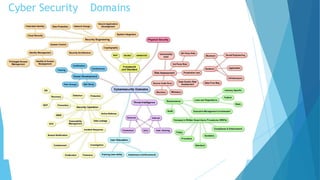
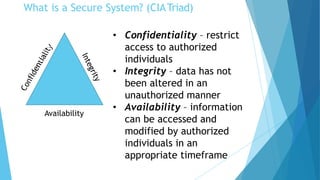
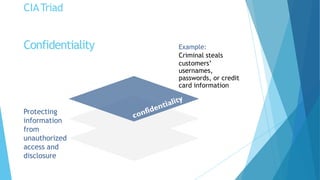
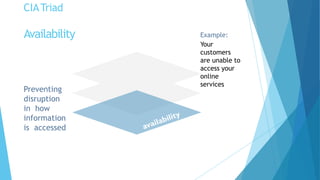
Cyber security is extremely important given how interconnected the world is through the internet. There is no such thing as absolute security, but efforts can be made to build reasonable comfort levels through processes and technologies that protect networks, devices, programs and data. The top threats organizations face come from web browsers, instant messaging clients, web applications, and excessive user rights. Cyber security aims to maintain the confidentiality, integrity and availability of information through safeguarding against threats and vulnerabilities.