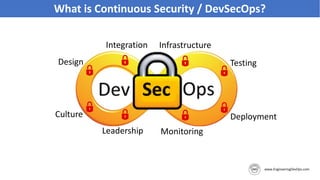
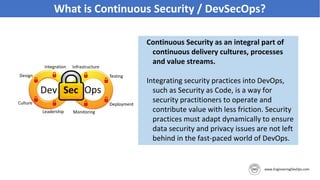
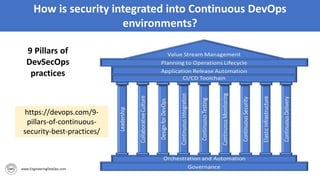
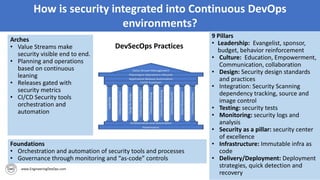
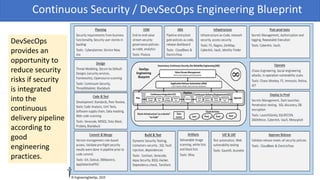
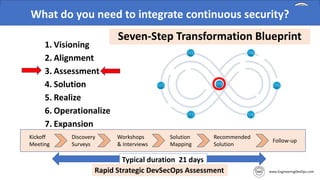
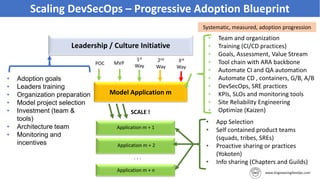
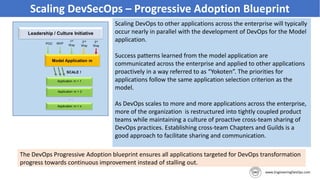
The document discusses the importance of continuous security and DevSecOps in improving security practices within DevOps environments. It highlights the integration of security into the development lifecycle, advocating for a cultural shift that empowers teams through training, automation, and leadership involvement. The provided frameworks and blueprints offer structured approaches for organizations to adopt DevSecOps practices effectively, ensuring security is an integral part of the development process.