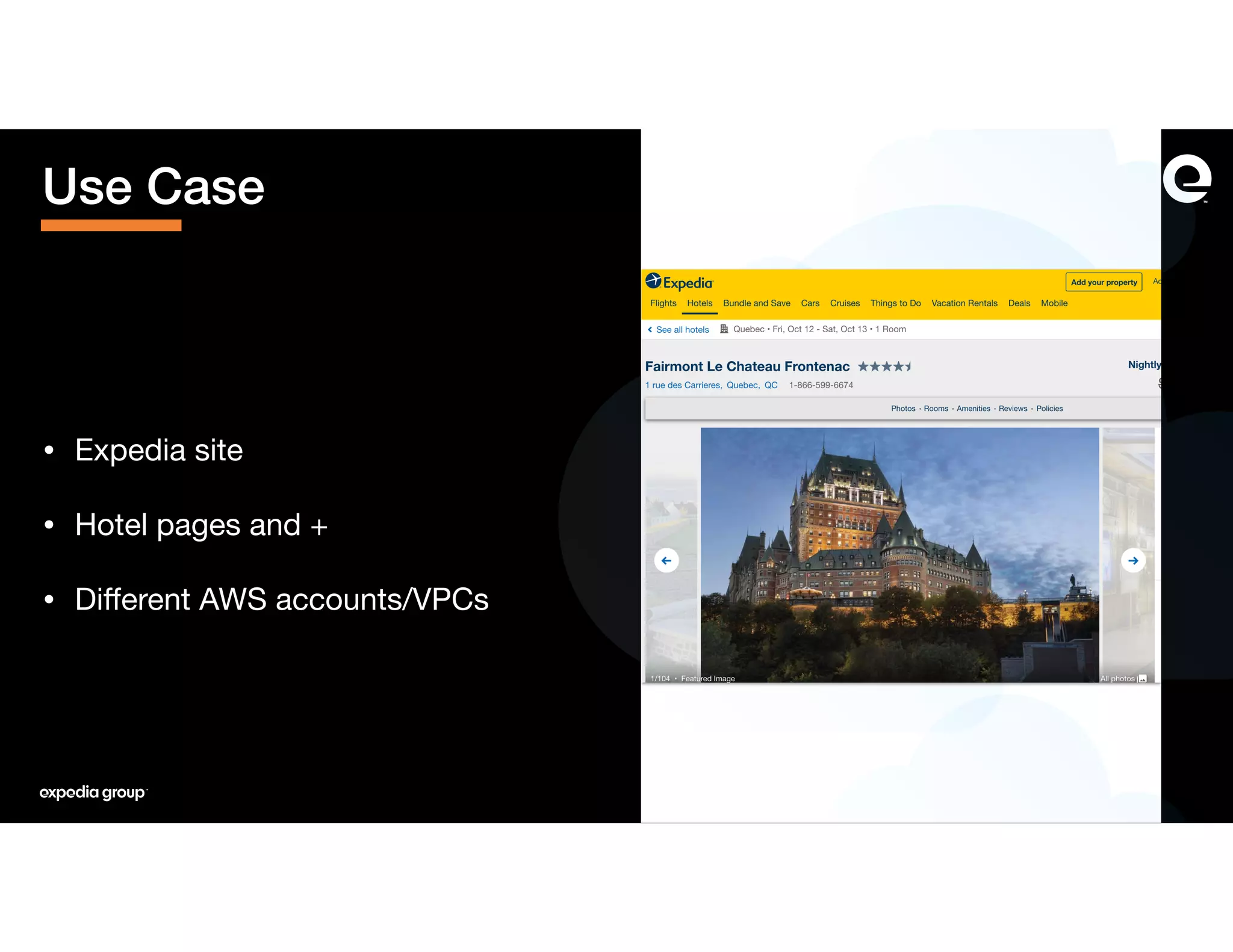
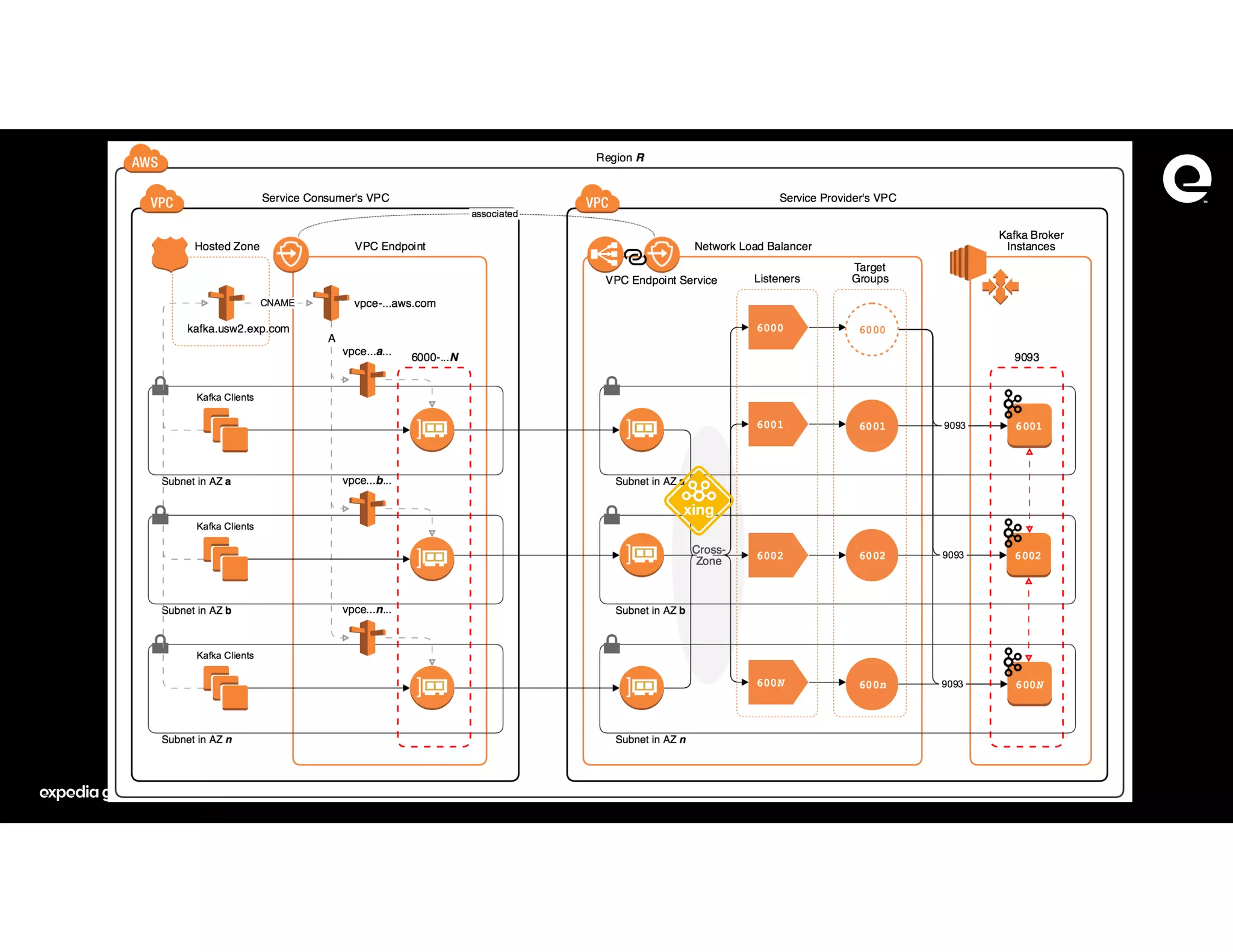
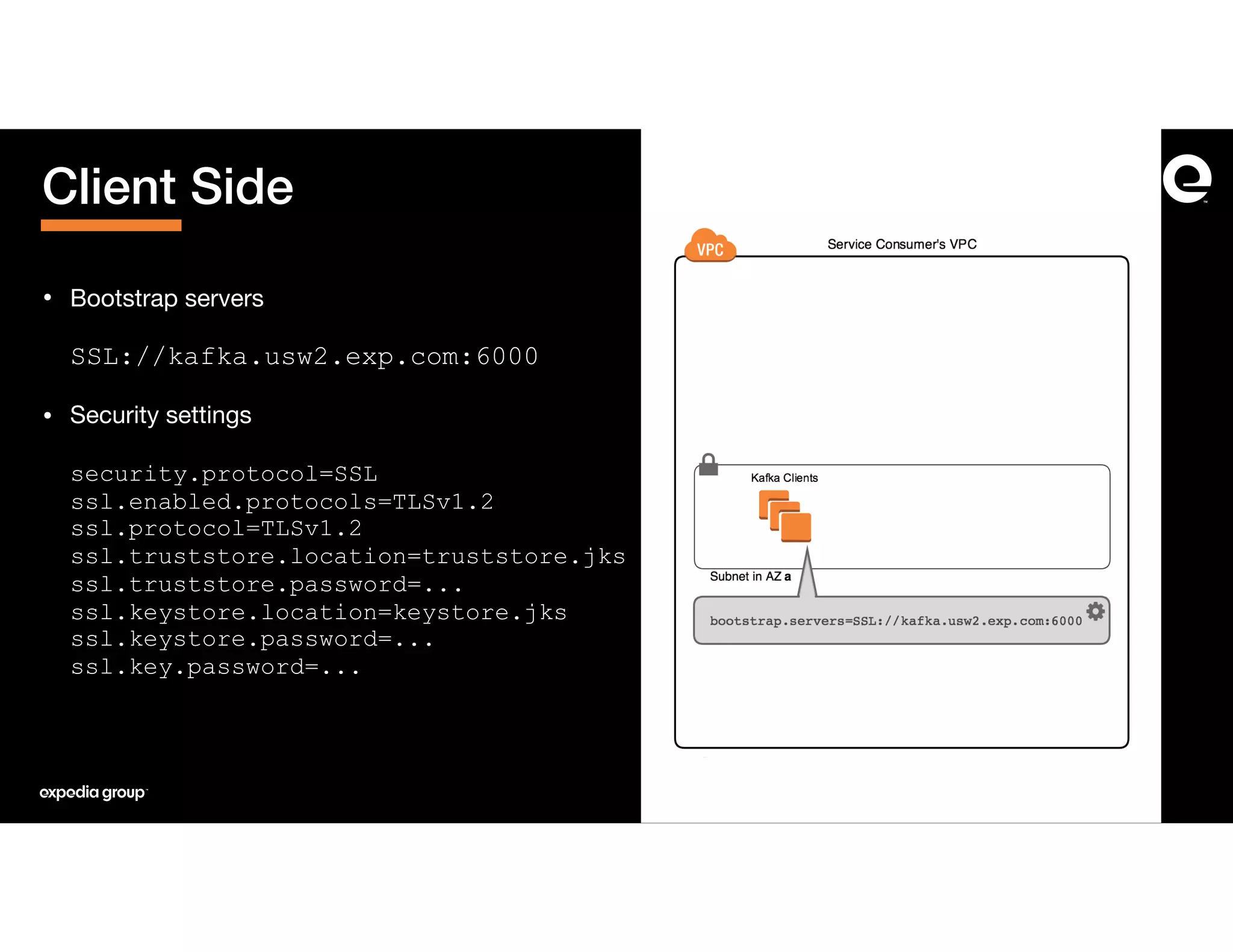
