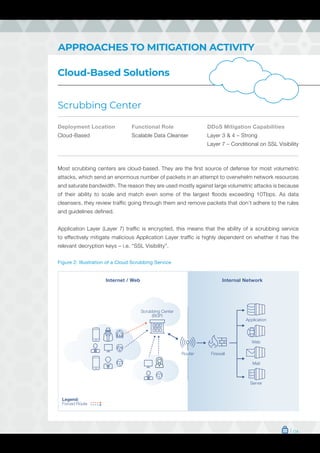
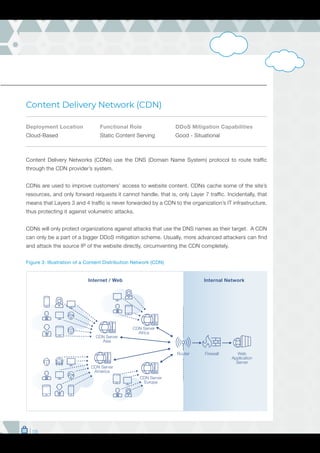
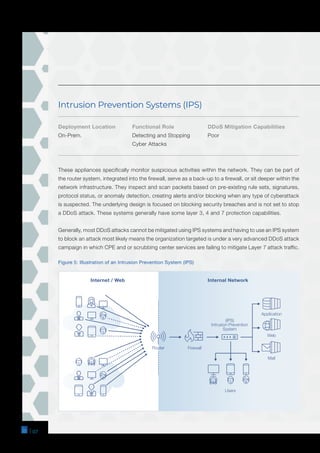
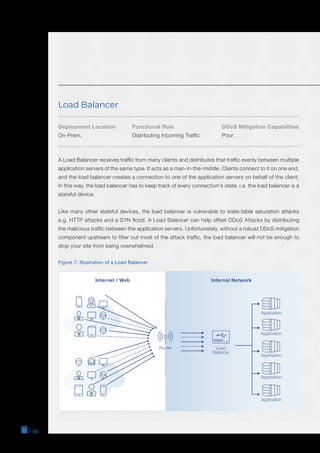
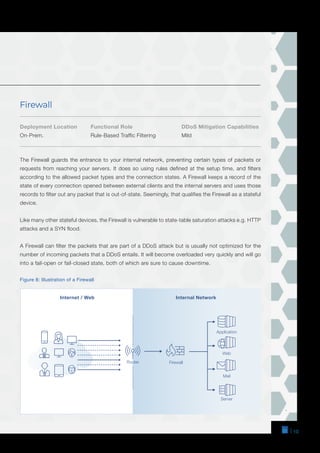
The document is a comprehensive guide on DDoS mitigation strategies, outlining the components and approaches, including cloud-based, on-premises, and hybrid solutions. It details various network devices critical for DDoS protection, such as scrubbing centers, CDNs, firewalls, and WAFs, highlighting their strengths and limitations. Additionally, it emphasizes the importance of properly configuring and stress-testing these systems to effectively safeguard against DDoS attacks.