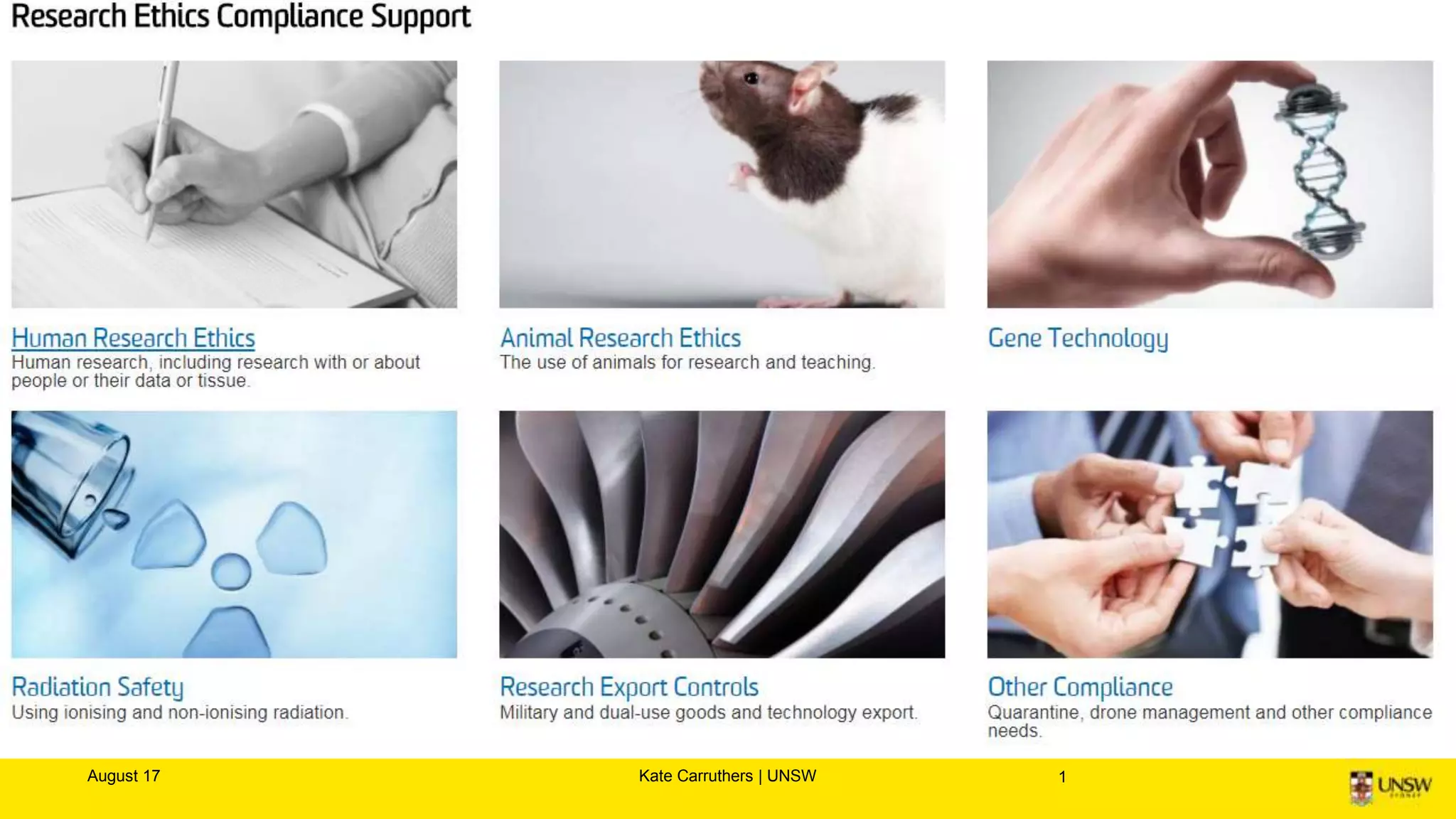
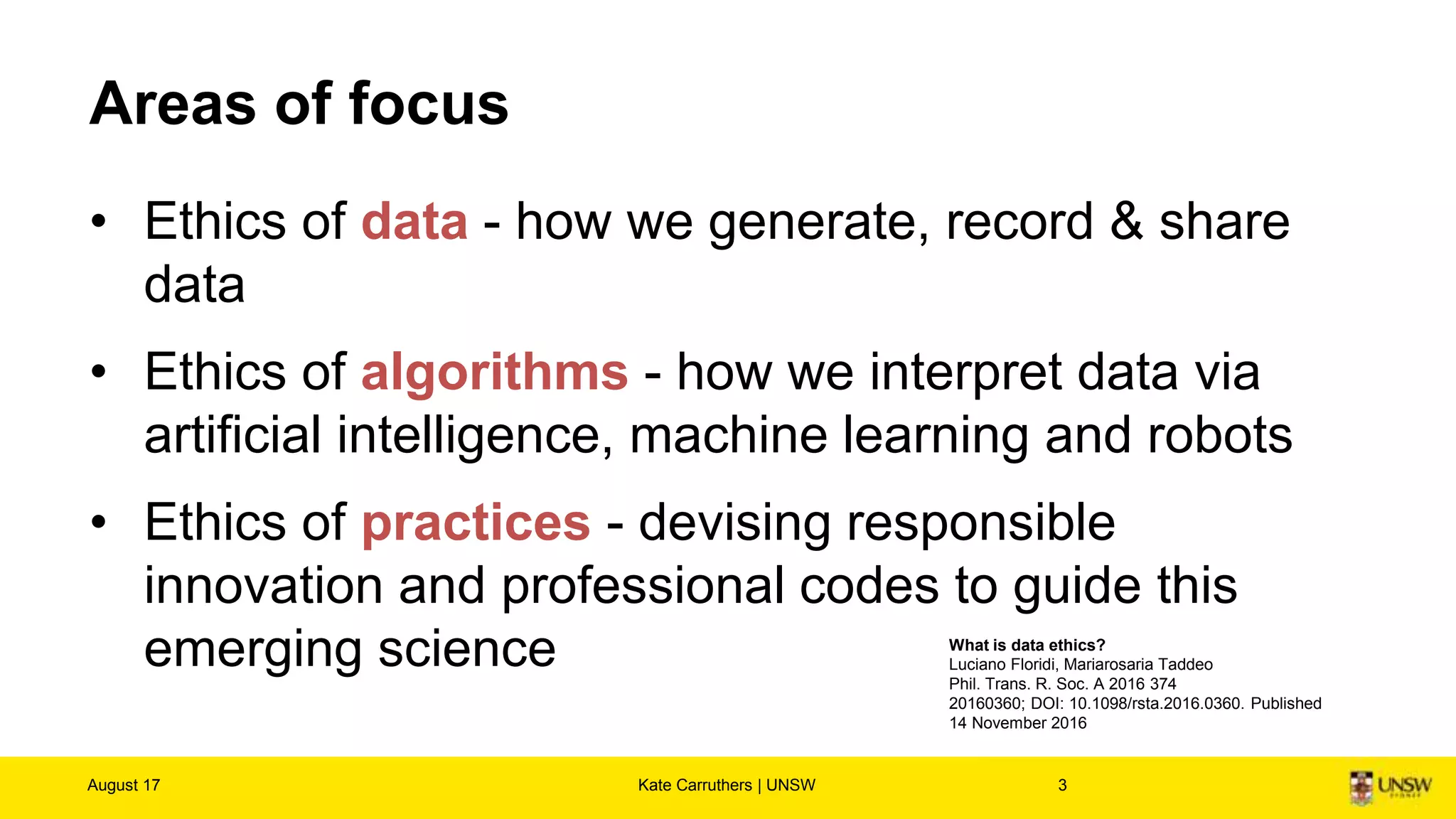
