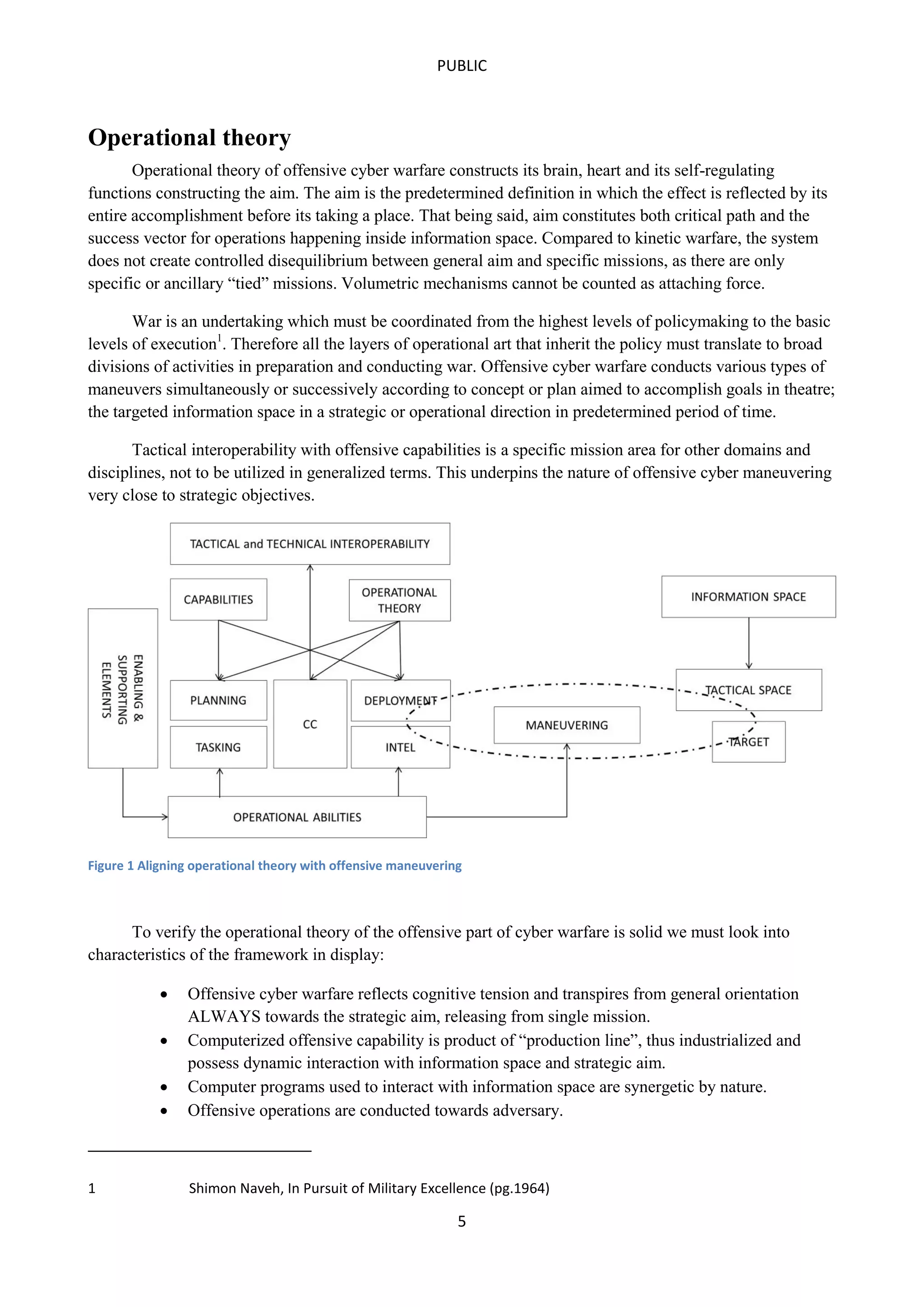
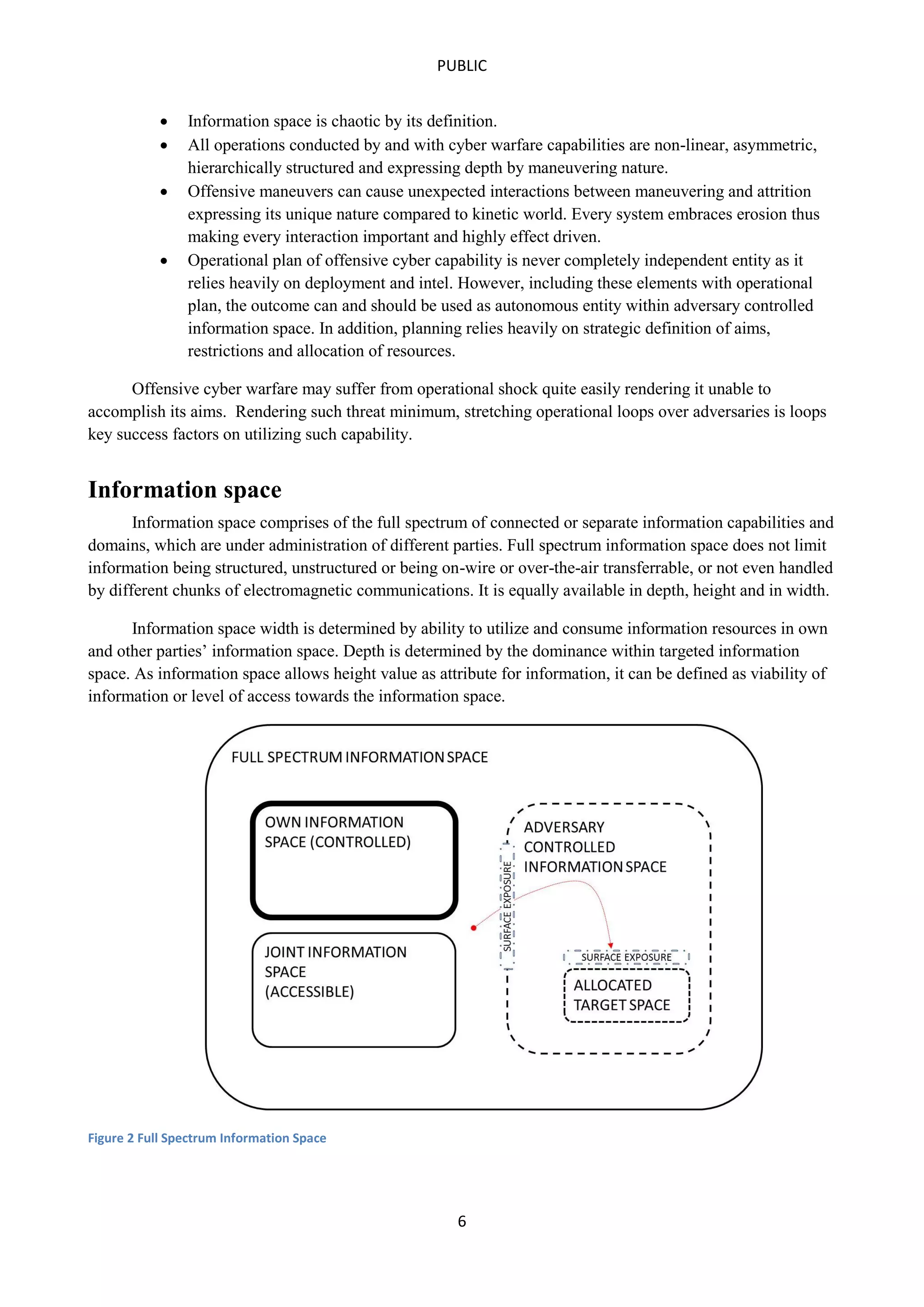
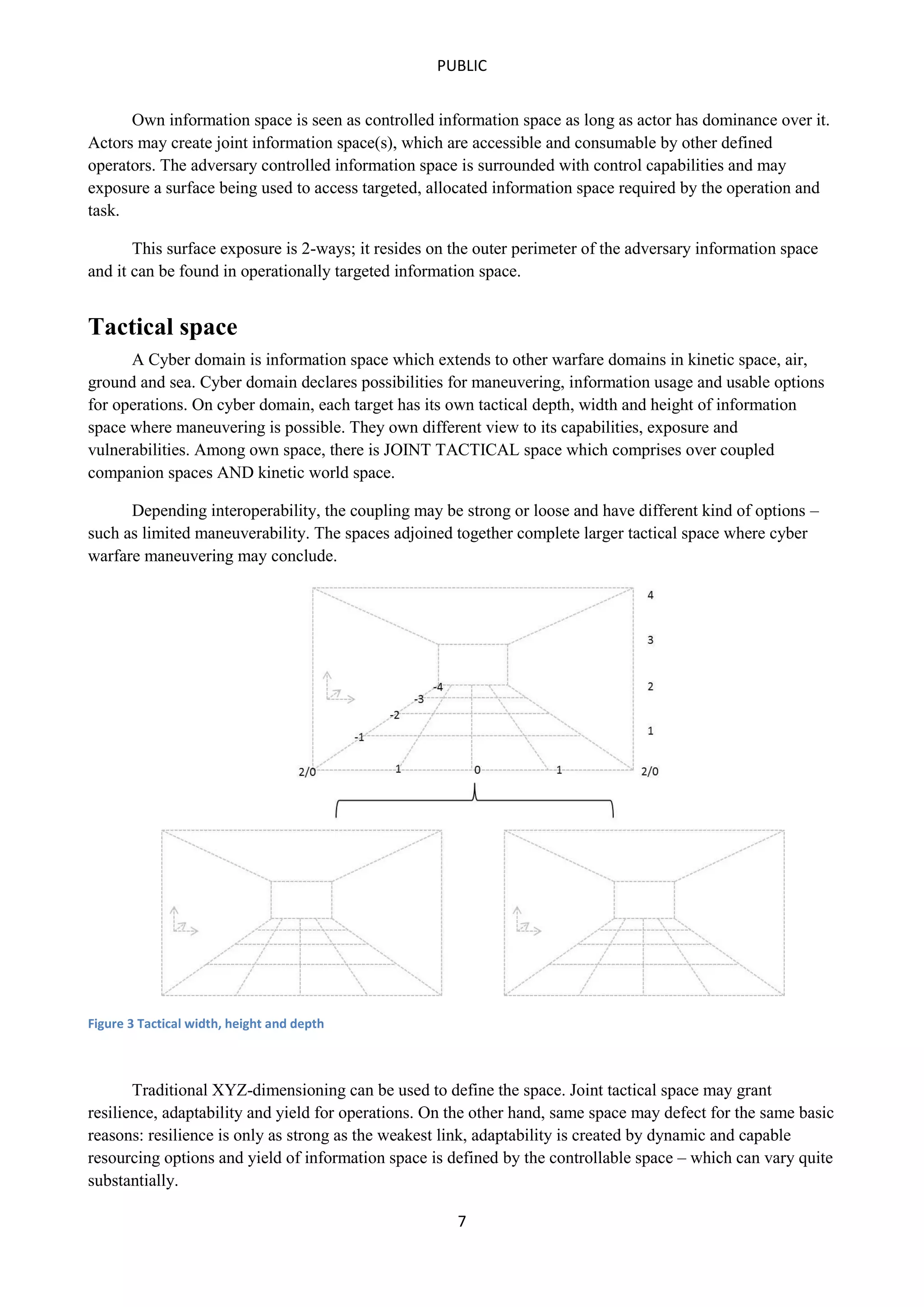
