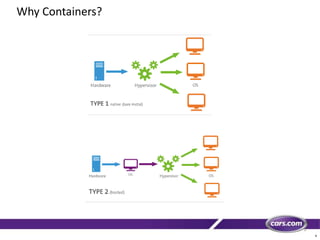
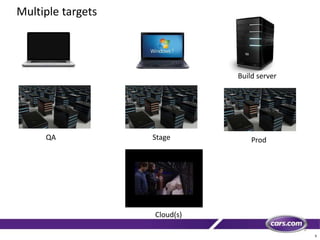
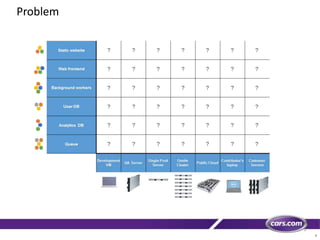
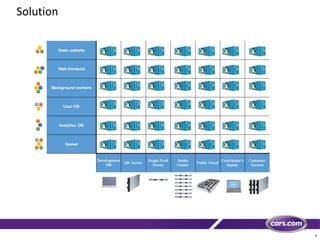
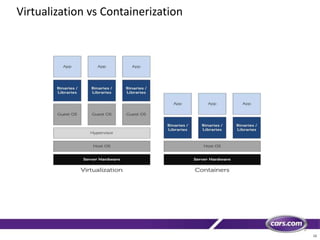
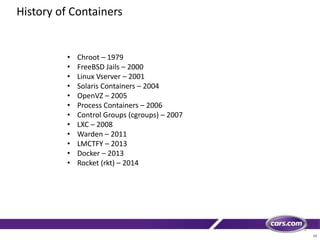
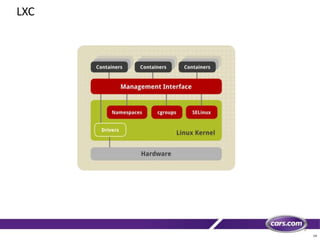
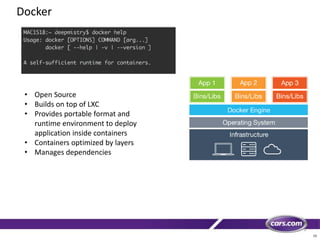
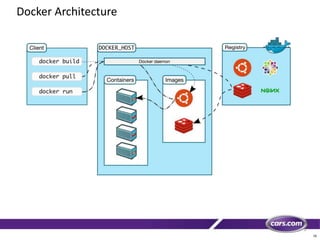
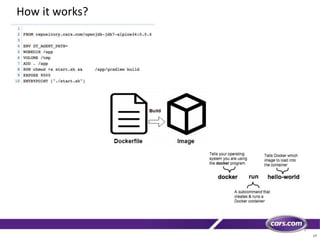
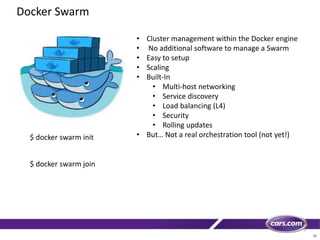
This document discusses containers in cloud computing. It begins with explaining why containers are useful for complex systems that need to deploy the same payloads across multiple environments like QA, staging and production servers. It then defines containers as isolated environments similar to virtual machines but with less overhead. The document provides a history of container technologies over time like chroot, LXC and Docker. It describes Docker as open source software that builds on LXC and provides a portable format and runtime for deploying applications in containers with optimized layers and dependency management. Finally, it introduces container orchestration tools like Docker Swarm for managing and provisioning multi-container applications across clusters with services like discovery, upgrades and load balancing.