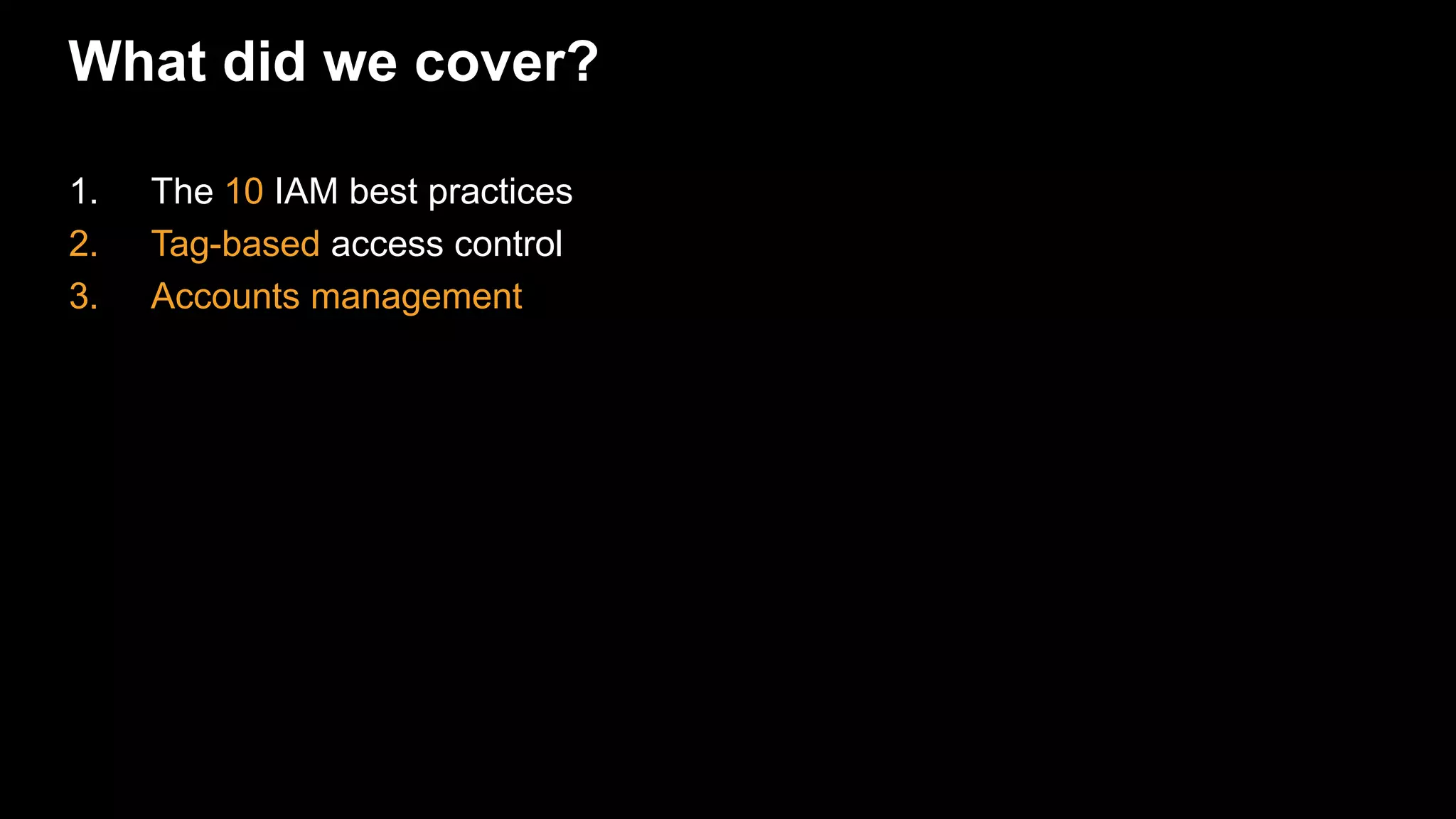
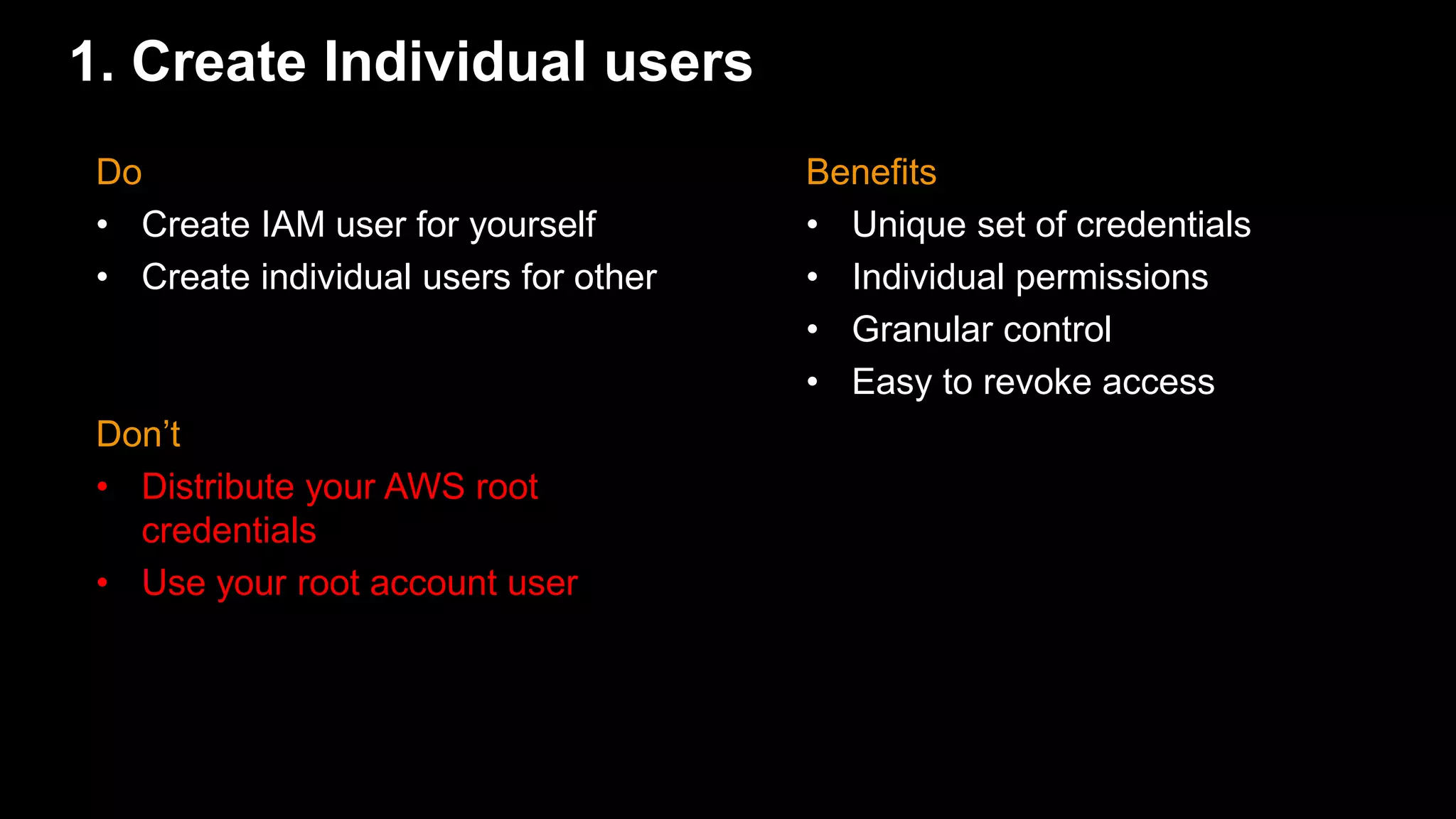
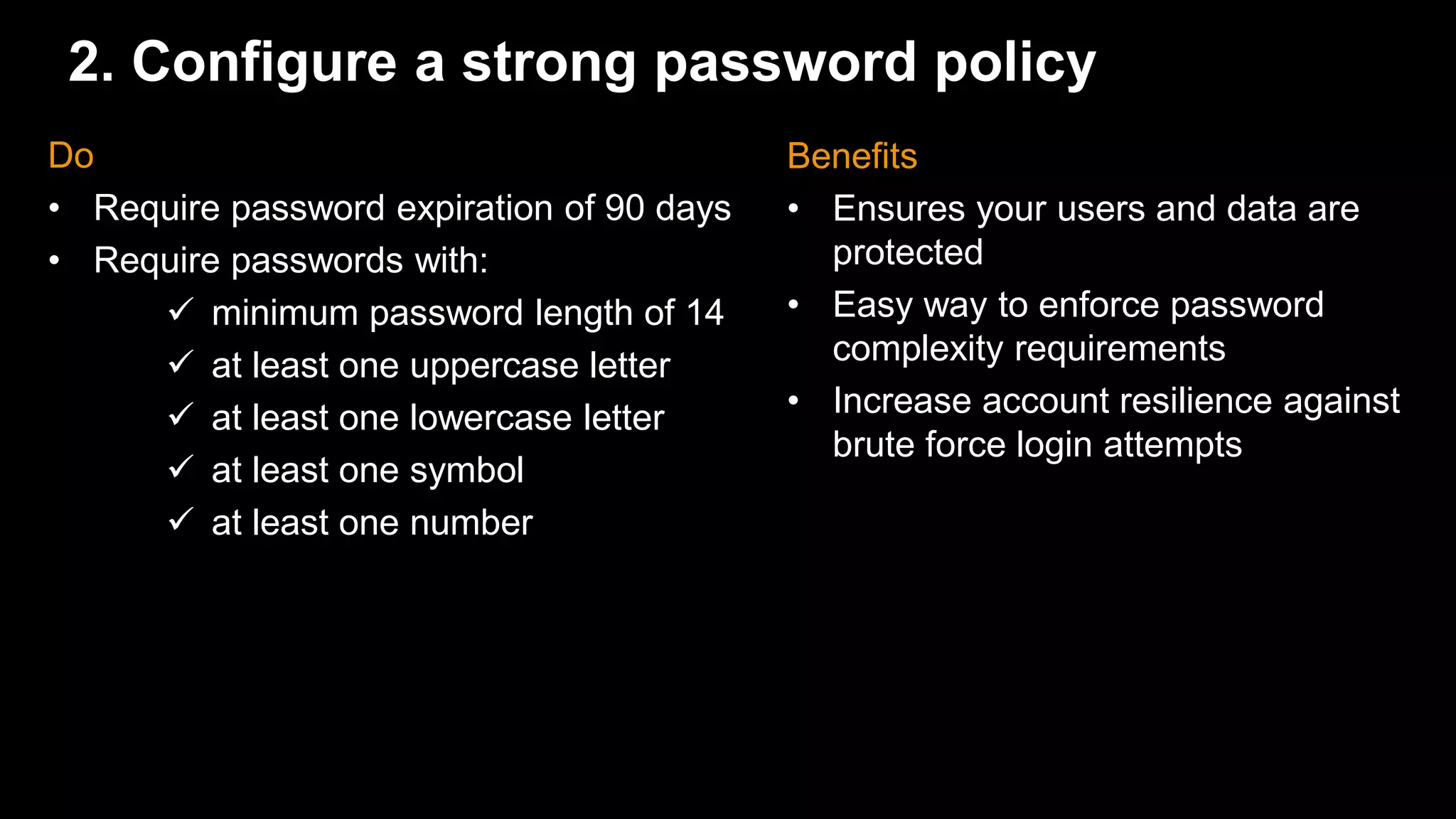
The document provides an overview of AWS Identity and Access Management (IAM) best practices and common use cases. It discusses 10 best practices for IAM including creating individual users, configuring strong password policies, rotating security credentials regularly, enabling MFA for privileged users, managing permissions with groups, granting least privilege, using IAM roles to share access, using IAM roles for EC2 instances, enabling AWS CloudTrail for auditing, and reducing use of root credentials. It also covers using tag-based access control and managing multiple AWS accounts.




