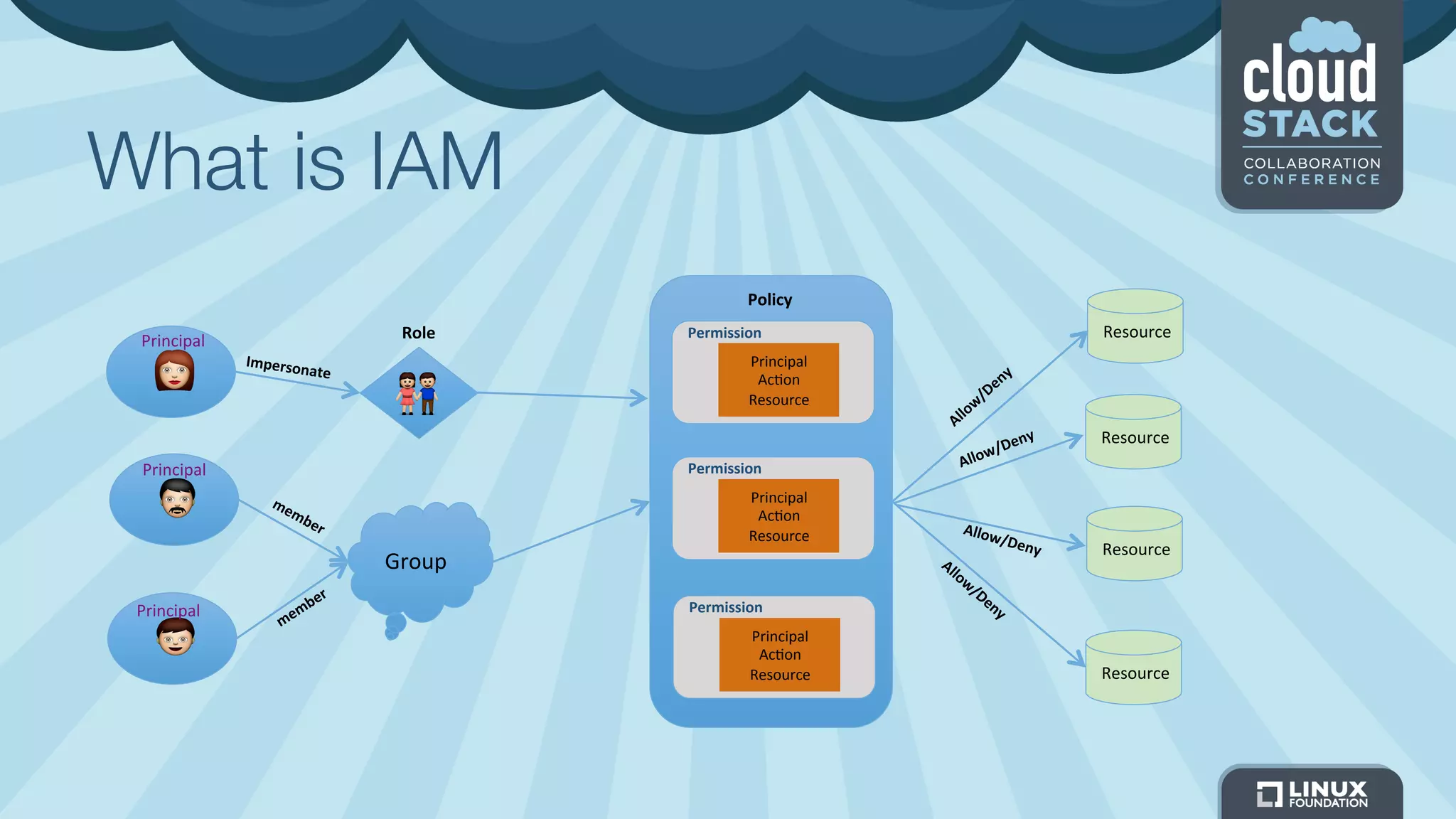
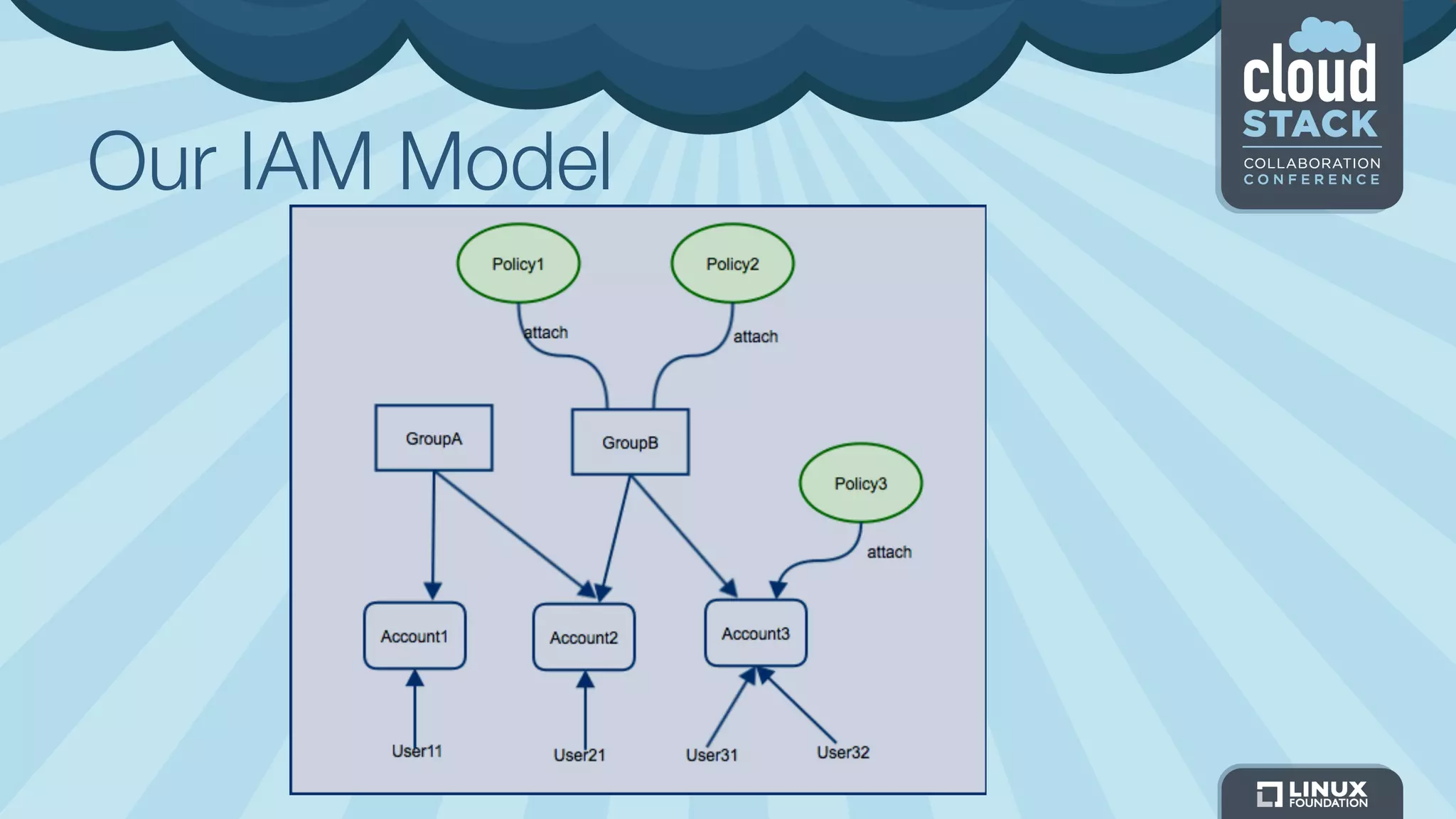
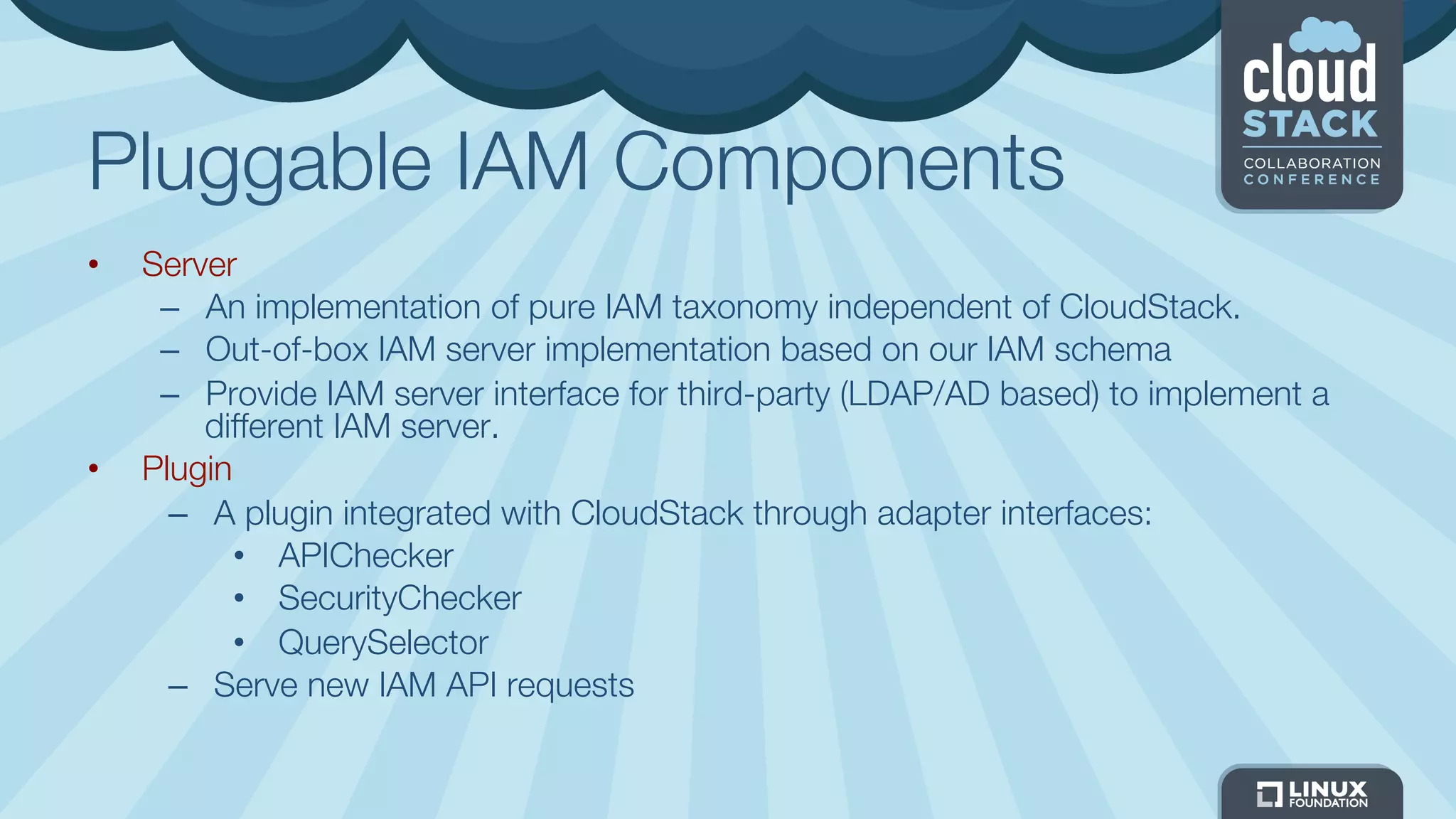
