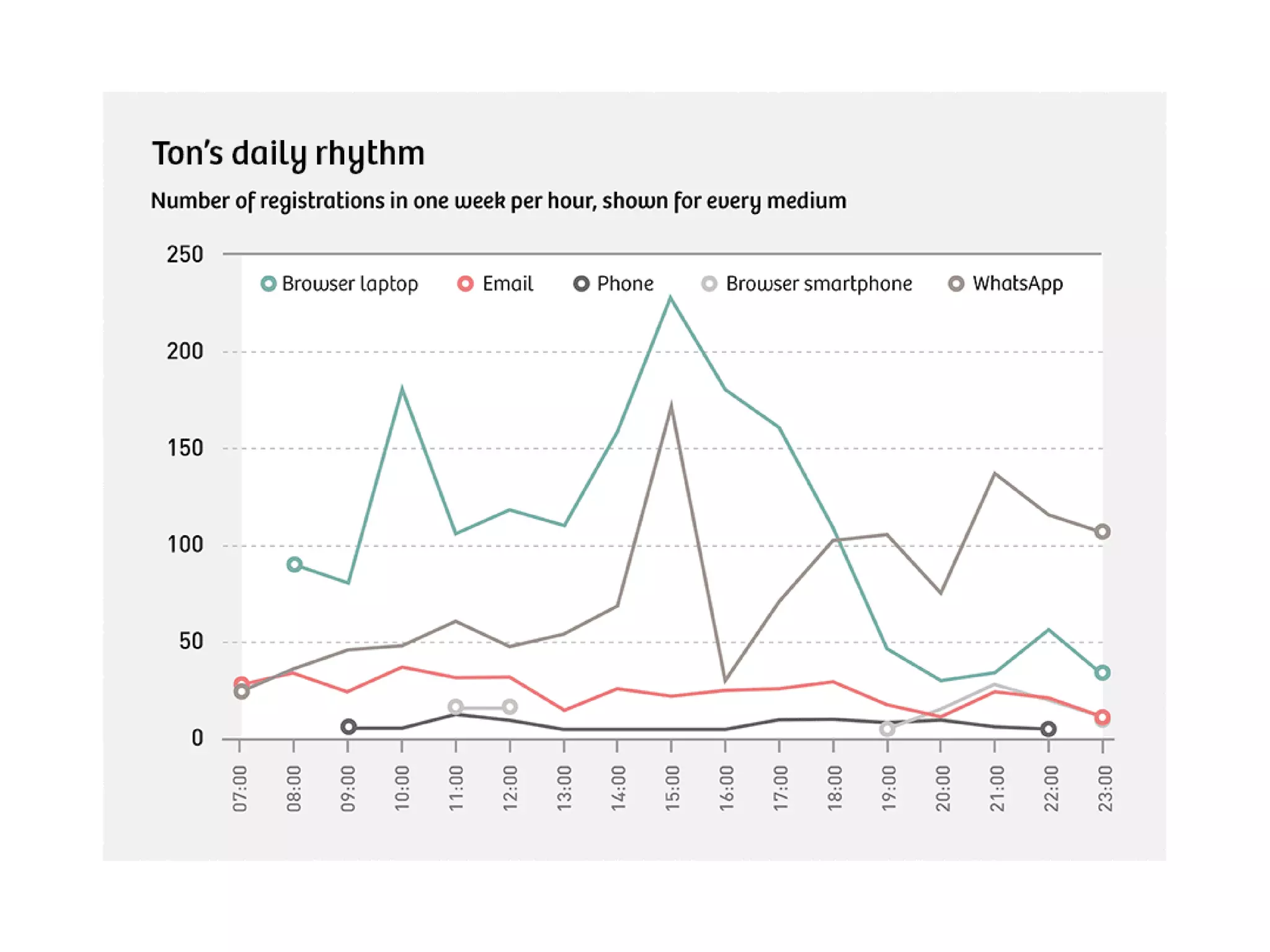
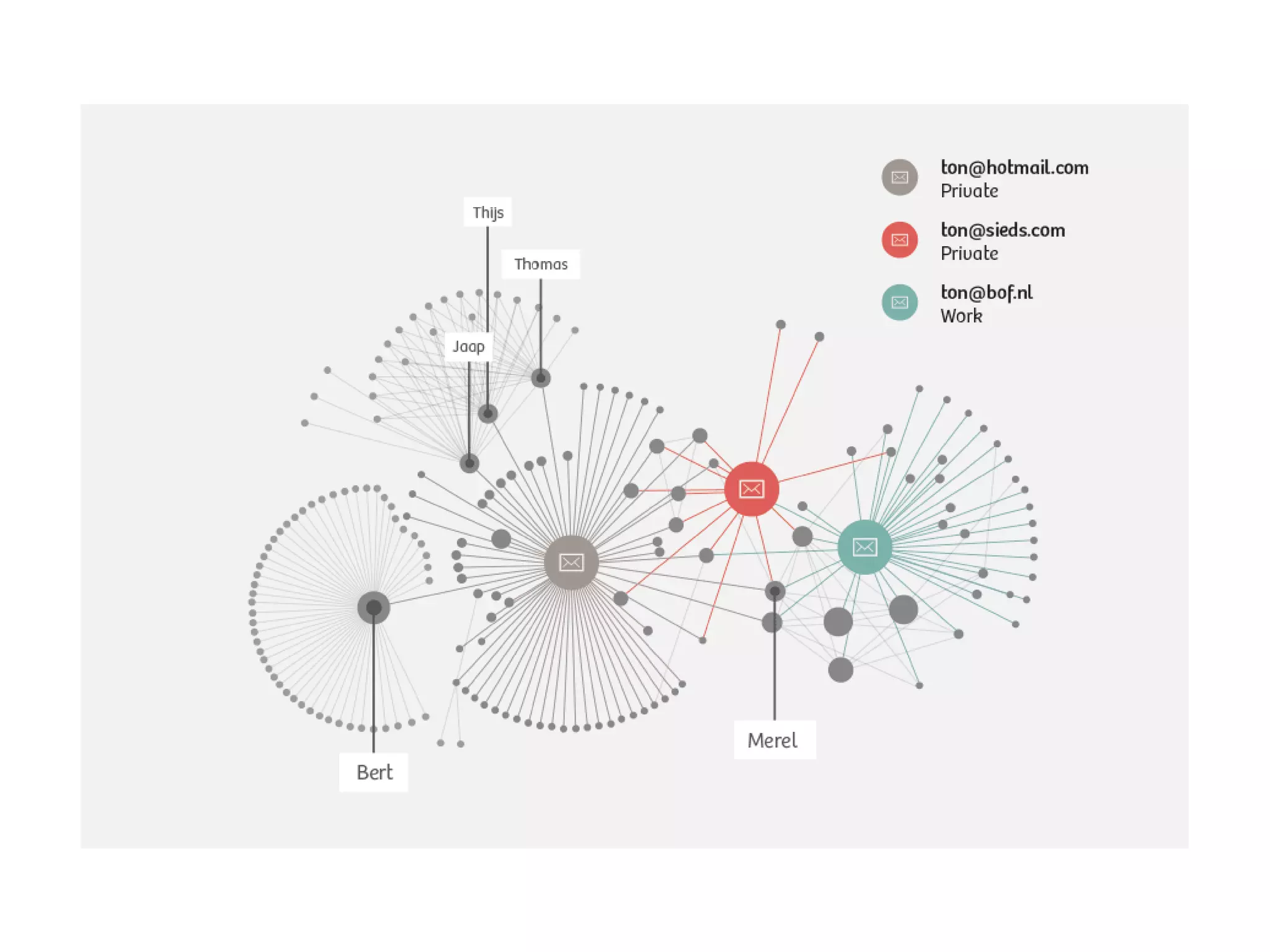
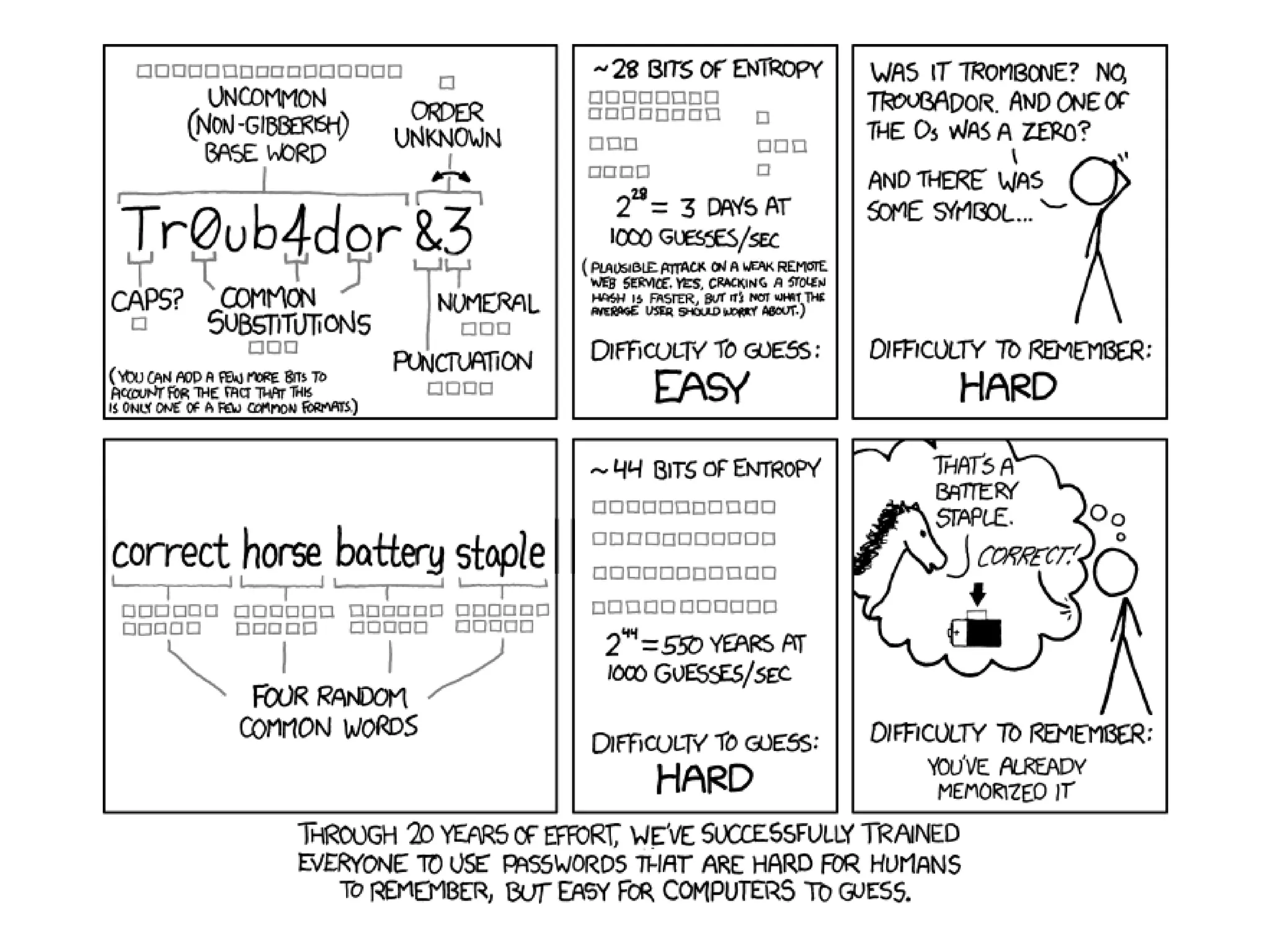
