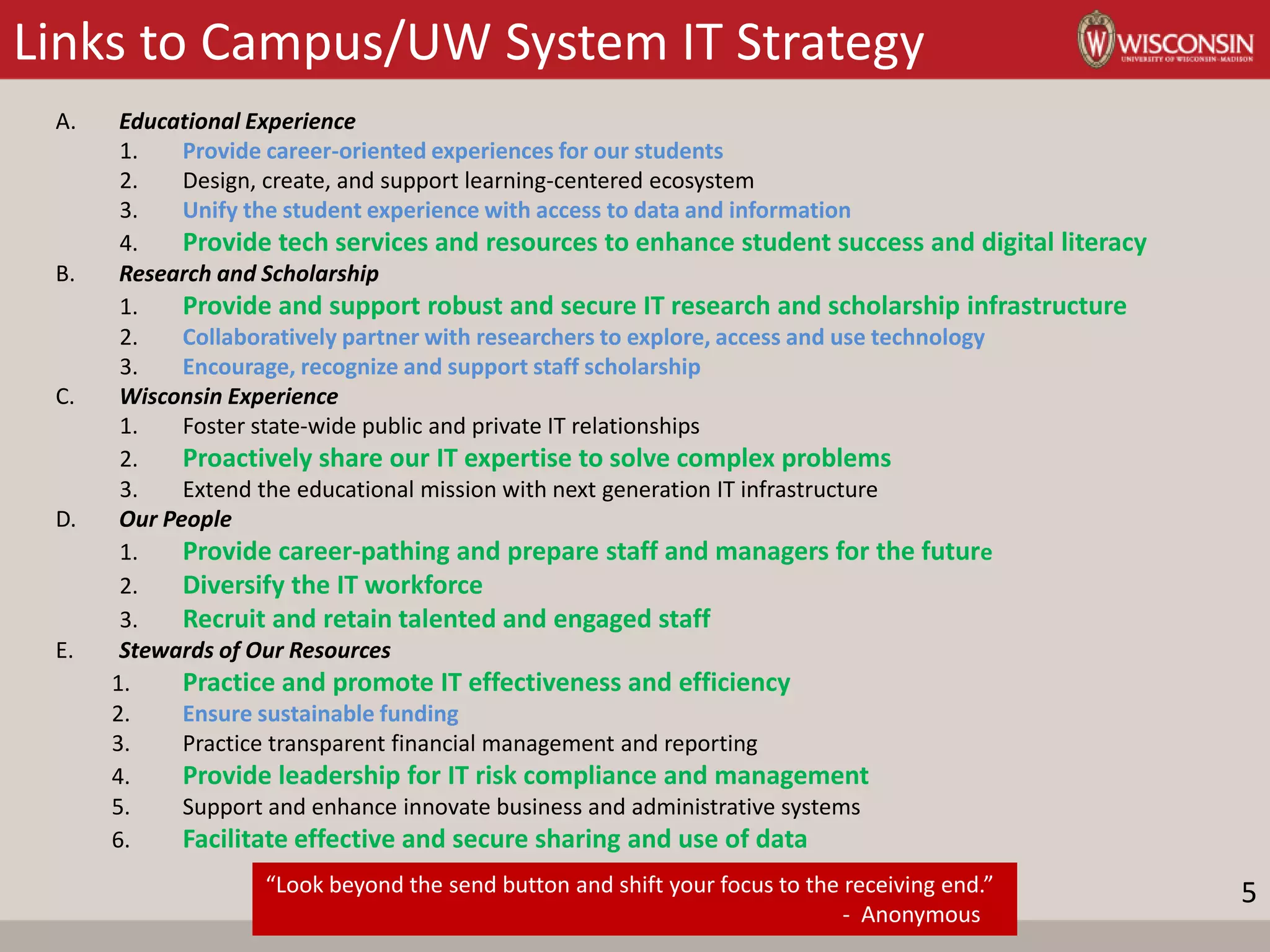
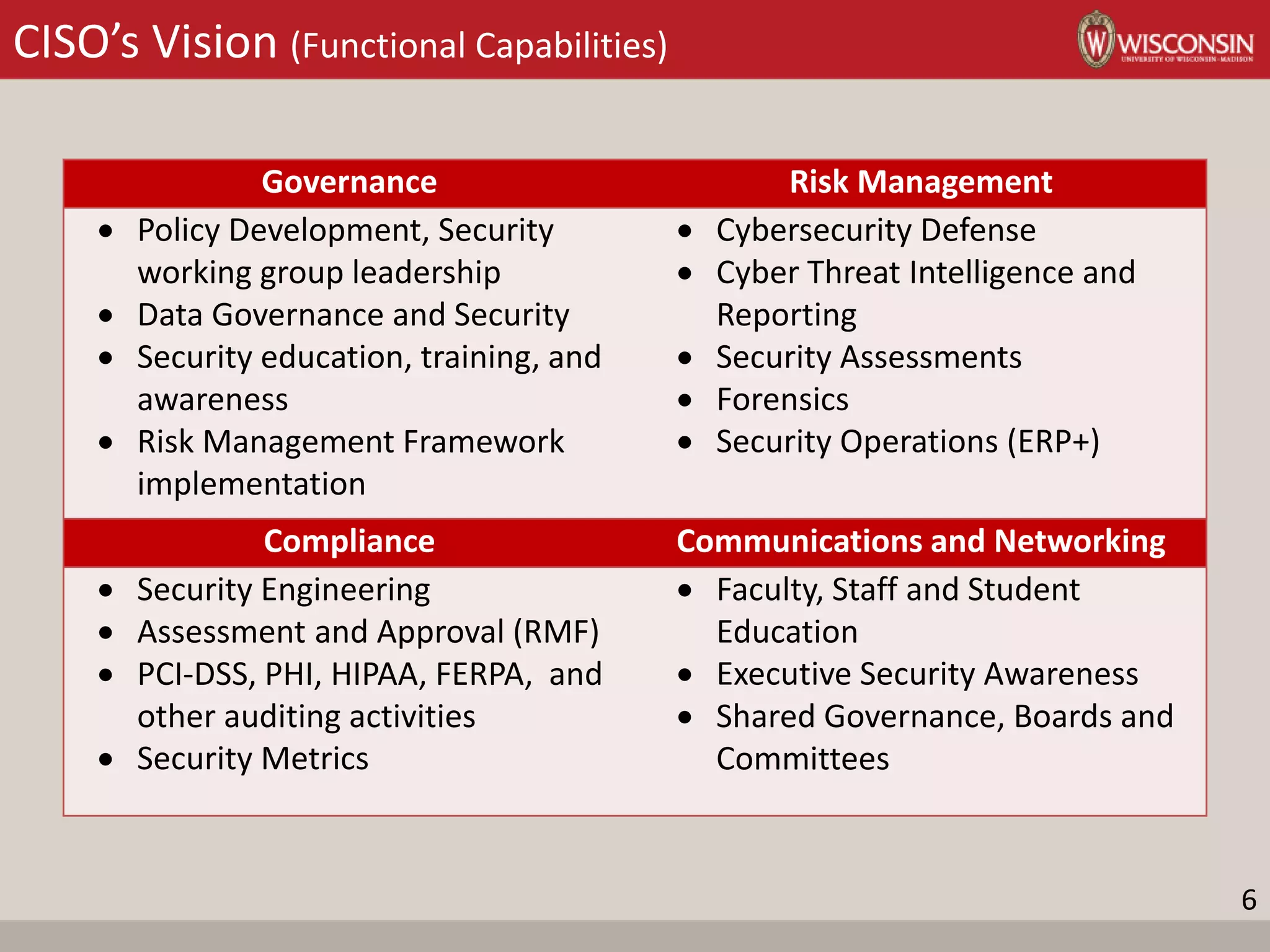
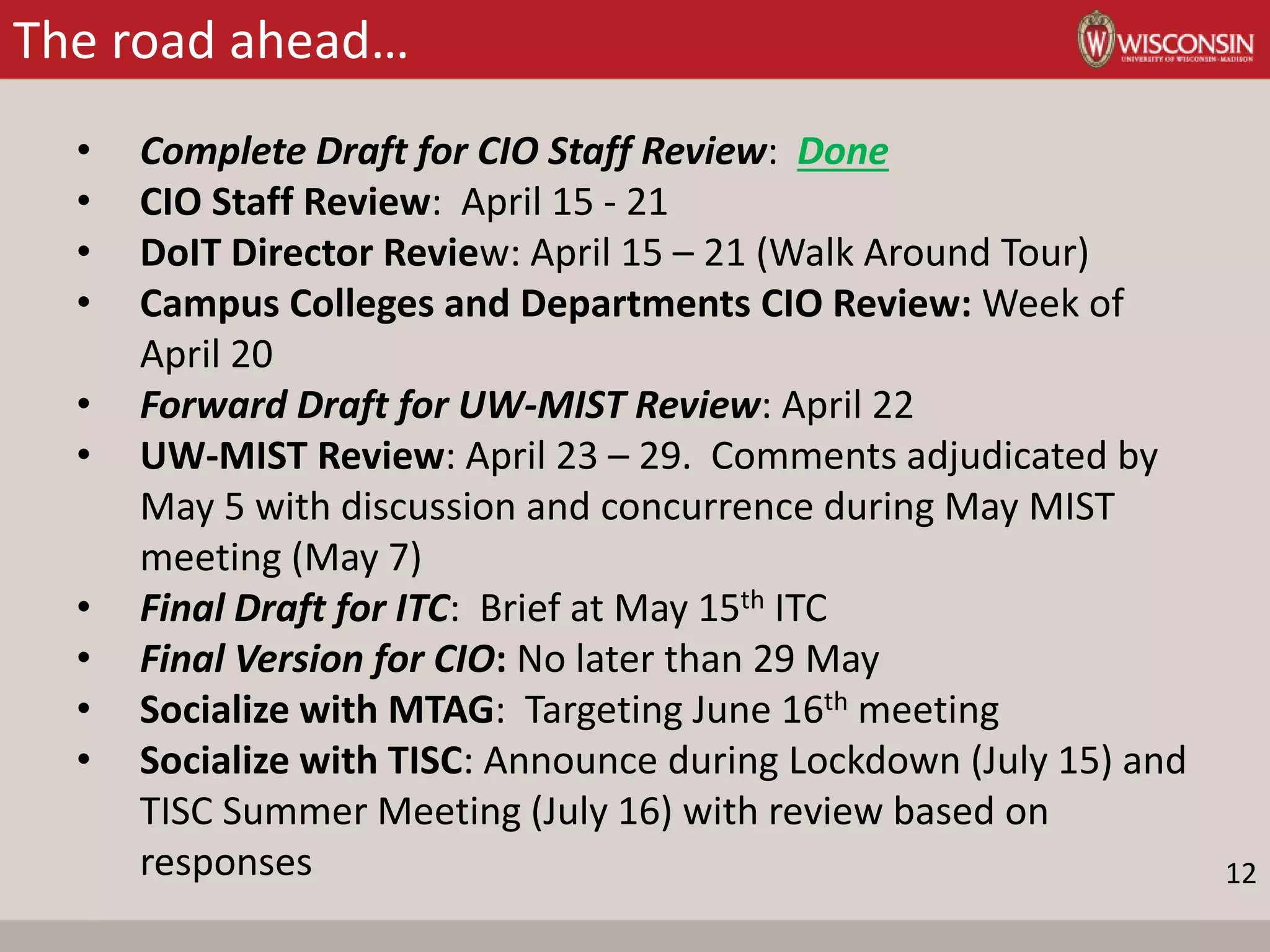
This document provides a summary of Bob Turner's cybersecurity strategic plan briefing to the Information Technology Committee. The strategic plan aims to improve cybersecurity at UW-Madison through establishing a risk management framework, promoting cyber hygiene, facilitating incident response, and consolidating incident response capabilities. The plan aligns with UW-Madison's strategic priorities of education, research, community engagement, diversity, and resource stewardship. Key elements of the cybersecurity strategy include implementing data governance, establishing a risk management framework, improving user competence through training, consolidating security operations, enhancing threat intelligence, and establishing collaborative partnerships. The roadmap provided outlines the review and socialization process for the strategic plan.