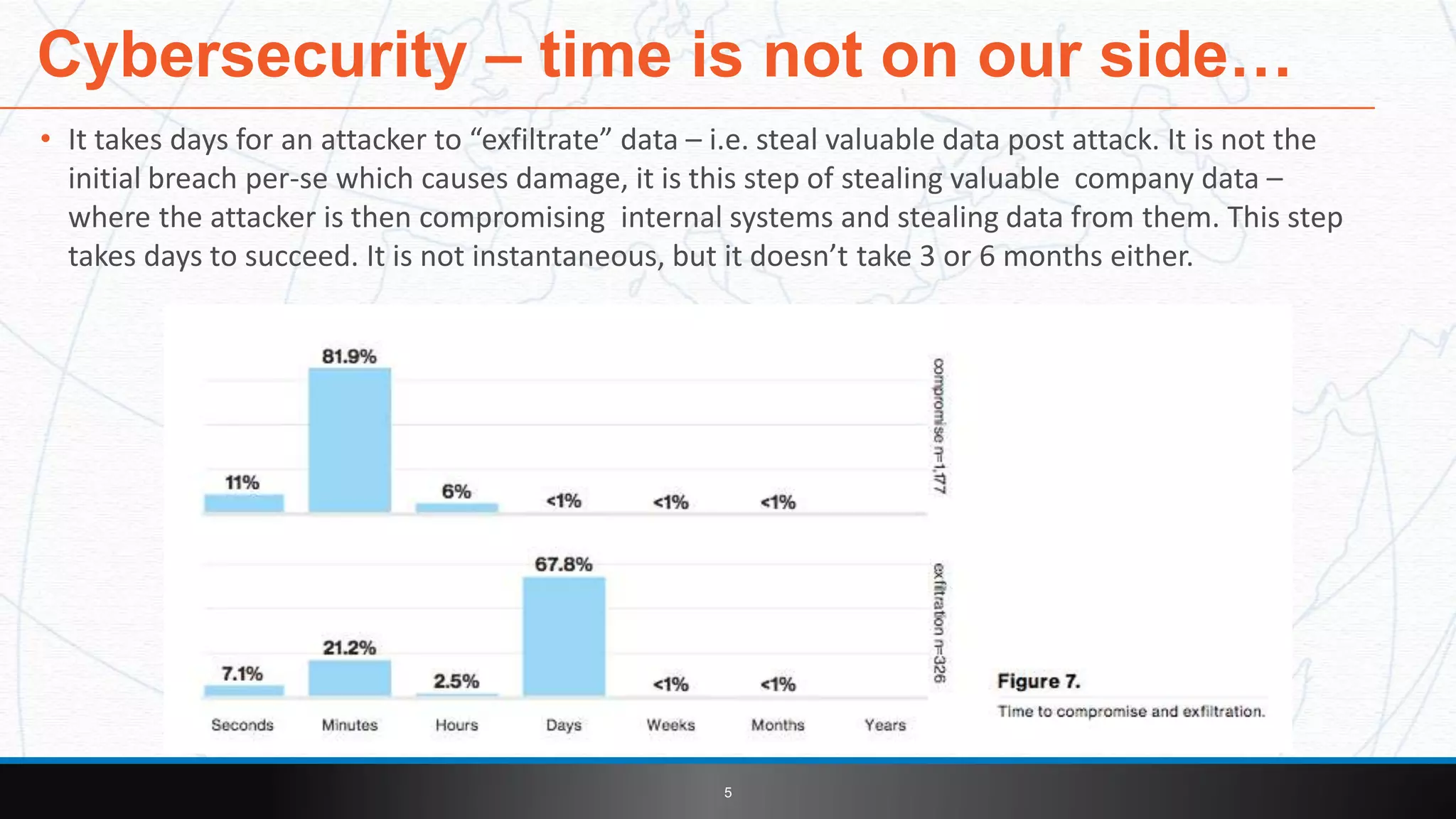
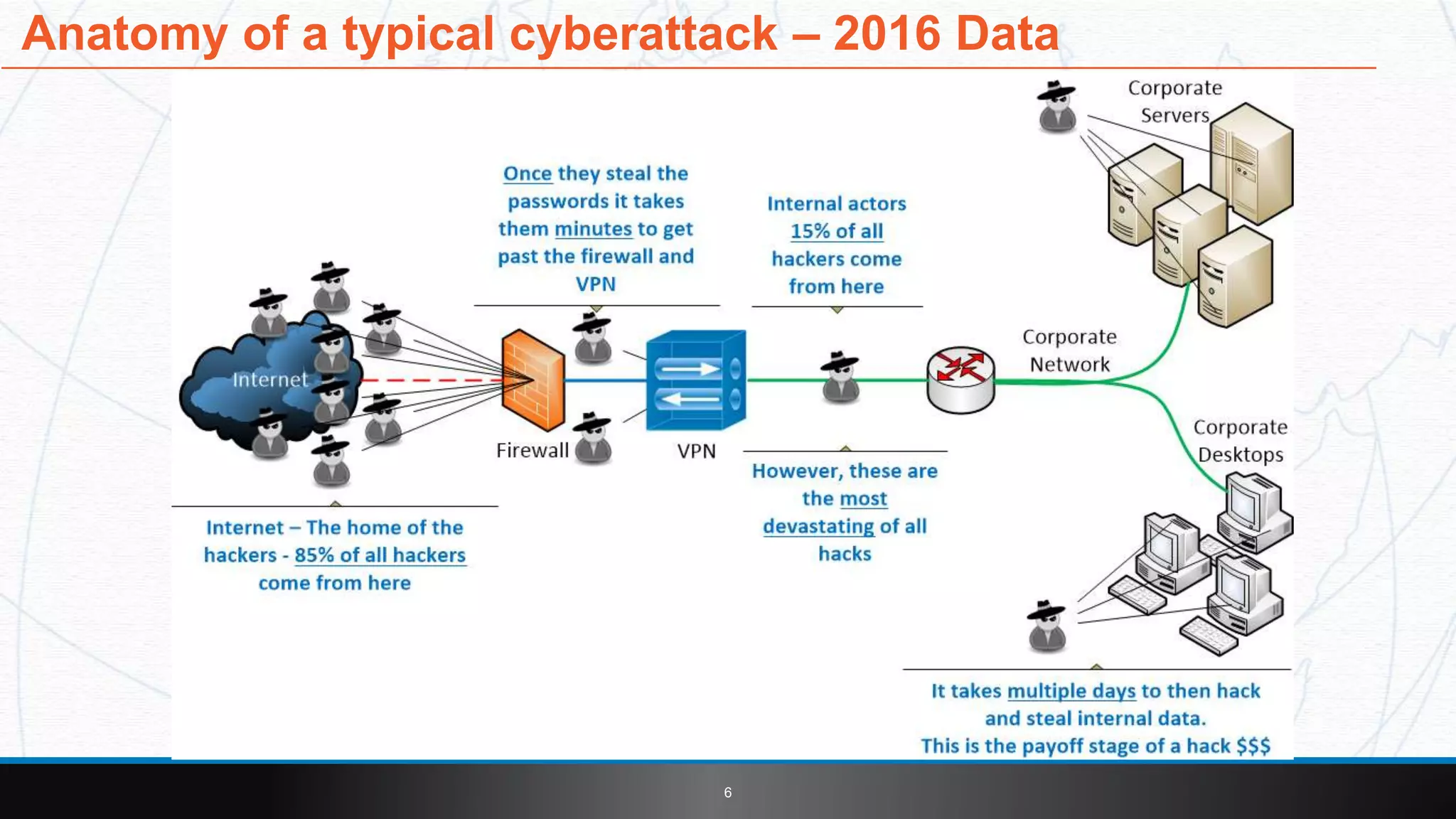
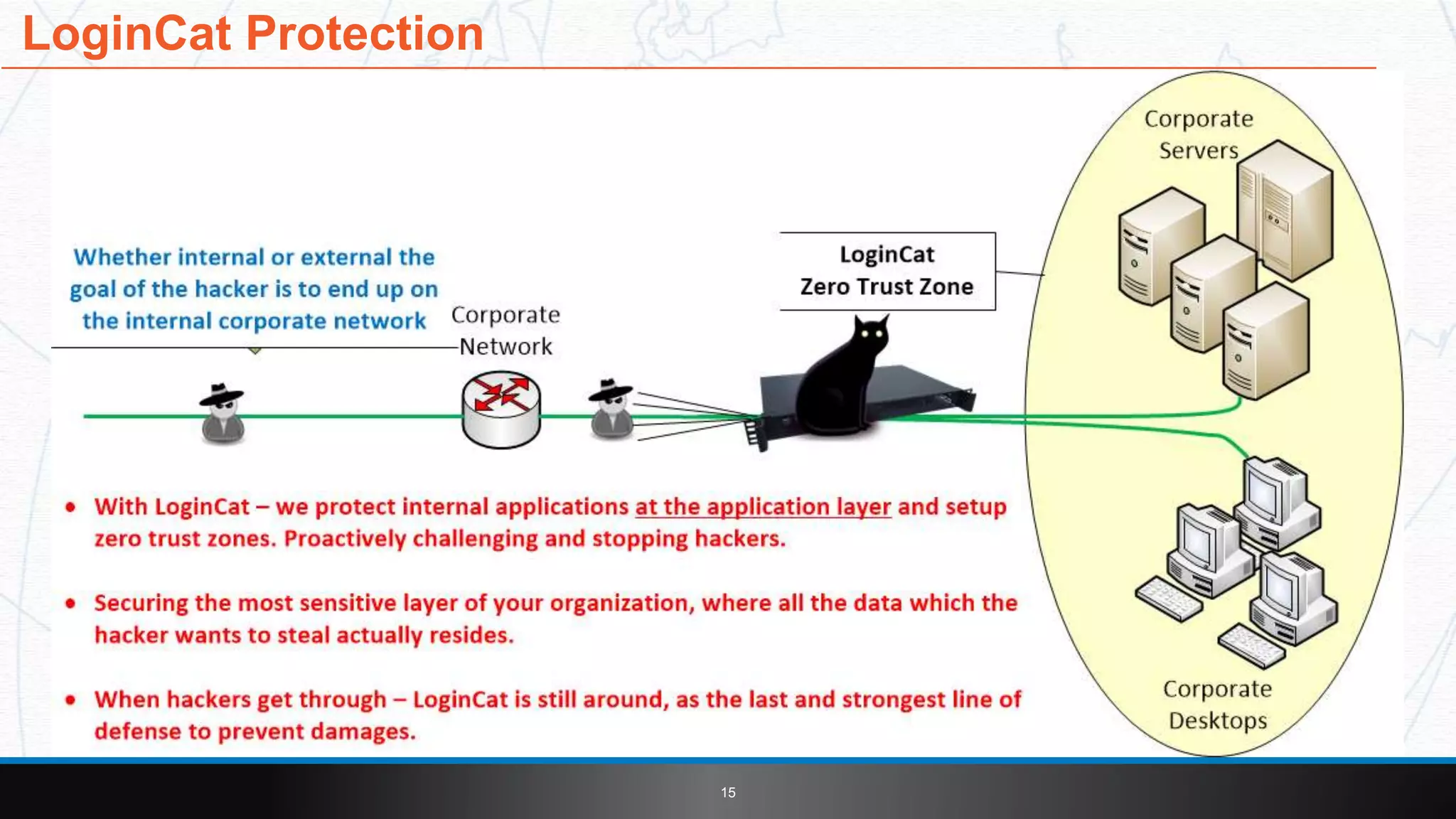
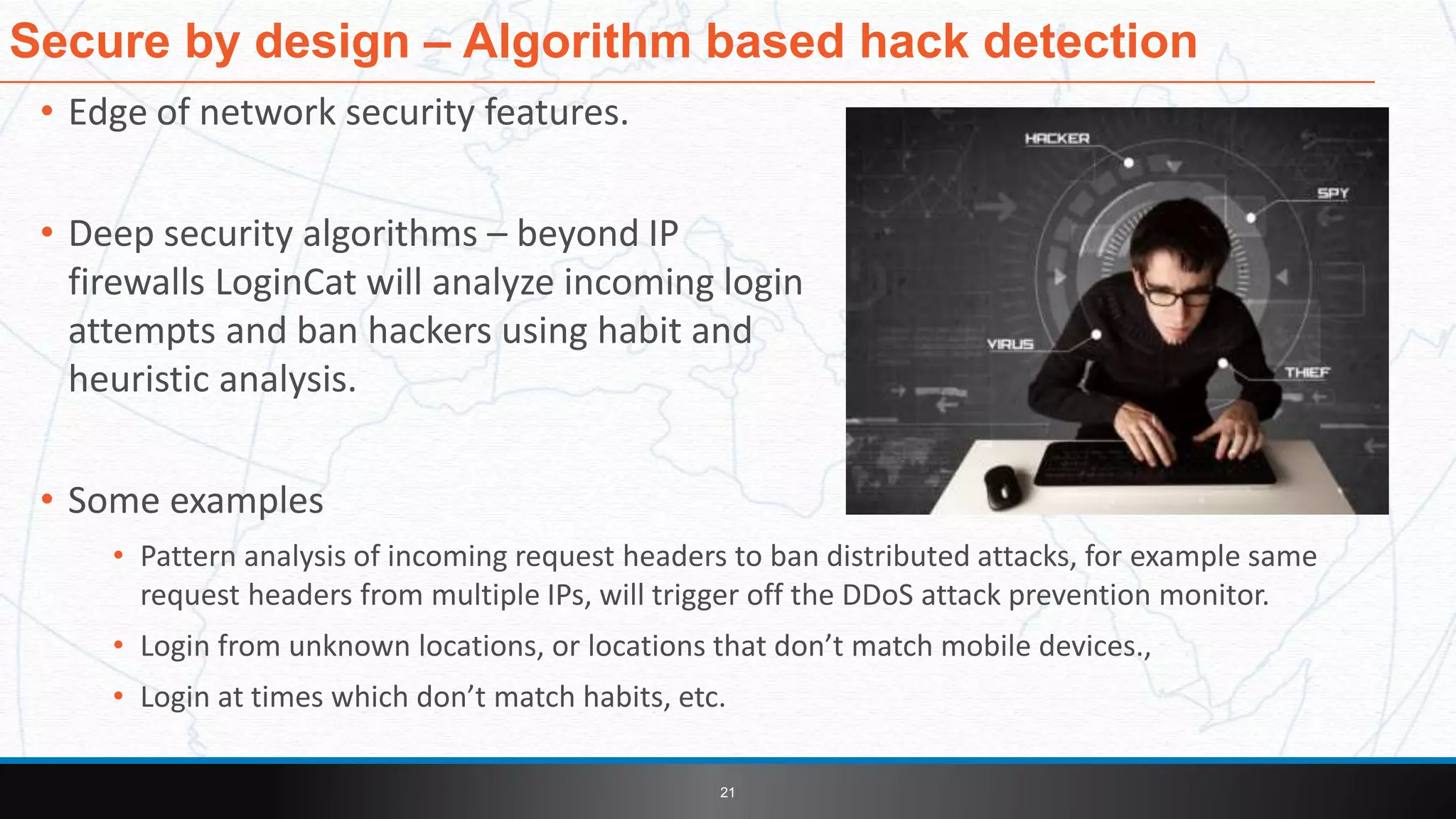
This document introduces LoginCat security software from TekMonks. It summarizes TekMonks' business operations and provides context on growing cybersecurity threats. LoginCat is presented as a solution to secure existing enterprise applications without modifications. It uses frequently changing passphrases instead of passwords and eliminates user IDs for zero-trust authentication. LoginCat integrates with applications via scripting adapters and detects hacks using behavioral analysis to prevent damages from internal breaches. The software is available both on-premises and in the cloud, and provides auditing of login activity across applications.