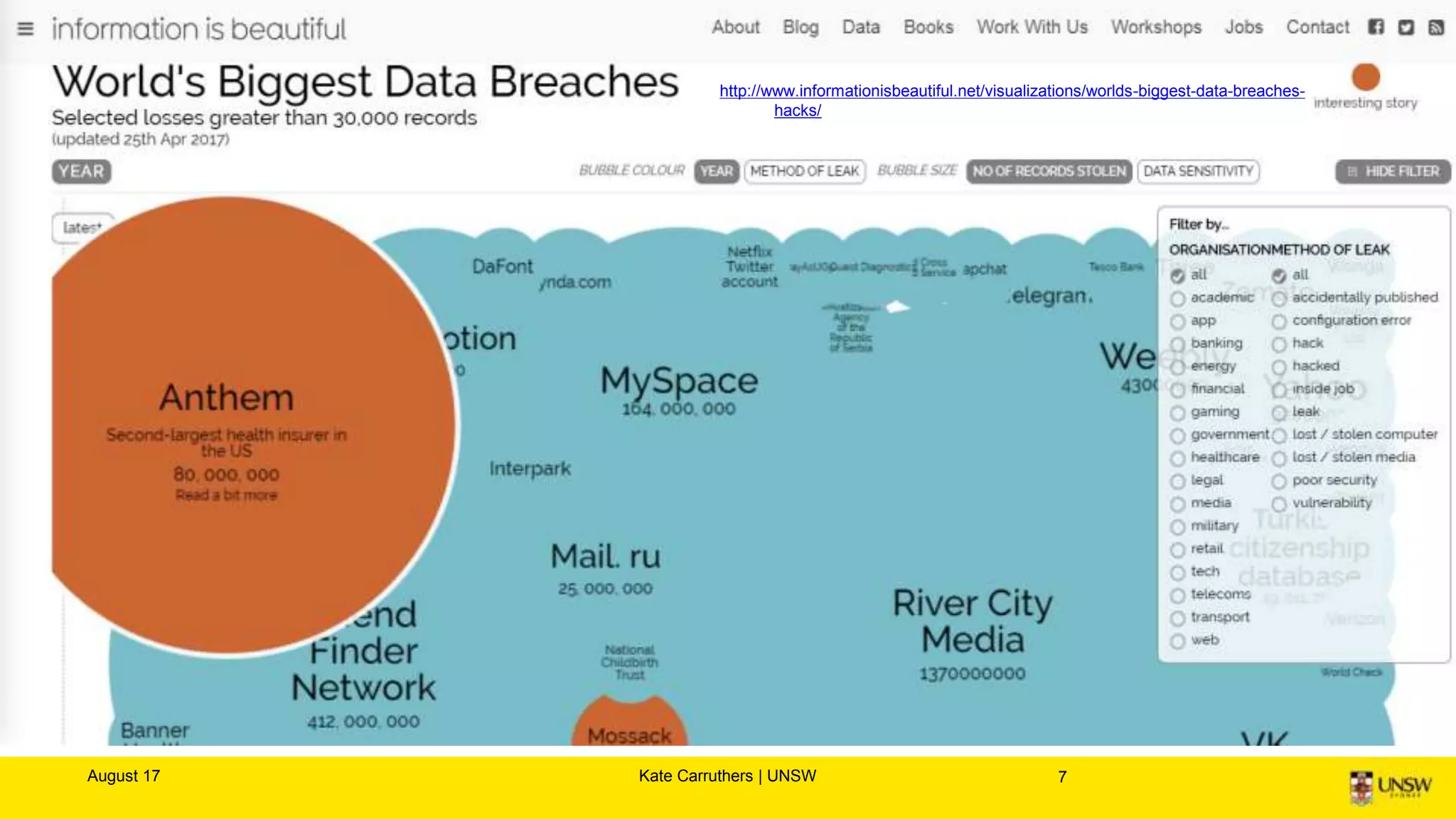
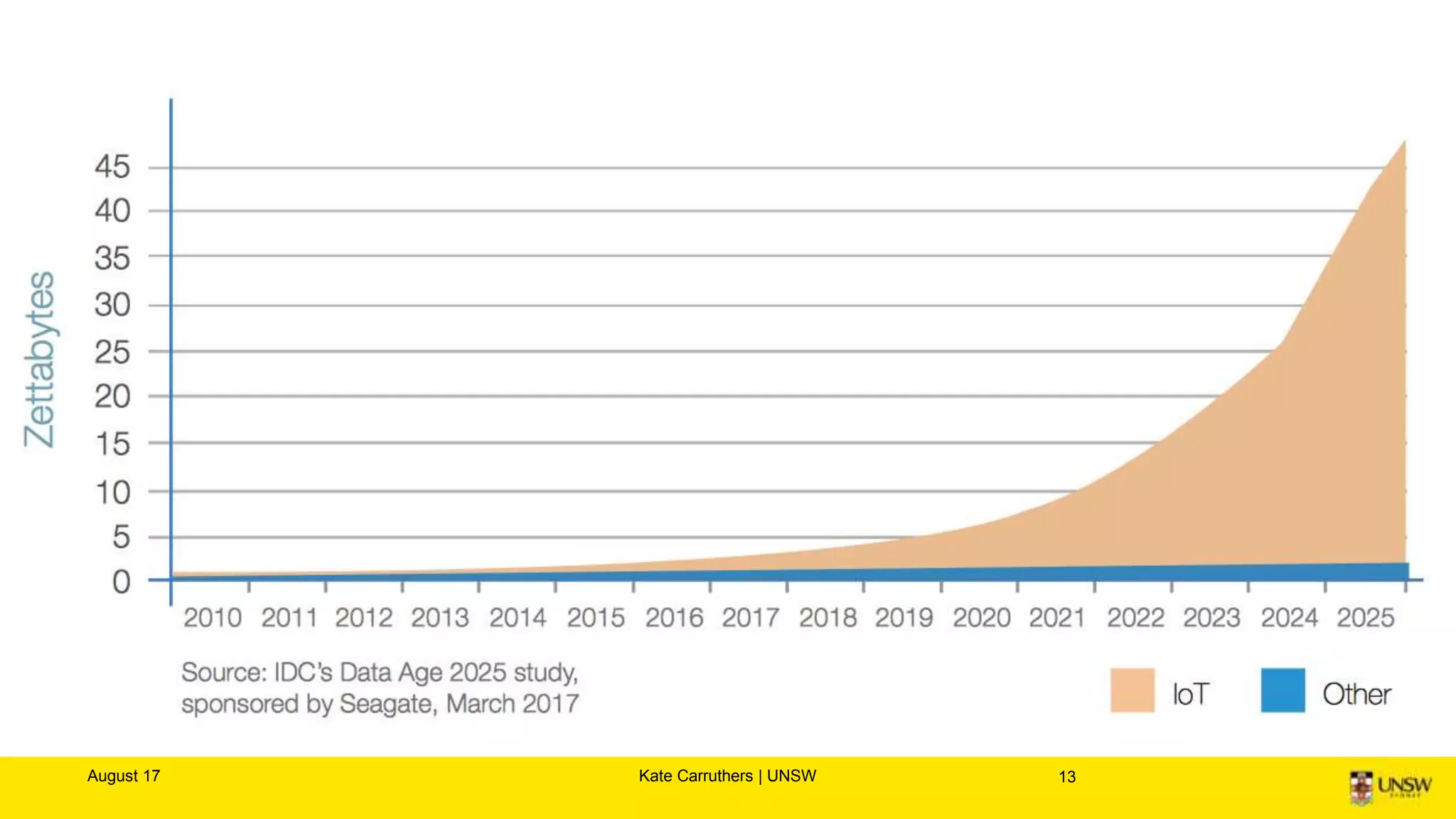
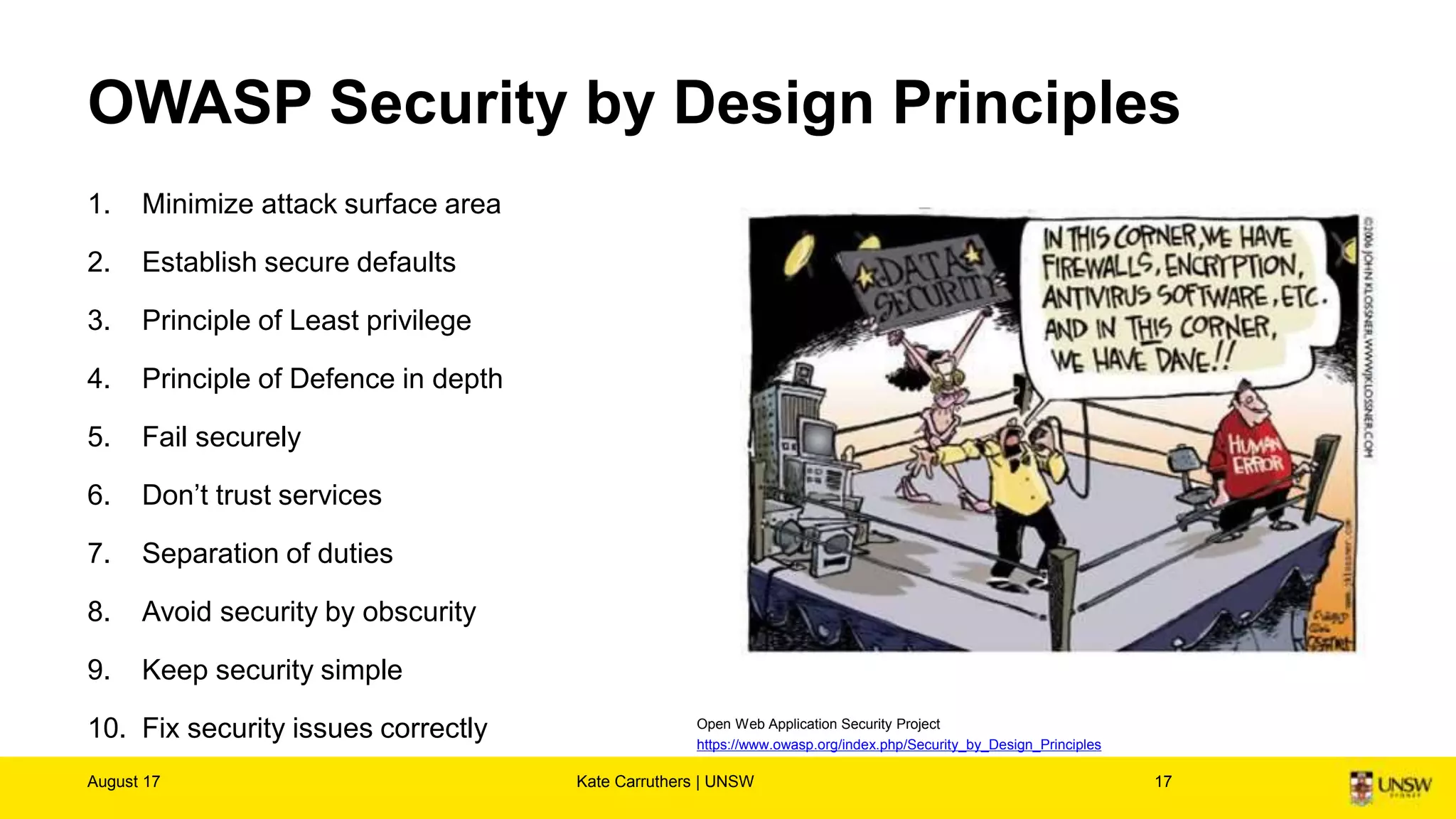
