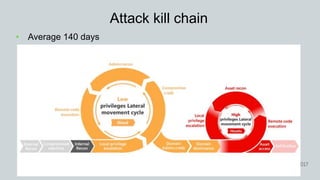
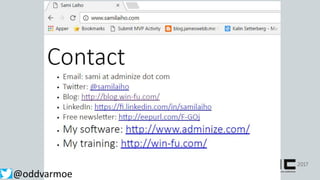
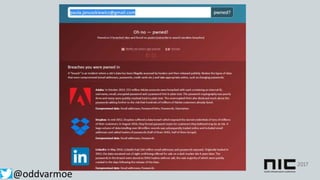
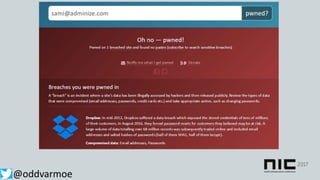
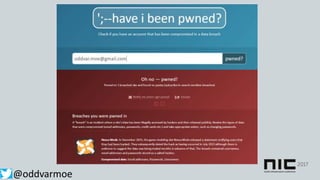
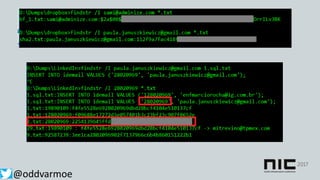
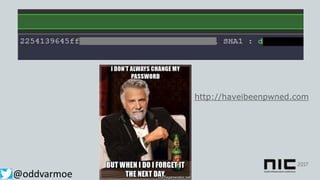
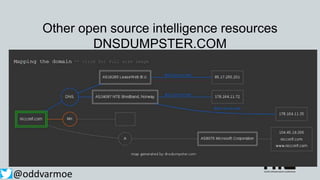
This document discusses attack and detection methods in Windows environments. It begins with an introduction of the presenter and their background. It then covers common attack vectors like phishing emails, exploiting NTLM hashes from pictures, and using compromised OWA accounts. The document discusses tools for open source intelligence gathering and demonstrates attacks. It provides recommendations for prevention through hardening configurations and enabling protections. Finally, it discusses tools and techniques for detection like Windows Defender ATP, logging, and hunting for threats. The overall message is to assume breach, implement defenses, enable detection, and regularly test security.