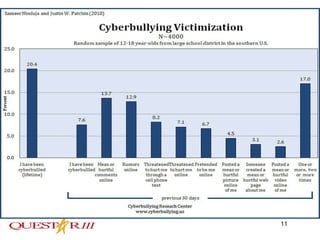
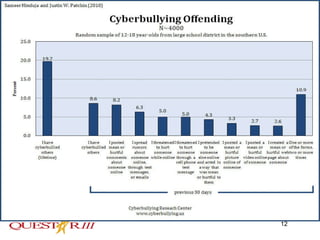
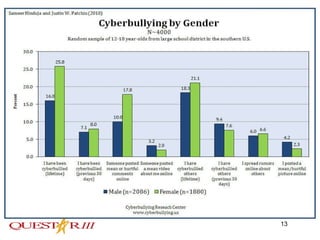
Cyber bullying involves using electronic means like email, text messages, social media to harass, threaten or embarrass someone. It is a growing problem, especially among teenagers who have widespread internet access. Some signs of cyber bullying include sadness after internet use or declining school performance. While some teens see it as harmless, it can have serious consequences like suicide. Educators need to teach safe internet use, communicate with students and parents, and work with authorities if threats are made to help address this issue.