![{
"Statement":
{
"Effect": "Allow",
"Action": "ec2:TerminateInstances",
"Resource": "arn:aws:ec2:ap-southeast-1:444455556666:instance/*",
"Condition" : {
“Bool": {"aws:MultiFactorAuthPresent": "true"},
"NumericLessThan":{"aws:MultiFactorAuthAge":"300"},
"IpAddress" : {"aws:SourceIp" : ["10.0.2.0/28", “203.0.113.0/29"]}
}
}
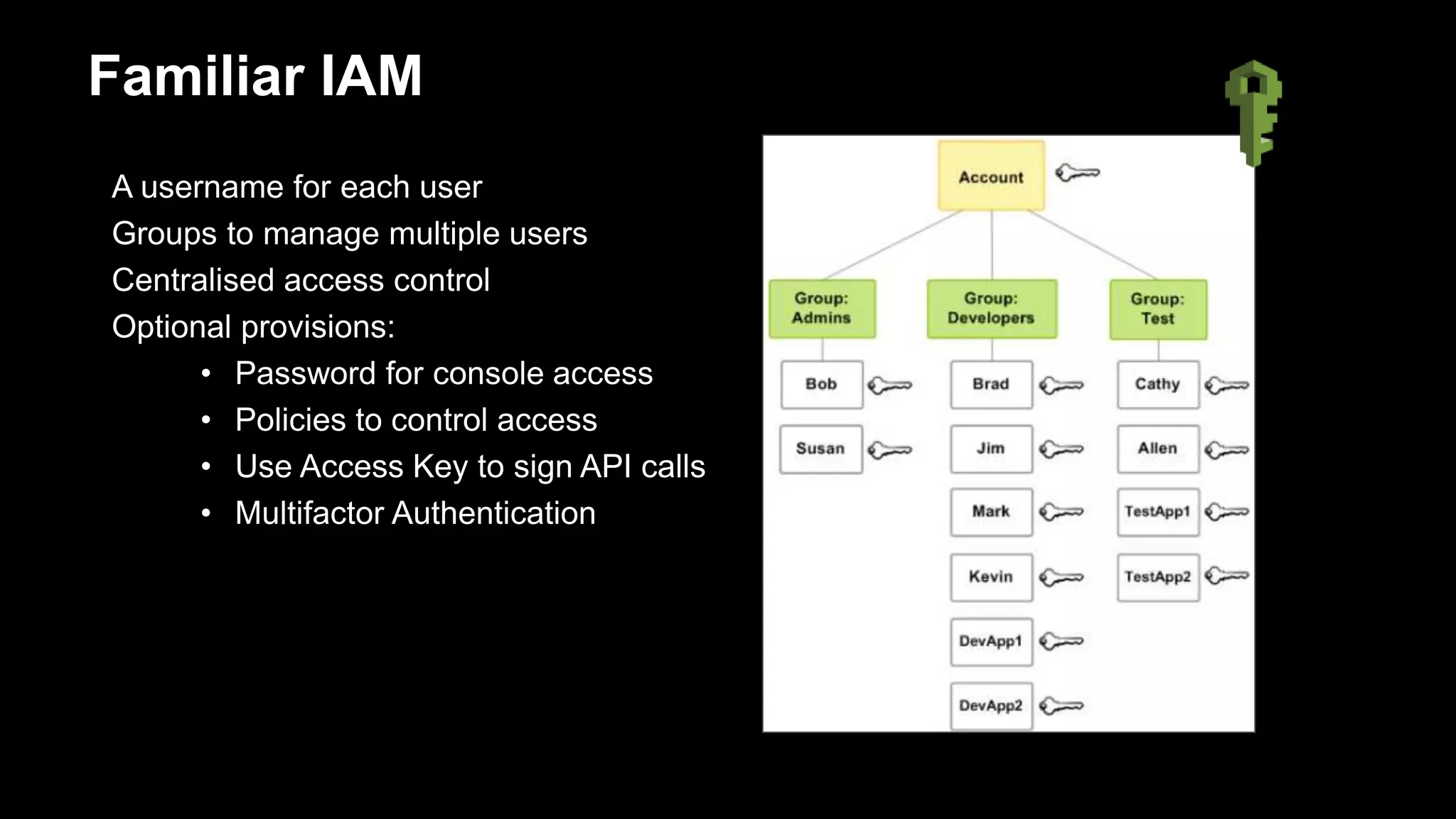
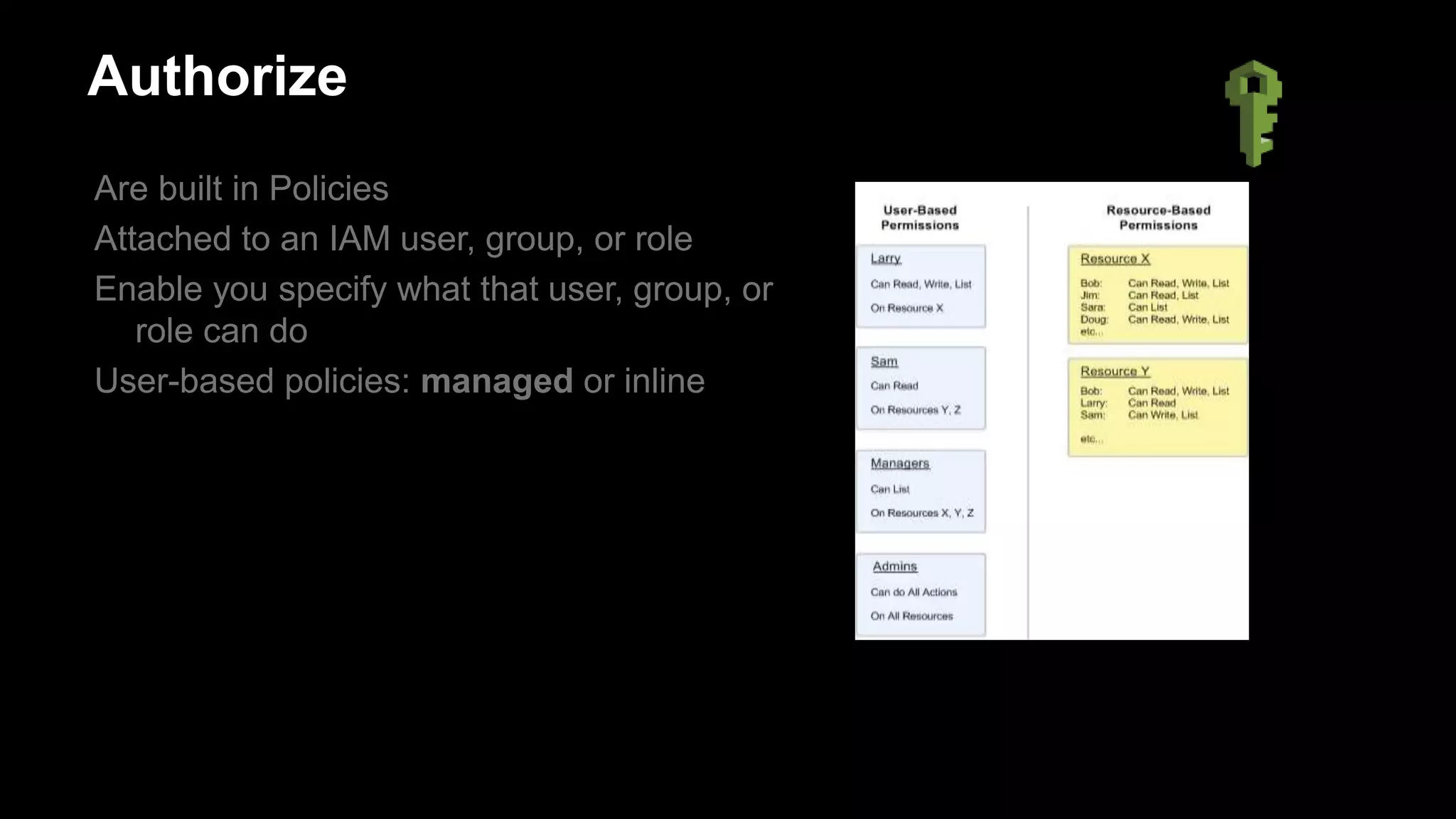
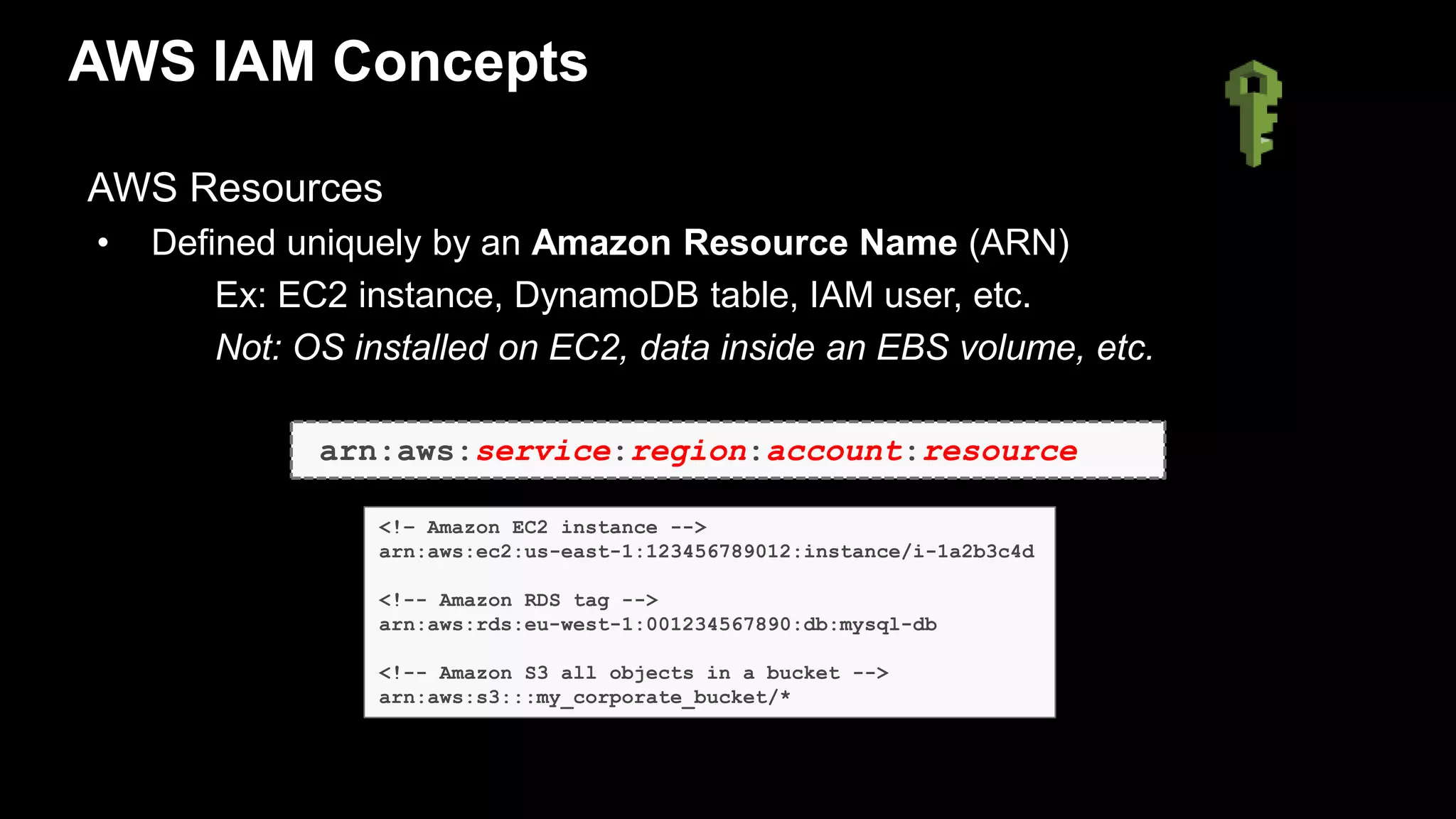
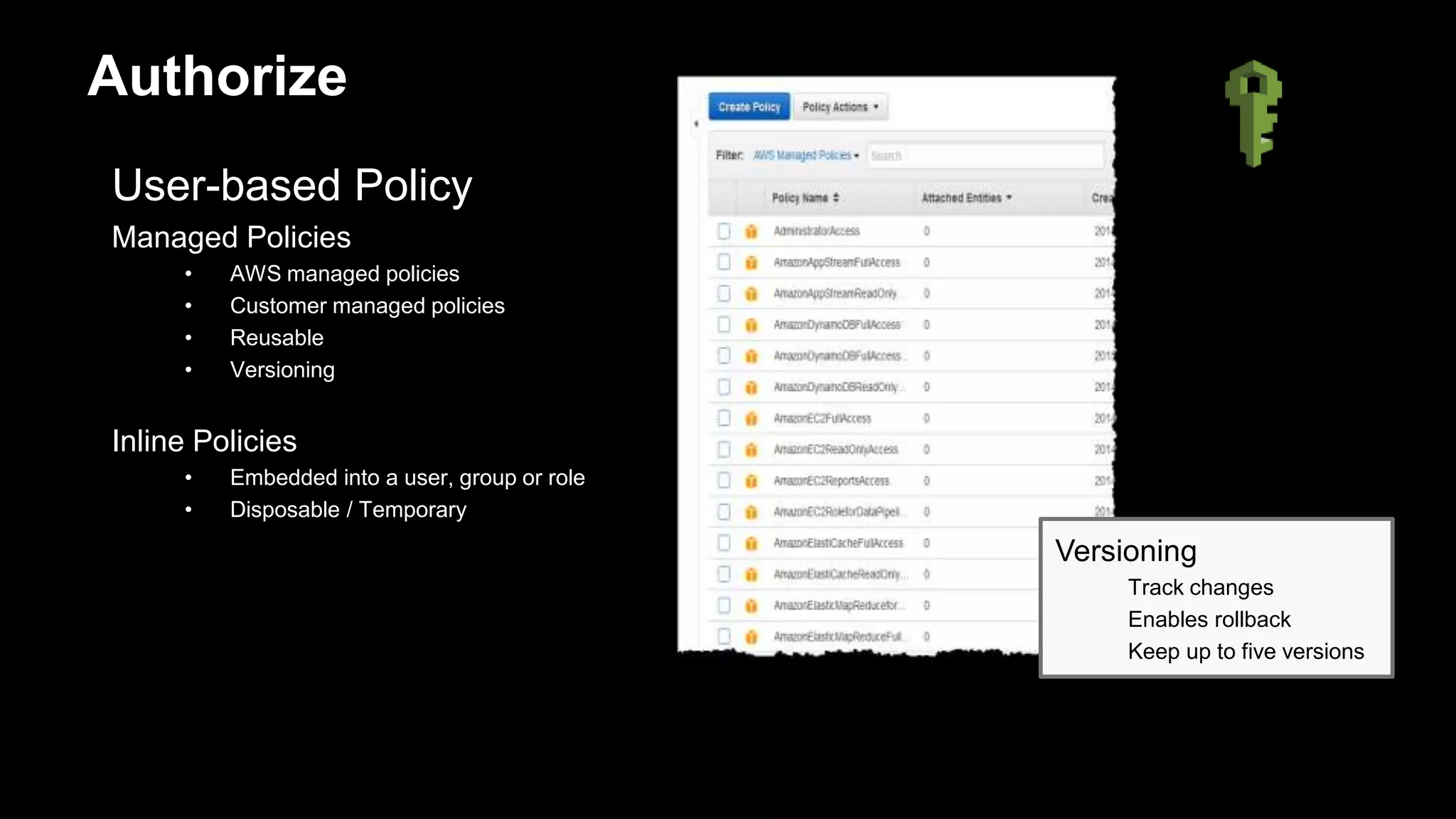
