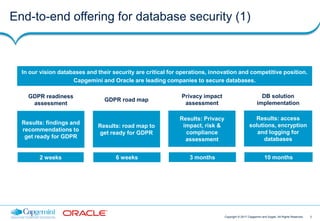
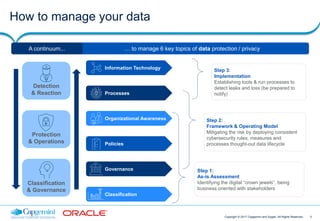
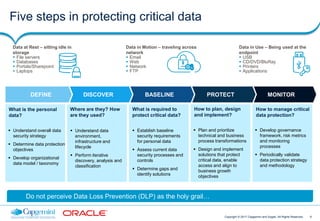
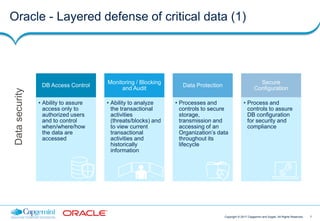
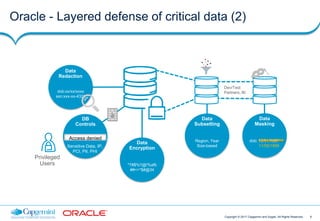
This document discusses Capgemini and Sogeti's end-to-end offering for database security and GDPR compliance. It outlines a four-phase approach including a GDPR readiness assessment, roadmap development, privacy impact assessment, and implementing database security solutions. Each phase has defined activities, timelines, and results to help organizations assess their GDPR compliance and secure databases containing personal data. The offering is designed to help organizations address new accountability and security requirements under the upcoming GDPR regulation.