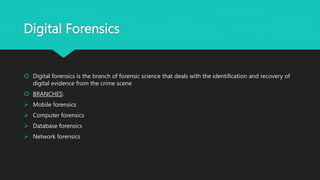
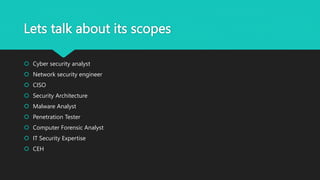
This document discusses cyber security and ethical hacking. It defines cyber security as protecting sensitive data, systems, networks and software from cyber attacks. Ethical hacking is defined as authorized hacking by a system's owner to test security. It describes different types of hackers including white hat, black hat, and grey hat hackers. Digital forensics deals with identifying and recovering digital evidence from crime scenes. The document outlines some common cyber security career paths and concludes that continued education is important as cyber threats evolve.