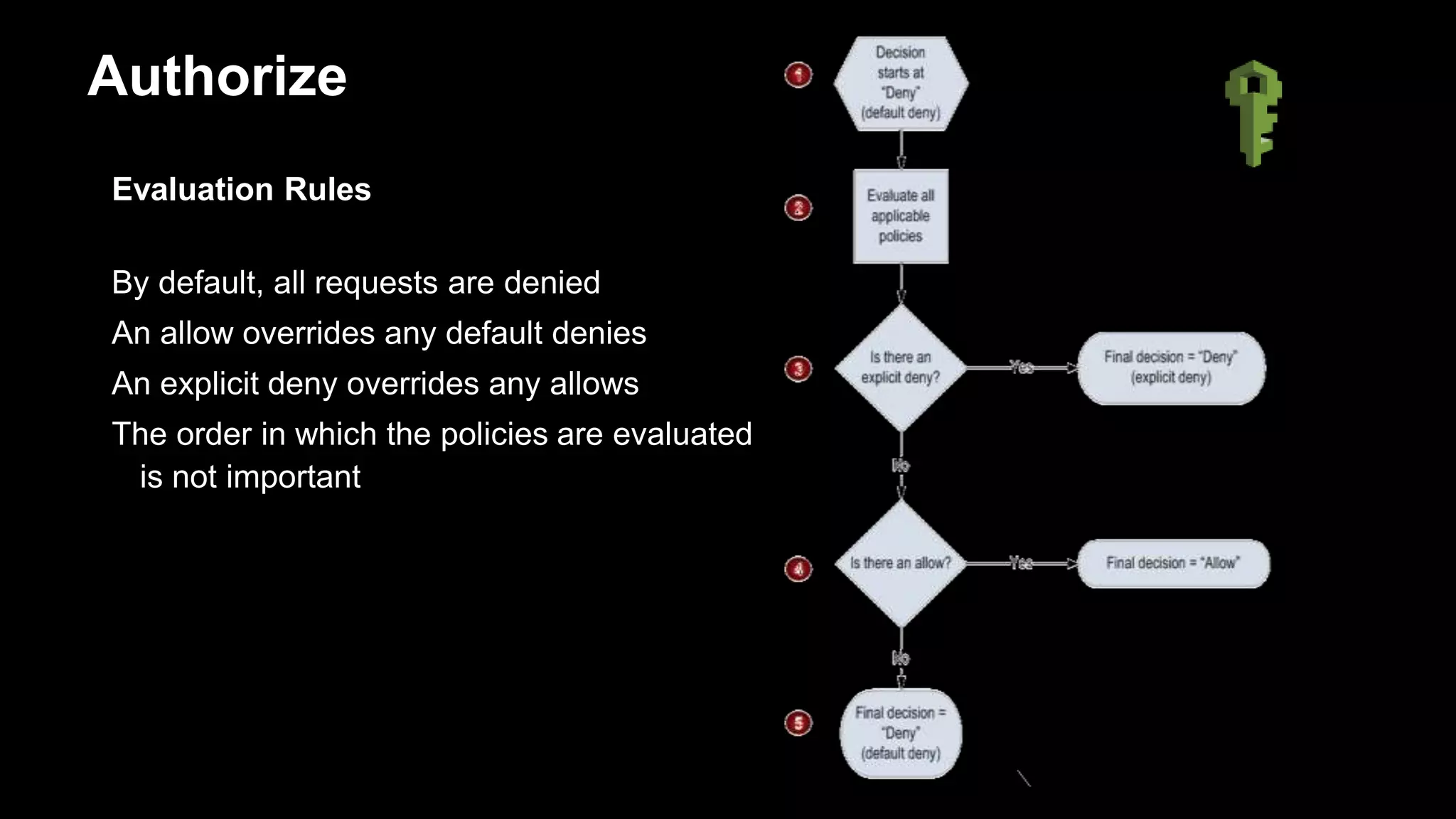
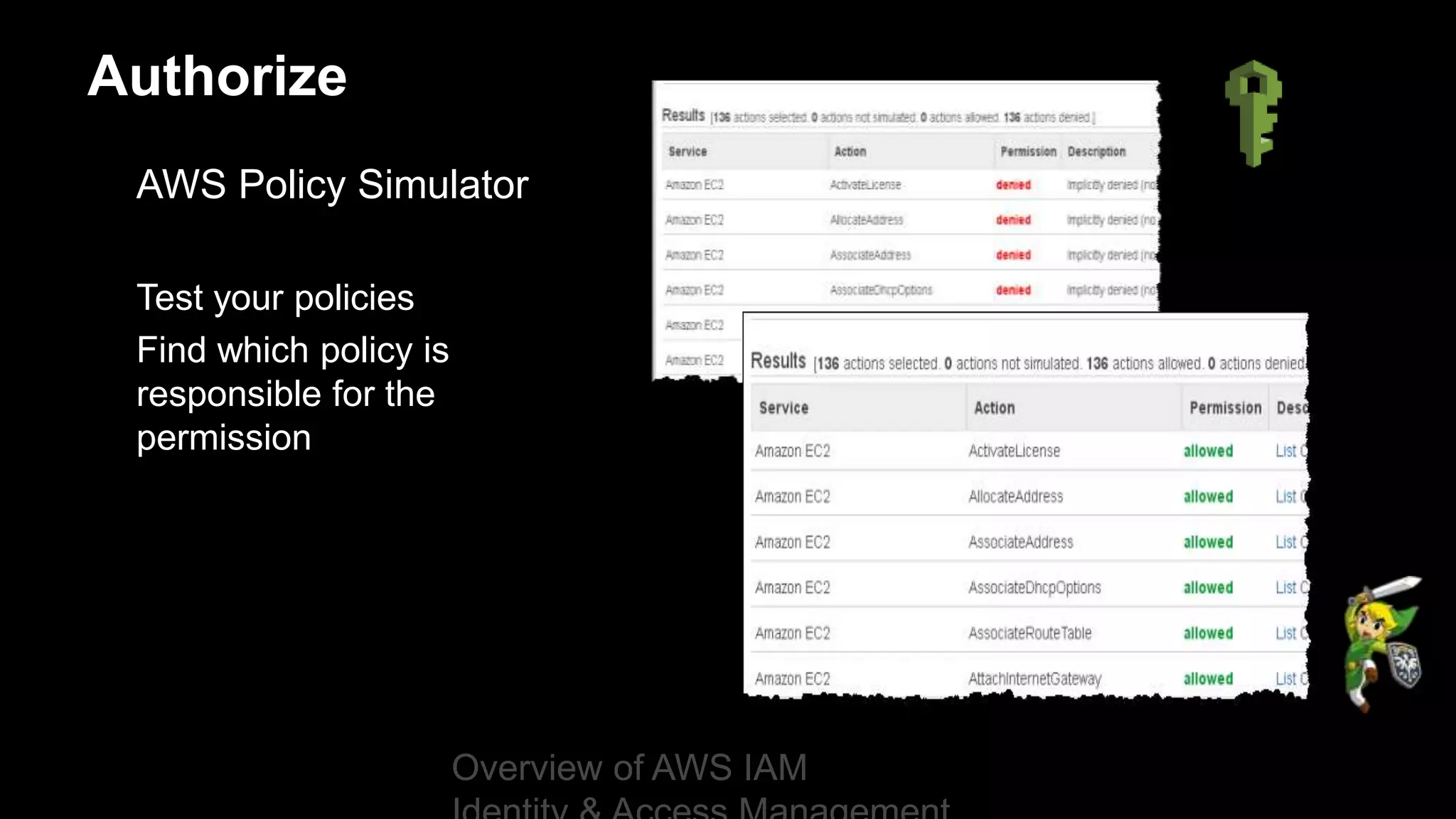
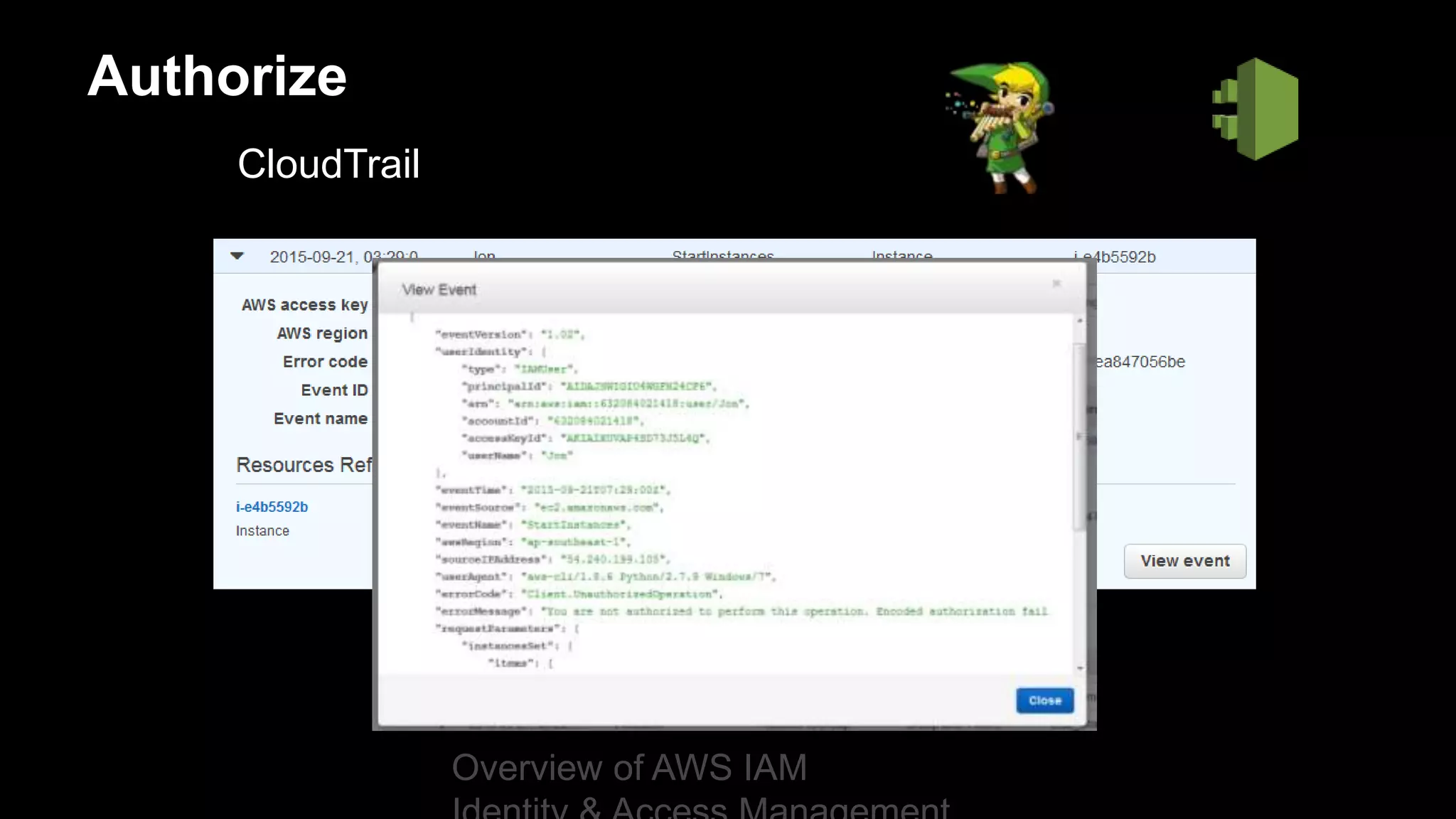
Authorize
Overview of AWS IAM
OR
AND](https://image.slidesharecdn.com/awsiambestpracticestoliveby-170615054516/75/Aws-iam-best-practices-to-live-by-12-2048.jpg)



![Enabling credential rotation for IAM users
(Enable access key rotation sample policy)
Access keys Steps to rotate access keys
1. Create a new set of credentials.
2. Update all applications to use the new
credentials.
