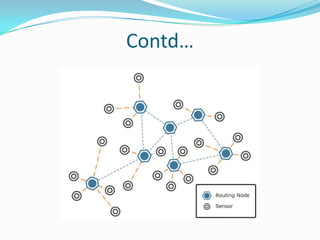
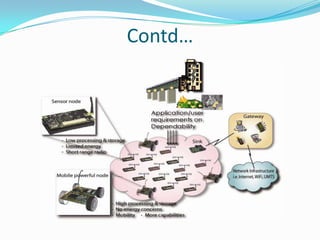
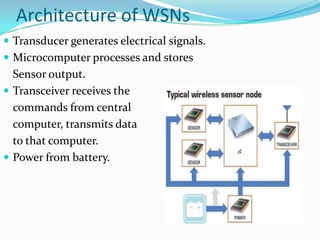
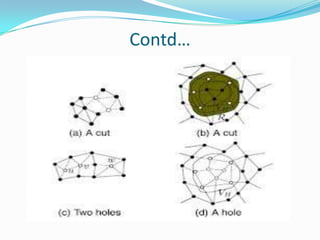
This document discusses sensor networks, including their architecture, applications, and challenges. It describes how sensor networks can become separated into multiple components due to node failures, known as "cuts". It then presents a distributed cut detection algorithm that allows nodes to detect when they become disconnected from the source node or when a cut occurs elsewhere in the network. The algorithm models the sensor network as an electrical circuit and uses iterative computation of node potentials to detect these cut events in a distributed manner without centralized control.