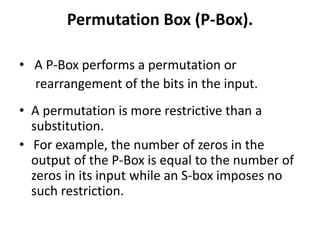
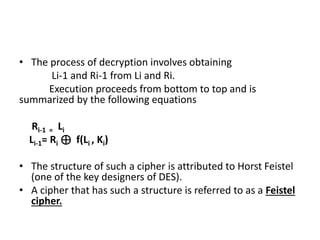
This document discusses secret key cryptography, specifically focusing on product ciphers that utilize substitution boxes (s-boxes) and permutation boxes (p-boxes) to enhance security. It details the DES (Data Encryption Standard) algorithm, including its structure, key size, and the round function employed in its encryption and decryption processes. The use of non-linear s-boxes and the Feistel structure are highlighted as critical elements in improving the strength and complexity of the cipher.