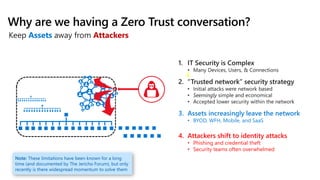
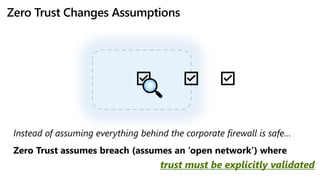
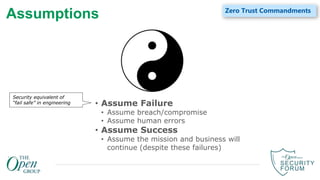
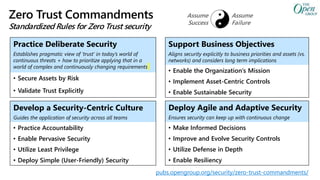
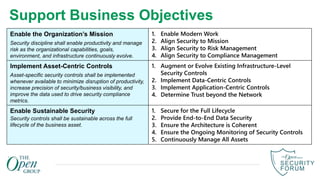
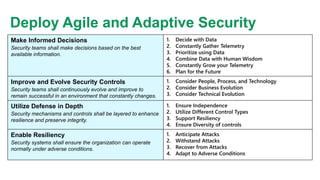
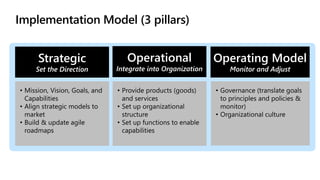
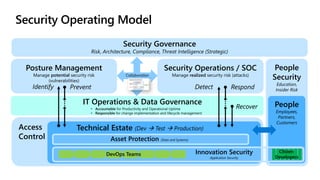
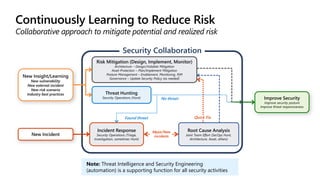
The document provides an overview of zero trust concepts including:
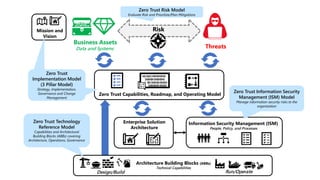
- Zero trust commandments that establish rules and cultural tenets for a zero trust strategy.
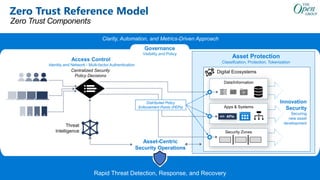
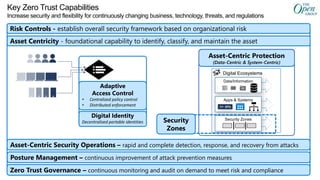
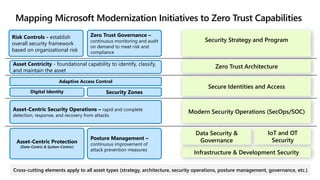
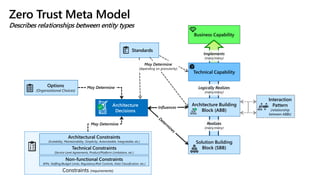
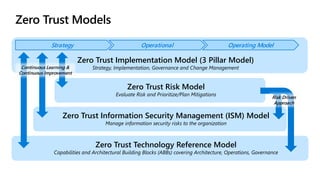
- A zero trust reference model that outlines key zero trust components and capabilities for designing and implementing zero trust.
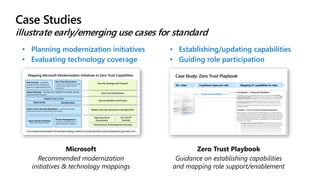
- Case studies that illustrate how organizations can map their initiatives and technologies to zero trust capabilities.
















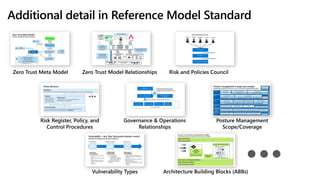




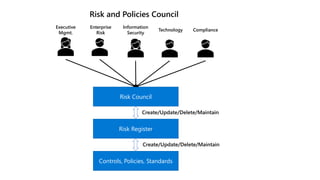
![Standard
Clearly define the
expected outcome,
reasons/risks, and
scope of the policy
Control Procedures
describe best practices on how to implement and assess compliance with the
standards and requirements. [often grouped into baseline(s)]
Risk Register
Ensures that security risk is linked to organizational risk management frameworks and methodologies
Policy Structure
Requirements
specify details on how the standard should be
interpreted and implemented](https://image.slidesharecdn.com/tog-ztcommandmentsandreferencemodel-231102172316-05dfcf7e/85/The-Open-Group-ZT-Commandments-and-Reference-Model-pptx-38-320.jpg)