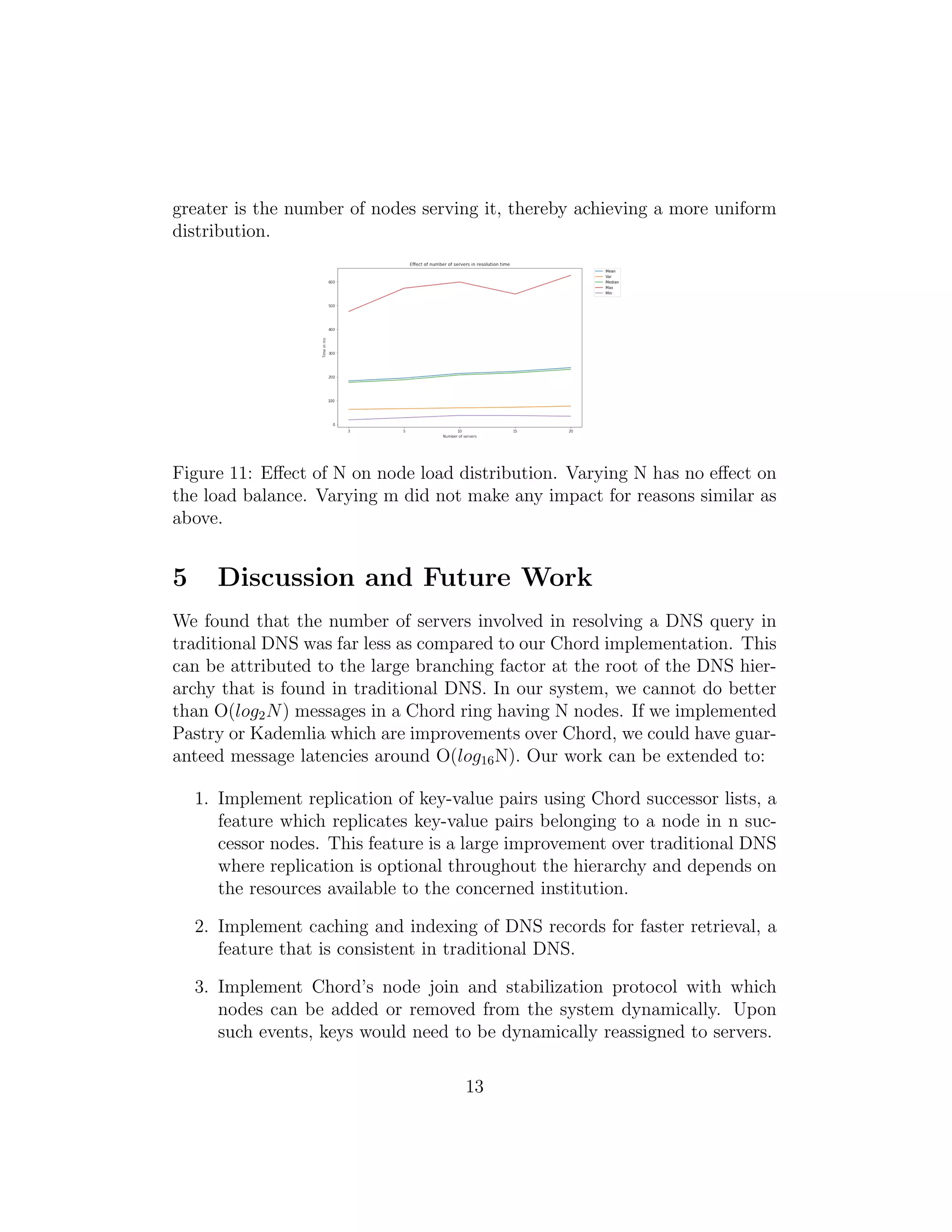
This project report describes implementing a peer-to-peer DNS service using Chord, a distributed hash table. Key points:
1. A P2P DNS eliminates hierarchy and single points of failure in traditional DNS, improving fault tolerance and load balancing.