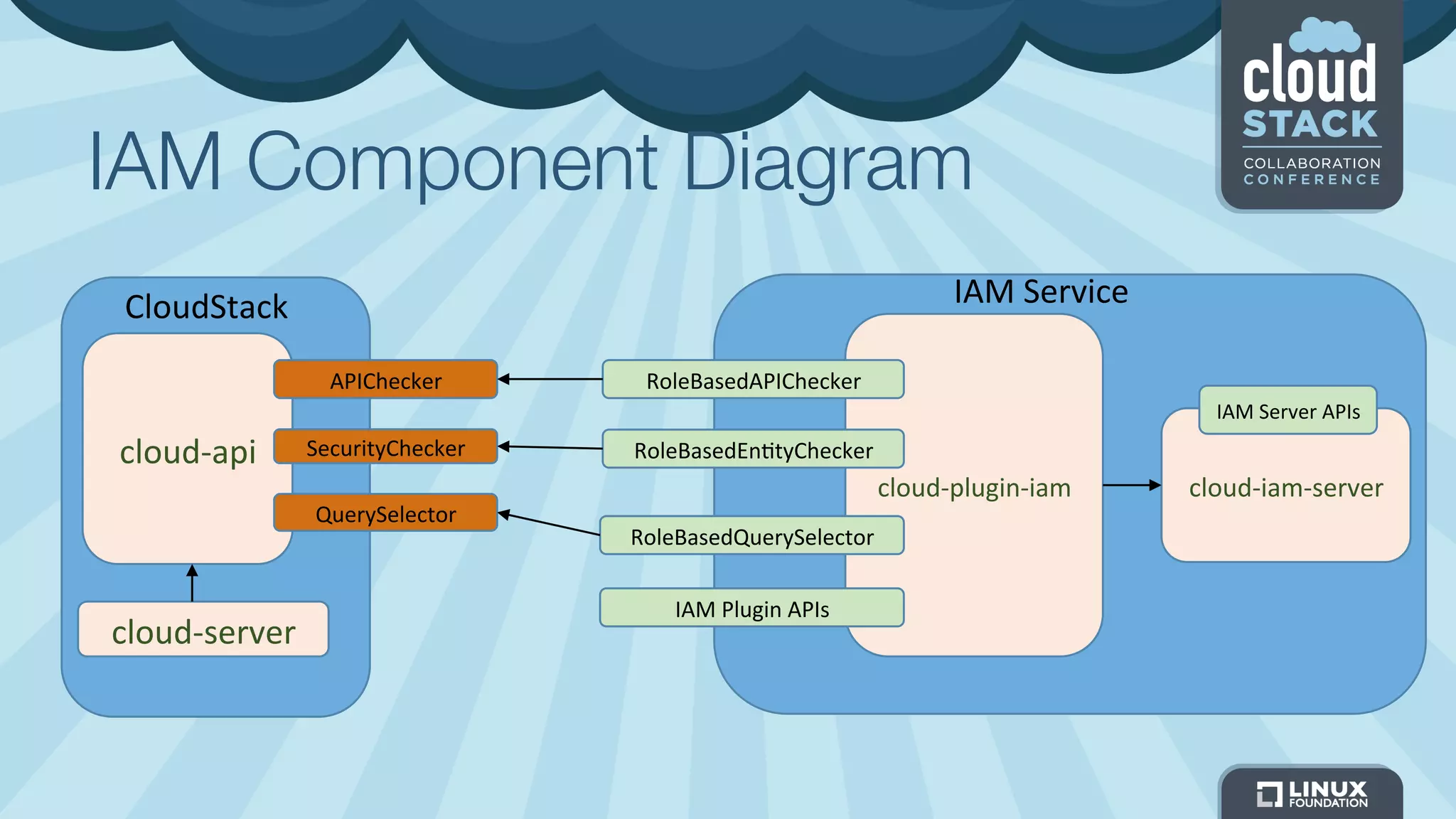
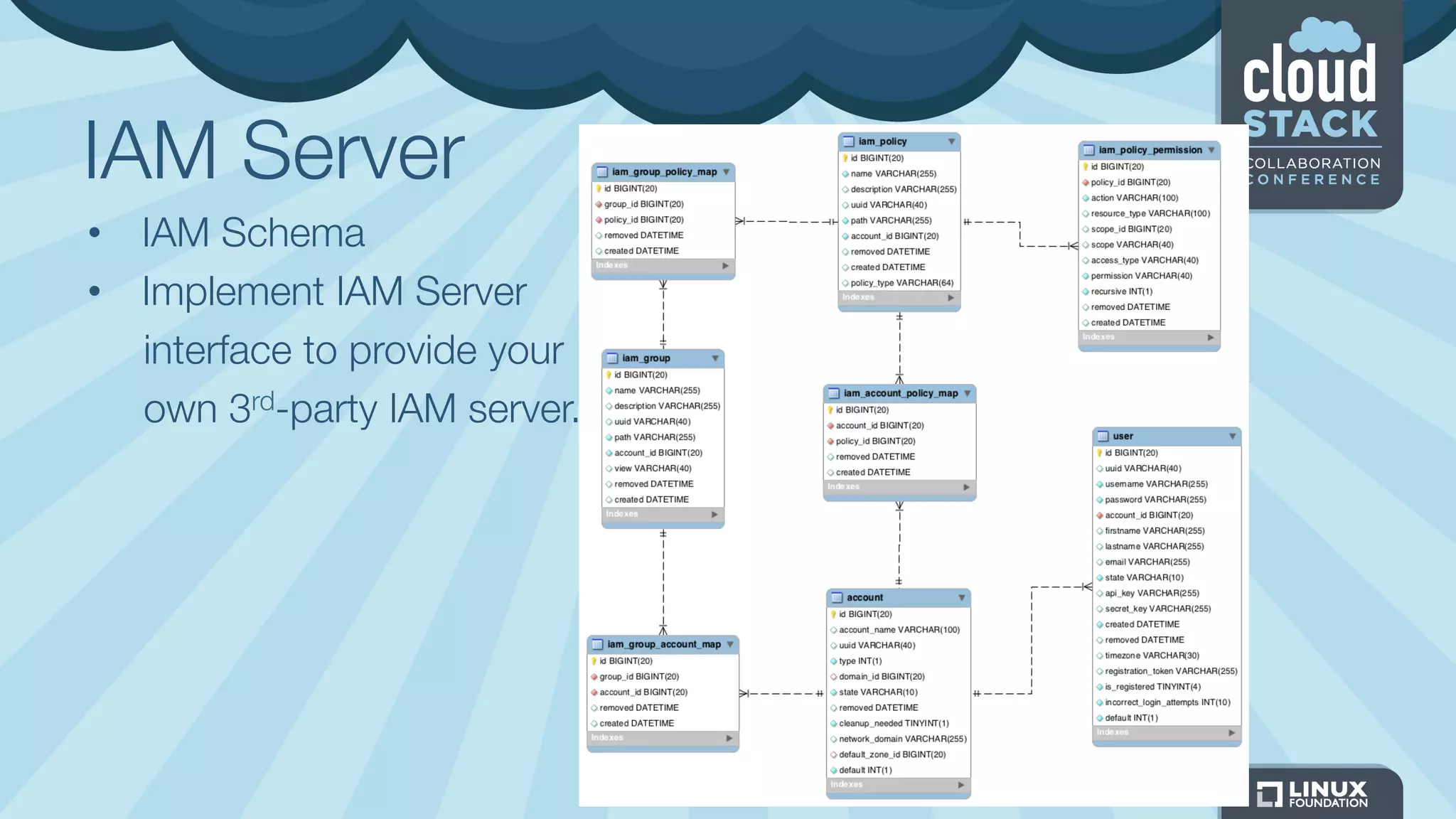
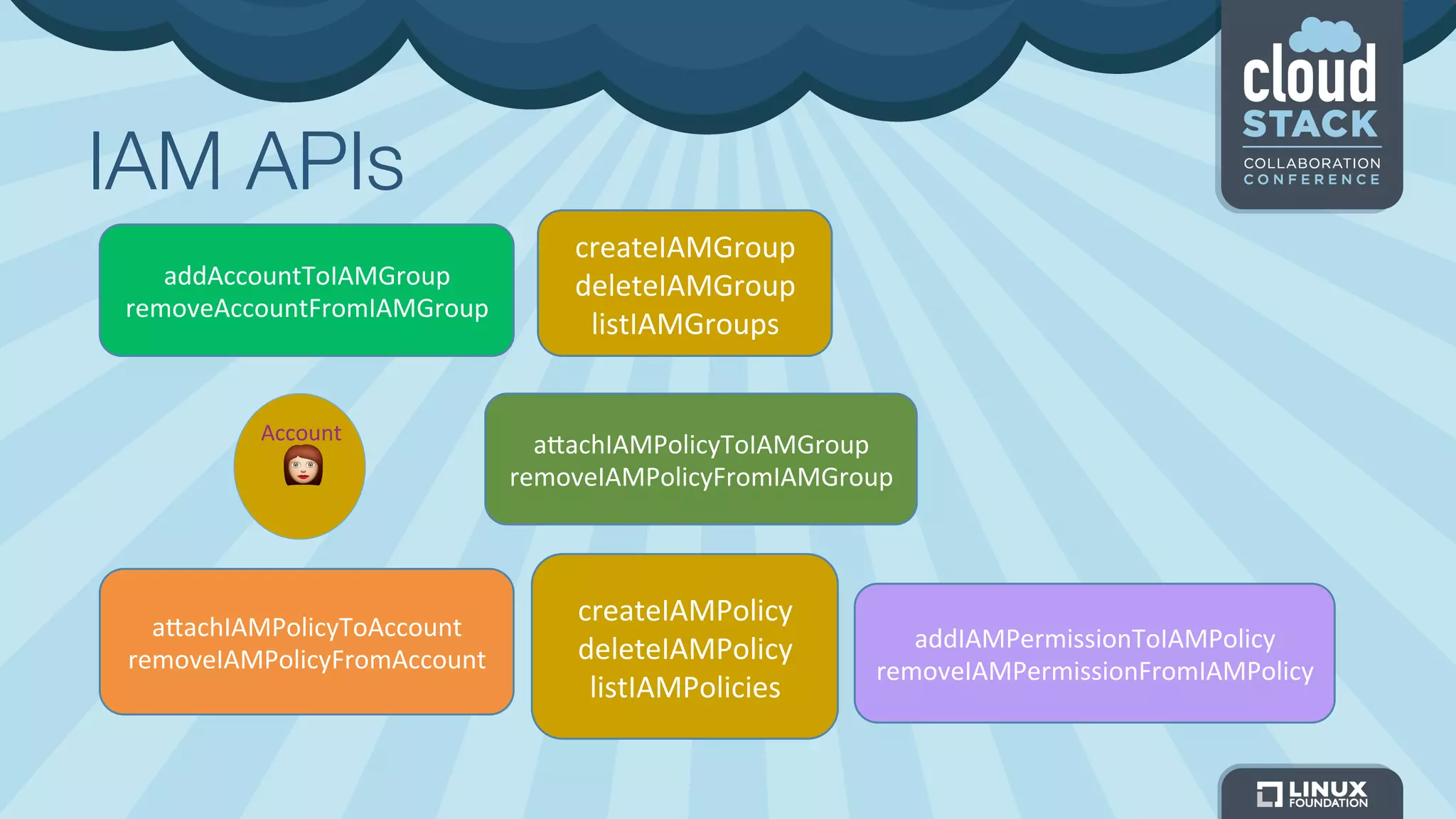
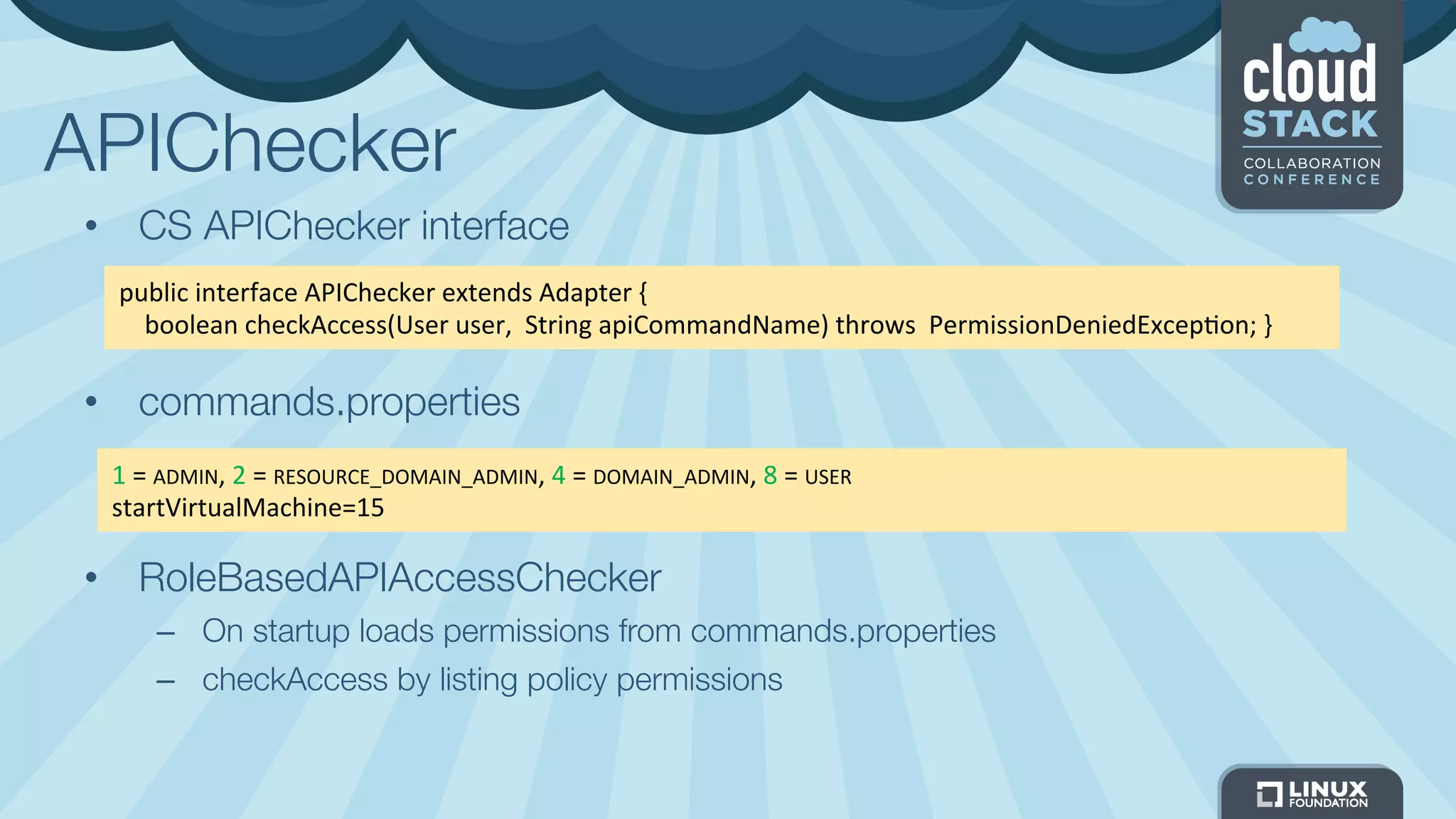
