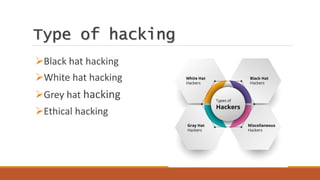
This document provides an overview of different types of hacking including black hat, white hat, grey hat, and ethical hacking. It discusses the motives and techniques used for each type. Black hat hacking involves unauthorized access for malicious purposes, while white hat or ethical hacking uses similar skills but is authorized for security testing. Grey hat hackers notify owners of vulnerabilities but may initially access without permission. The document also covers specific hacking techniques like password cracking, network scanning, exploiting software vulnerabilities, backdoors, man-in-the-middle attacks, DDoS attacks, DNS spoofing, phishing, hacktivism, SQL injection, social engineering, ransomware, and cross-site scripting.