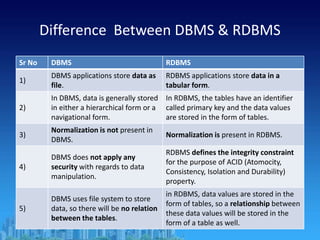
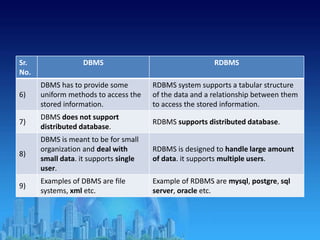
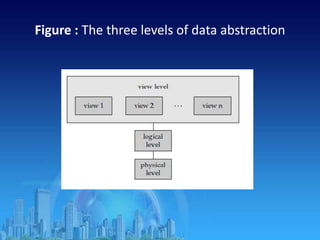
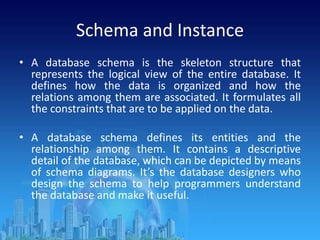
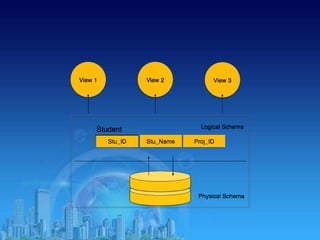
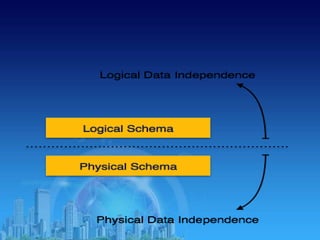
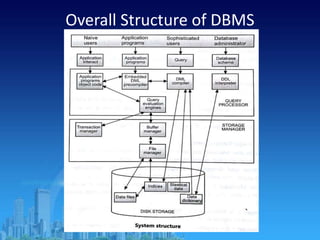
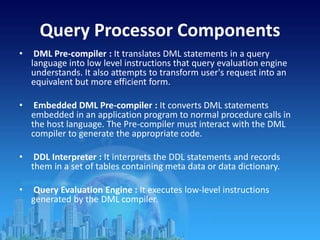
This document provides an overview of relational database management systems (RDBMS). It defines key terms like data, database, DBMS, and discusses the disadvantages of file processing systems and advantages of DBMS. It explains concepts like data abstraction, database languages including DDL, DML, DCL. It also describes database schema and instance, data independence, and the overall architecture of a DBMS including components like the query processor and storage manager.