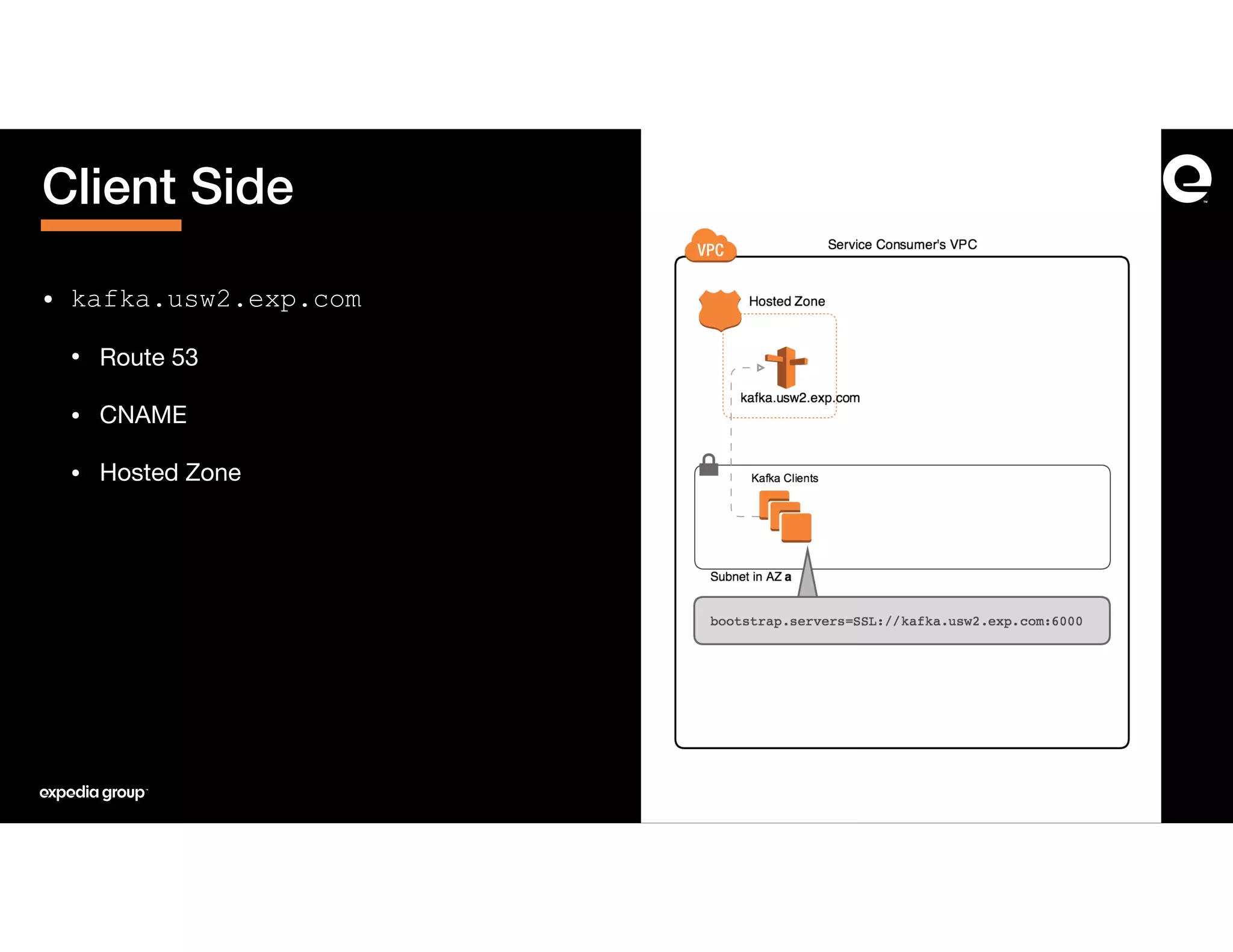
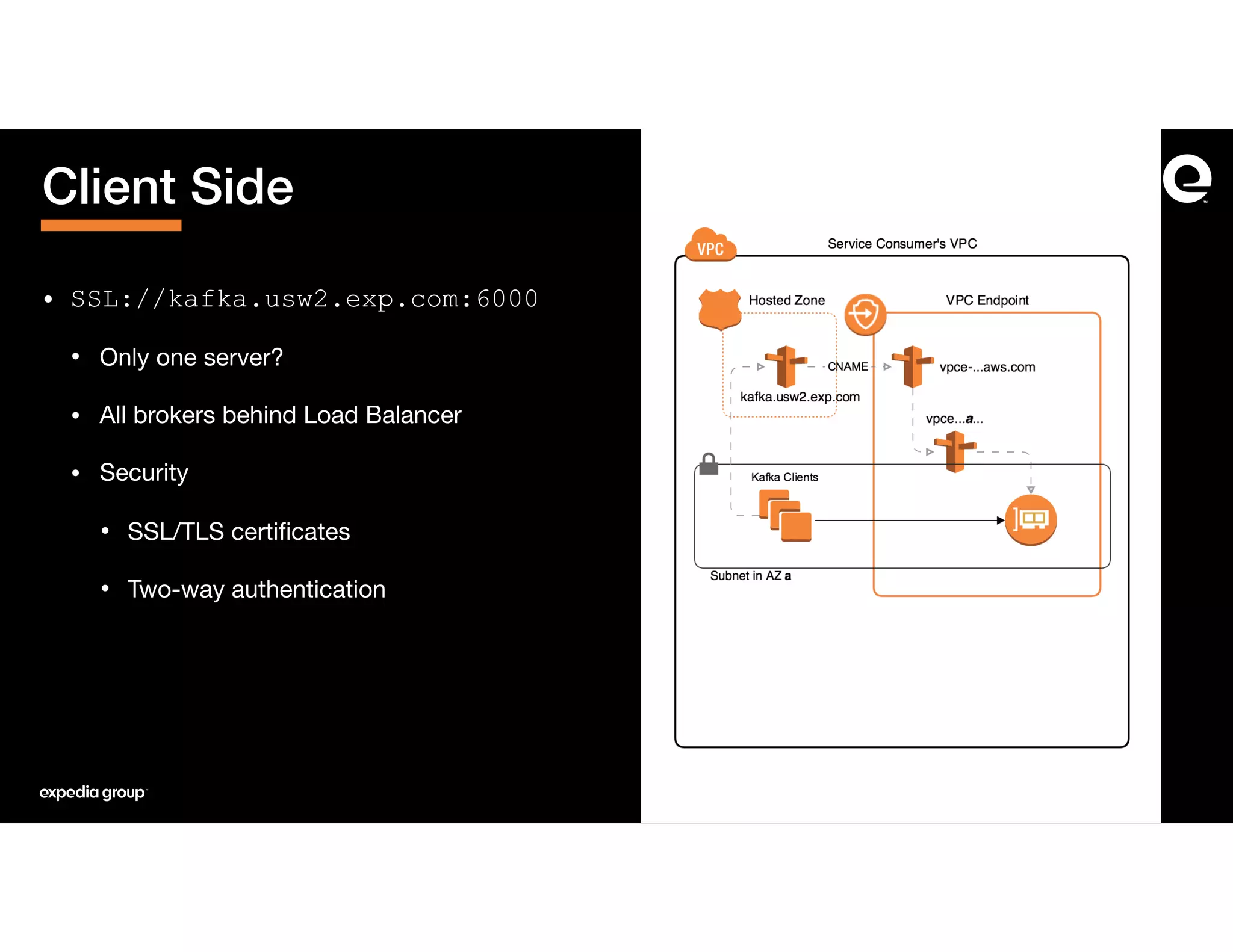
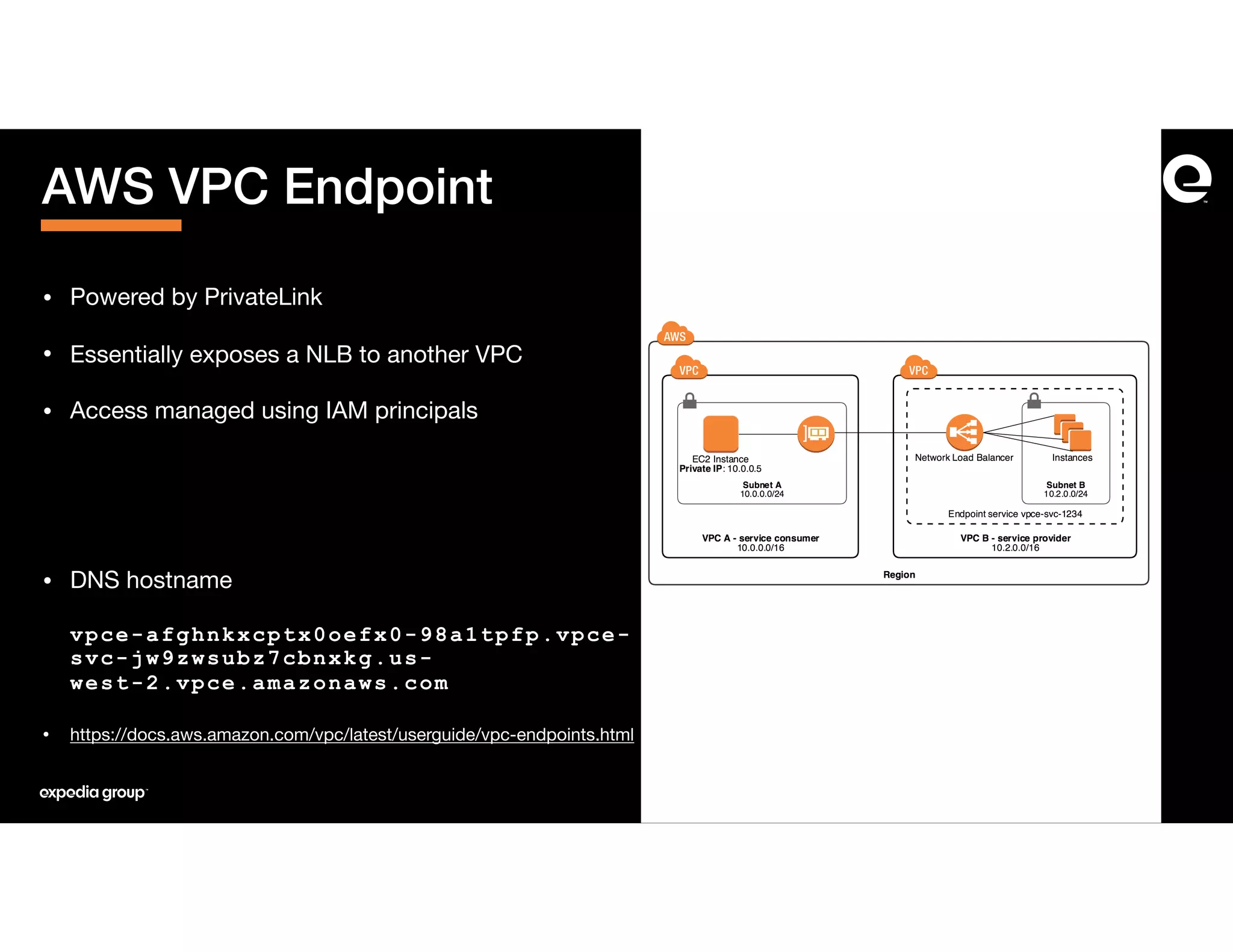
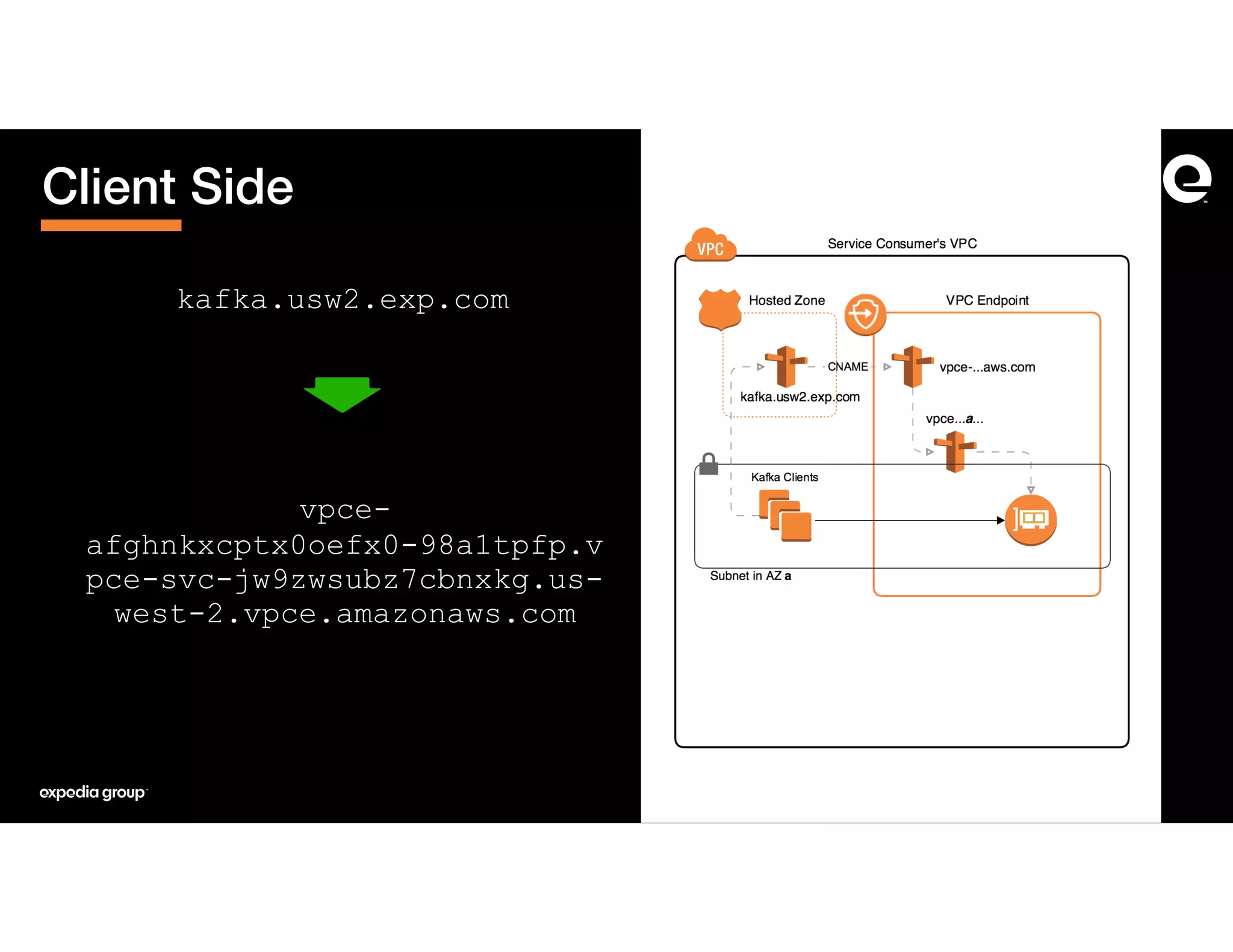