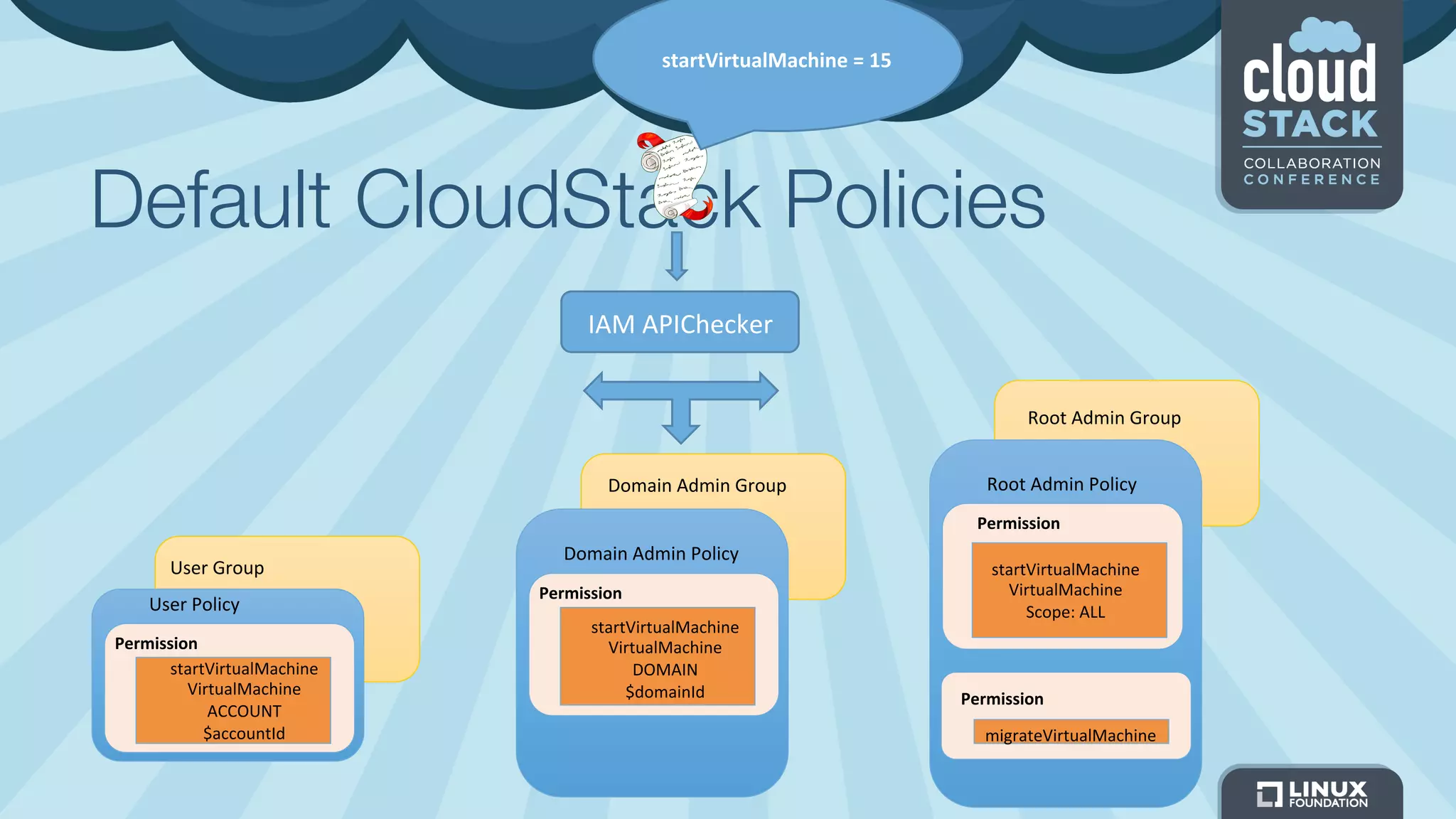
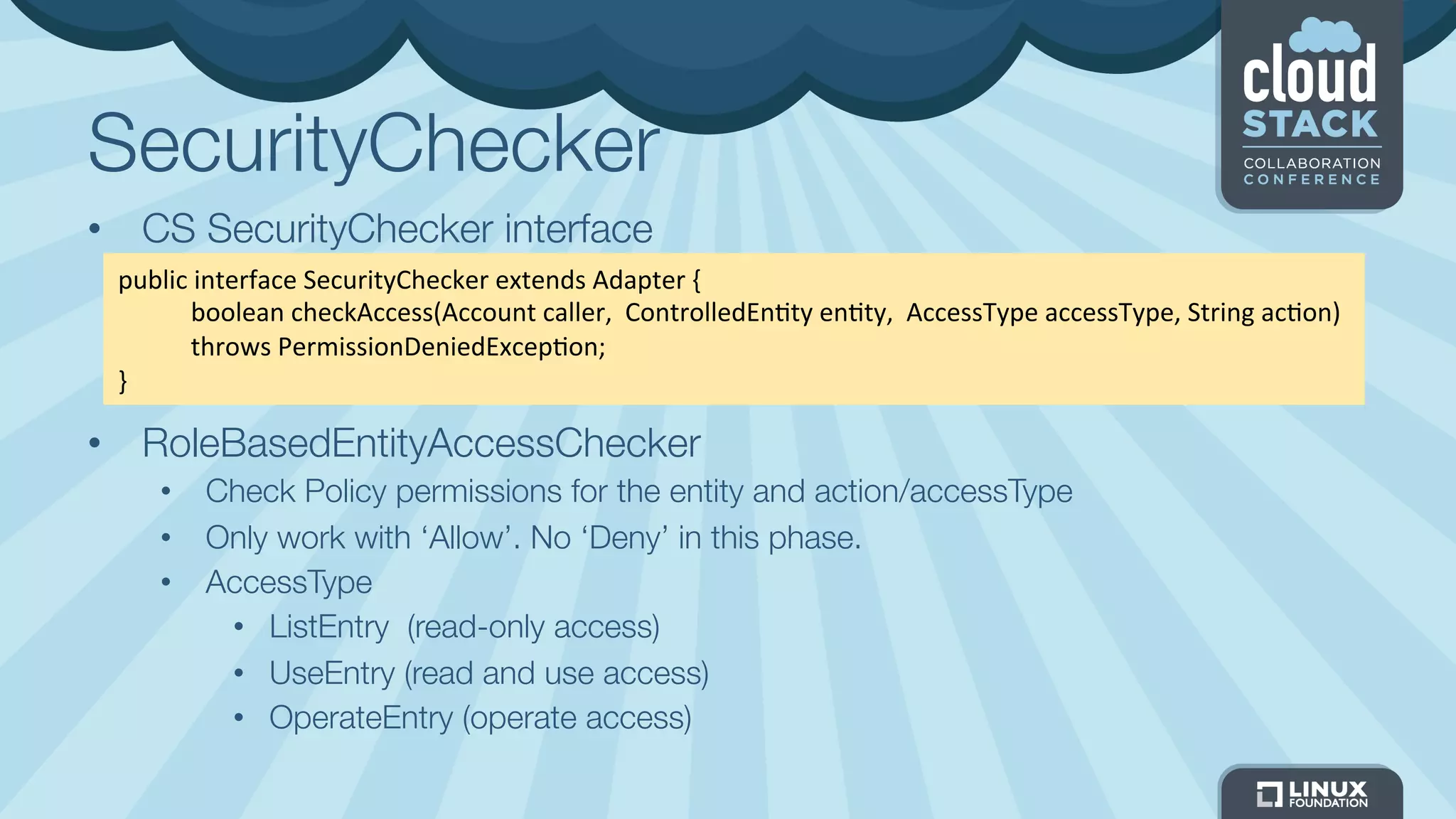
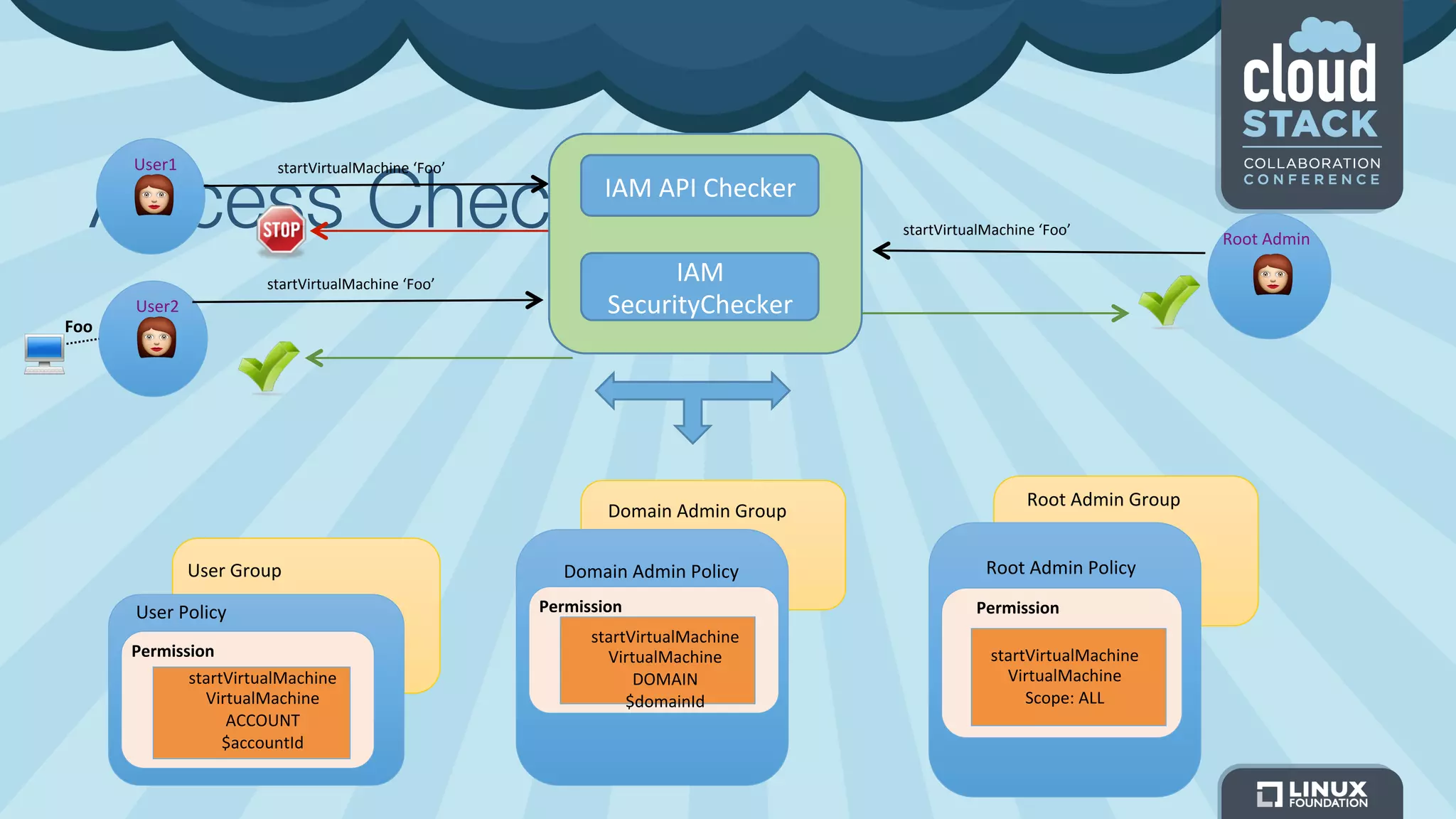
