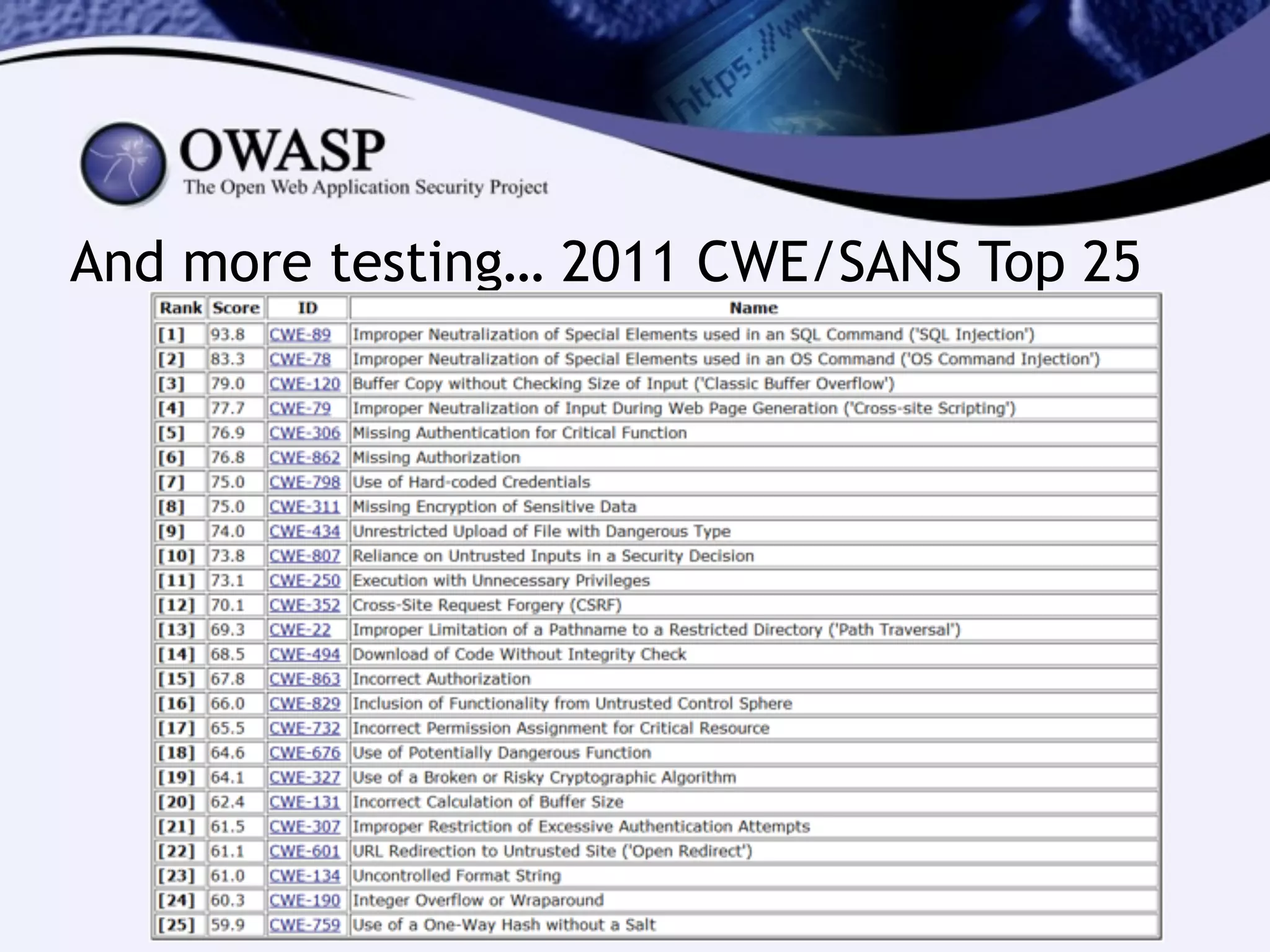
The document discusses the importance of web application security, highlighting that data breaches can be costly, averaging $5.5 million. It emphasizes the need for security testing, code reviews, and implementing a secure development lifecycle (SDL) to avoid common vulnerabilities. The text also advocates for collaboration between developers and security teams to ensure effective security practices are integrated into the development process.