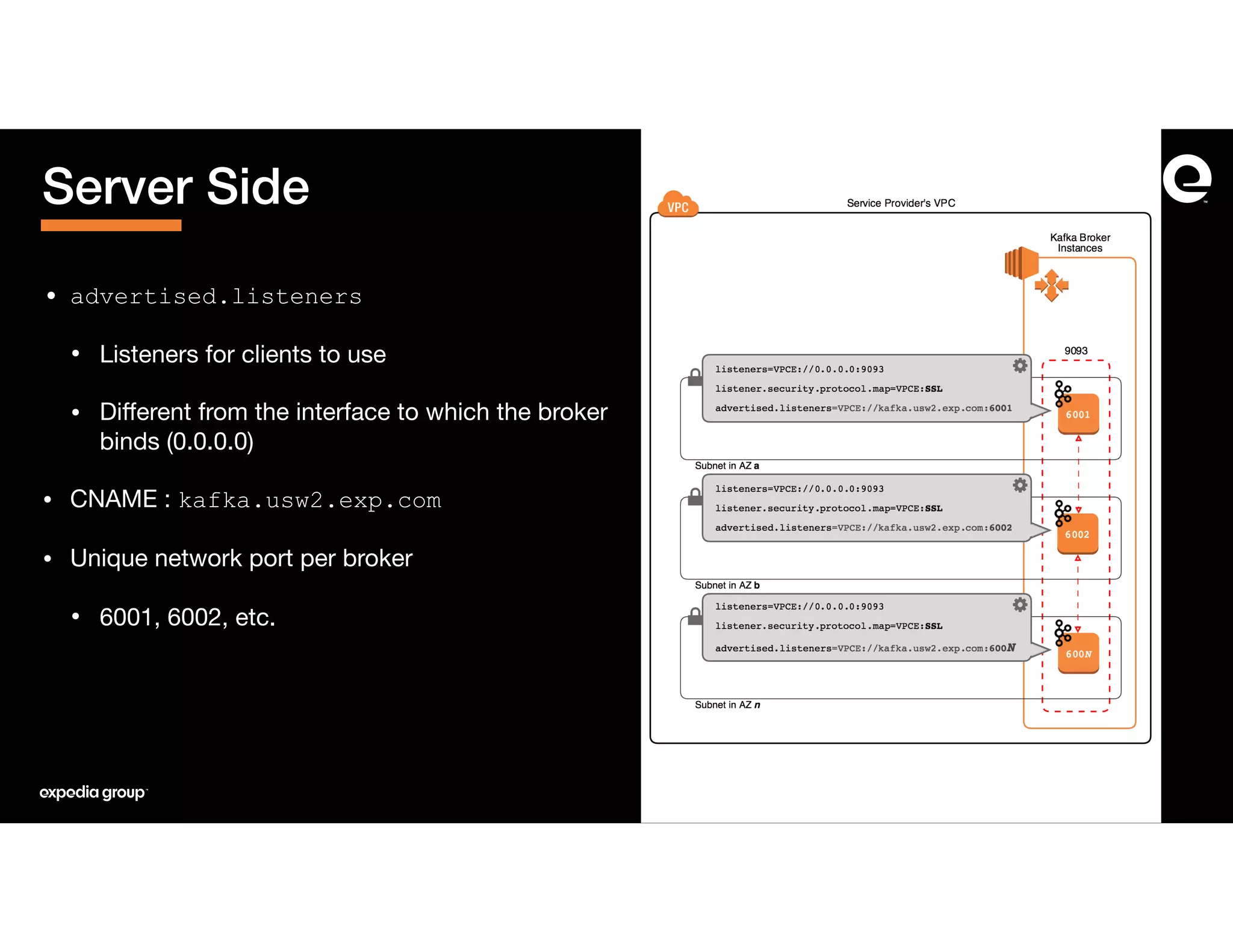
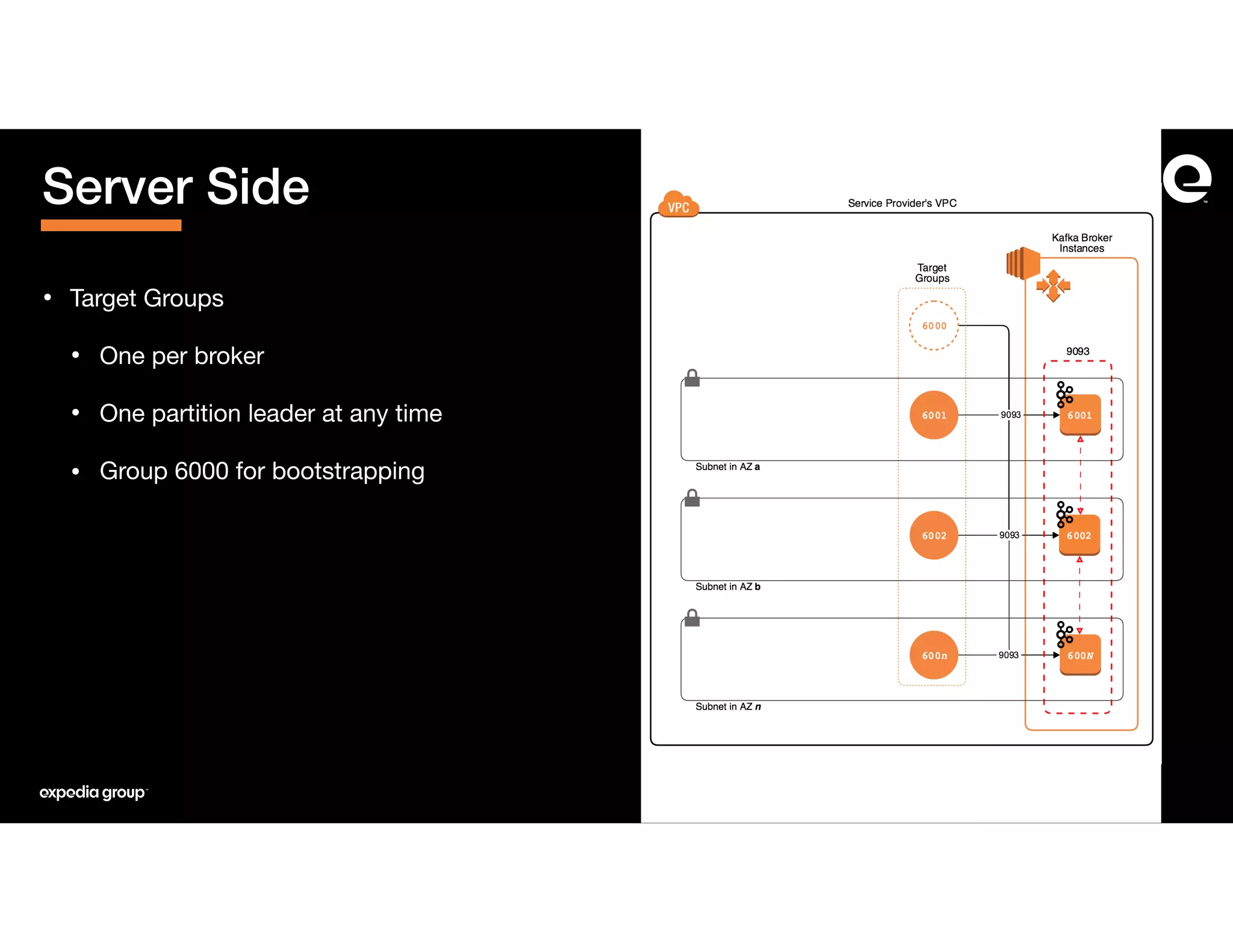
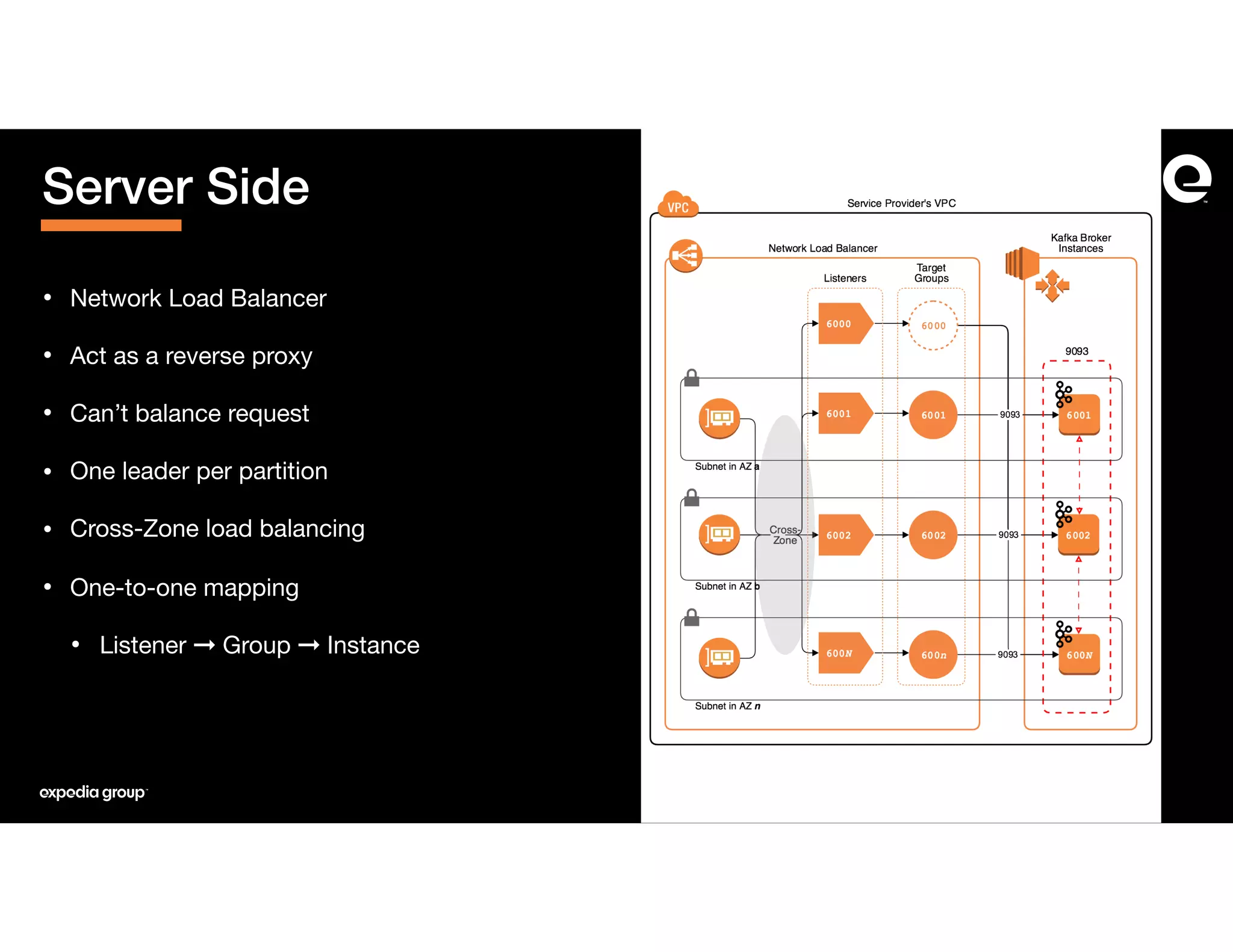