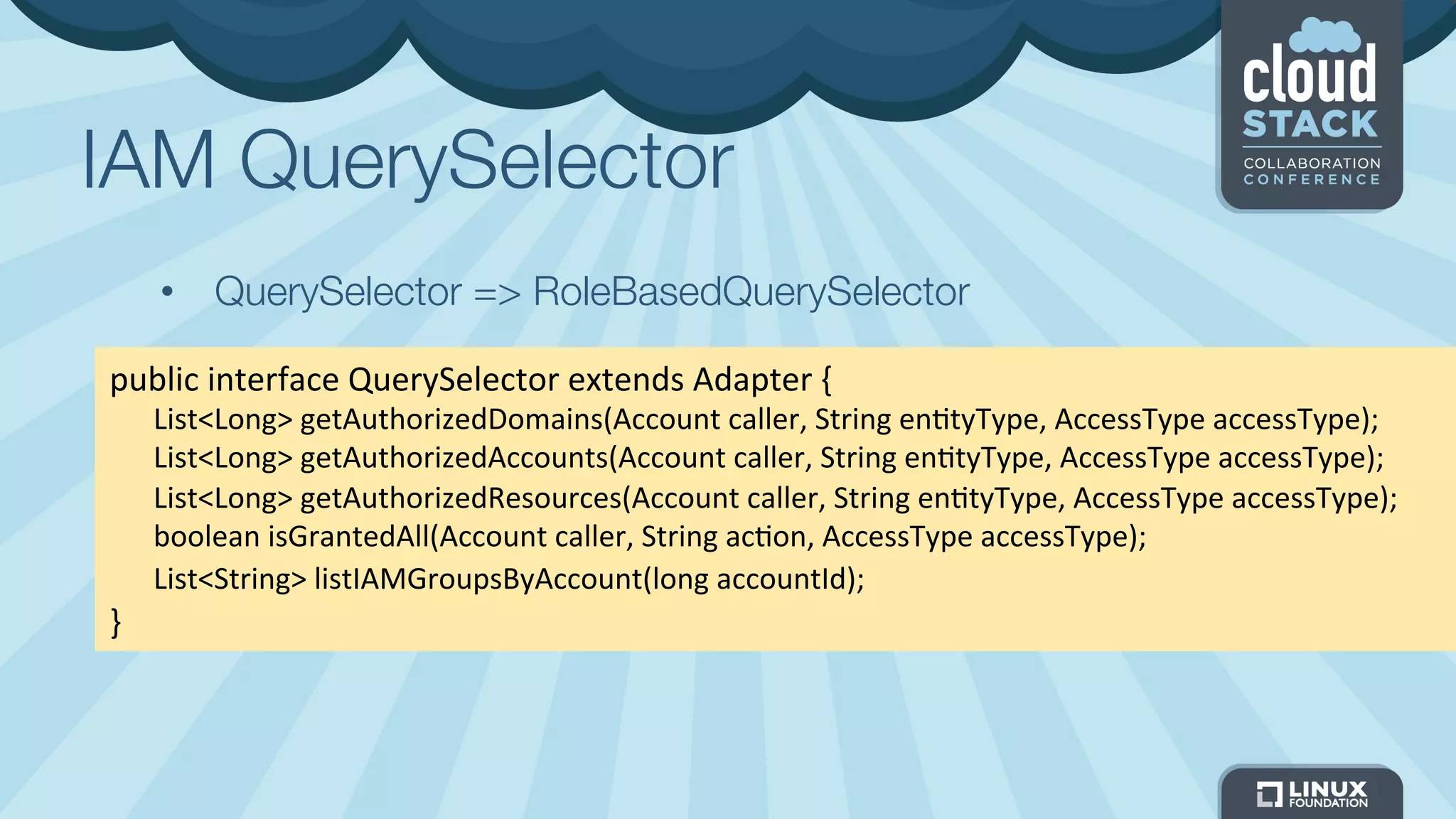
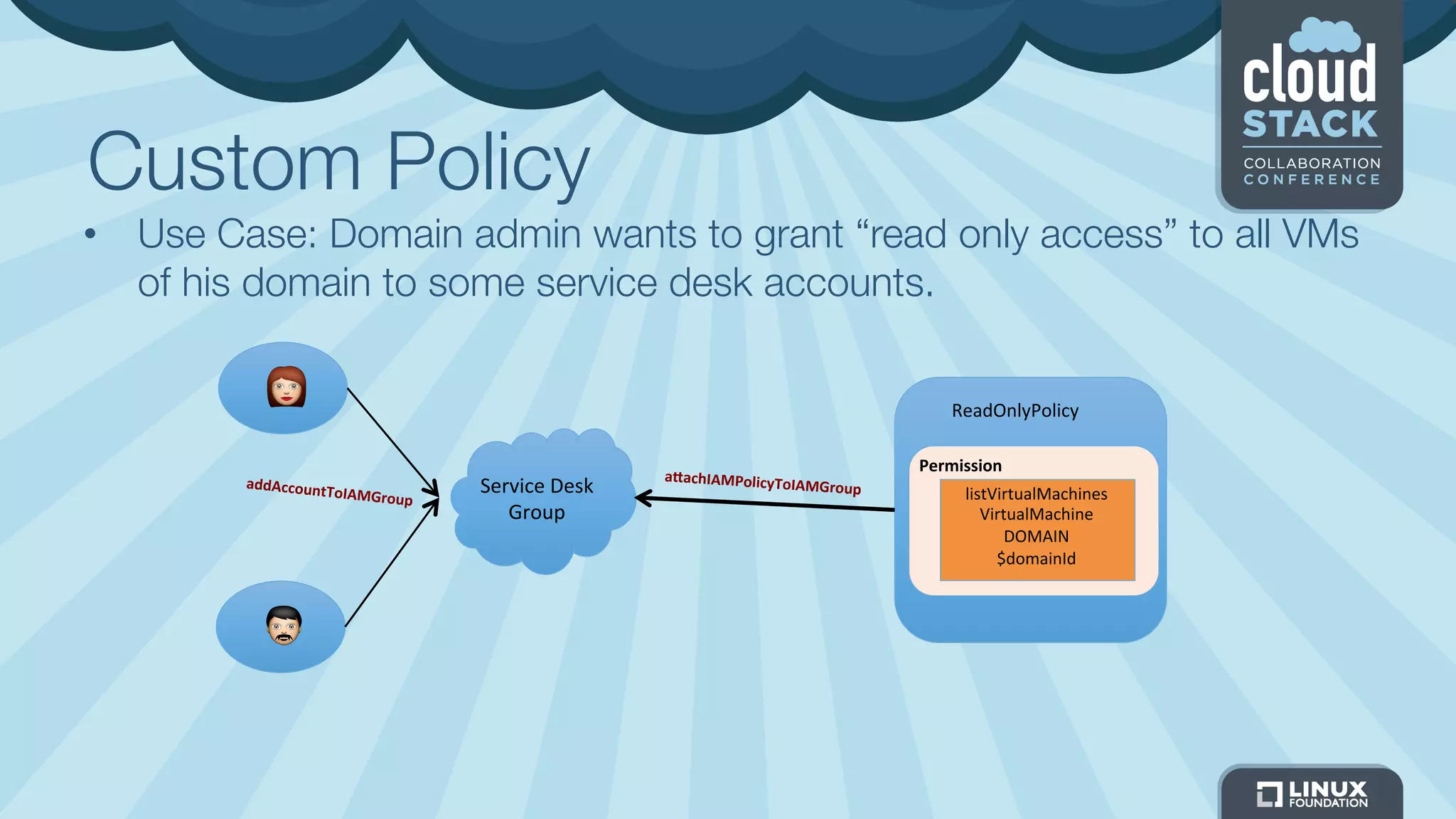
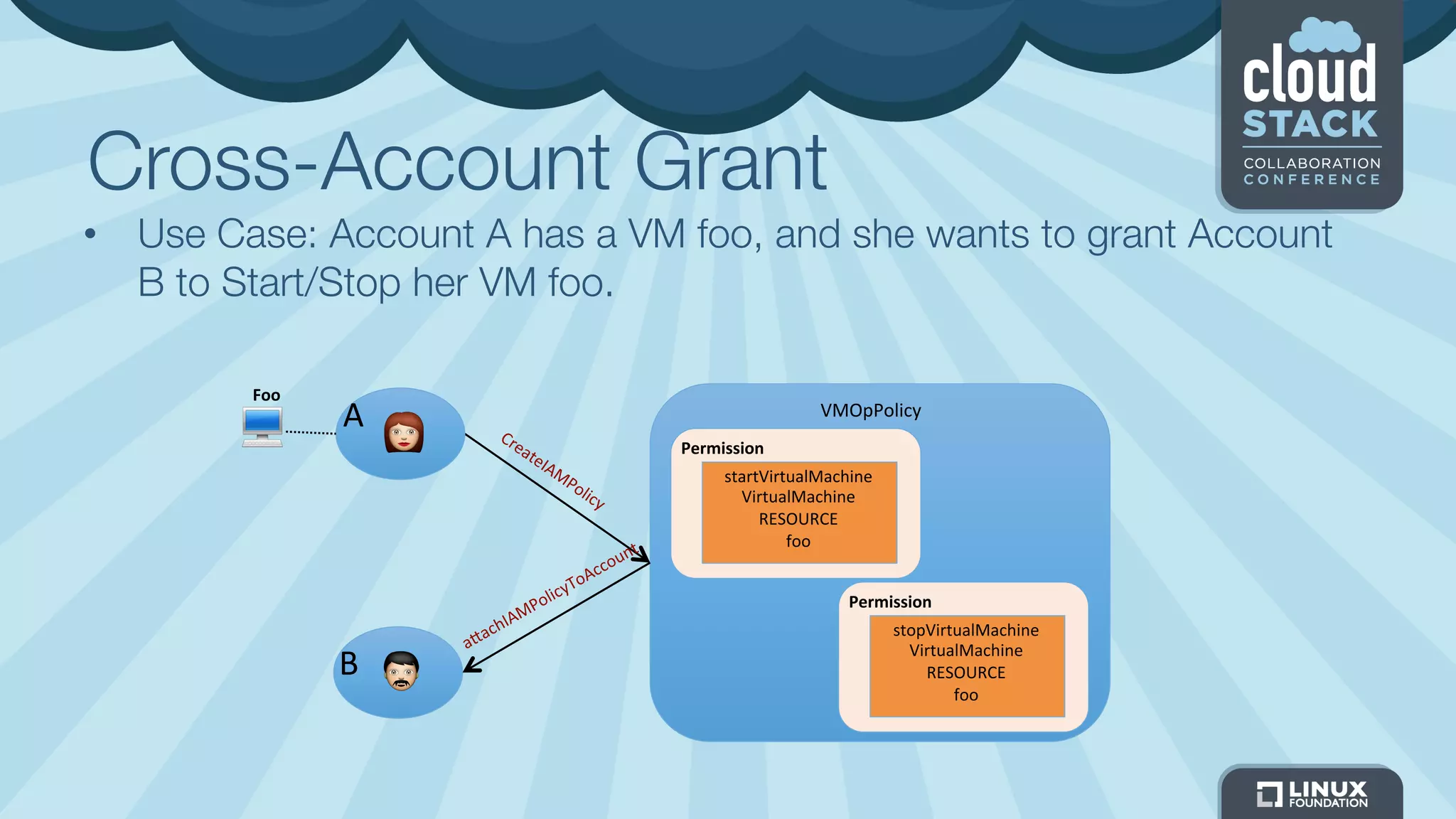
The document discusses CloudStack's plans to implement an Identity and Access Management (IAM) service. It describes CloudStack's current limited IAM capabilities and the goal to provide a pluggable IAM service. The proposed architecture includes hosting an independent IAM server and integrating an IAM plugin with CloudStack via adapter interfaces. The plugin would support new IAM APIs and policies to control access at the user, group, and resource levels. Example use cases are provided to demonstrate how the IAM service could enable cross-account access policies and role-based access controls.