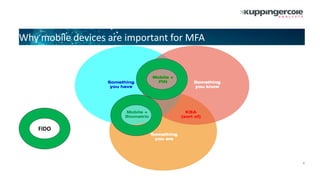
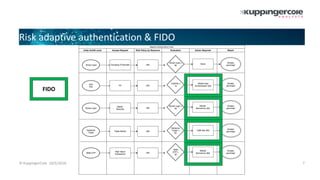
The document discusses the role of mobile devices in multi-factor authentication (MFA) and highlights various authentication methods like FIDO and adaptive authentication. It outlines the importance of factors such as geo-location, user history, and device health in assessing authentication risks. Additionally, it lists vendors recognized in the leadership compass for adaptive authentication solutions and evaluates their market positions and innovations.