3. Deactivate the first set of credentials.
4. Confirm that your applications are
working well.
5. Delete the first set of credentials.
{
"Version":"2012-10-17",
“Statement": [{
"Effect": "Allow",
"Action": [
"iam:CreateAccessKey",
"iam:DeleteAccessKey",
"iam:ListAccessKeys",
"iam:UpdateAccessKey"],
"Resource":
"arn:aws:iam::123456789012:
user/${aws:username}"
}]}](https://image.slidesharecdn.com/awsiambestpracticestoliveby-170615054516/75/Aws-iam-best-practices-to-live-by-20-2048.jpg)







![prod@example.com
Acct ID: 111122223333
ddb-role
{ "Statement": [
{ "Action":
[
"dynamodb:GetItem",
"dynamodb:BatchGetItem",
"dynamodb:DescribeTable",
"dynamodb:ListTables"
],
"Effect": "Allow",
"Resource": "*“
}]}
dev@example.com
Acct ID: 123456789012
Authenticate with
Rob’s access keys
Get temporary
security credentials
for ddb-role
Call AWS APIs
using temporary
security credentials
of ddb-role
{ "Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource":
"arn:aws:iam::111122223333:role/ddb-role"
}]}
{ "Statement": [
{
"Effect":"Allow",
"Principal":{"AWS":"123456789012"},
"Action":"sts:AssumeRole"
}]}
ddb-role trusts IAM users from the AWS account
dev@example.com (123456789012)
Permissions assigned
to Rob granting him
permission to assume
ddb-role in account B
IAM user: Rob
Permissions assigned to ddb-role
STS
How does federated access work?](https://image.slidesharecdn.com/awsiambestpracticestoliveby-170615054516/75/Aws-iam-best-practices-to-live-by-28-2048.jpg)





![How does tag-based access control work?
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:*",
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/Project" : "Blue"
}
}
}
]
}
Permissions assigned to Rob granting him permission to
perform any EC2 action on resources tagged with
Project=Blue
IAM user: Rob
i-a1234b12
Project=Blue
i-a4321b12
Project=Blue
i-a4321b12
Project=Green](https://image.slidesharecdn.com/awsiambestpracticestoliveby-170615054516/75/Aws-iam-best-practices-to-live-by-35-2048.jpg)