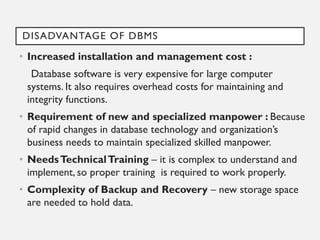
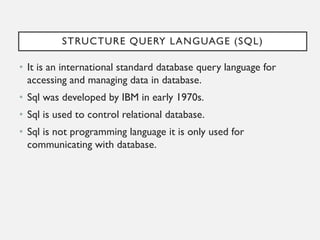
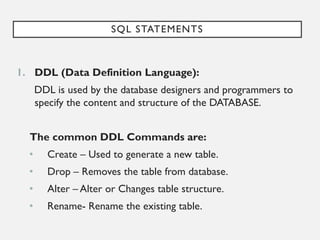
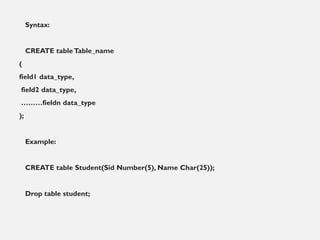
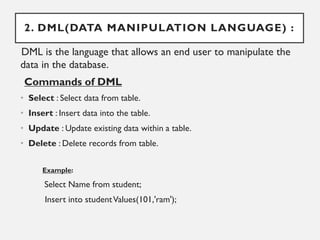
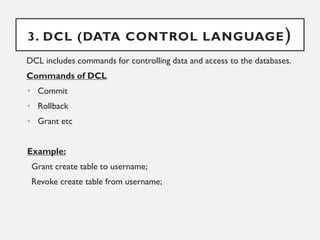
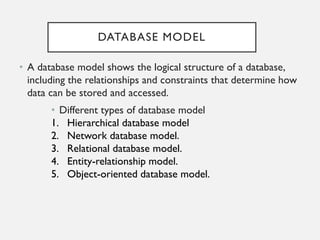
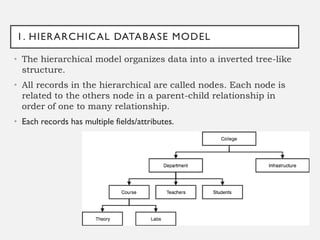
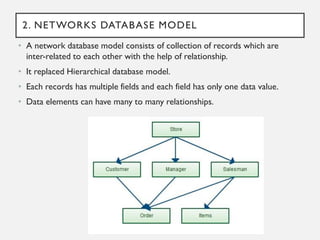
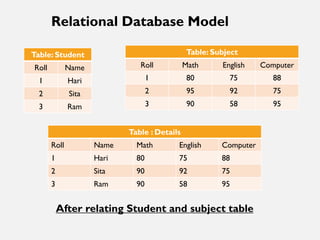
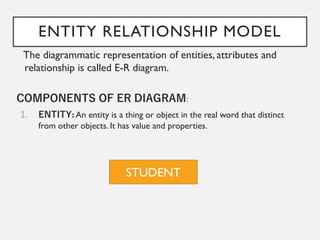
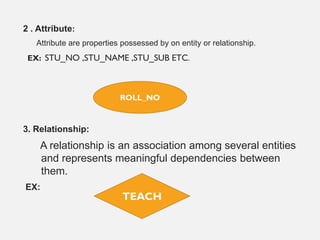
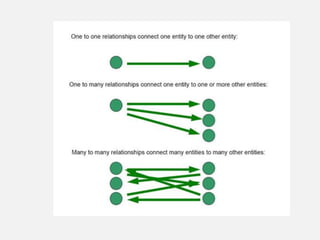
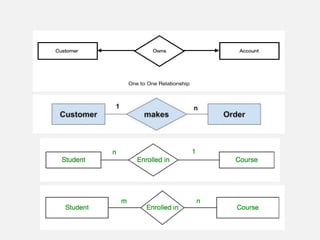
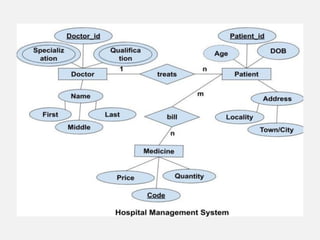
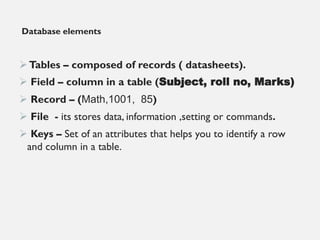
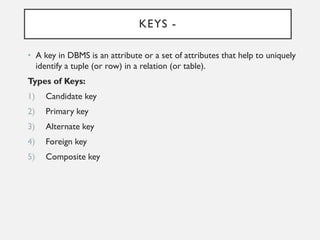
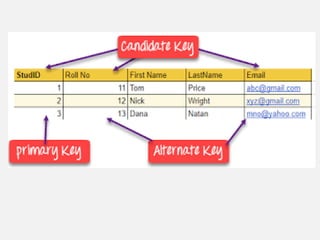
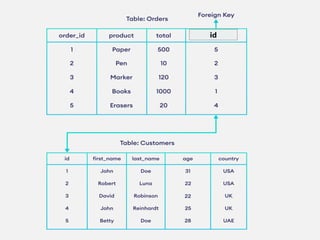
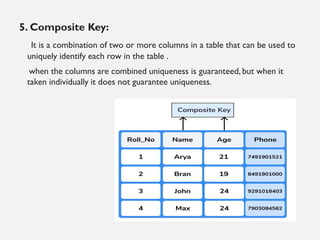
