ([vSoC]). [vSoC] leverages virtualization technology to provide a shared training environment for public sector, academia, and industry. It currently hosts over 2,500 virtual machines across various operating systems and security tools. Modules in the [vSoC] have been used to teach over 500 students across various cybersecurity courses. Current work is focused on integrating additional security tools like F5 Big-IP, RSA Security Analytics, and Splunk, as well developing mobile access and capture the flag exercises.
![Design and Evaluation of
[vSoC]: Virtualised
Security Operations
Centre
Prof William J Buchanan, Charley Celice, Peter
Aaby, Bruce Ramsay, Richard Macfarlane, Adrian
Smales, Dr Gordon Russell and Bobby Soutar
http://thecyberacademy.org
[vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-1-2048.jpg)
![Building vSoC
Intrusion
Detection
System
Firewall
Internet
Switch
Router (NAT)
Email
server
Web
server
DMZ
FTP
server
Firewall
Eve
Bob
Alice
Data Centre
Load balancer
Syslog
server [vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-3-2048.jpg)
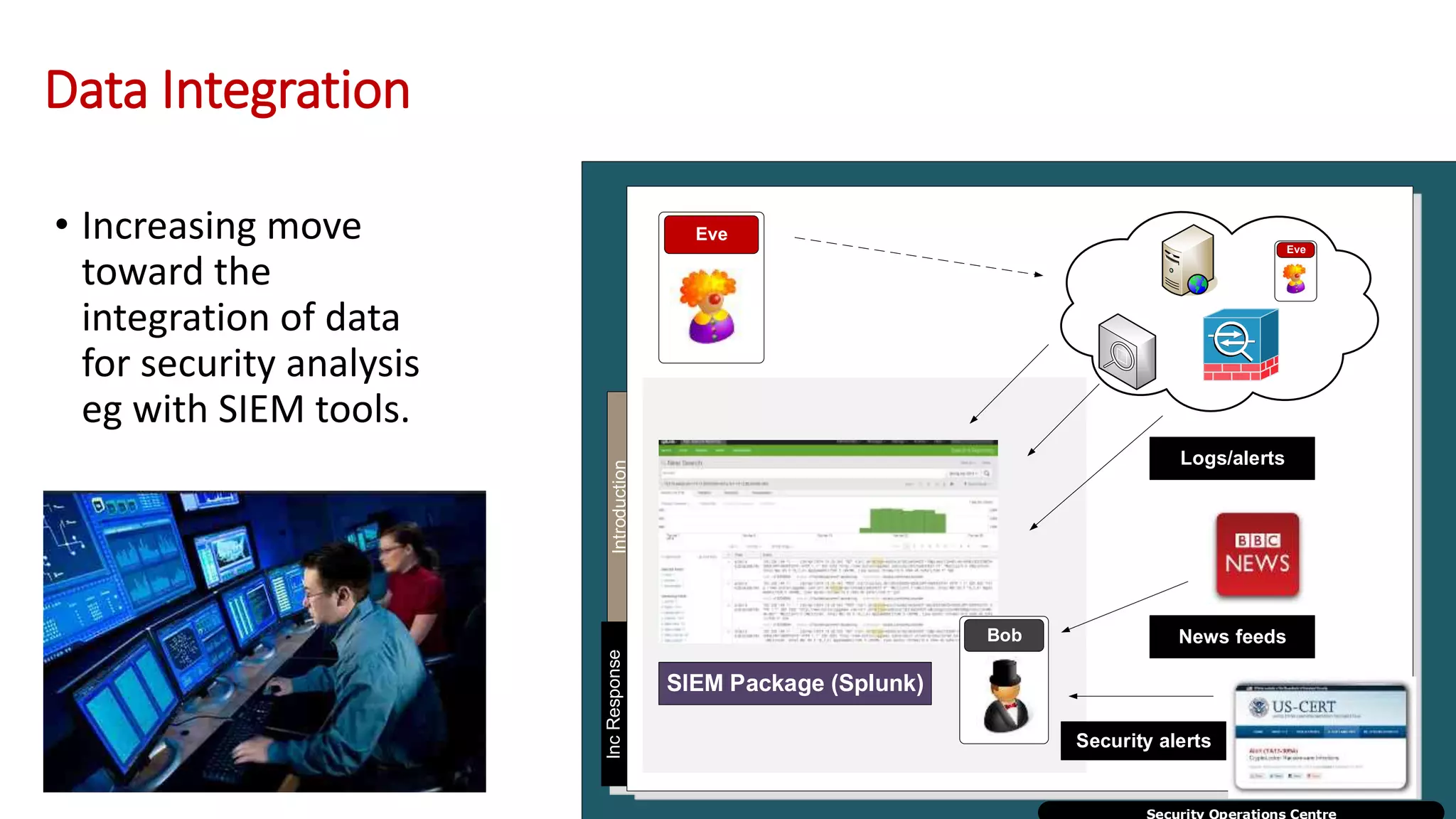
![The Move Toward
Security Analytics
Big Data/SIEM
[vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-5-2048.jpg)