2. The implementation maps DNS records to nodes in a Chord ring using consistent hashing. Record lookups are routed through the ring in O(logN) hops on average.
3. An evaluation compares the P2P DNS to traditional DNS, finding improvements in average query time and number of hops due to the lack of hierarchy. Network latency is simulated for fair comparison on a single machine testbed.
![Project report : DNS on Chord
https://github.com/soumyadeep2007/dns chord
Anupam Samanta, Jatin Garg, Soumyadeep Chakraborty
May 2018
1 Abstract
A peer to peer DNS service eliminates the coupling between service and
administration that is inherent in traditional hierarchical DNS. An over-
whelming source of incorrect replies or DNS query failures is borne out of
name-server administrative errors[1, 2]. Implementing such a service on top
of Chord [3], a distributed hash table, not only remedies this problem, but
also confers benefits such as fault-tolerance through replication and load-
balance. [4] explores this idea at considerable depth and we look towards it
as our main source of inspiration. Studies[2] have shown that as much as
18% of overall DNS traffic is towards the root servers. A peer-to-peer system
essentially eliminates any hierarchy whatsoever, and by extension, obviates
the need to have root or TLD servers, providing for better load balance. This
project, through an implementation of DNS on top of Chord, has provided
an opportunity to study the aforementioned aspects. The implementation
is done on top of a research language, DistAlgo [5], which provides powerful
primitives for distributed programming. A comparative performance study