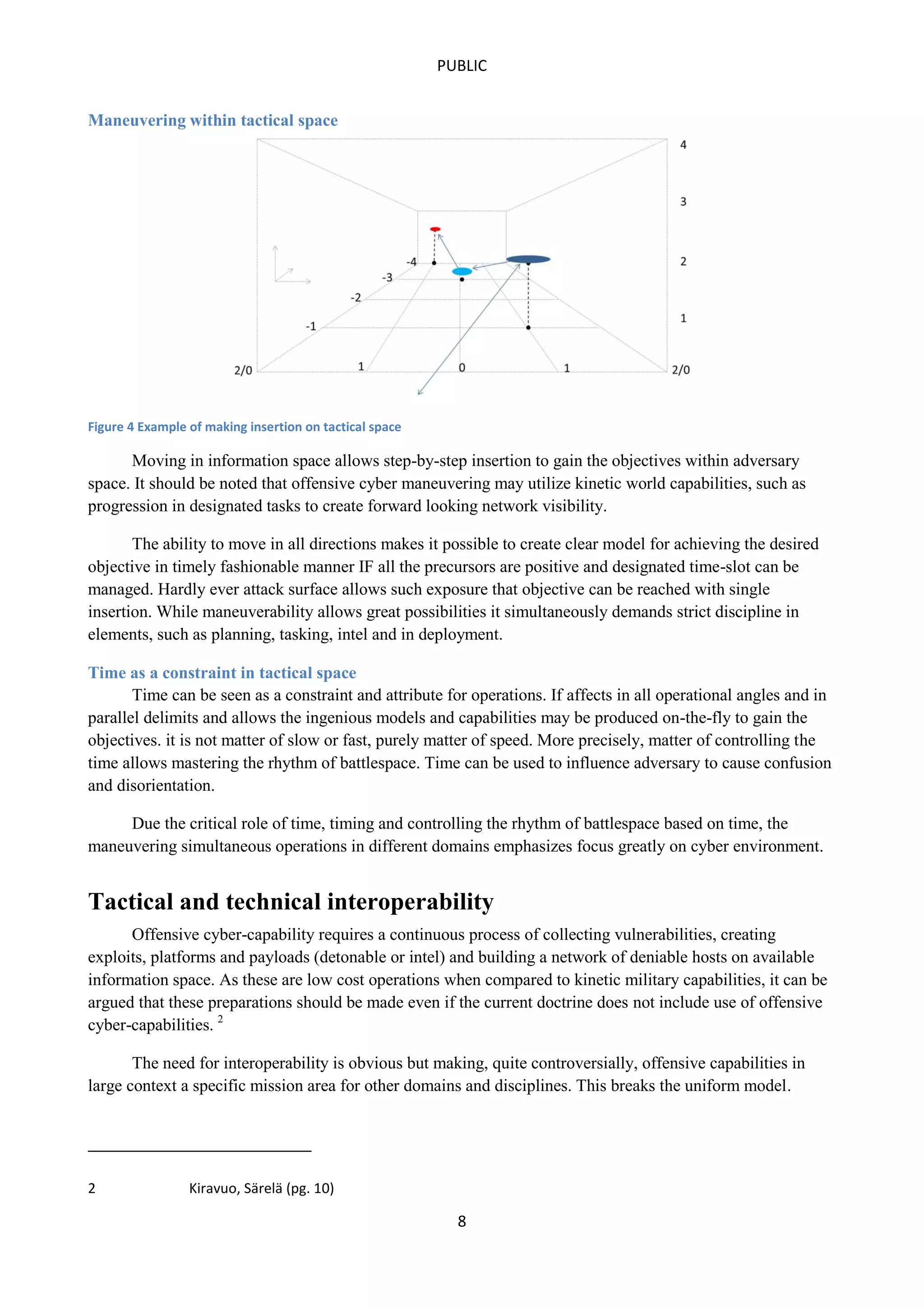
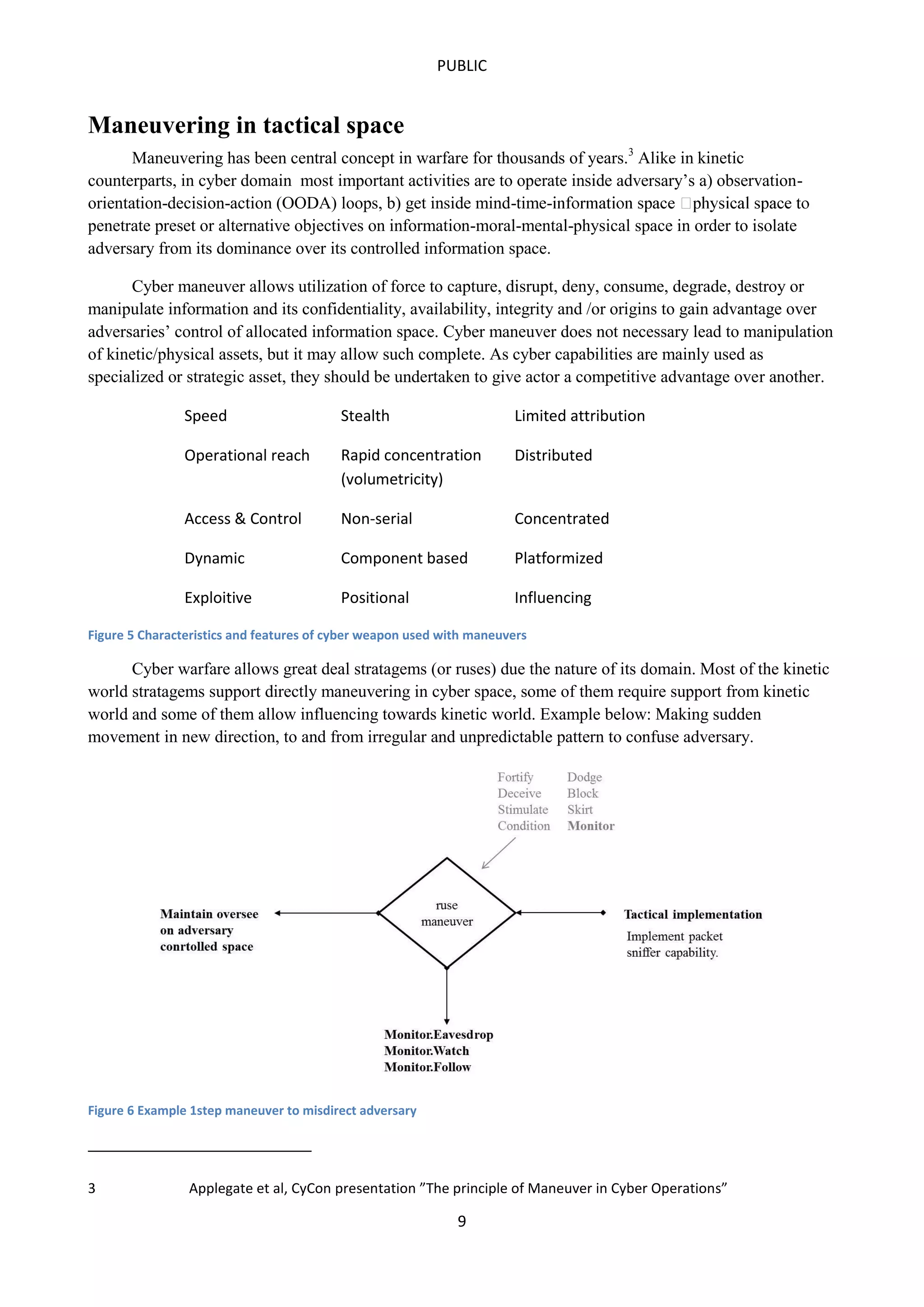
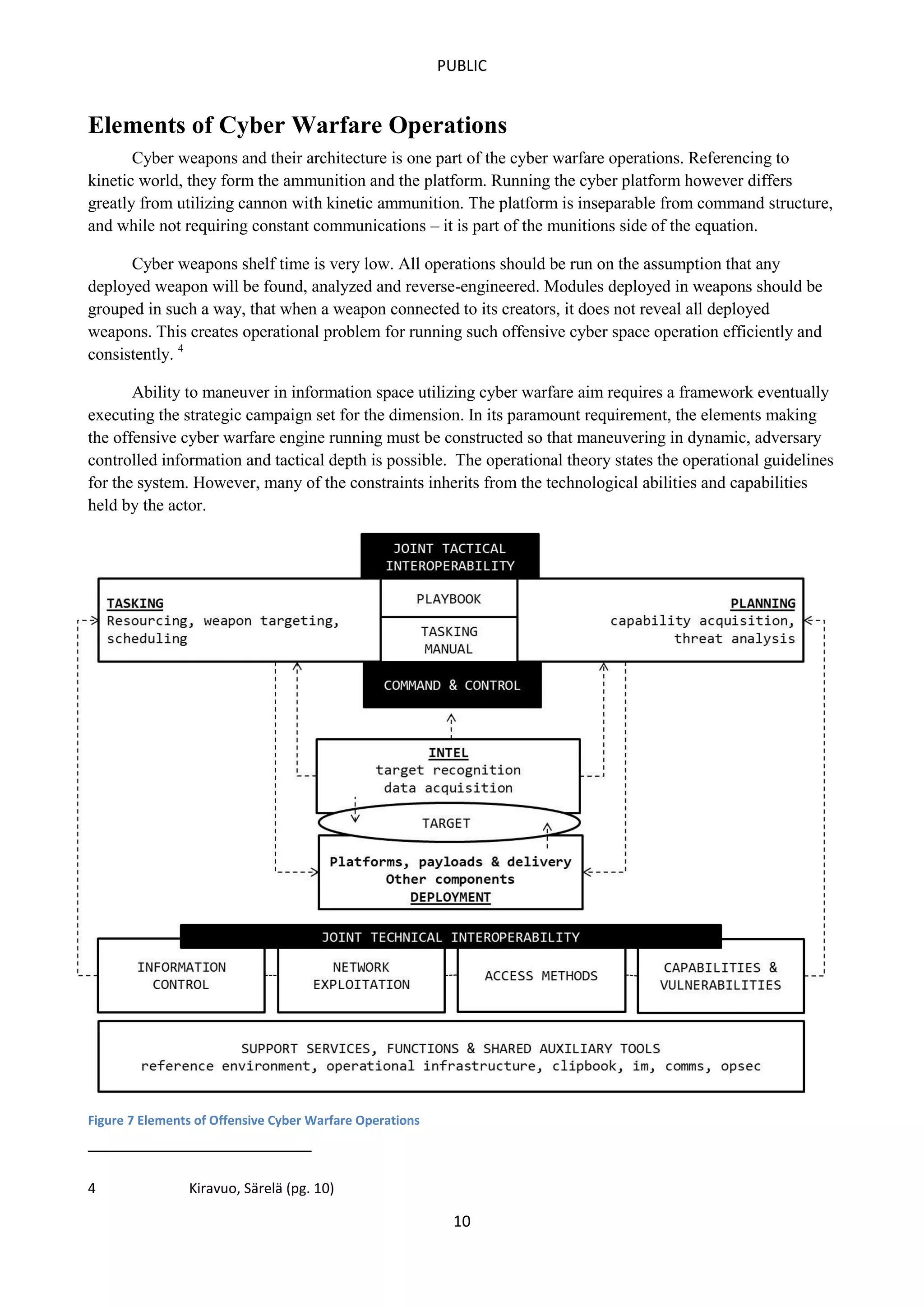