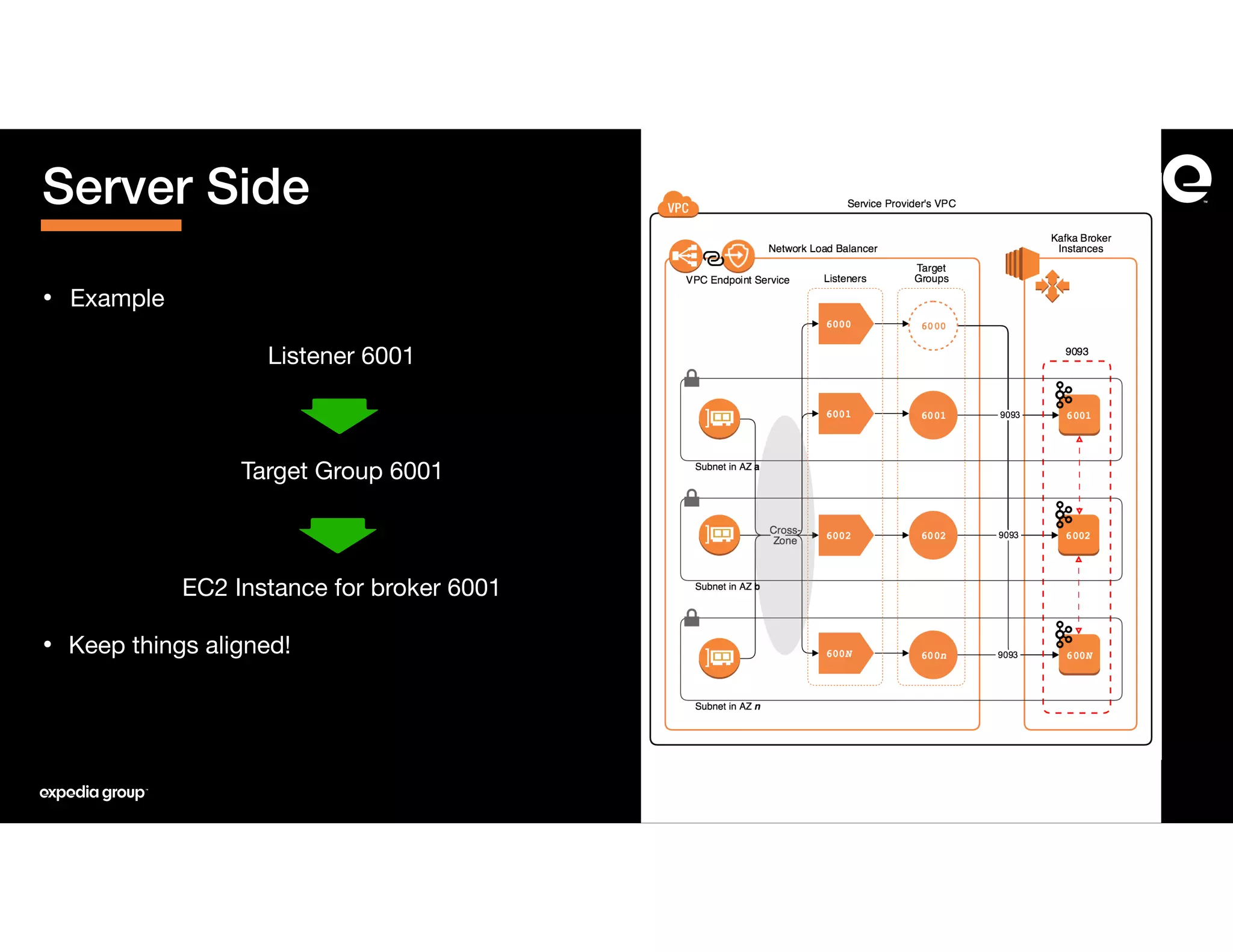
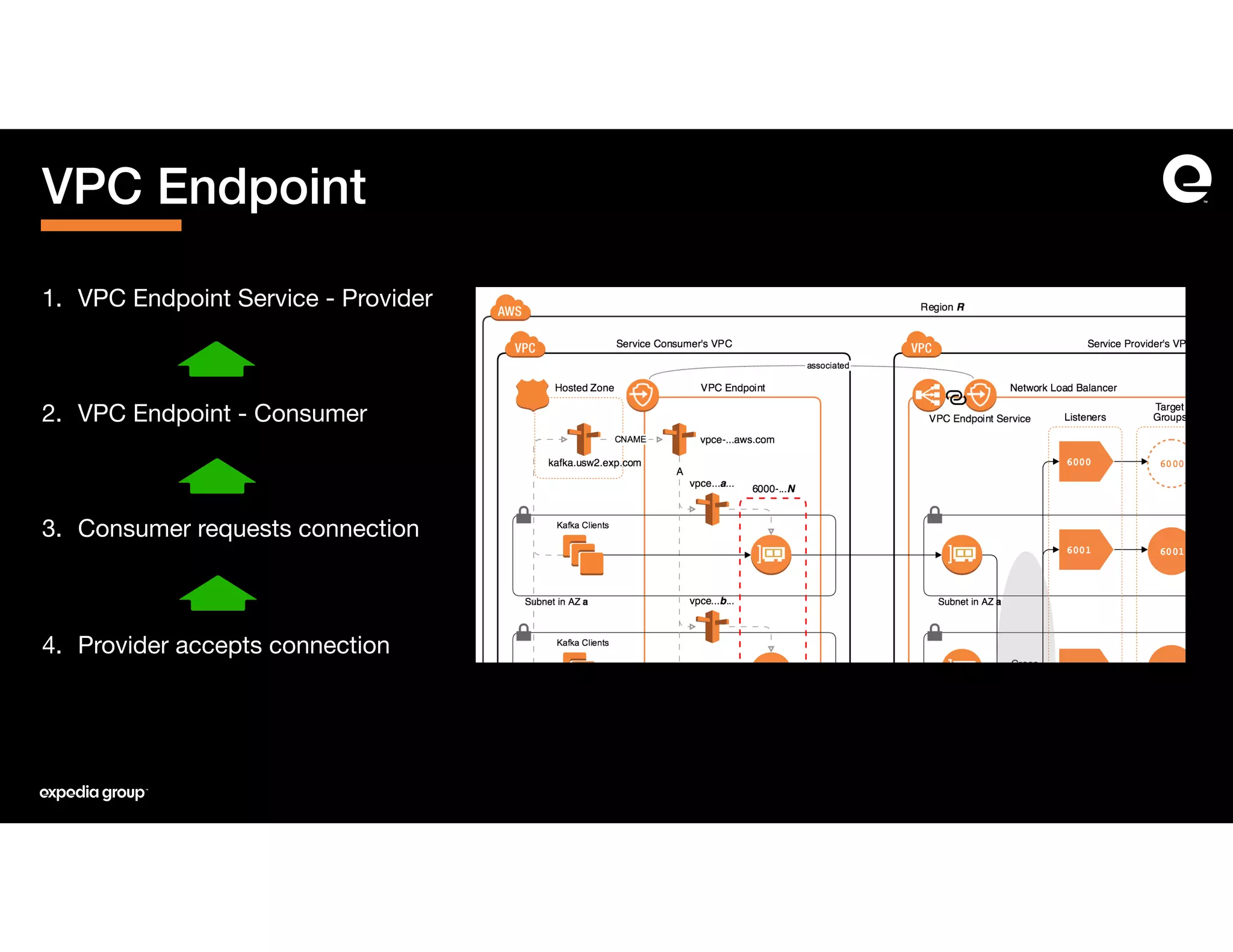
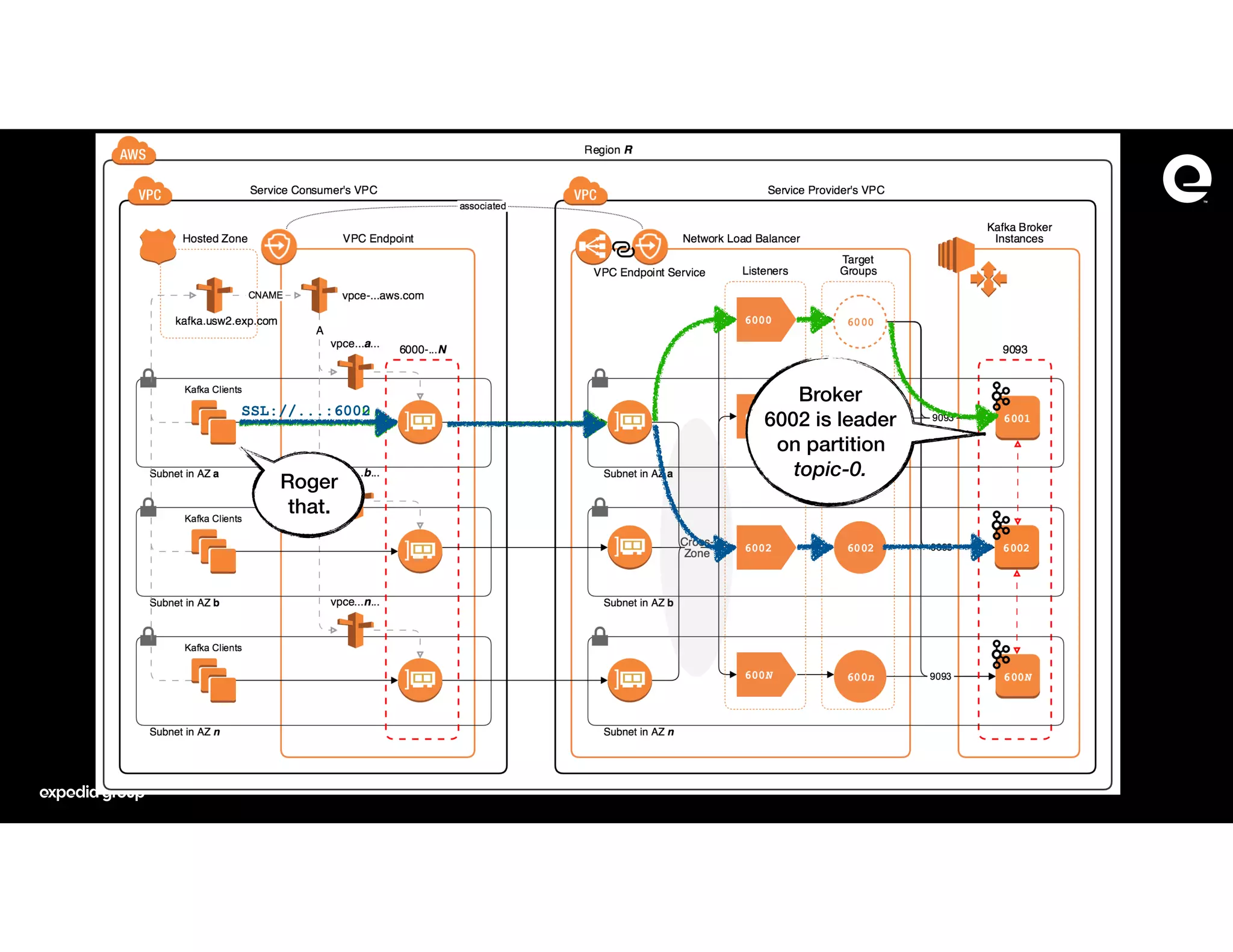
