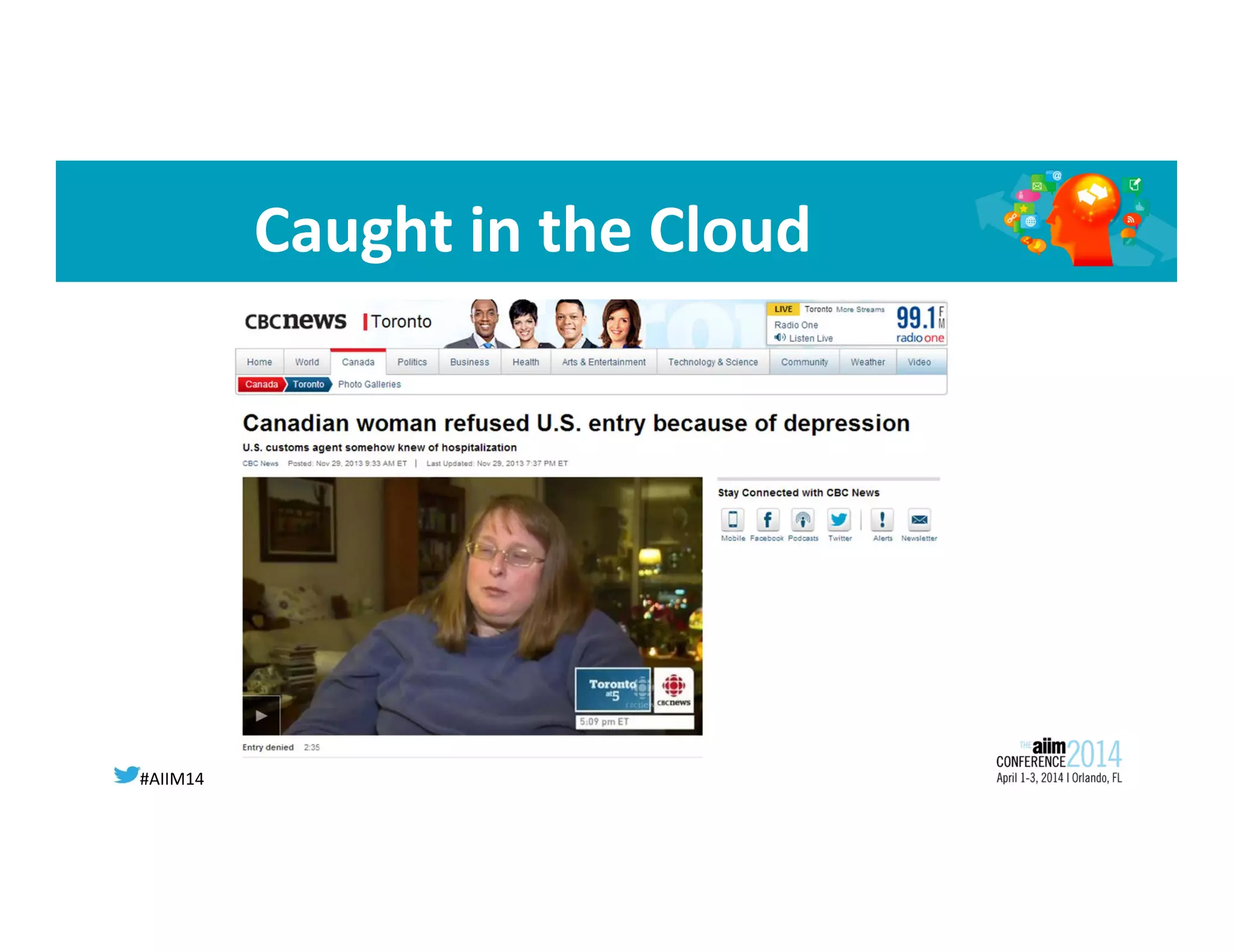
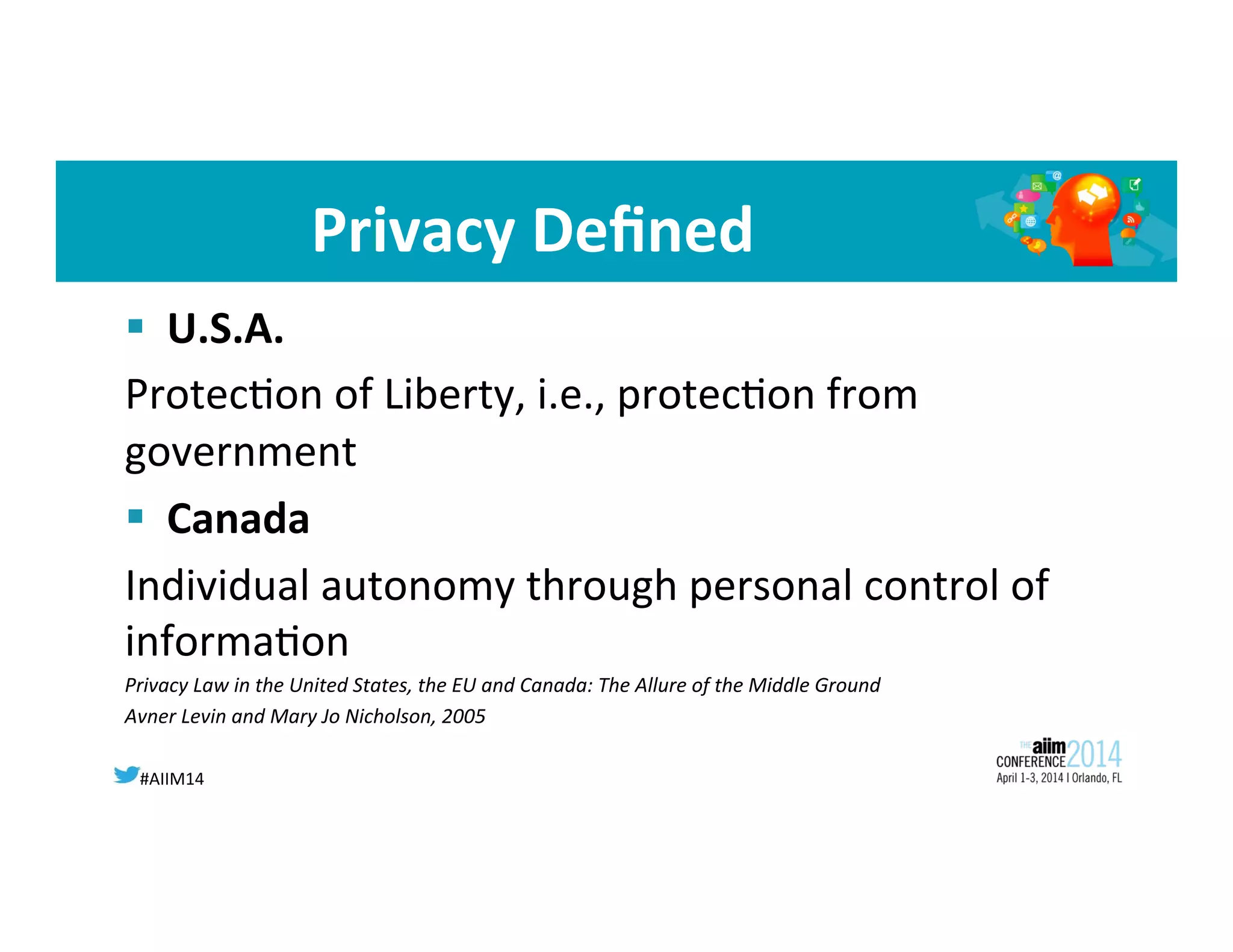
The document discusses the privacy risks associated with cloud computing, highlighting the loss of control over data and governance. It outlines Canadian privacy laws and the implications of U.S. legislation like the USA Patriot Act on personal information. Additionally, it emphasizes the need for accountability and strong contracts when outsourcing services to ensure compliance with privacy standards.