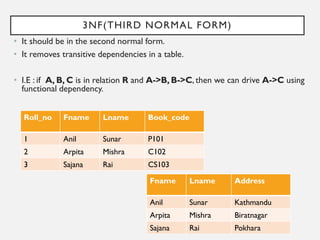
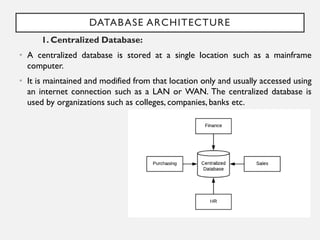
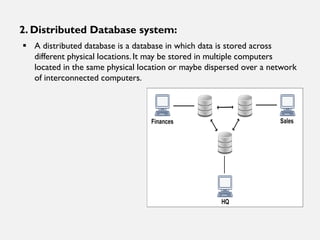
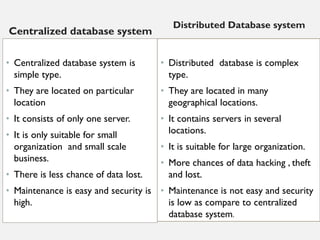
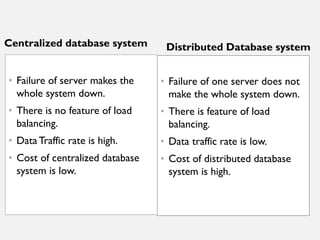
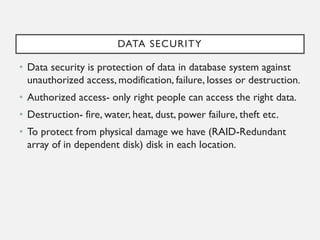
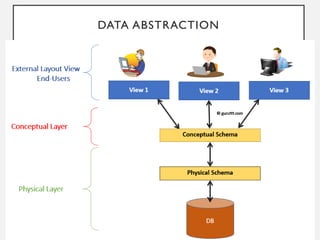
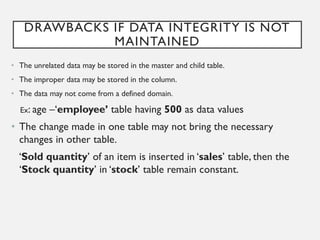
This document provides an overview of database concepts including data, information, databases, database management systems (DBMS), structured query language (SQL), database models, database architecture, database security, and data integrity. It defines key terms and explains topics such as data normalization, database activities, advantages and disadvantages of DBMS, SQL statements, entity relationship diagrams, and database constraints. The document is an introductory guide to fundamental database concepts.