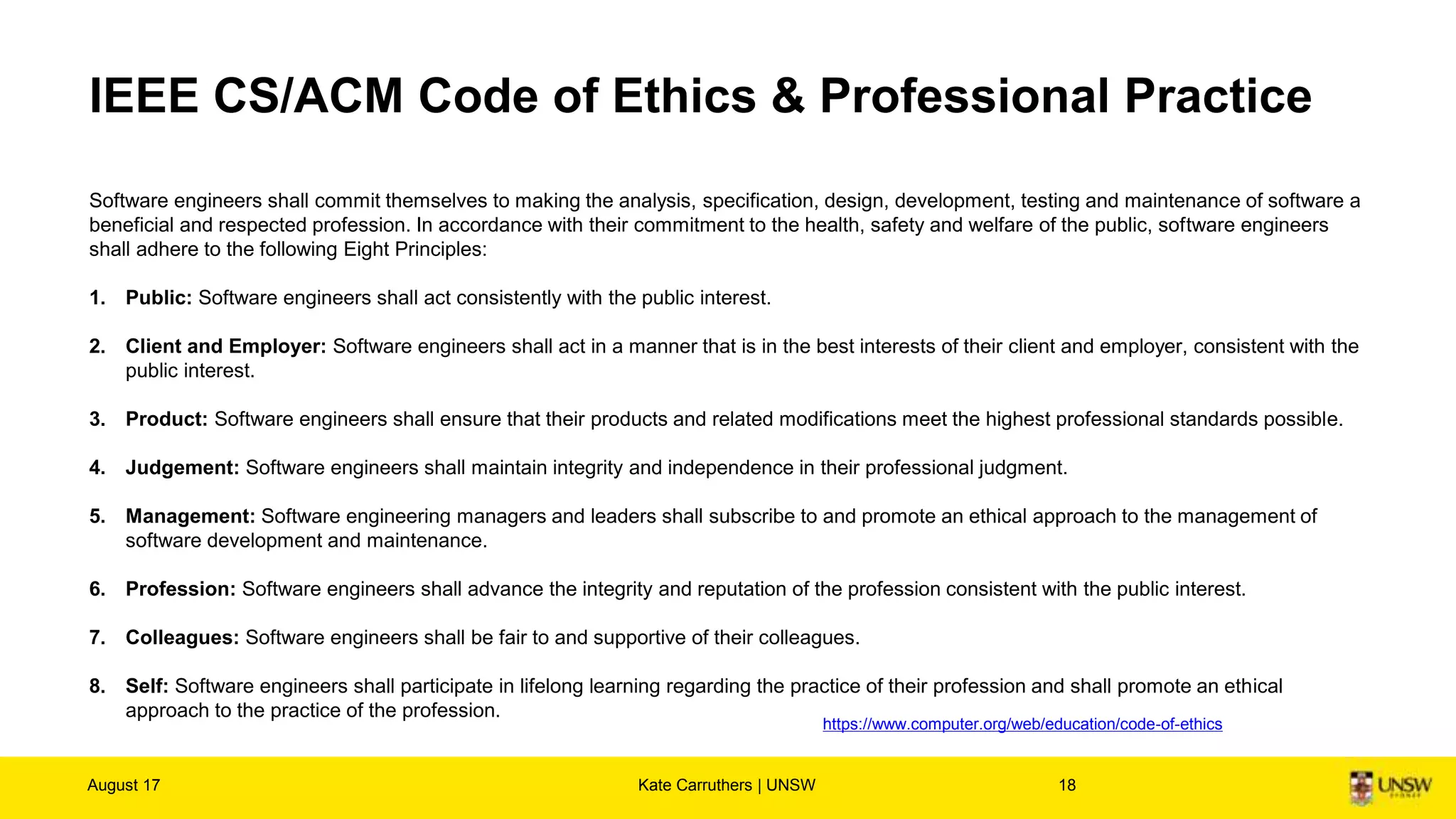
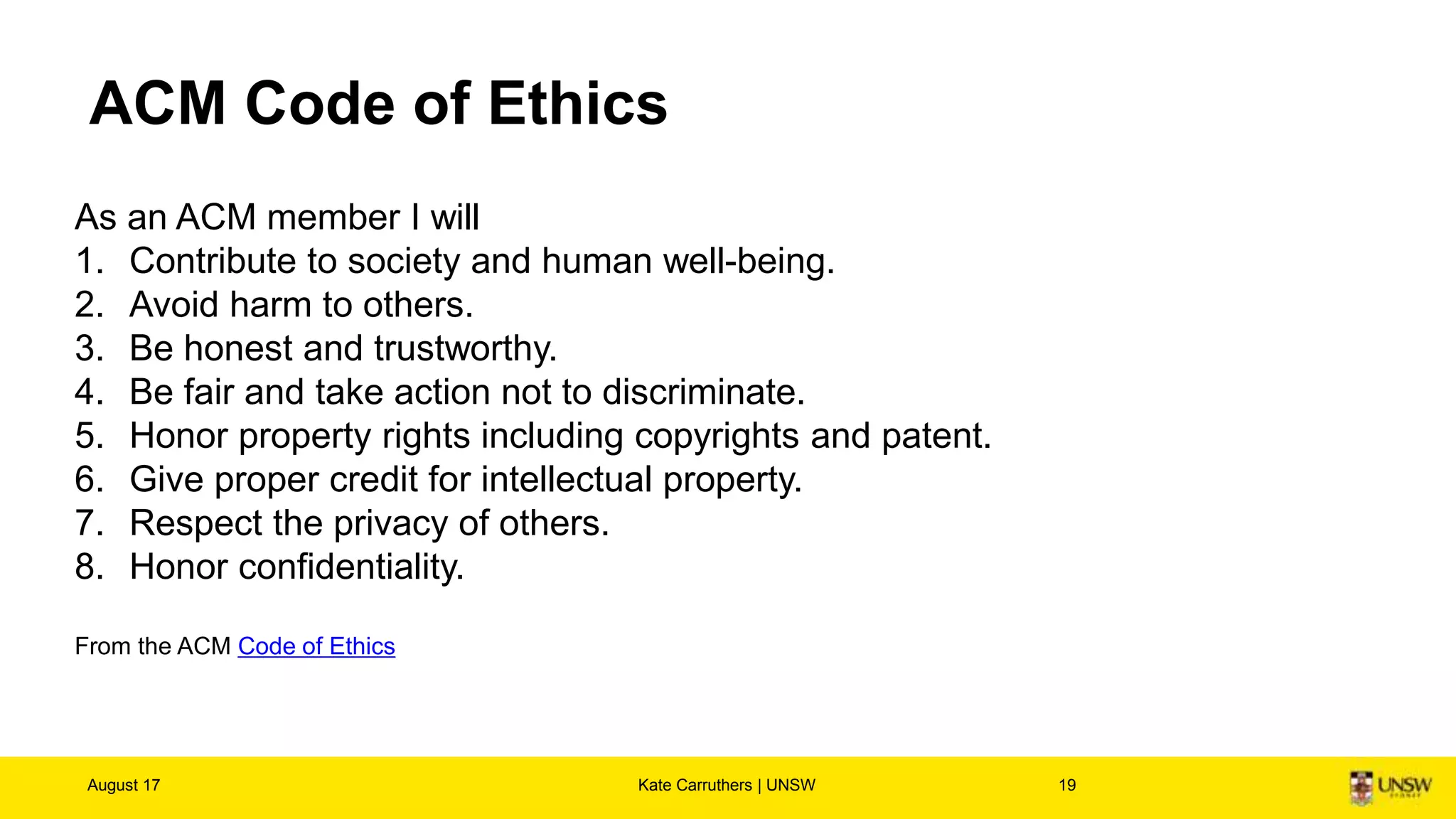
