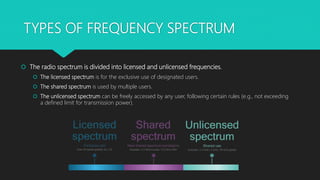
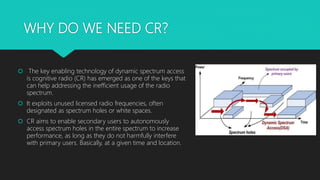
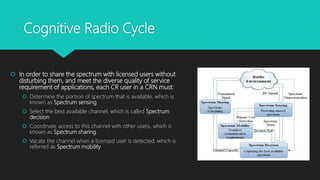
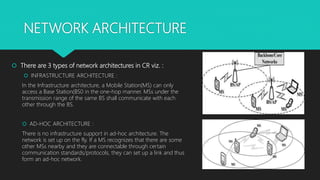
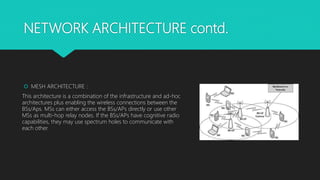
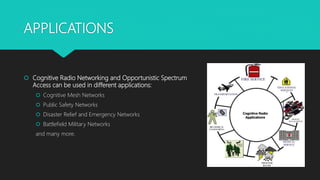
Cognitive radios are smart radios that can sense their environment and adjust their transmission parameters accordingly. They were first proposed in 1999 to more efficiently utilize limited radio spectrum. Cognitive radios operate in a cycle of spectrum sensing, decision, sharing, and mobility. They can access licensed spectrum as secondary users as long as they do not interfere with primary users. This allows for increased spectrum utilization. Cognitive radios have characteristics of cognitive capability, reconfigurability, and self-organization. They enable applications such as cognitive mesh networks and public safety networks through techniques like dynamic spectrum management.