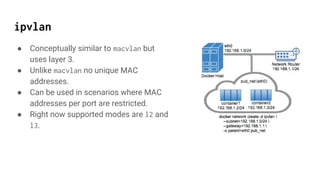
macvlan and ipvlan allow VMs and containers to have direct exposure to the host network by assigning them their own MAC/IP addresses without requiring a bridge. macvlan uses MAC addresses to separate traffic while ipvlan uses layer 3. Both are lighter weight than bridges. macvlan is commonly used in bridge mode to allow communication between VMs/containers on the same host, while ipvlan may be preferred when MAC limits are in place or for untrusted networks.