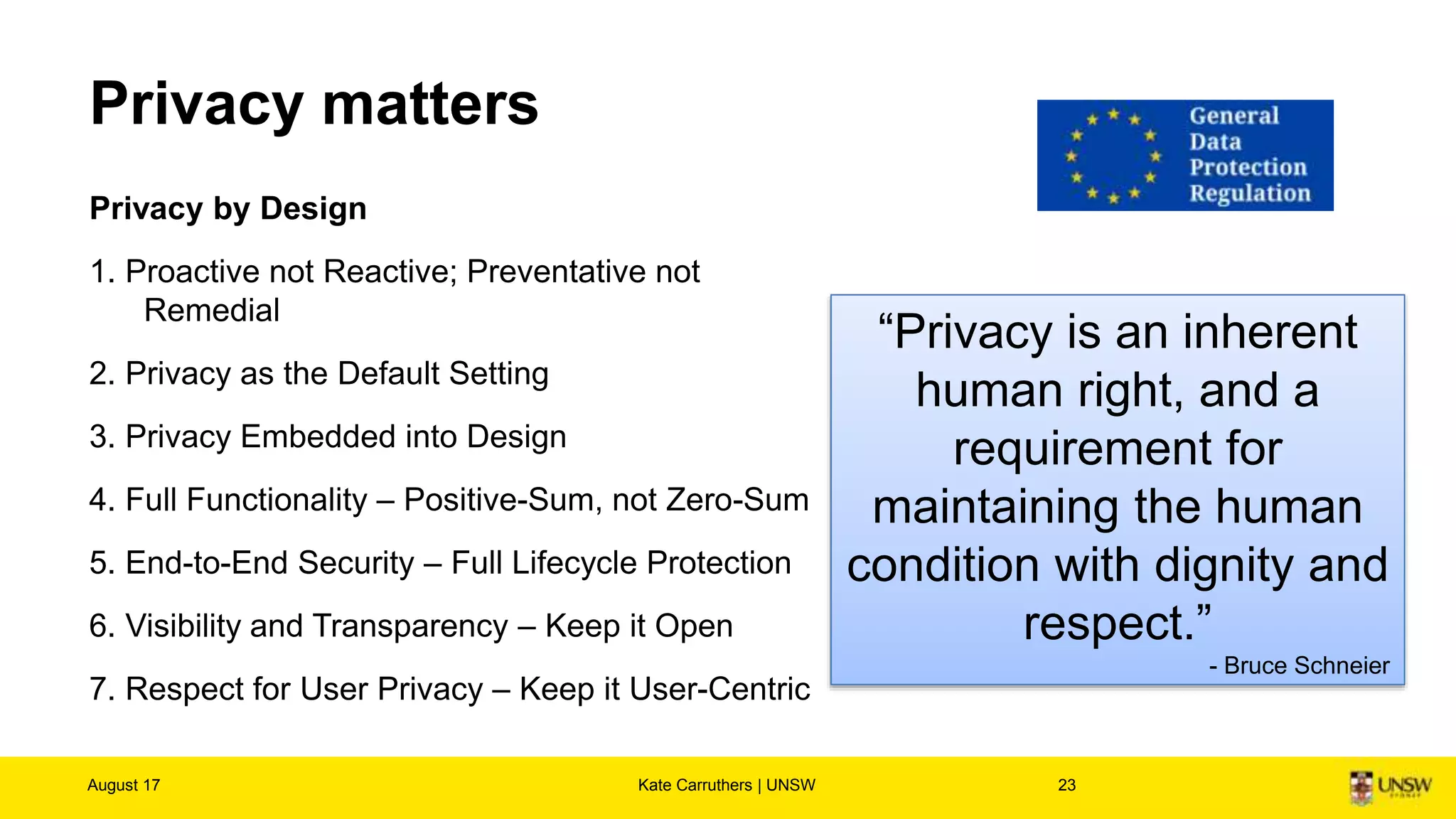
The document discusses the importance of digital ethics, emphasizing moral principles guiding data use, algorithm practices, and responsible innovation. It outlines key ethical guidelines, including respect for individuals behind data, the significance of privacy, and transparency in data practices. Additionally, it highlights the need for continuous dialogue on ethics in technology and has various resources for further exploration of data ethics.