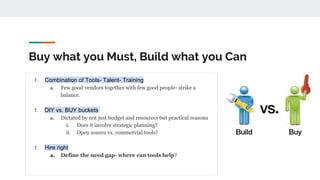
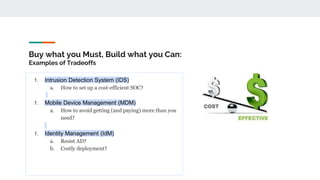
The document is a presentation by Rafaebhatti on improving security and privacy practices within organizations, focusing on practical approaches to overcoming challenges in operationalizing security. It discusses the importance of strategic decision-making, ally identification, and resource management while highlighting the gap between theoretical advice and real-world implementation. Key recommendations include making selective trade-offs, understanding risk profiles, and balancing solutions through a combination of buying and building resources.