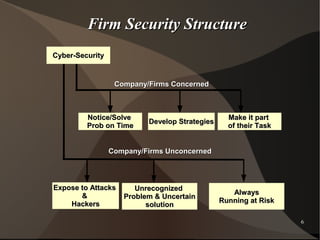
Cybersecurity and user privacy have become critical concerns for organizations and governments, driven by increasing demands for privacy protection and rising identity theft. Continuous improvements in security systems are necessary, as digital connectivity exposes firms to various cyber threats. Privacy literacy is essential for individuals to navigate the digital world responsibly, protecting personal information while engaging online.