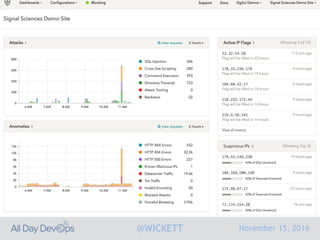
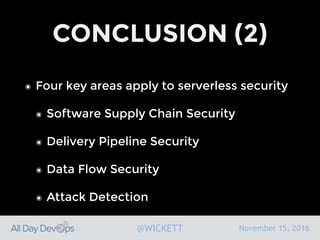
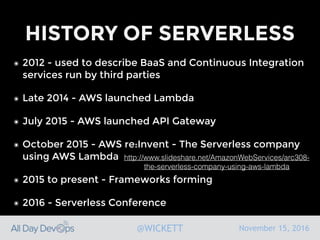
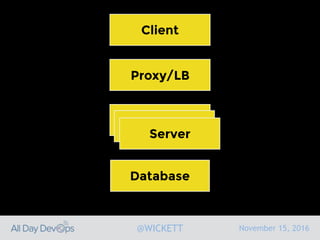
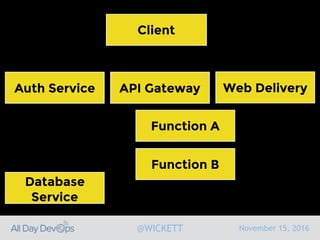
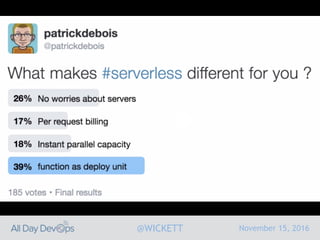
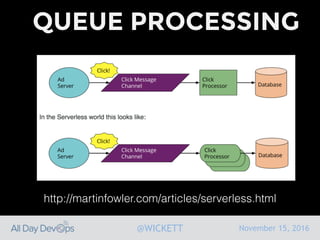
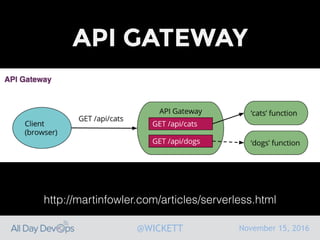
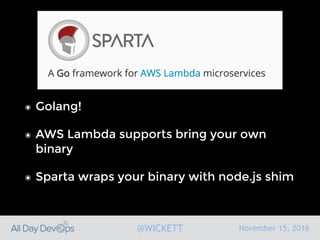
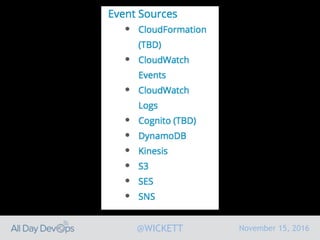
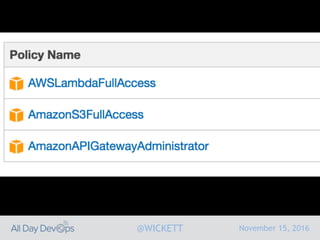
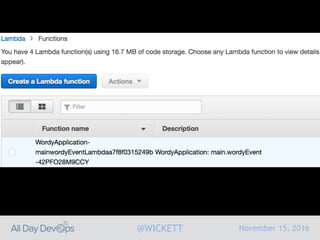
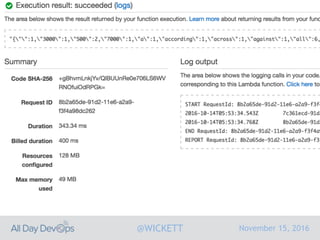
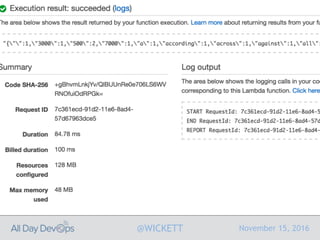
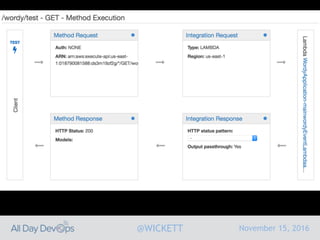
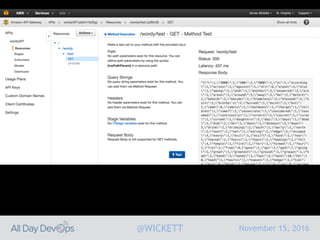
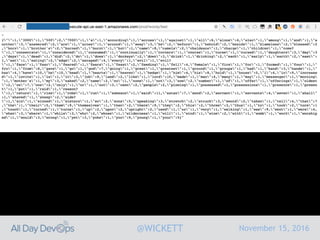
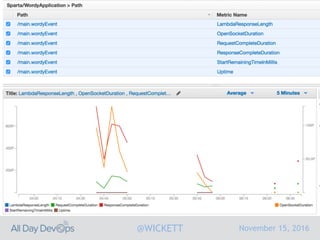
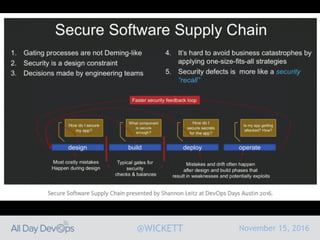
Serverless computing encourages deploying applications as small functions that are triggered by events, coupled with third party services that allow running applications without managing servers. While security is easier in some ways with serverless, it is also harder due to factors like increased vendor lock-in and attack surface. The document discusses key areas of security for serverless including software supply chain security, delivery pipeline security, data flow security, and attack detection.