of our DNS service with traditional DNS is performed. For our experiments,
we utilized a sizeable dataset of AAAA records which we obtained from the
Forward DNS dataset [6].
1](https://image.slidesharecdn.com/2018a-2-211116134914/75/2018a-1324654jhjkhkhkkjhk-1-2048.jpg)

![Figure 1: Chord ring having 10 nodes storing 5 keys
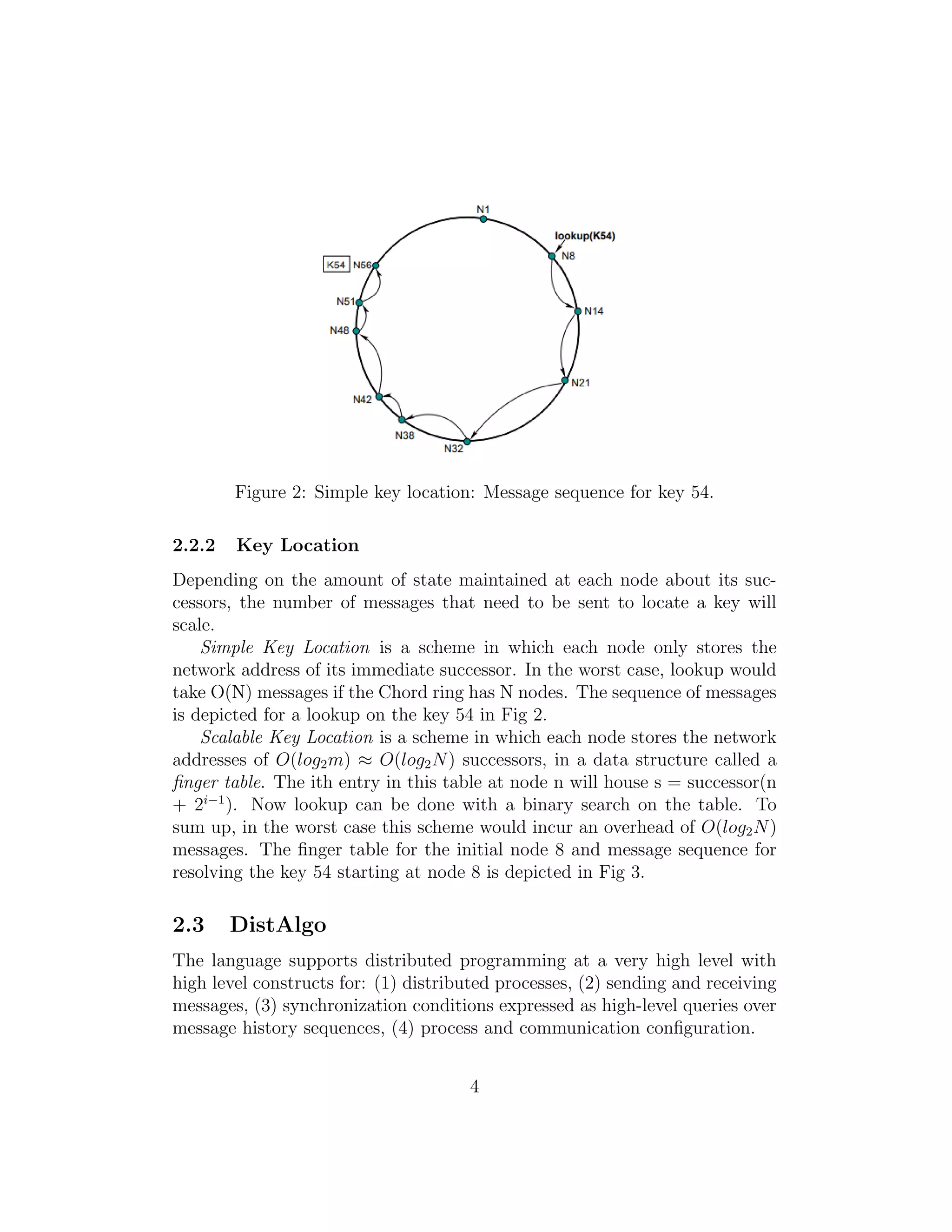
2.2.1 Consistent Hashing
Chord relies on Consistent Hashing[7] to assign keys to nodes. In this scheme,
both keys for data and for nodes are hashed to different positions in an
identifier circle, with keys ranging from 0 to 2m
− 1. The circle represents a
key space of 2m
keys. Each position in the ring is represented as an m-bit
identifier. Please note that throughout this report, we have referred to keys
and identifiers interchangeably. Identifiers are obtained as follows:
1. Identifiers for data are obtained by hashing their keys with SHA-1[8].
2. Identifiers for nodes are obtained by hashing their IP addresses with
SHA-1.
To avoid collisions in the assignment of identifiers, techniques such as
Universal Hashing can be adopted.
Consistent hashing works in the following manner: Identifiers are ordered
in the circle modulo 2m
. Key k is assigned to the first node whose identifier
either is equal to k or succeeds k in the identifier circle in the clockwise
direction. Such a node is defined as successor(k). Similarly, predecessor(k)
can be defined. As depicted in Fig. 1, the successor of K10 is N14 since 14
follows 10 in the Chord ring. In general, for a node with identifier i will hold
keys lying in the interval: (predecessor(k), i].
