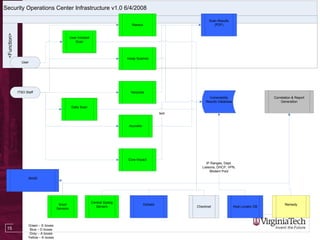
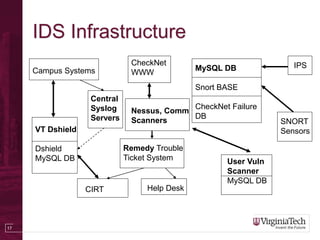
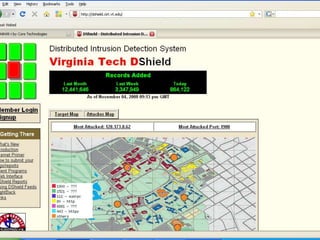
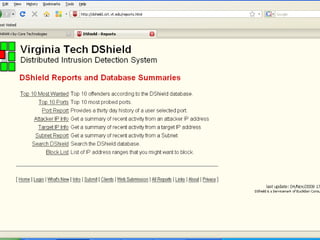
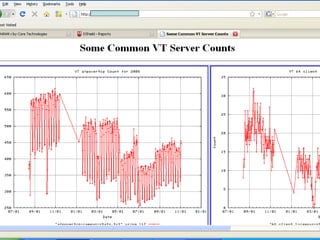
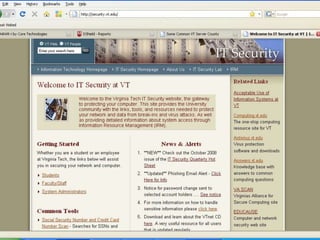
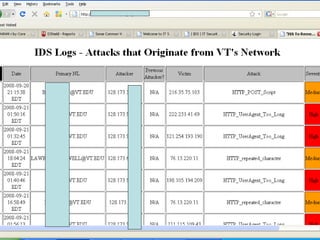
The document discusses building a Cyber Security Operations Center (CSOC) at Virginia Tech to analyze security-related data from various sources and help assess risks, attacks, and compliance with policies. The CSOC will collect and correlate log/event data from systems like IDS sensors, firewalls, vulnerability scanners, and the trouble ticket system to gain a comprehensive view of the university's security posture. This centralized monitoring is meant to support the school's defense in depth strategy and provide metrics for both security operations and executive reporting. The CSOC infrastructure pulls data from distributed servers and sensors via a security information and event management system.