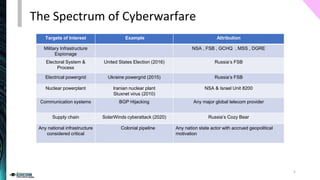
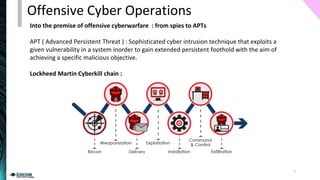
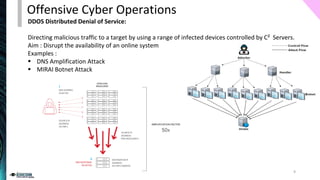
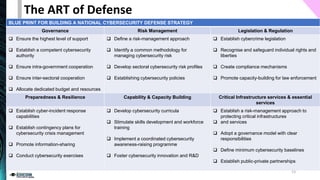
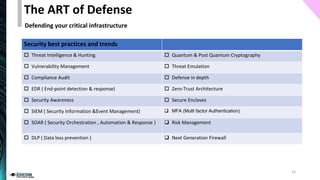
The document outlines the spectrum of cyberwarfare, defining key concepts such as cyberwarfare, offensive cyber operations, and cybersecurity strategies. It discusses both offensive techniques, like advanced persistent threats and social engineering, and defensive measures for national cybersecurity strategies. Furthermore, it emphasizes the importance of understanding adversary tactics and outlines essential frameworks for improving national cyber defense.