3](https://image.slidesharecdn.com/2018a-2-211116134914/75/2018a-1324654jhjkhkhkkjhk-3-2048.jpg)
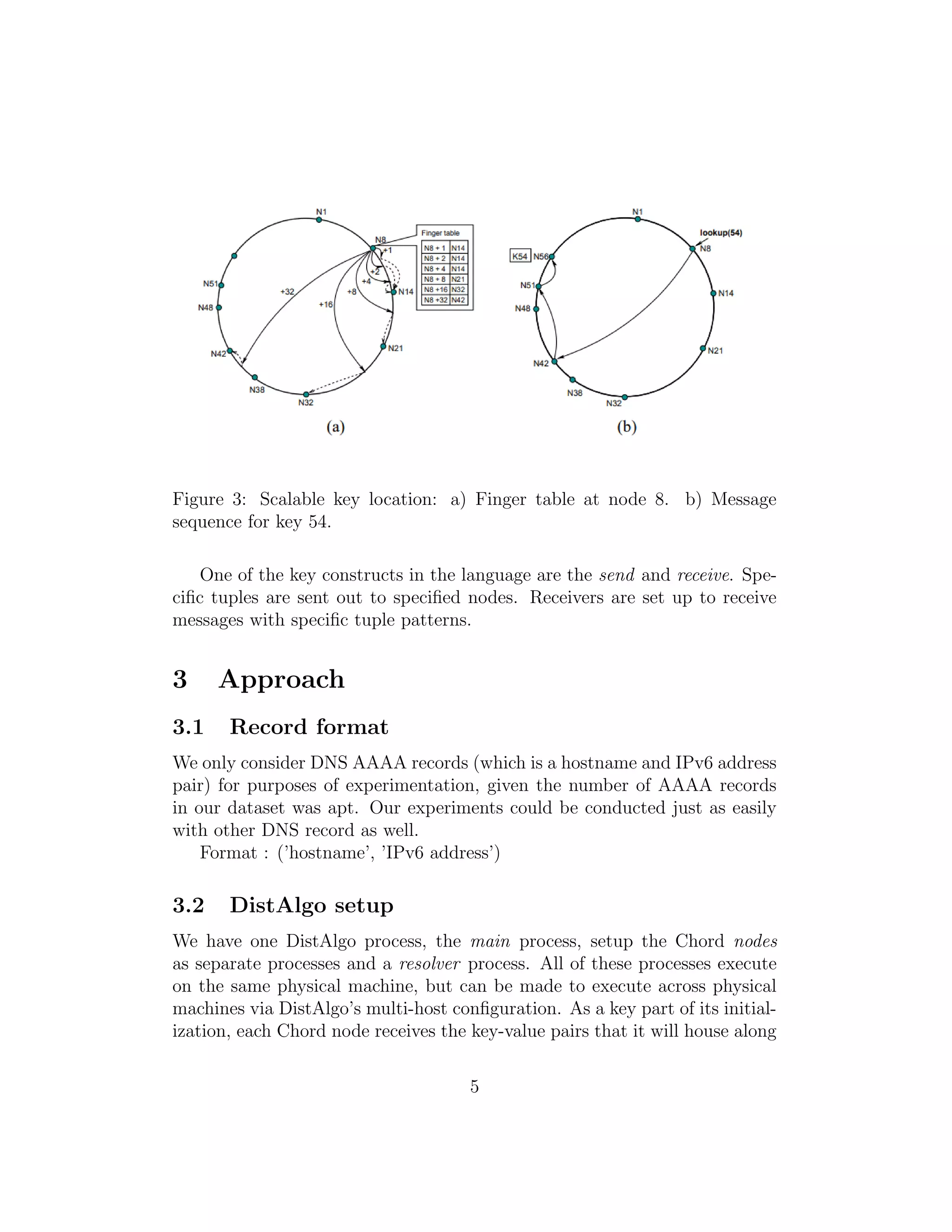

![Figure 4: A typical workflow of messages for resolving the key ’kx’
4 Evaluation
4.1 Experimental setup
DistAlgo can be executed over both reliable (TCP) and unreliable (UDP)
channels via a configuration parameter. We chose to do both and we have
compared their performance.
The Forward DNS dataset was easy to use and we applied it both on our
Chord implementation and traditional DNS with the help of an online Dig
tool[9]. We conducted the experiments with a random subset of these records.
We randomly sampled 10,000 AAAA DNS records from the dataset. These
10,000 records have 8328 2nd level domains, following a zipfian distribution.
4.2 Performance Study
For the performance study, we collected the following metrics: (1) average
query resolution time (2) average number of DNS servers (hops) involved in
7](https://image.slidesharecdn.com/2018a-2-211116134914/75/2018a-1324654jhjkhkhkkjhk-7-2048.jpg)