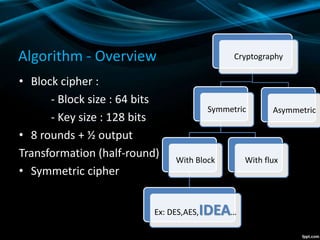
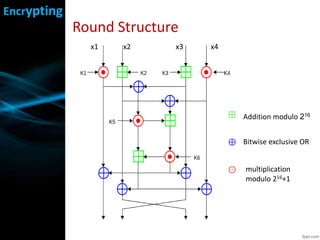
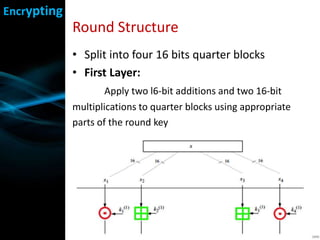
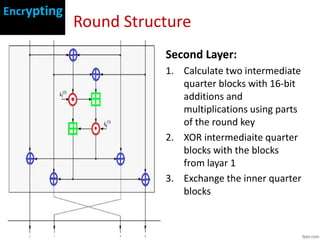
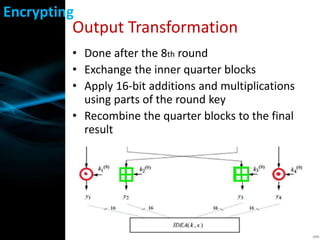
IDEA is a symmetric block cipher that operates on 64-bit blocks with a 128-bit key. It was designed in 1991 as an improvement over DES. IDEA consists of 8 rounds plus a half round. Each round splits the block into four 16-bit quarters, applies additions and multiplications using parts of the round key, exchanges inner quarters, and XORs with the output of the previous operations. The key schedule generates subkeys by rotating the main key and combining values. IDEA is considered secure and was faster than DES, though its simple key schedule was a potential weakness.