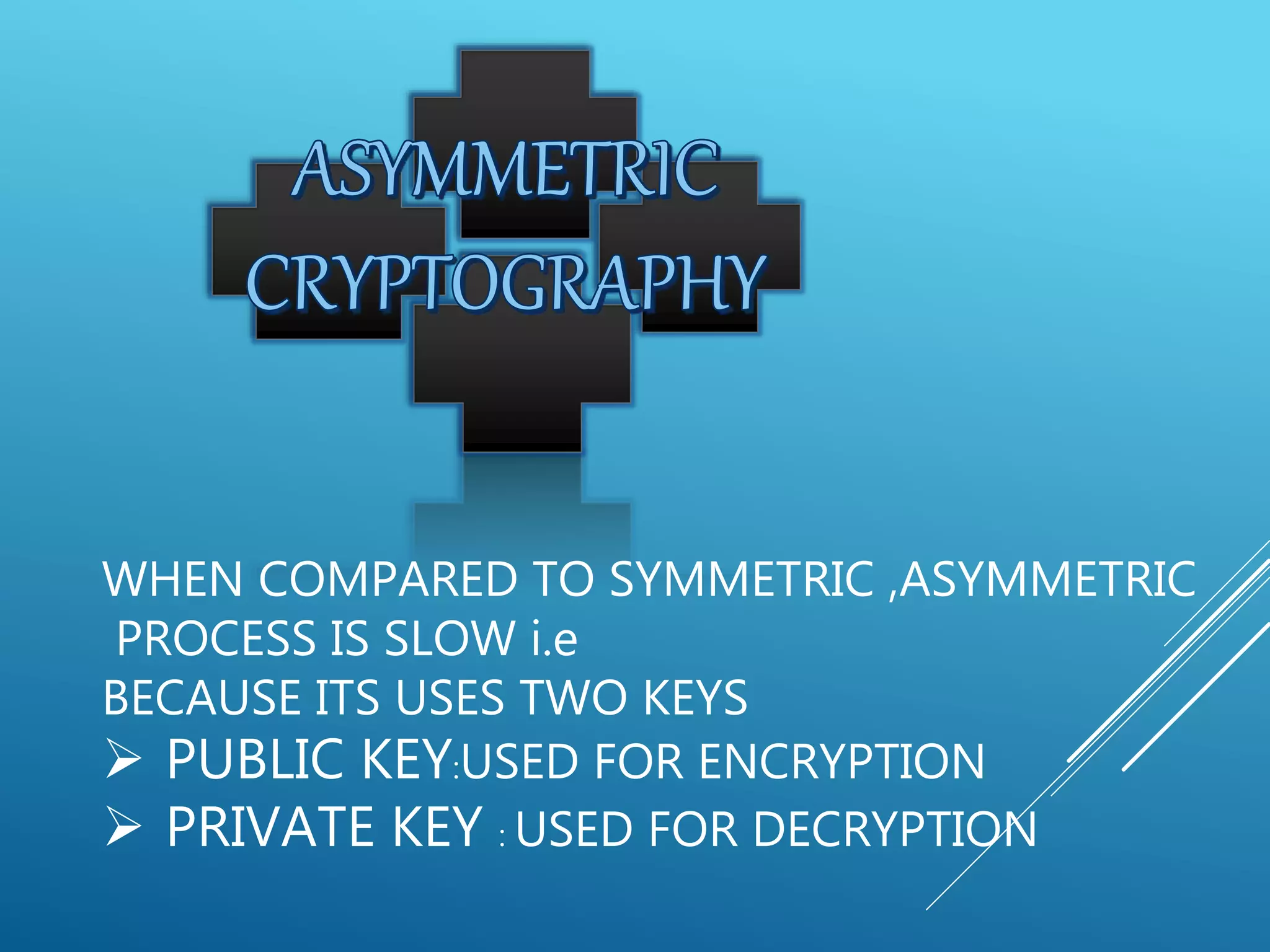
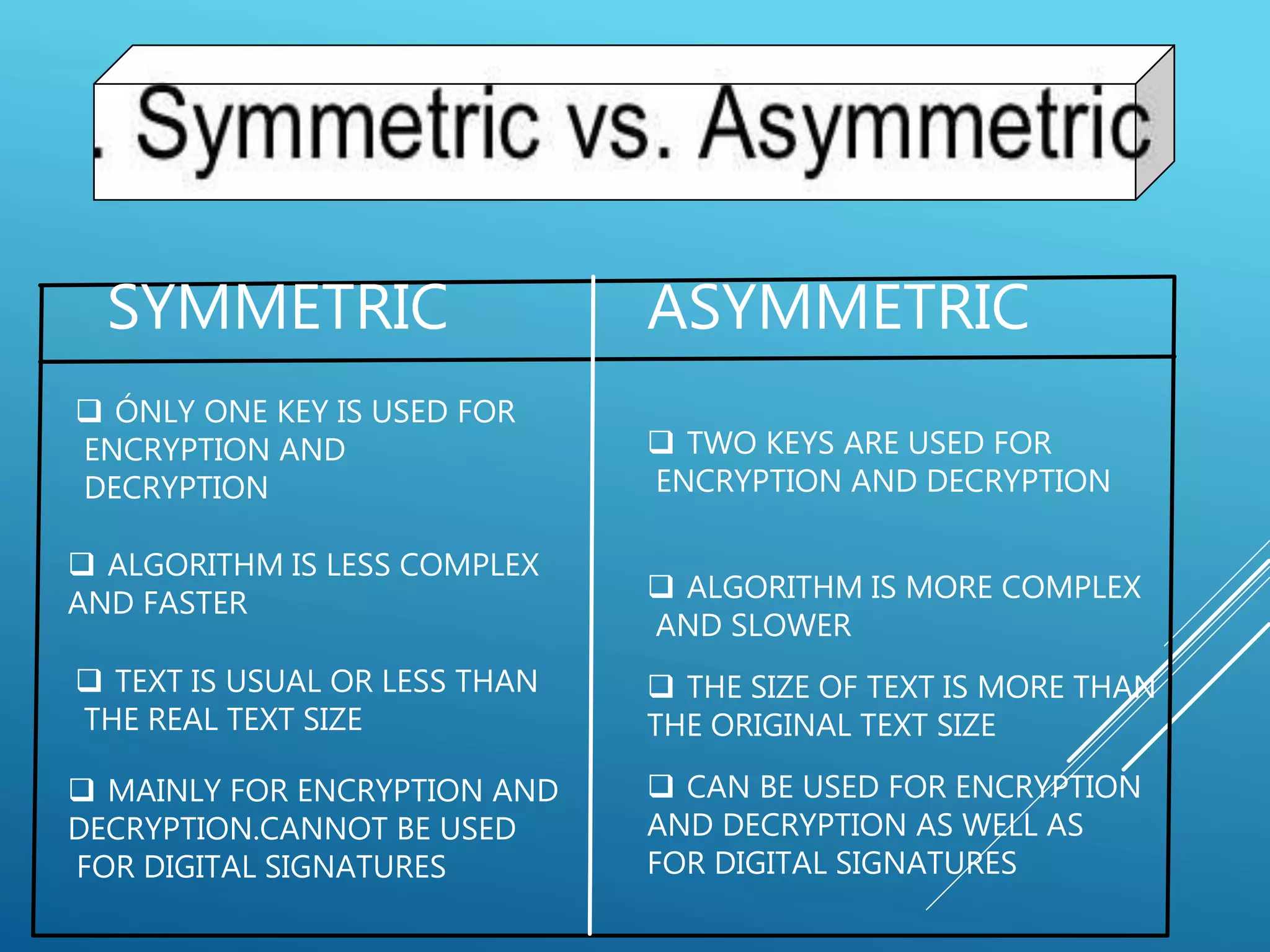
This document provides an overview of cryptography, including its history, types (symmetric and asymmetric), differences between the types, characteristics, uses, and importance. It discusses how cryptography evolved from a public field to being used secretly by governments during World Wars. It also outlines how demand increased with more widespread computer and communication technology use. The document describes common cryptography techniques like the Caesar cipher and public key encryption. It compares symmetric and asymmetric cryptography and lists examples of cryptography usage such as digital signatures, encryption, and authentication.