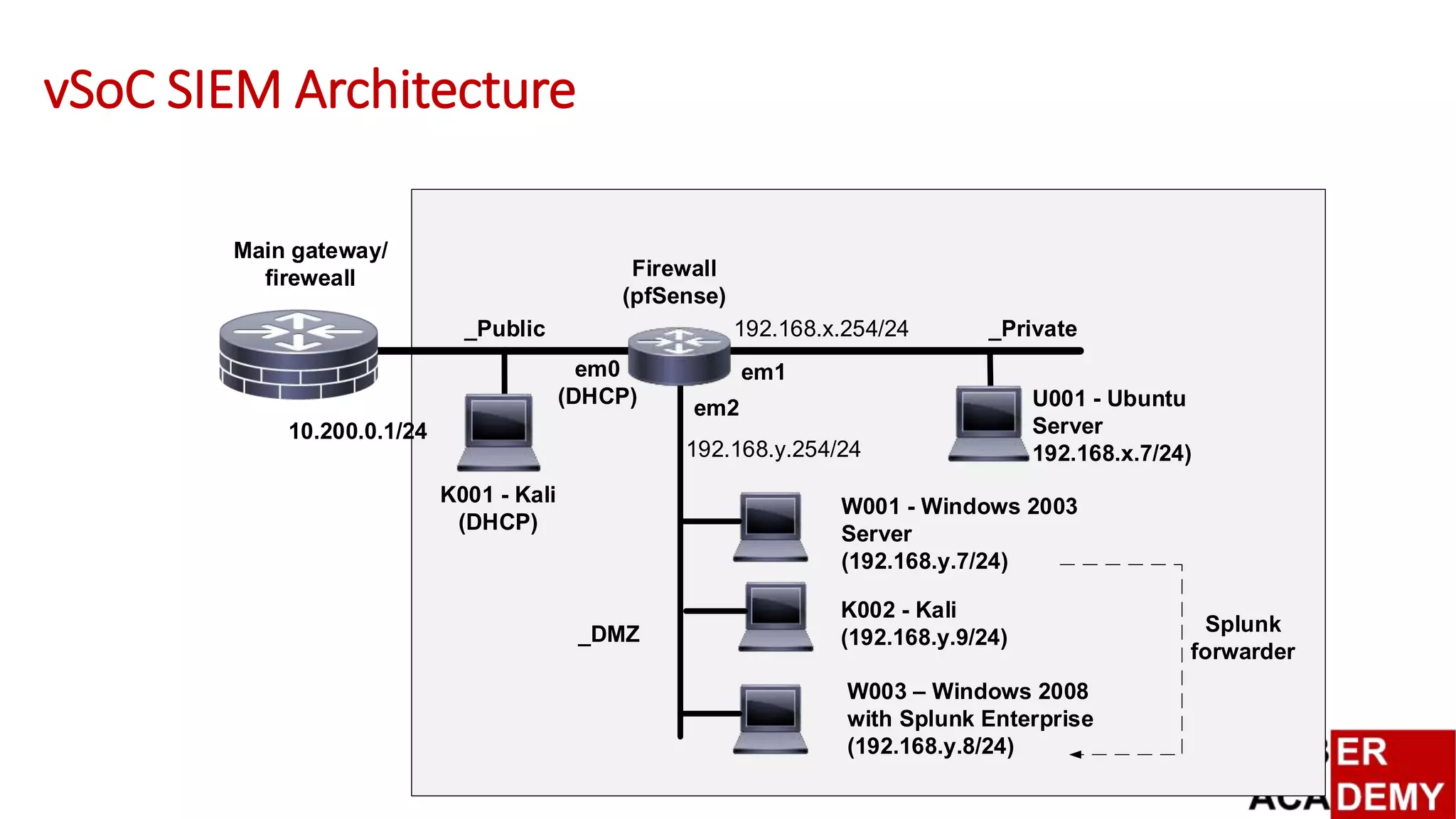
![Design and Evaluation of
[vSoC]: Virtualised
Security Operations
Centre
Splunk Lab Integration
[vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-9-2048.jpg)
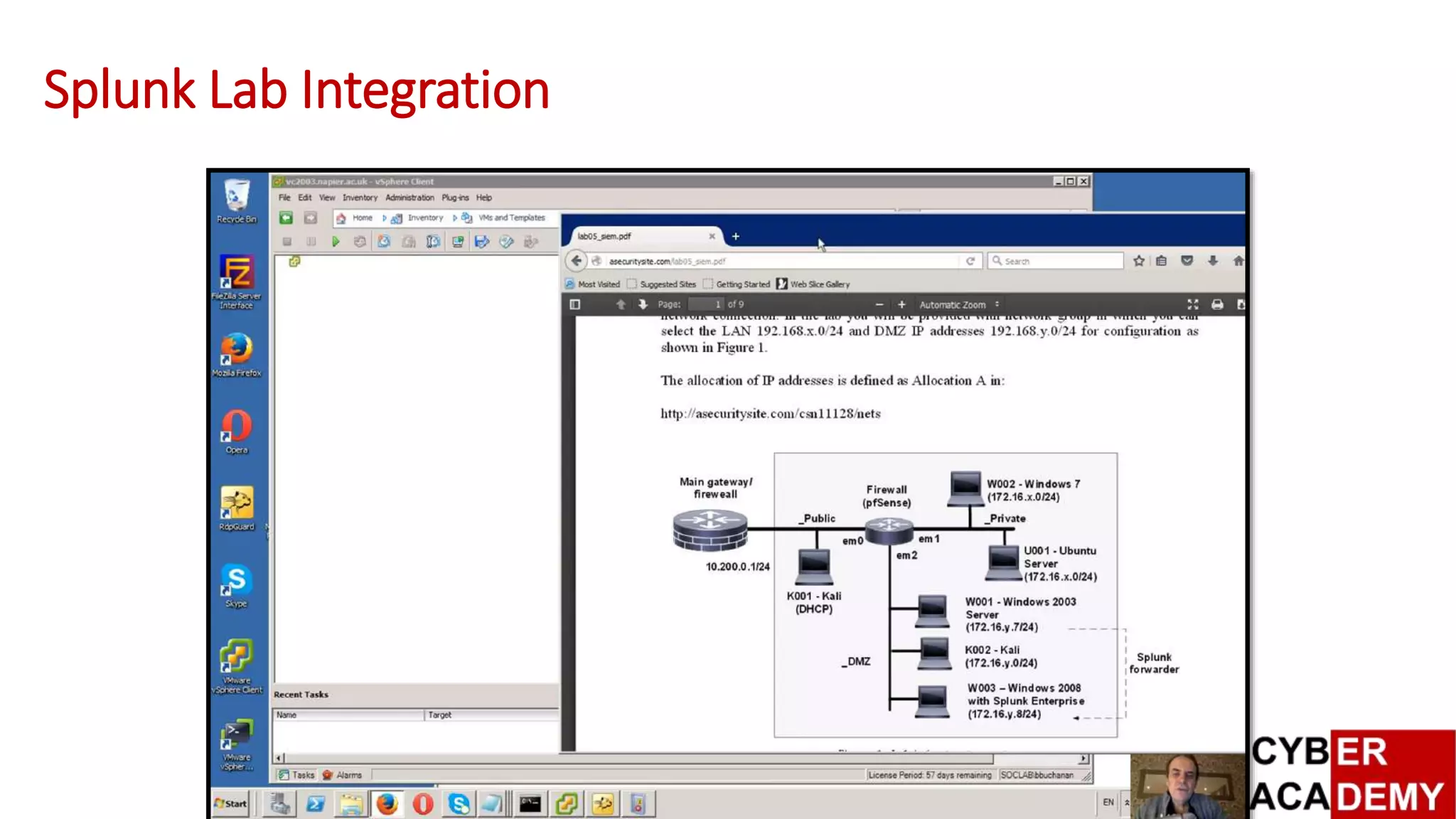
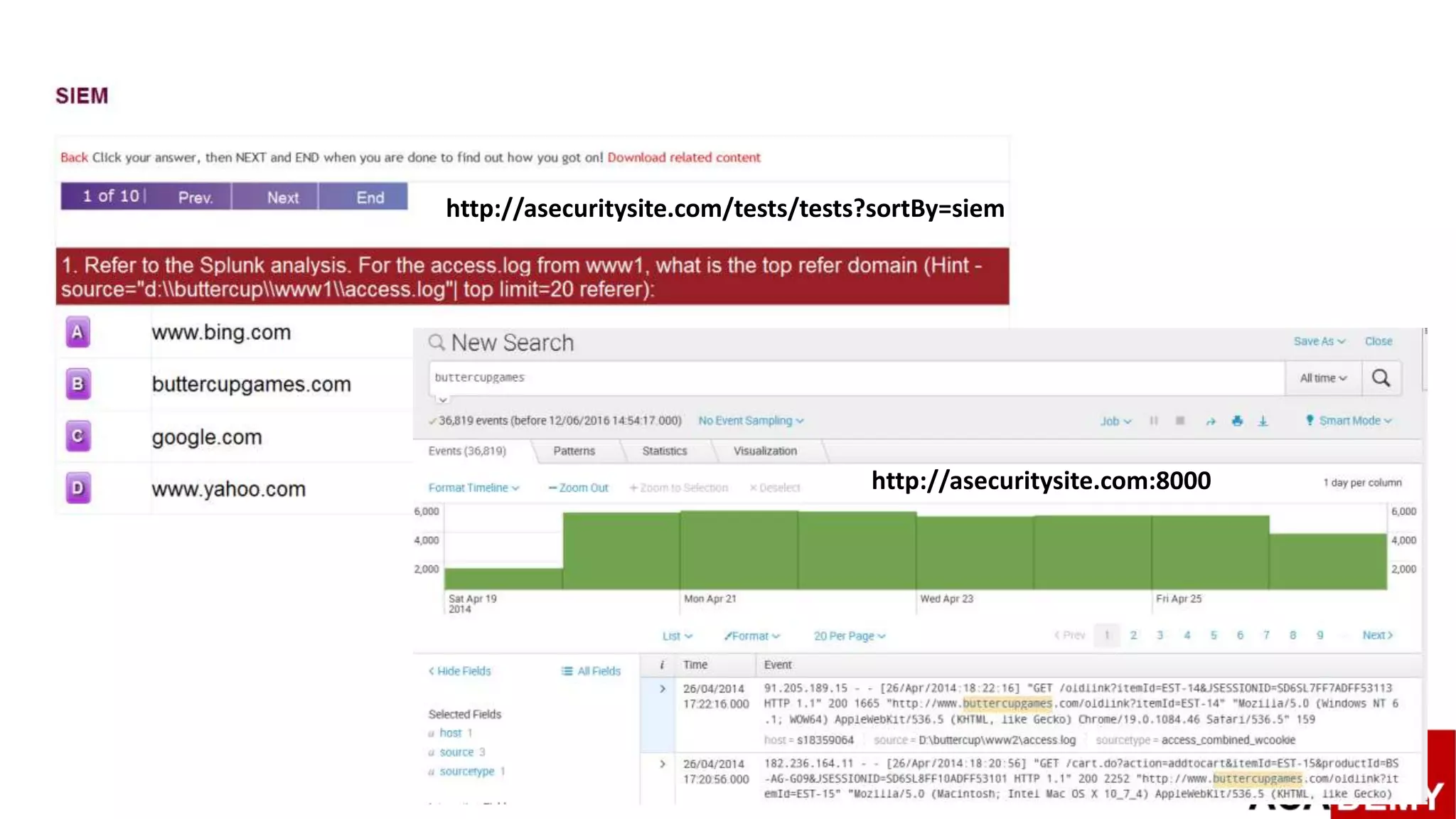
![Design and Evaluation of
[vSoC]: Virtualised
Security Operations
Centre
Splunk Testing Environment –
Buttercupgames
[vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-12-2048.jpg)
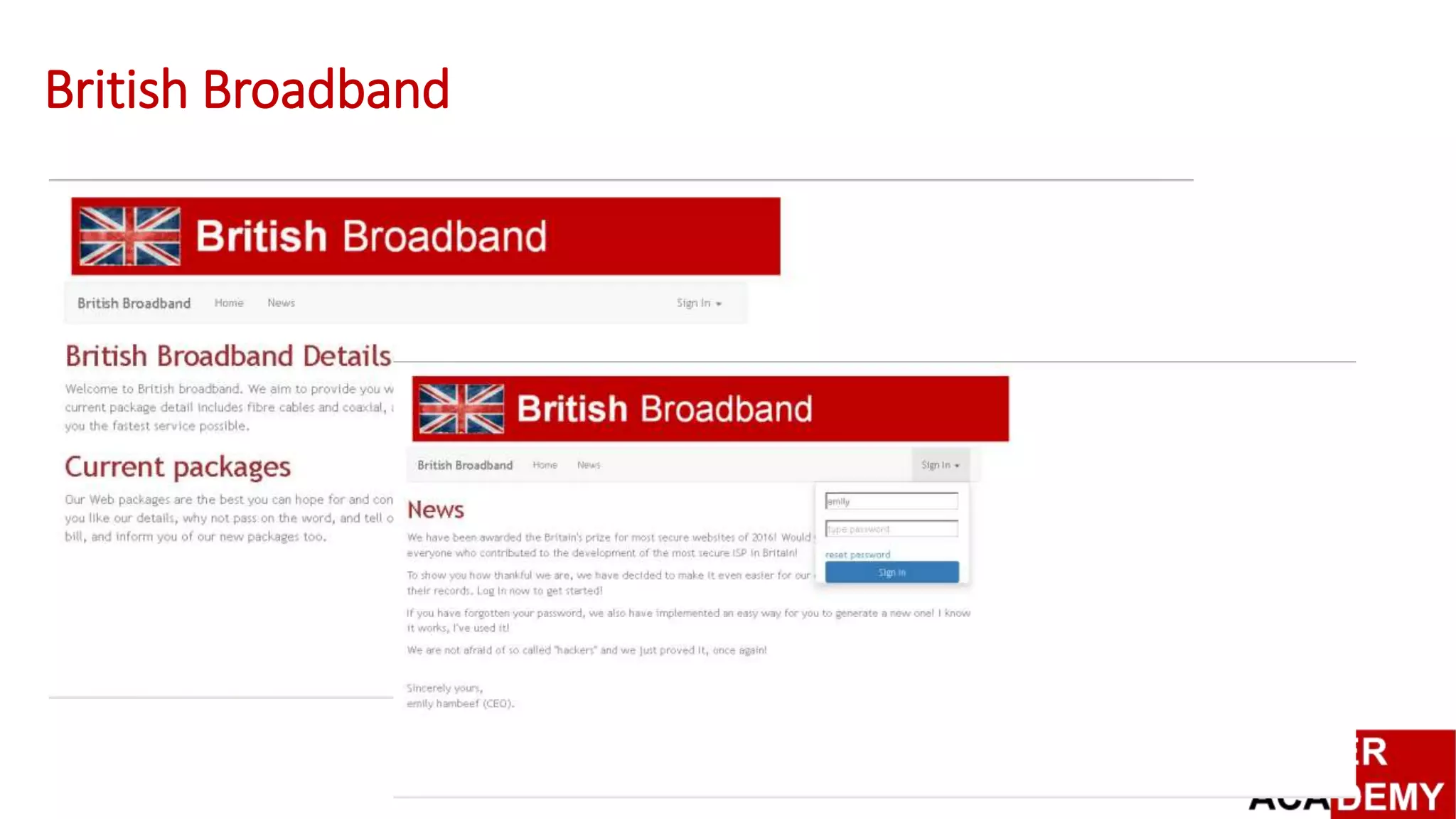
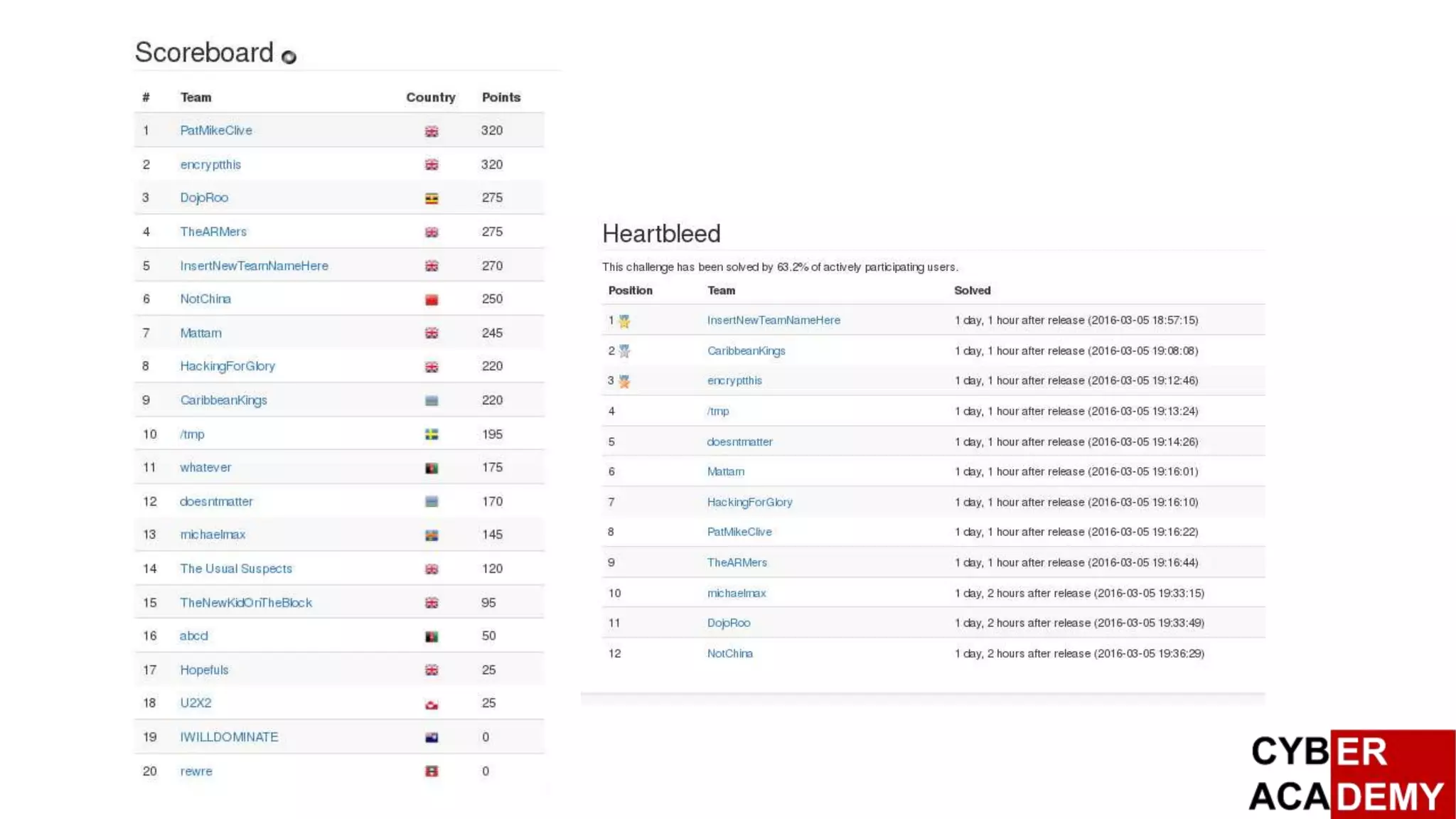
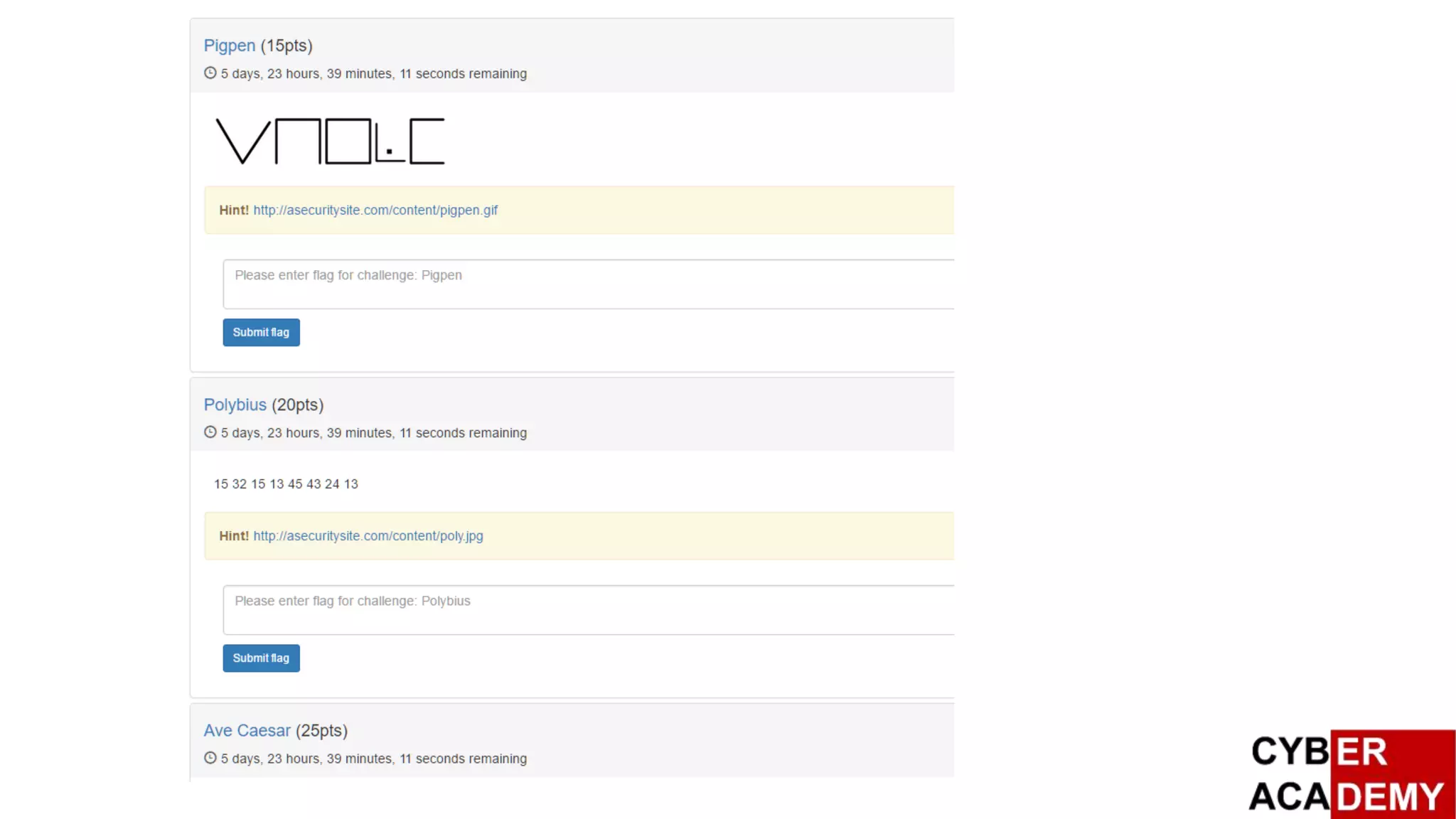
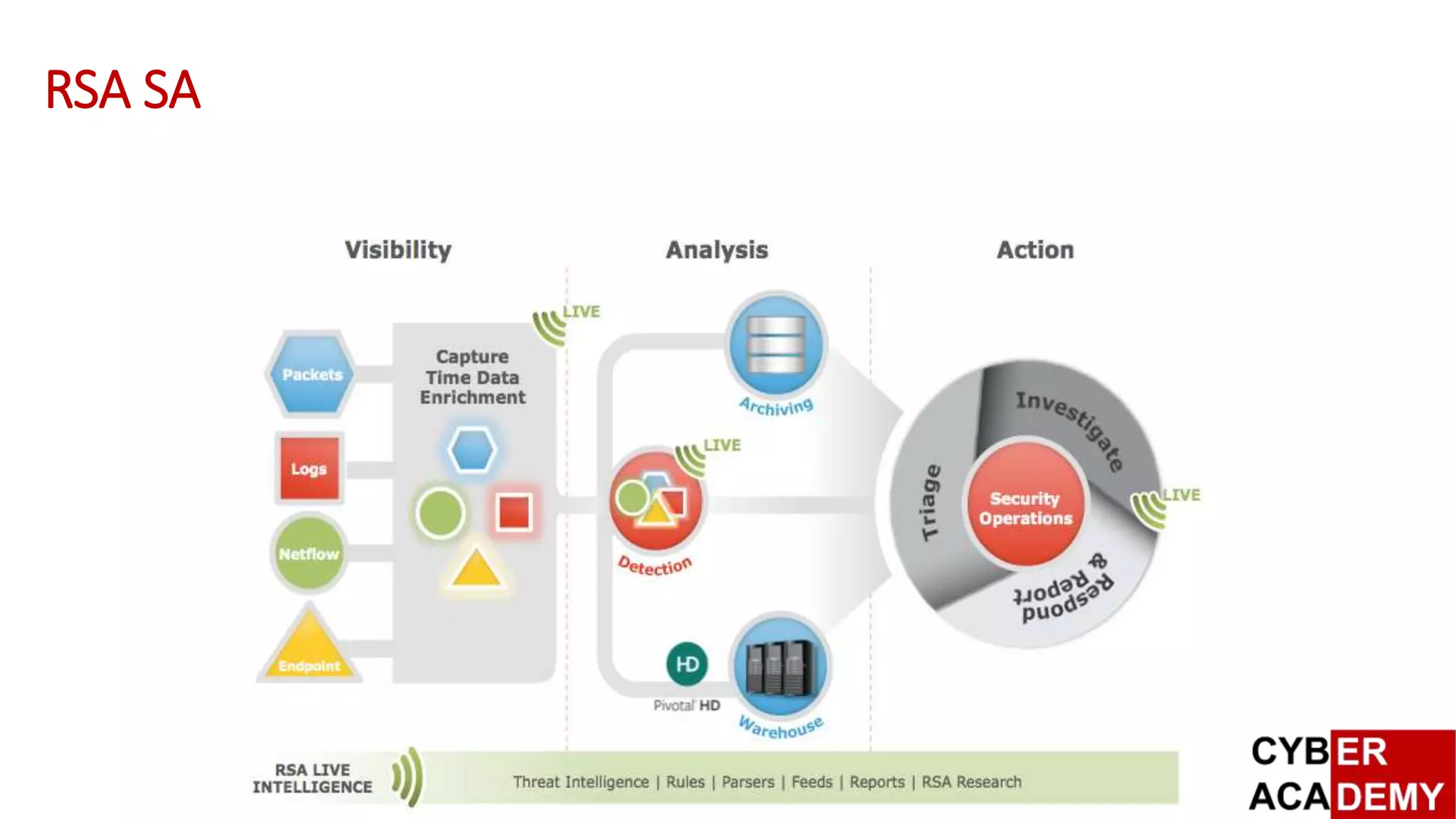
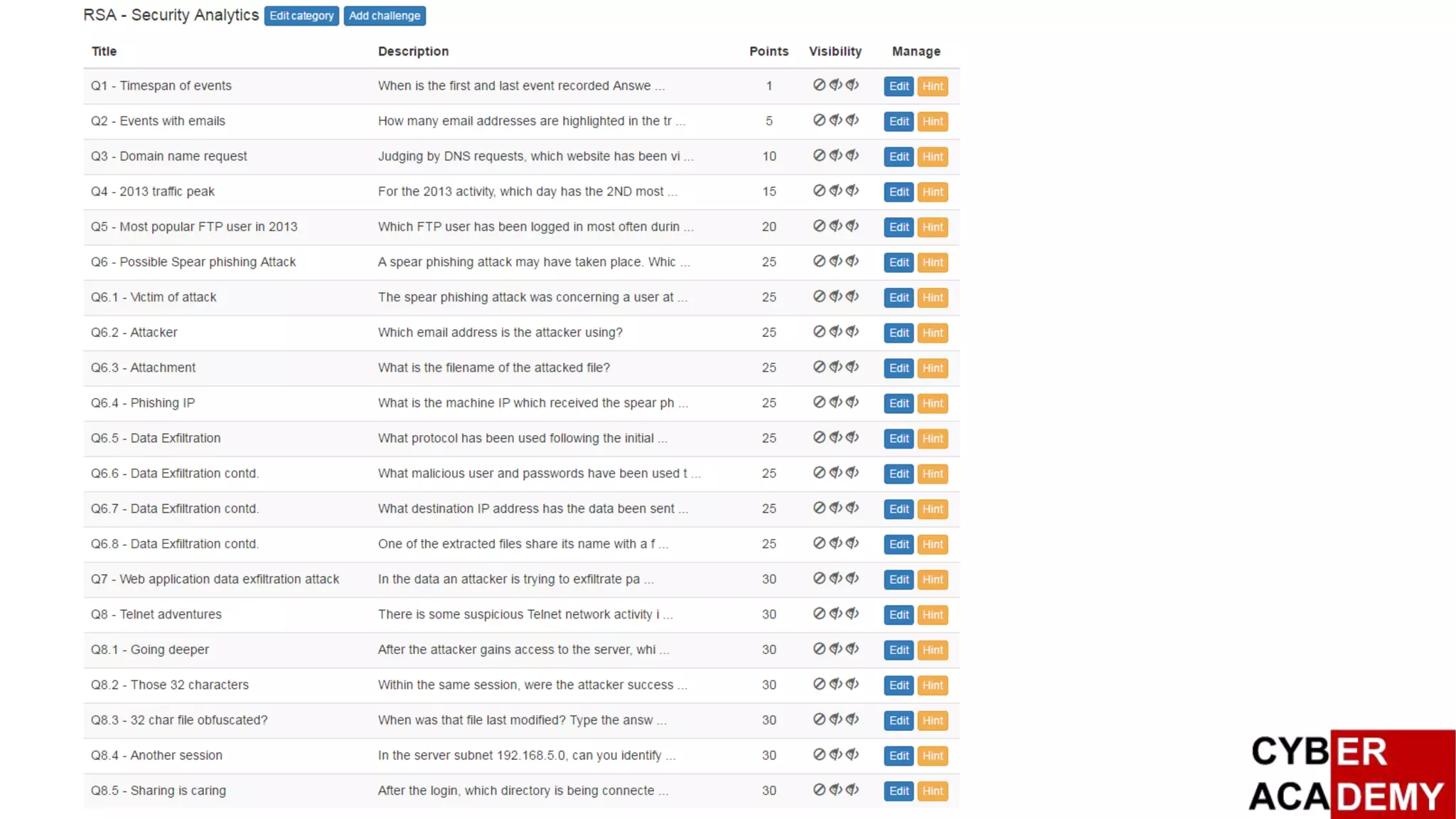
![Capture The Flag
British Broadband, and RSA SA
[vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-14-2048.jpg)



![Design and Evaluation of
[vSoC]: Virtualised
