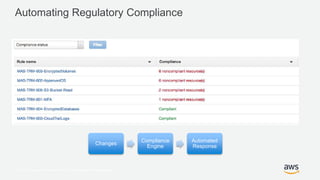
This document discusses the importance of data security and outlines best practices for ensuring confidentiality, integrity, and availability of data in the cloud. It describes Amazon Web Services' (AWS) physical and logical security controls to prevent unauthorized access to data centers and data. AWS provides a suite of security services to help with identity and access control, detection of threats, infrastructure security, incident response, and data protection through encryption. The document emphasizes automating security checks and compliance to help customers securely use AWS cloud services.