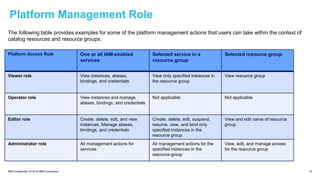
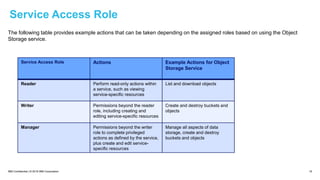
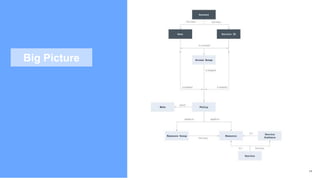
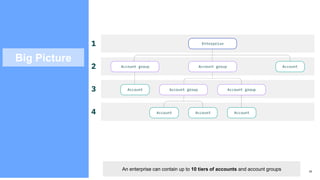
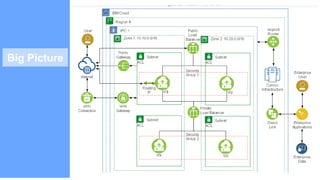
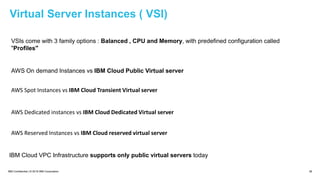
The document provides an in-depth overview of IBM Cloud's Virtual Private Cloud (VPC) offerings, highlighting its features, architecture, and comparison with classic infrastructure. Key topics include identity and access management (IAM), resource organization, security measures, and support tiers, as well as specifics on virtual server instances and connectivity options. It emphasizes IBM Cloud's hybrid capabilities and structure tailored for enterprises looking for robust cloud solutions.