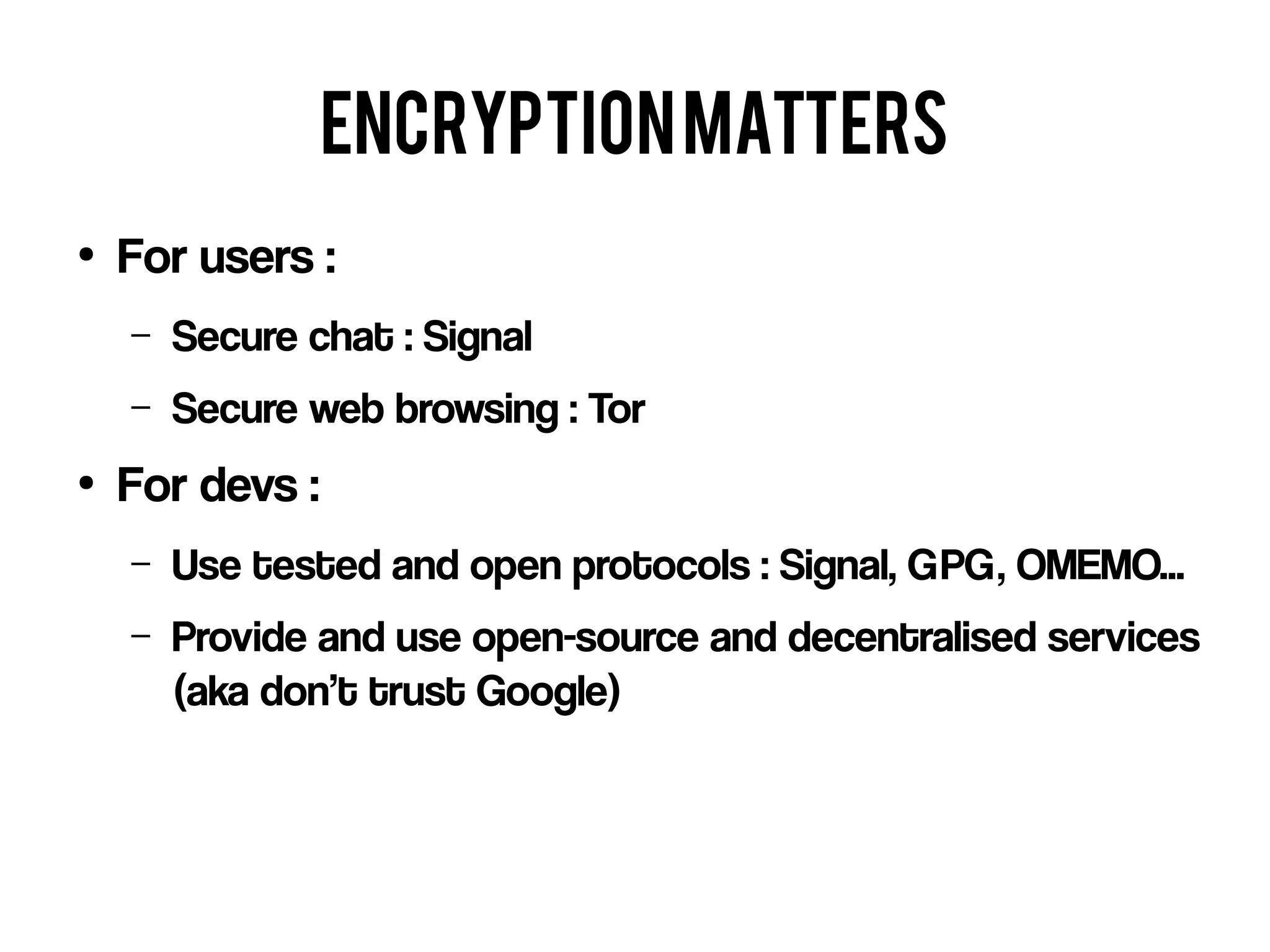
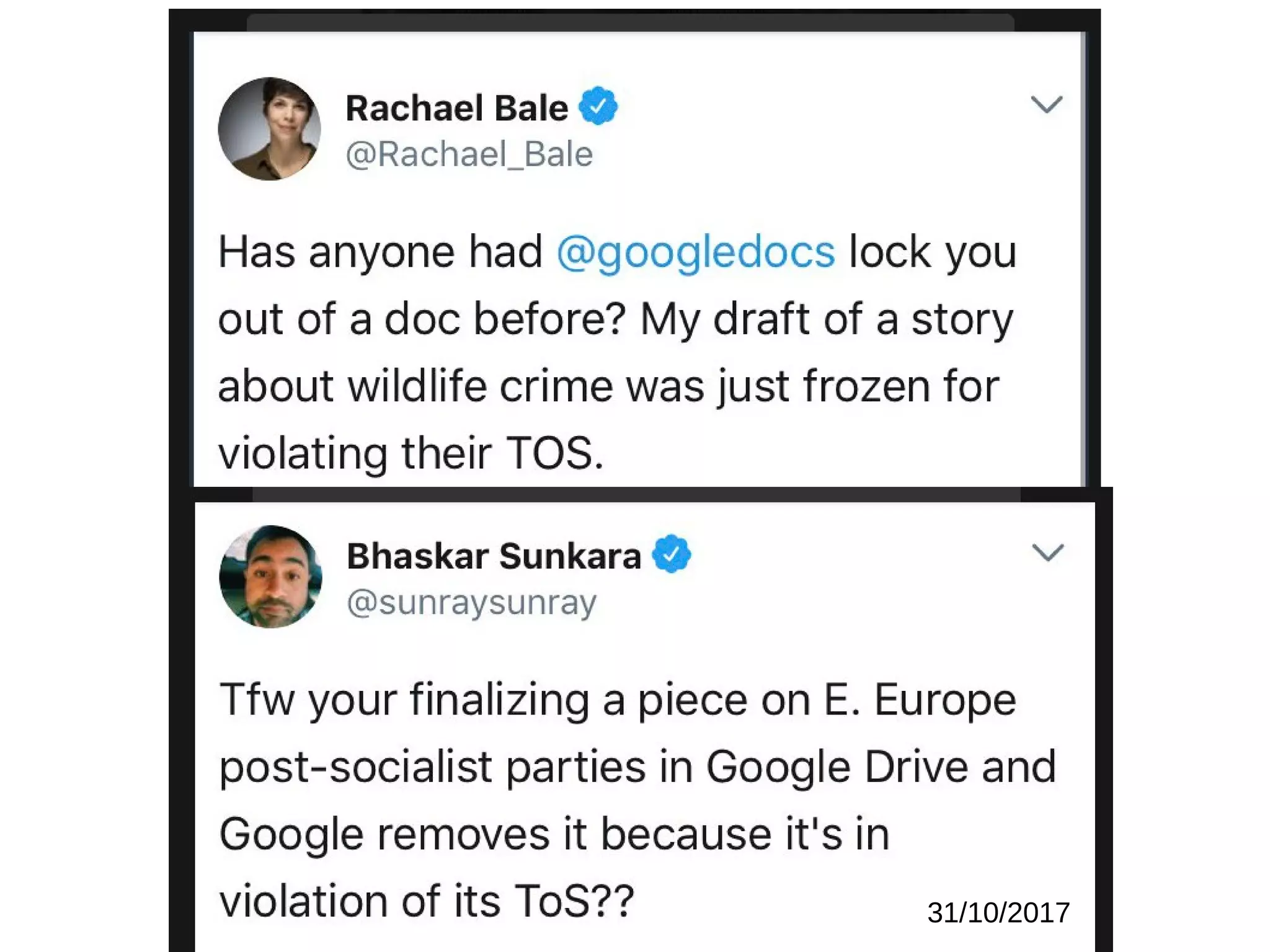
The document outlines key strategies for enhancing online privacy and security for users and developers, emphasizing the importance of password management, data encryption, and the use of open-source software. It discusses potential threats, the need for data minimization, and the concept of privacy by design. It also provides resources and references for further learning and tools, encouraging a proactive approach to safeguarding personal information.