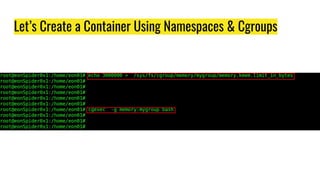
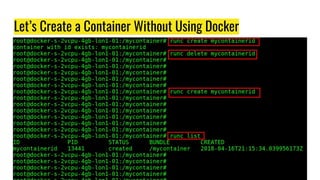
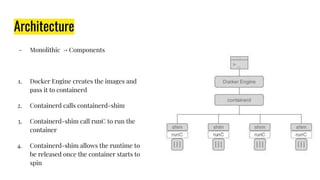
This document discusses Docker and its ecosystem. It provides a history of container technologies from chroot jails in 1979 to modern tools like Docker, Kubernetes, containerd, and RunC. It describes the architecture and components of Docker including how it leverages containerd and RunC. Finally, it discusses orchestration tools like Kubernetes and how Docker is organized into various modular projects under the Moby project.