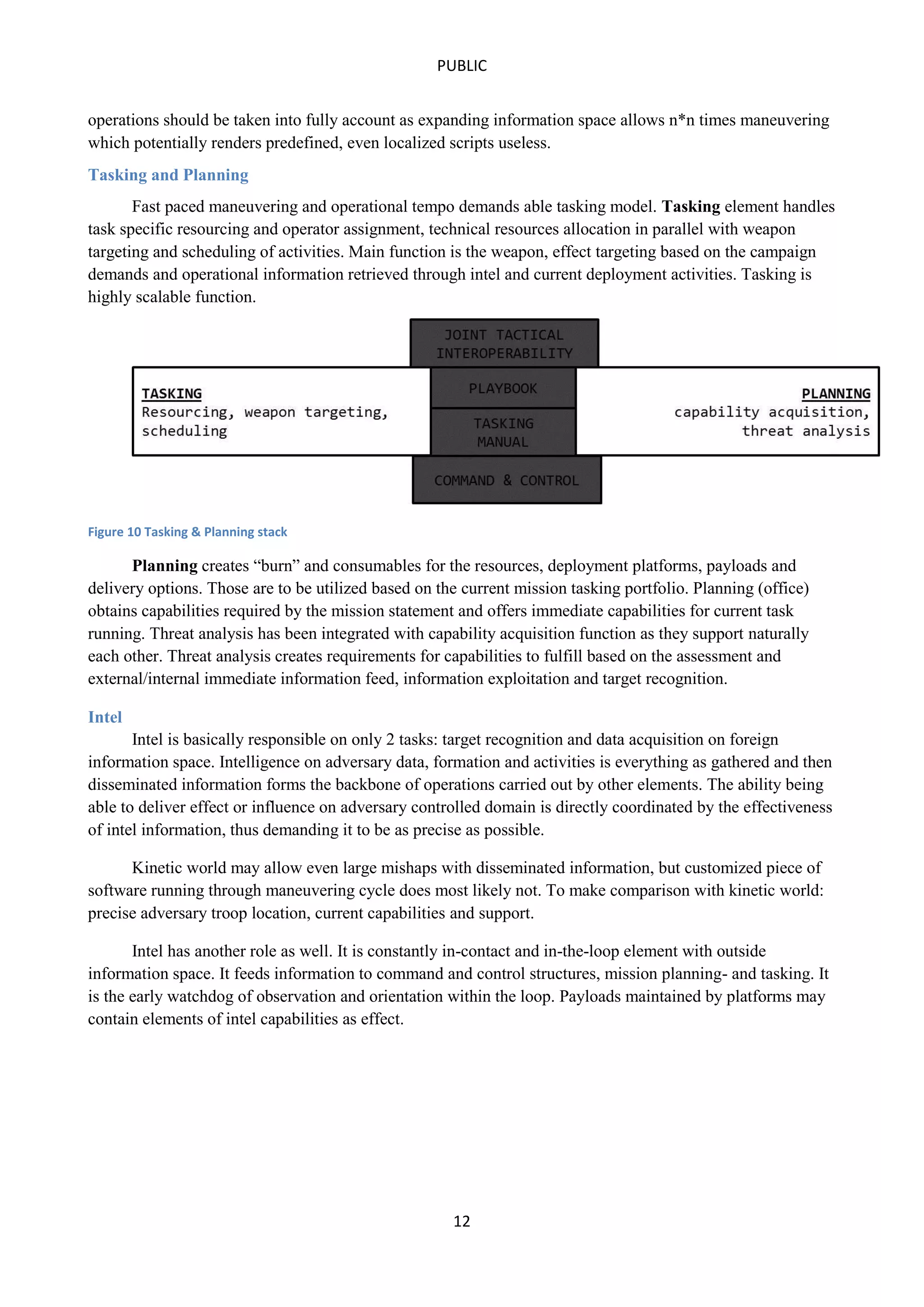
This document outlines a concept of operations for offensive cyber warfare, focusing on navigation within allocated information spaces through a framework that encompasses target recognition, payload delivery, and execution. It emphasizes the need for tactical interoperability across varied domains, contrasting the non-linear, asymmetric nature of cyber maneuvering with kinetic warfare principles. The operational theory and various elements, including command & control, intelligence, and deployment, are essential for effective offensive cyber operations targeting adversaries' information systems.