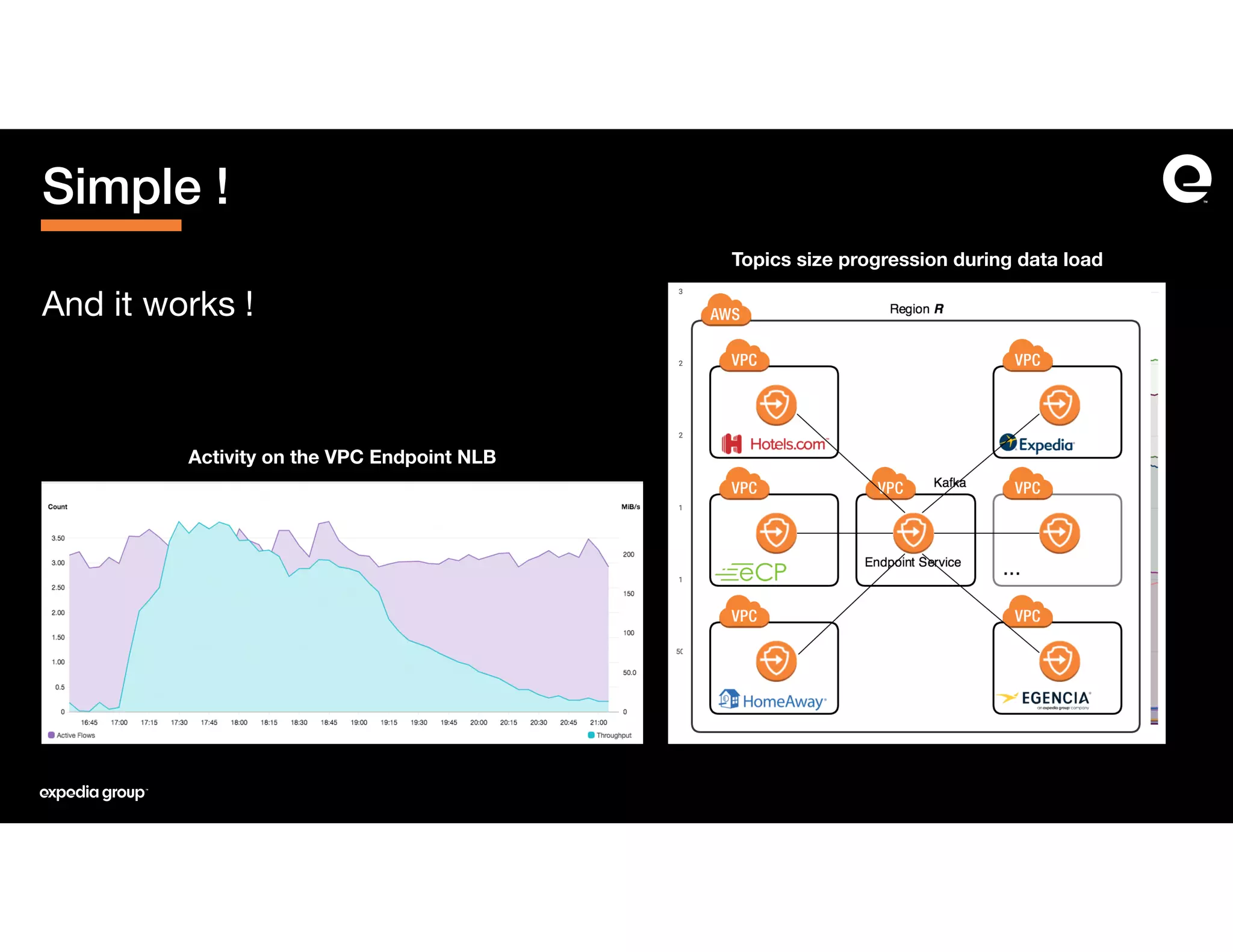
The document discusses how Expedia Group connected Kafka across multiple AWS VPCs while addressing challenges such as overlapping IP spaces and management of numerous peerings. They proposed a solution using AWS VPC endpoints and Network Load Balancers (NLB) to facilitate secure and efficient communication without the need for VPC peering or internet exposure. The key takeaways highlight the VPC endpoint's viability for distributed systems, improving security and resilience in data transmission.