Security Operations
Centre
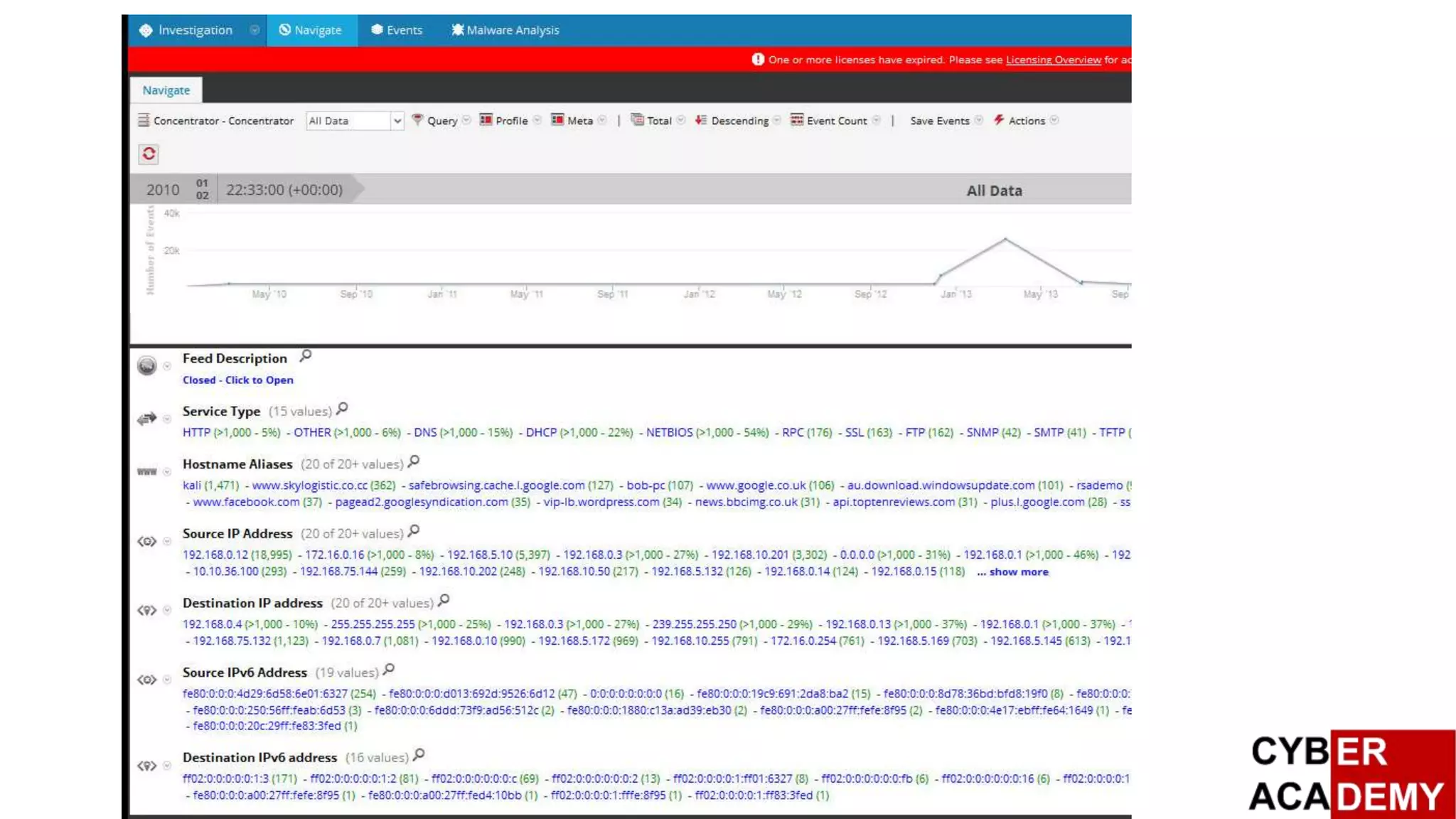
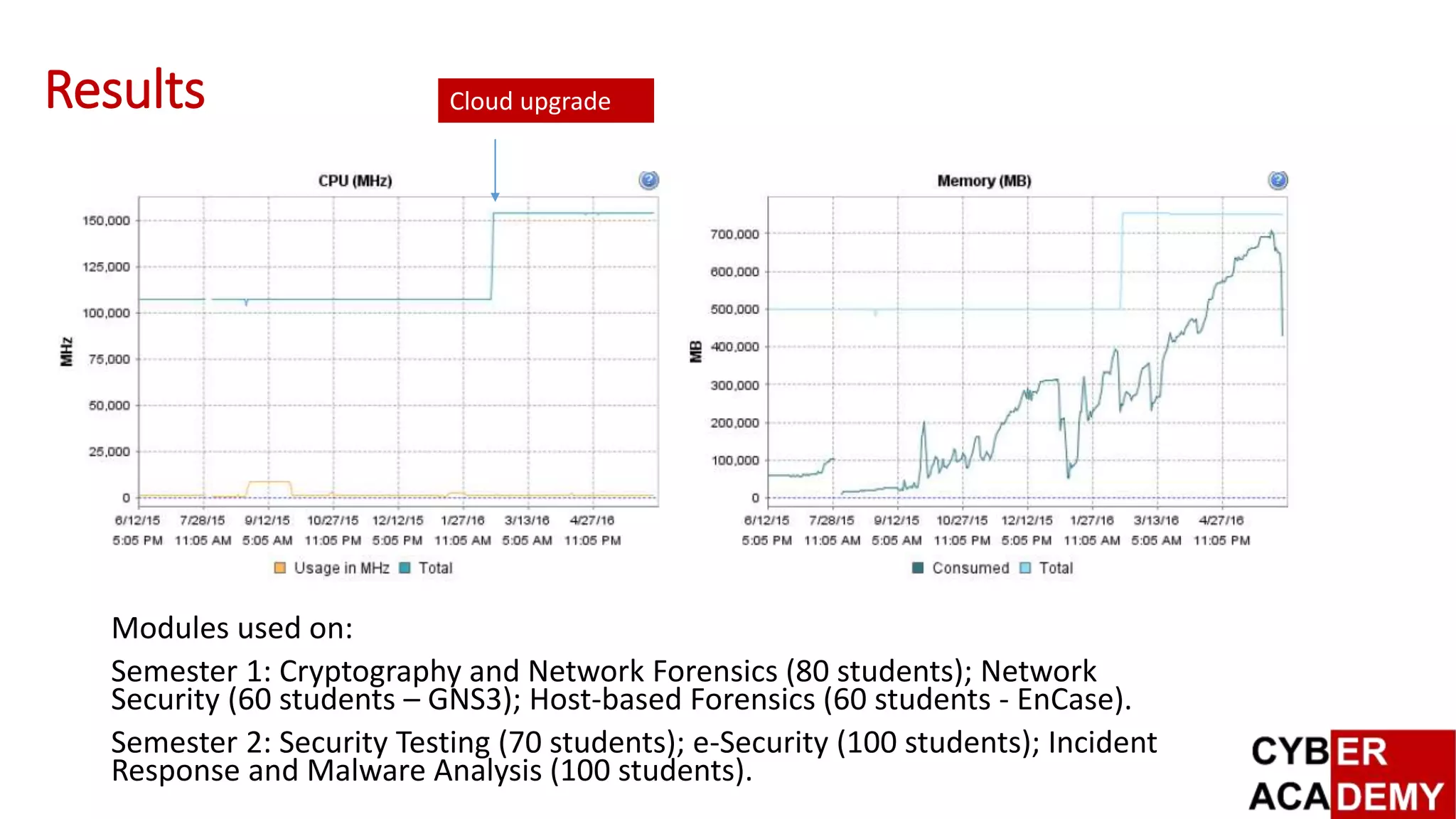
Results
[vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-25-2048.jpg)
![Example $tubuntu = "t_ubuntu_205"
if ($args[1].contains("u"))
{
$ins = $prefix+$iubuntu +$i.ToString("000")+"_private";
...
Write-Output "Creating: $($ins) from $($temp) in $($folder) for $($folder) disk:
$($disk) "
new-vm -name $ins -template $temp -datastore $disk -resourcepool DFETLab -
DiskStorageFormat thin -location $folder
$apt = Get-NetworkAdapter -VM $ins
Set-NetworkAdapter -NetworkAdapter $apt -NetworkName $private -
confirm:$false
Write-Output "Creating: $($ins) from $($temp) in $($folder) for $($folder) disk:
$($disk) "
new-snapshot -VM $ins -Name snapshot
}
Setup network
Create VM
Create known
snapshot](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-27-2048.jpg)

![Design and Evaluation of
[vSoC]: Virtualised
Security Operations
Centre
Prof William J Buchanan, Charley Celice, Peter
Aaby, Bruce Ramsay, Richard Macfarlane, Adrian
Smales, Dr Gordon Russell and Bobby Soutar
http://thecyberacademy.org
[vSoC]](https://image.slidesharecdn.com/vsoc-160704110823/75/Design-and-Evaluation-of-vSoC-Virtualised-Security-Operations-Centre-30-2048.jpg)