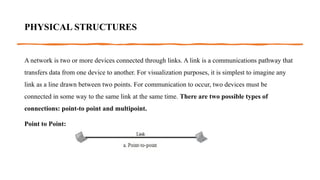
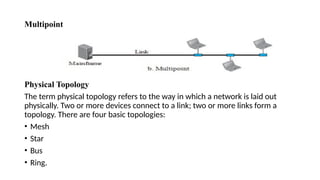
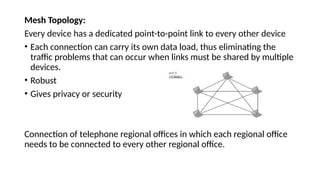
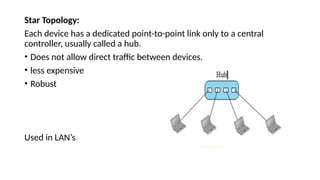
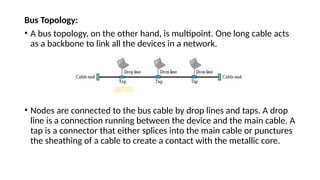
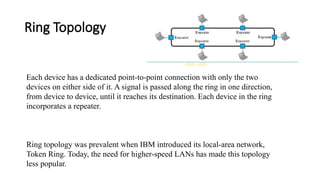
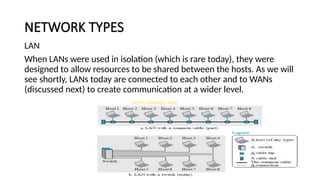
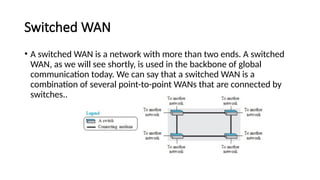
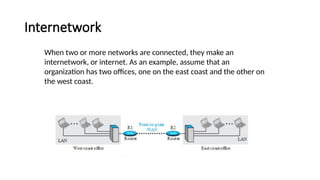
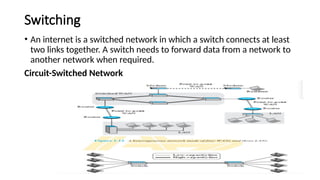
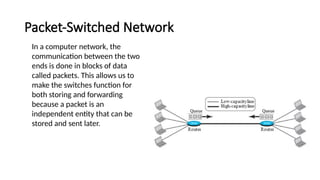
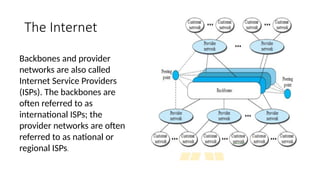
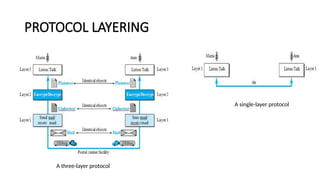
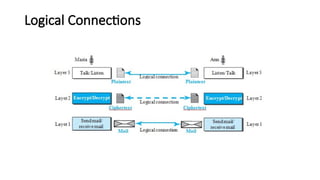
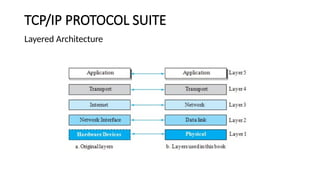
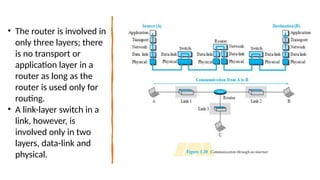
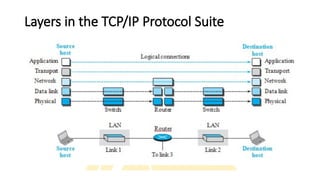
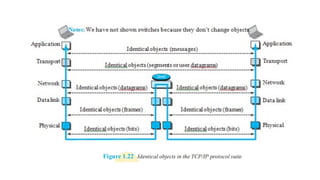
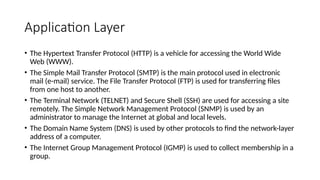
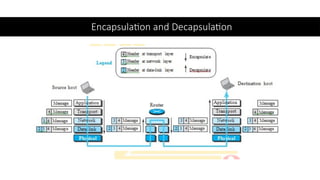
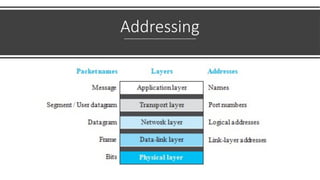
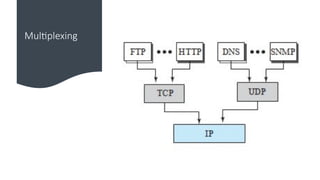
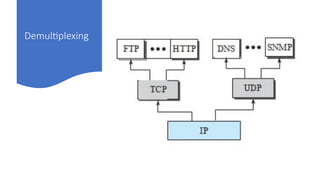
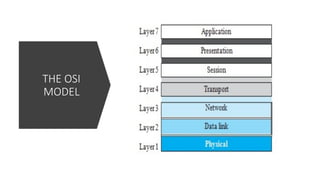
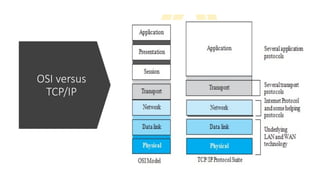
The document provides a comprehensive overview of data communications, including definitions and characteristics such as delivery, accuracy, timeliness, and jitter. It discusses elements like messages, senders, receivers, protocols, and the representation of different types of data (text, images, audio, video). Additionally, it outlines network structures, types (LAN and WAN), protocol layering, and compares the OSI model to the TCP/IP model.